RaaS 101: Building Your Ransomware Defense Strategy
Written by: ceren
Written by Gokcen Tapkan
Additional Contributor Yavuz Han
Edited by Haley Williams
There is not a single person, nor group, that can assume full responsibility for infamous ransomware attacks. The ransomware business model has rapidly evolved over the past few years, creating the Ransomware as a Service (RaaS) cybercrime ecosystem where groups like REvil, DarkSide and Conti have thrived.
Ransomware as a Service (RaaS) 101
Affiliates and Ransomware as a Service have replaced the word gang in terms of their association with ransomware. Infamous REvil, DarkSide and Conti attacks have been executed by an affiliate model that involve much more than one individual group.
What is RaaS?
Just like the SaaS model, a ransomware affiliate can subscribe to the RaaS program for a lifetime, monthly, or on a project basis with profit-sharing conditions.
There are four common RaaS revenue models:
- Monthly subscriptions
- Affiliate programs: These are designed similar to subscription models, except a percentage of the profits (usually 20-30%) are shared with the RaaS operator
- Life-time subscriptions with no profit sharing
- Pure profit sharing
How does an affiliate enter the RaaS ecosystem?
When an affiliate pays for malware, he or she gains access to the same support, communities, documentation, feature updates, and other perks as legitimate SaaS product subscribers. The most advanced RaaS providers give customers access to portals that show the state of infections, total payments, total files encrypted, and other data about their targets.
An affiliate must act in accordance with the following steps to engage in a RaaS package:
- An online black market seller sells a copy of the RaaS software to a criminal. The program is purchased as a service, which means it can target many systems several times.
- The criminal makes an account, provides details about the sort of malware they want to develop, and submits the order (usually through Bitcoin). Depending on the subscription model, an affiliate may pay once for the malware and then use it repeatedly without paying again or following another model.
- The attacker then configures the software by selecting their preferred language and related parameters such as the amount of money they intend to demand from victims.
- Finally, the attacker obtains a unique cryptographic key connected with their copy of the malware, that will eventually be used to encrypt files on a victims’ system. The criminal can now conduct attacks on specific targets, knowing that only their files, with a particular extension, would be encrypted.
When the reward is big, marketing ramps up
RaaS operators have started to offer attractive incentives to recruit more affiliates. Thus, their marketing efforts fuel up as we witnessed with the AvosLocker Partnership program.
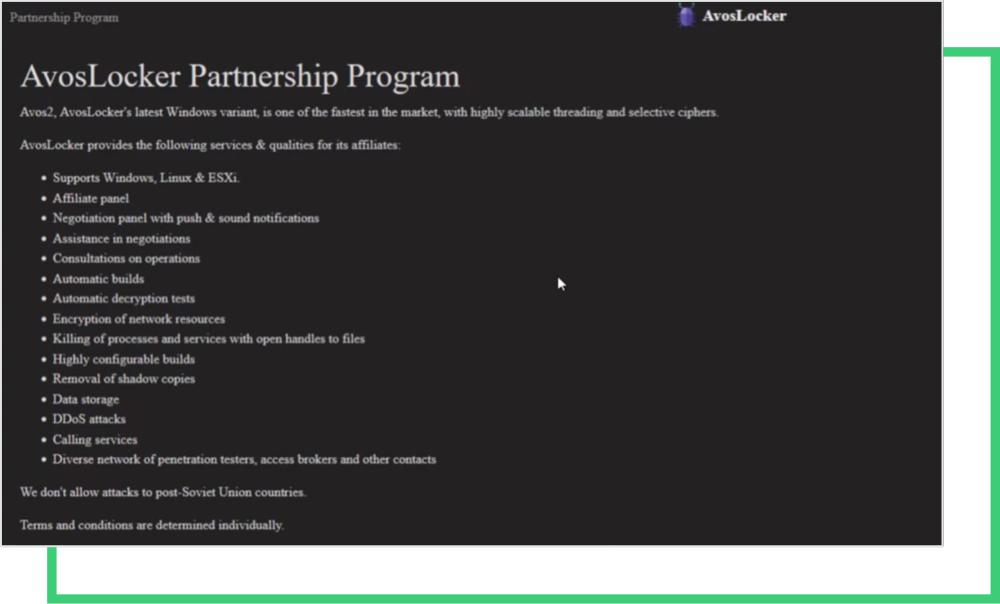
Among the skillsets & services these RaaS operators promote are:
- Windows, Linux, ESXi
- Affiliate panel
- Negotiation panel with push & sound notifications
- Assistance in negotiation
- Consultations on operations
- Automatic builds
- Encryption of network resources
- Killing of processes and services with open handles to files
- Highly configurable builds
- Removal of database copies
- DDoS attacks
- Calling services
- Disaster network penetration testers access brokers and other contacts
The services listed above outline the skills required to manage a ransomware operation. Recently observed is the addition of DDoS attacks, which triple the extortion process in a ransomware attack.
RaaS provides almost any service to affiliates for a complete ransomware attack based on the ad. Operators also lay the condition of not attacking Soviet Union countries. After all, there are many companies to attack in the world other than the Soviet Union, and everyone is trying to get a piece of this pie.
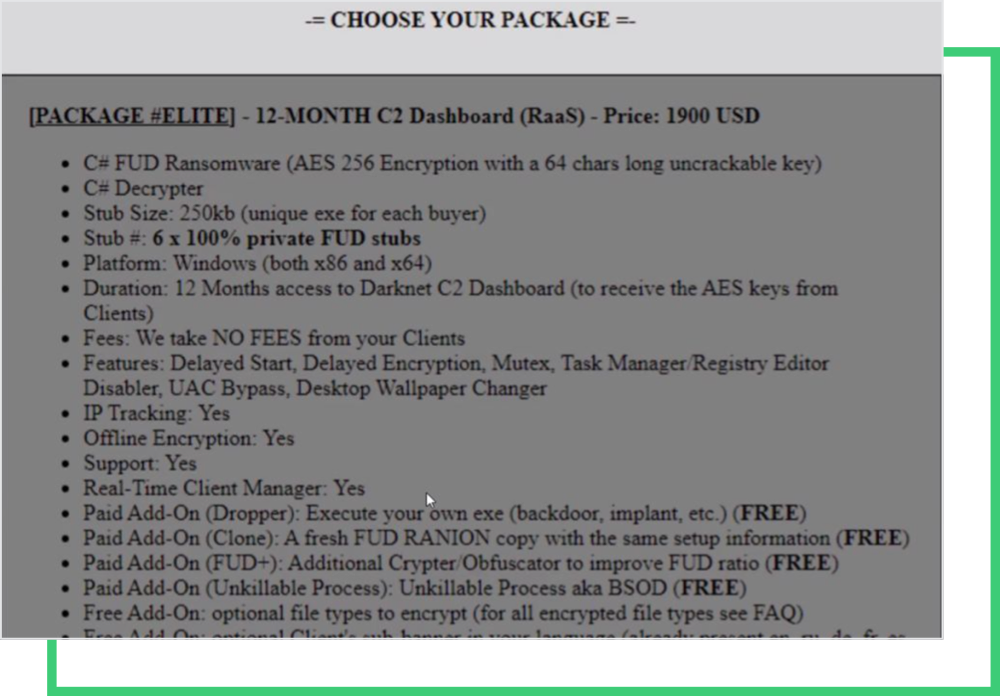
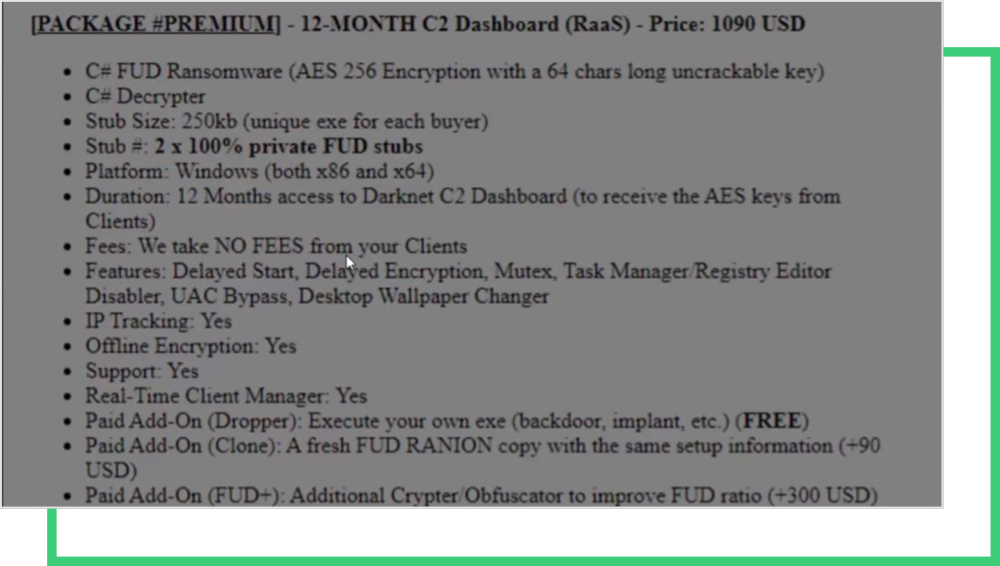
These screenshots are examples of another RaaS “marketing” post that offers membership to the FUD ransomware program. It offers two packages (Premium and Elite), just like in a SaaS membership. The posts’ owners grant access to Command-and-Control (C2) dashboards. The details in the ad also give a lot of information about how the RaaS service and ransomware groups work. Some of the features of the ransomware are:
- Delayed Start
- Delayed encryption
- Mutex
- Task Manager/ Registry Editor Disabler
- UAC bypass
- Desktop wallpaper changer
There are also paid add-ons, like droppers, crypto obfuscators, additional file types to encrypt, which can be provided for free, depending on the package the affiliate chooses to subscribe to.
How is RaaS evolving?
From intelligence of the deep web and headline news, these businesses are extremely lucrative. The government has many efforts in place to disrupt RaaS operations, such as the FBI’s seizure of ransomware wallets and servers. An example of a past disruption into the RaaS (Ransomware as a Service) business was the FBI’s gaining custody of a Revil and GrandCrab affiliate’s crypto wallet. Similarly, a closely-connected gang, the DarkSide’s servers, were shut down back in May after the Colonial Pipeline attack.
Despite all efforts, the RaaS ecosystem operates at full strength, rebrands where needed, and does not seem to stop in growth. However, as we covered in our last blog, criminals in this ecosystem have the maximum adaptation, as they might sign up for another platform once the one they partnered with has been taken down. So, these law breakers have a proven track record in responding to government pressure.
Although ransomware is not a new threat to the cybersecurity community, RaaS has introduced multifaceted extortion models. These days, in addition to encryption of systems, they threaten companies with
- Data leak
- DDoS threats
- Reaching out to media
- Reaching out to customers
- Harassing employees
- Harassing customers
News from a fresh RaaS: Yanluowang Gang
RaaS are continuously developing their tactics, malware, and partnerships. According to the link below, an affiliate of the gangs (Yanluowang) started to target some high-profile companies in the finance sector, leveraging BazarLoader malware. Other industries within their radar included manufacturing, IT services, consulting, and engineering sectors. As demonstrated in the case of Avloslocker, threat actors do not discriminate against sectors while growing.
Learn more about Yanluowang and DDoS threats.
How should CISOs address RaaS?
A cybersecurity program needs to be proactive rather than reactive, especially for a situation involving ransomware. Therefore, a CISO must ask these questions to evaluate the maturity of its cybersecurity security program for ransomware preparedness, along with all cybersecurity measures we covered in earlier blogs.
There are three questions about RaaS that all CISOs must ask their internal team:
- Do we have a clear strategy for ransomware? If so, are we more likely to be proactive or reactive, given the current maturity level?
- Are we aware of the legal repercussions of a ransomware attack? Does my team have legal respondents in case of ransomware?
- Do we have the capacity/bandwidth to deal with a ransomware attack?
Finally, perhaps the most critical question after a company gets hit is: “should we pay or not?” Although there is no “right” answer, the FBI and CISA strongly urge companies not to pay for ransomware demands. Payments made to these operators only makes matters worse, although it might seem like a quick solution in the midst of an attack.
When ransomware gangs are funded, they grow and add more affiliates to their program. Companies cannot be sure whether cybercriminals will sell their exposed data, even after the ransom payment. Since they deal with multiple affiliates, it’s important not to rely on the criminal’s word.
Taking it step by step to secure your sector from RaaS attacks is the best way to reduce risk and build a solid ransomware strategy. One way to do that is to check your RSI Rating.
Get a Free RSITM Rating
