Automate Compliance of Third-Party Cyber Assessments with Industry’s First Cyber-Aware AI Engine
Black Kite Transforms third-party compliance assessments with automation, saving companies days’ worth of manual effort
Streamline compliance assessment process and get the information you need on the gaps in compliance all in one place.
Black Kite Enterprise Frameworks
Automate compliance to a customized set of standards and controls.
As sophisticated TPRM programs know, no one single compliance framework (e.g., NIST, GDPR) covers all of their compliance needs. That’s why Black Kite created a way for our customers to create a completely custom framework unique to your organization. Pull controls from any of our 15 standardly supported frameworks or create your own.
With Black Kite Enterprise Frameworks, organizations can tailor compliance assessments to their exact needs. And, by leveraging Parser 2.0’s cyber-aware AI to parse and score compliance documentation (compliance policies, SOC2’s, and even questionnaire responses!), you can automate the vendor onboarding process and reduce review times from days to minutes.
Black Kite’s Parser

Current process
- Requires vendors to complete numerous questionnaires
- Modified, custom questionnaires can be labor intensive and complicated
- Vendors’ established policies place an added burden to parse and analyze
- Tedious for all parties involved
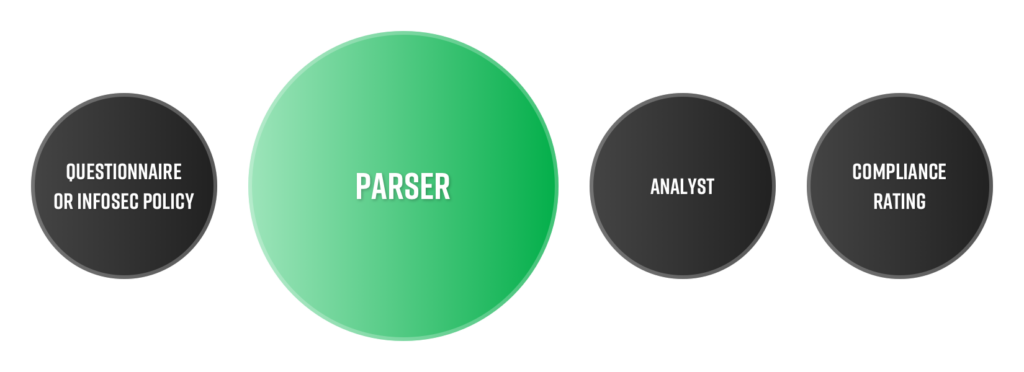
Automated with unique
- Consumes virtually any compliance document – SOC2, PenTests, and even questionnaire responses
- Parses documents within seconds using cyber-aware AI and maps content to 15 standardly supported compliance frameworks including NIST, GDPR, ISO27001, and more
- Immediately get a comprehensive view of your vendors’ compliance with a framework and identify the gaps in their procedures
- Natural language processing model correlates vendor cybersecurity findings to 15 industry regulations and standards
- Recognizes more than 130 different languages and trained to be cyber-aware
Black Kite Enterprise Frameworks
Automate compliance to a customized set of standards and controls.
As sophisticated TPRM programs know, no one single compliance framework (e.g., NIST, GDPR) covers all of their compliance needs. That’s why Black Kite created a way for our customers to create a completely custom framework unique to your organization. Pull controls from any of our 15 standardly supported frameworks or create your own.
With Black Kite Enterprise Frameworks, organizations can tailor compliance assessments to their exact needs. And, by leveraging Parser 2.0’s cyber-aware AI to parse and score compliance documentation (compliance policies, SOC2’s, and even questionnaire responses!), you can automate the vendor onboarding process and reduce review times from days to minutes.
Black Kite Compliance Gap Analysis
Provides a report of the controls that don’t meet a specified level of satisfactory compliance.
When used with Black Kite’s Parser 2.0, it reduces the number of questions you need to ask vendors and compliance controls that need further analysis.
Black Kite Compliance Ratings Are…
Based on Industry Standards
Strict adherence to cybersecurity compliance requirements reduces the risk of a data breach and the associated response and recovery costs, as well as the less-quantifiable costs of a breach such as reputation damage, business interruption, and loss of business. Black Kite allows you to measure the compliance level of any company for different regulations and standards, including NIST 800-53, ISO27001, PCI-DSS, HIPAA, GDPR, Shared Assessments, and others.
![]()
Cross-Correlated
Black Kite’s platform estimates the external compliance of target companies. The cross-correlation capability measures the compliance level of a target company based on the standard input, saving time and effort for both you and your vendors.
Shareable & Vendor-Friendly
You can share compliance control items/questions with vendors using Black Kite’s Strategy Report, or by directly inviting them to the Black Kite platform. Vendors can then fill out the control items/questions, and Black Kite can map the answers to other regulations and frameworks available in the system.
Verified via AI
If a third party is compliant with a regulation or framework, the vendor can then upload evidence documents (SIG and map data) to the Black Kite platform. Black Kite’s advanced AI algorithm then estimates the compliance level for the other regulations/frameworks using prior compliance standards.
Trusted by