The Secret to Ransomware Risk Management in 2021
Written by: Black Kite
By Bob Maley, Chief Security Officer at Black Kite
One of the most frequently asked questions I receive as a CSO in today’s risk environment is, “how can organizations avoid ransomware”? With a predicted attack rate of once every 11 seconds and a hefty $20 billion price tag, it’s no wonder as to why it’s at the top of the list of digital supply chain threats in 2021.
There’s a very low possibility that any simple set of guidelines will do the trick. The key instead is in understanding what cybercriminals look for when designing a ransomware attack, and addressing those issues before they have the chance to. In other words: Put yourself in the mind of a cybercriminals.
The Eight Most Common Ransomware Indicators and How to Avoid Them
1. Open Critical Ports
The more open ports, the larger the attack surface.
Certain ports are required to remain open in order for any network to function properly. Keeping too many open ports on your network, however, can significantly increase your likelihood of experiencing a ransomware event. In fact, open ports are quickly catching up to phishing as the most common vulnerabilities leveraged by ransomware attackers.
How to prevent vulnerabilities caused by open ports:
The need to keep ports open while keeping “unknown” threats out may sound like a catch-22 situation. Organizations can still address these issues by actively scanning and closing unauthorized open ports. If possible, only allow connections from known IP addresses that are in good standing. Use of multifactor authentication is also a good strategy.
2. Phishing or fraudulent domains
The most common attack vectors associated with ransomware are phishing and fraudulent domains.
The majority (65%) of ransomware attacks leverage phishing as a primary attack vector. The onset of the pandemic and the shift to remote work have only made matters worse, and malicious emails are up 600%. As a result, over half of IT decision makers agree targeted phishing attacks are their No. 1 security concern.
How to prevent phishing attacks from becoming successful:
All employees should be enrolled in continuous cybersecurity training, regardless of their function. Some employee training programs also allow IT teams to simulate phishing attacks. Those outside of the department then know exactly what to look for, instilling confidence in your staff and pinpointing any knowledge gaps that may exist within the organization.

Follow and analyze risky fraudulent domains with Black Kite’s free Phishing Domain Feed.
3. Vulnerabilities with Remote Code Execution (RCE)
Vulnerabilities with remote code execution enable network manipulation.
RCE intrusions are complex attacks made by malicious actors to gain access to a device, regardless of its geographical location. By posing as an approved network user, cybercriminals receive the same privileges and network access as the system user, enabling them to steal, delete, and/ or copy troughs of critical data.
How to avoid vulnerabilities associated with remote code execution:
Timely patch management and security updates are integral security measures for protecting and monitoring any risky service throughout your entire vendor ecosystem. As the world continues to shift to a new business paradigm, we should expect more zero-trust security models to guarantee data remains in the right hands.
4. Endpoint Security
Endpoint security holds an integral position in any supply chain’s line of defense.
The majority (68%) of organizations have experienced at least one attack that’s resulted in compromised data and or/ IT infrastructure. Centralized network protection is not enough to combat today’s threat landscape. Each endpoint serves as a gate protecting your digital assets from bad actors. More remote devices pose greater cyber risk—making endpoint security another key ransomware indicator.
How to optimize endpoint security:
It’s virtually impossible to expect all vendors, suppliers, or other third parties to implement identical cybersecurity policies and procedures. Still, they need to be held accountable. Work together with third parties to ensure all gateways throughout your entire cyber ecosystem are actively monitored and reviewed for suspicious activity.
5. Email Security
Email is the most common channel leveraged during ransomware deployment.
About 1 in 6,000 emails contain suspicious URLs, yet only a mere 3% of targeted report malicious emails to management. Advanced hacking techniques that are harder to detect add another layer to the complexities associated with email security, as cybercriminals turn to social engineering attacks and other advanced, harder-to-detect techniques.
How to strengthen email security:
To combat growing security concerns over email communication, pressure should be placed on IT and security teams to deploy Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-Based Authentication, Reporting and Conformance (DMARC) implementations for all domains and subdomains.
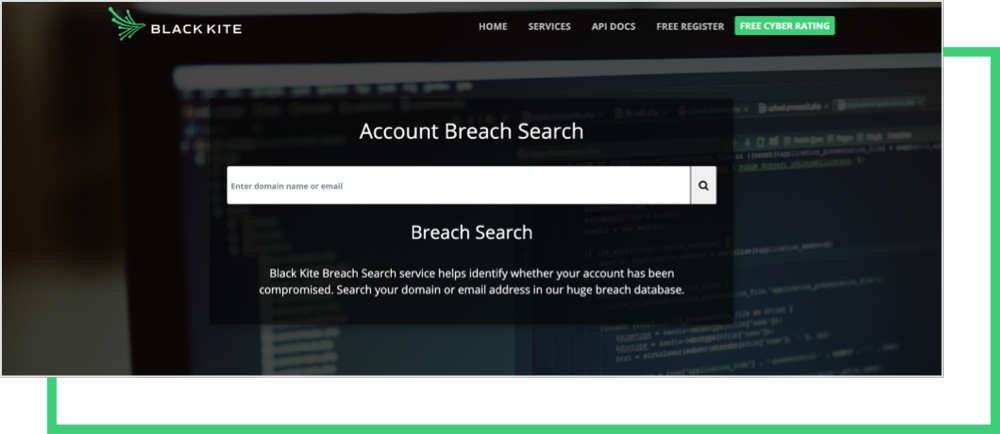
6. Leaked Credentials
Compromised credentials are the most common initial attack vector.
Credential theft is a significant vulnerability leveraged in ransomware attacks, with over 80% of hacking breaches involve brute force or stolen credentials. With the frequency of credential theft on the rise, password policies and password management solutions have become more top-of-mind for today’s security teams.
How to keep your accounts protected:
All organizations, regardless of the level of data sensitivity, should require employees to use strong, unique passwords and challenge responses. Multi-factor authentication (MFA) should also be made mandatory wherever possible. When multiple identification processes are required, it makes it extremely difficult for threat actors to infiltrate a user’s account using a password alone.
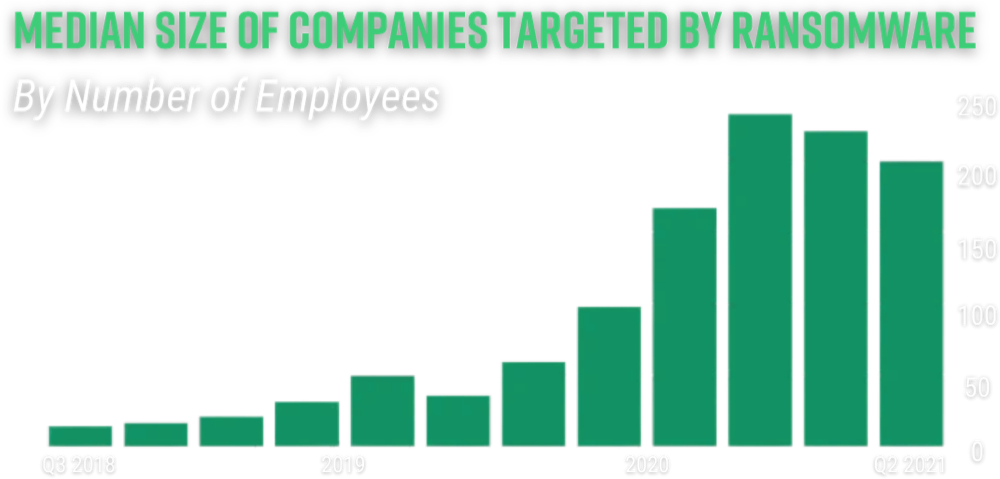
7. Company Size
The size of your organization plays a direct role in your ransomware susceptibility…
Despite 71% of ransomware attacks now targeting small businesses, most (70%) of them do not feel prepared to properly address a cyberattack. Ransomware groups are benefitting from a ‘low effort, high reward’ model by leveraging weaker links within a supply chain to infiltrate larger organizations with a higher payout.
How to address security concerns specific to company size:
All organizations require an enterprise-level cybersecurity program. Although security budgets are a common pain point for many small and mid-sized businesses (SMBs), increasing ransom demands are enough to justify the investment. Managed security service providers (MSSPs) are a great option for those that cannot maintain in-house cyber management operations.
8. Company Industry
… as well as the industry you’re in.
Eighty percent of healthcare organizations have experienced a data breach over the past few years. It’s not just by coincidence that the industry sits on top of cybercriminals’ hit list, either. The essentialness of healthcare operations as well as the sensitivity of patient data makes it a goldmine for ransom demands.
How to minimize industry-related security risks:
Every industry is at risk. While you can’t change the nature of your business because of its heightened ransomware risk exposure, you can take extra precautions to keep the attention away from your organization. Actively monitor your cyber posture as well as the vendors you exchange critical information with to keep the target off your back.
Ransomware Risk Management From a Different Perspective
These indicators aren’t necessarily news to people. In fact, companies have been encouraged to actively monitor and address these controls for over a decade. CISA’s ‘Stop Ransomware’ campaign, for example, provides guidance for addressing these common ransomware attack vectors. However, these compliance checklists aren’t built to scale.
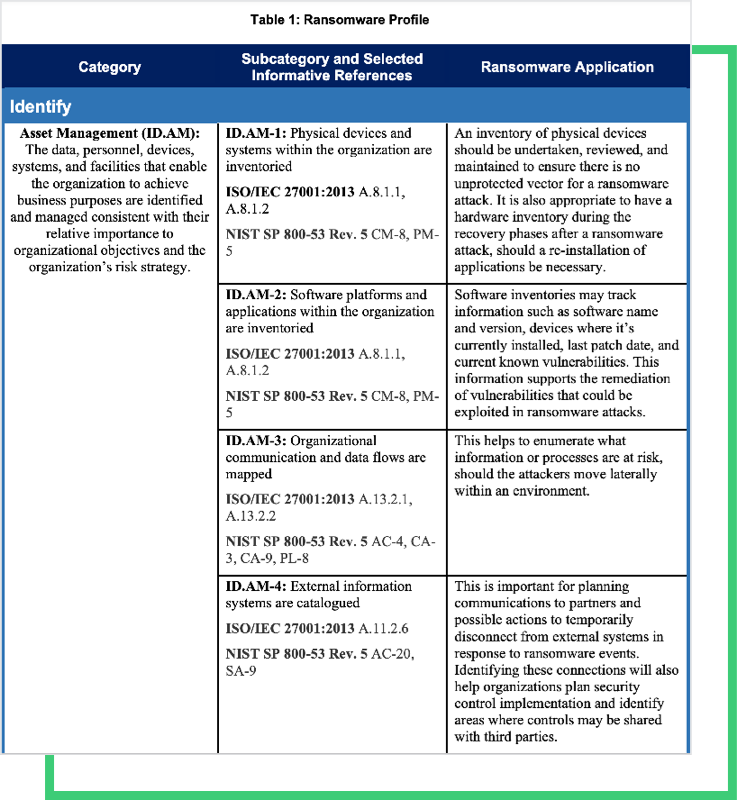
Say, for example, you have 1,000 vendors within your cyber ecosystem. The eight controls listed above alone would require you to capture, analyze and manually prioritize 8,000 raw data points… only a fraction of the working NIST Cybersecurity Framework Profile for Ransomware Risk Management (NISTIR 8374).
Another problem with compliance checklists is that they aren’t designed to match the sophistication of evolving ransomware threats. Multiplying in frequency, cost and now complexity, today’s ransomware model is enough to threaten even the most mature cybersecurity programs.
The Kaseya, T-Mobile, Accellion and other major data breach victims all follow a similar theme. Why? History repeats itself. Signals may be your secret weapon, but understanding how they’re perceived by malicious actors is your silver bullet when it comes to ransomware risk detection.
Perhaps the only silver lining from the uptick in ransomware is the ability to detect trends. Delaying a software update won’t necessarily result in a ransomware attack, just as a compromised credential won’t always lead to a data breach. The correlation between these controls and more will provide much more insight into your ransomware risk exposure.
Simply put: The “secret” to uncovering your ransomware susceptibility is understanding the interrelationship between controls—and being able to do so at scale. Black Kite’s Ransomware Susceptibility Index® reduces that unscalable compliance checklist approach with a data-driven methodology that discovers the likelihood of experiencing a ransomware attack.



