Conti Catches Fire as Ransomware Business Model Matures
Written by: ceren
Written by Gokcen Tapkan
Additional Contributor Yavuz Han
Edited by Haley Williams
Conti—one of the most notorious groups of all time—has orchestrated yet another development in the sophistication of ransomware as a service (RaaS). Already naming over 400 victims and counting, the Conti ransomware gang is made up of some of the greediest masterminds the cyber community has seen to date.
Now selling its initial access broker (IAB) services for various companies across the UK and US, Conti continues to reinvent ransomware operations. While the Black Kite Research Team recently analyzed the indicators of compromise (IOCs) in our recent analysis of Conti’s ransomware playbook, there’s already a new business model catching fire as this cyber epidemic continues.
What’s New to the Conti Ransomware Playbook?
“We are looking for a buyer to access the network of this organization and sell data from their network.”
The Black Kite Research Team discovered Conti’s posts beginning October 23rd include the additional sentence above, hinted that the threat actors expanded to a more effortless model instead of orchestrating the whole ransomware operation. This role is known by the ransomware community as Initial Access Broker (IAB).
As the ransomware business continues to scale, it’s more challenging to coordinate the ransomware operation from initial access to ransom payment negotiation and sale of data. Although Conti has subcontracted some tasks to its affiliates, the ransomware gang is the brain behind the operations.
What is Initial Access Brokerage? (IAB)
IAB is a commonly used term in the ransomware business, referring to the middlemen who use their methods to breach a company’s network. IABs frequently sell access to other threat actors, most commonly ransomware gangs or their associates, once they have gained access and established some amount of persistence on the network.
As reported by Infosecurity Magazine, the uptick in remote access from the pandemic is a primary factor that aids IABs in establishing and maintaining access. Due to this epidemic, organizations have rapidly accelerated their adoption of cloud apps, often without integrating basic security measures such as multi-factor authentication (MFA) for authorized accounts. As a result, attackers gain a foothold in vulnerable networks by exposing remote services.
IABs save ransomware attackers the time and effort to gain initial access and then move laterally through the network to infect and encrypt other assets before demanding the ransom. That way, they can devote all of their time and resources to their malware payloads and coordinating the ransomware operation.
As we discovered in the Conti playbook, RDP is one of the most utilized entry points for ransomware actors or end-products for IABs. Some groups, including Conti, scan the internet for exposed RDP ports and brute-force the credentials to gain a foothold on the target network, so that they can sell it on the dark web or on their own sites, as in Conti’s case.
What are Conti’s Common Indicators of Compromise (IOCs)?
Driven by Conti’s ransomware IOCs, the research team analyzed a sample set of 20,000 companies continuously monitored by the Black Kite platform. The cyber posture of companies consists of data gathered in the last three months. Our analysis took into account the three attack vectors leveraged by Conti.
1. Exposed RDP ports
88% of companies on our sample set have exposed critical ports, including RDP. Remote Desktop Protocol (RDP) is a Microsoft-developed proprietary protocol that allows users to connect to another computer via a network connection using a graphical interface. The user uses RDP client software, while RDP server software is required on the other machine.
RDP allows users to control their remote Windows machine, as if they were working on it locally. It’s a popular protocol to access a Windows machine remotely.
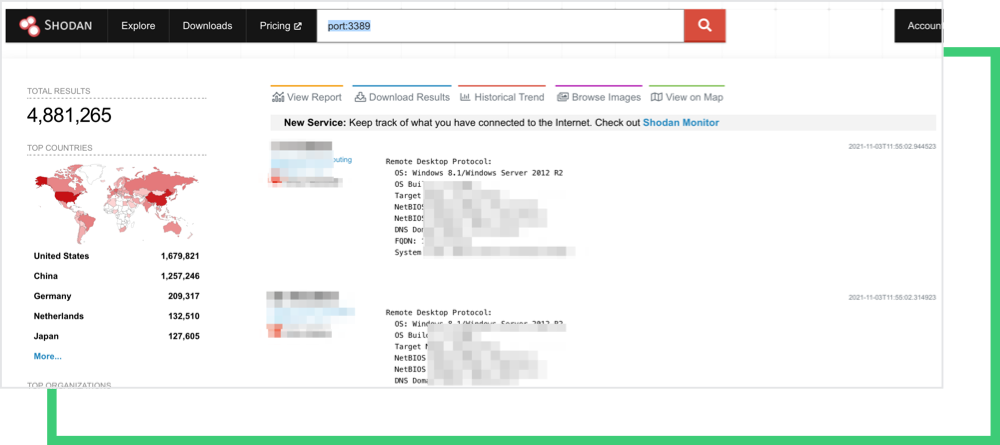
There are around 4.8 million RDP servers exposed to the internet and more accessible from the internal networks. This is an important issue, as it is the default connection protocol for Microsoft Azure and Hyper*-V, in which hackers are well aware of this fact.
2. Phishing
Nearly 20% of the pool have poor email security configuration, which makes them susceptible to phishing.
3. Software vulnerabilities
About 14% of the victims have vulnerabilities associated with at least one of the following CVEs commonly exploited by the Conti gang.
- CVE-2018-1337 , Fortinet vulnerability
- CVE-2018-13374, Fortinet vulnerabilitiy
- CVE-2020-1472, Zerologon (Windows Netlogon) vulnerability
- CVE -2021-34527, Print Nightmare, Windows Print Spooler vulnerability
- CVE-2017-0144, MS17_010, Windows Server SMB
The Ransomware Susceptibility Index® Distribution of Conti Victims
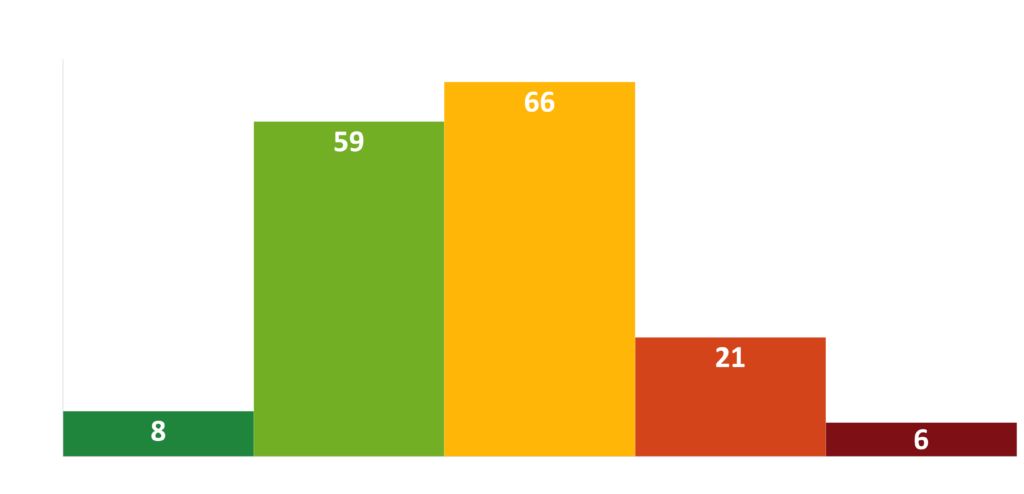
Ransomware attacks made by Conti in the last six months yielded significant RSI™ ratings with a mean RSI™ of 0.46. Black Kite Research considers it a risky zone if a company’s RSI™ score is above the 0.4 threshold and a critical zone if a company’s score is above 0.6.
Why Expand Now?
As the ransomware business scales, it becomes much more complicated and even dirtier as was apparent in the Graff Diamond attack. The attackers had not done enough checks before publicizing the leaked files, most likely due to insufficient resources, staff shortage, etc.
Eventually, Conti had to apologize for some of the personal information they published. Initial access had always been one of the strengths of Conti, and they were also recruiting members or hiring affiliates for the lateral movement. The sale of data was always through their dedicated site. Moving forward, they probably would want to channel their resources to a more effortless model including IAB and leave the data sales to other actors.
Conti’s Attack on Graff Diamond
London-based jewelry retailer Graff Diamond joined Conti’s list of ransomware victims last week. Conti demanded a multimillion dollar ransom to recover the 69,000 files it stole, which included documents for 11,000 high-profile clients.
Conti has already published receipts of purchases belonging to some notable celebrities including Victoria Beckham, Oprah Winfrey and Tom Hanks, as well as royal family members from Saudi Arabia and UAE. The leaked list also contained an item purchased on behalf of “Make a Wish” charity. The debate around the incident continued as the threat actors posted a statement in response.

So what does the announcement tell us? At first glance, it points out the hypocrisy of this business. The threat actors positively discriminate against some individuals and state that Saudi Arabia, Qatar, and UAB family members will be exempt from any disclosure. While apologizing to ‘select members’ for not doing enough due diligence on published files, Conti promises to target companies/individuals in the US and EU.
The announcement reads:
“Our goal is to publish as much Graff’s information as possible regarding the financial declarations made by the US-UK-EU Neo-liberal plutocracy which engages in obnoxiously expensive purchases when their nations are crumbling under the economic crisis, unemployment and COVID. While the Nations of America and Europe are choked by lockdowns and totalitarian surveillance, the neoliberal elites of these states enjoy the luxury of a feast in time of plague”
The mention of “people crumbling under the crisis of unemployment and COVID” is engrossing and hard to believe, as it is obvious from past cyberattacks, that the least Conti cares about is humanity. If this was the case, healthcare would not have been a target of ransomware gangs in the current time of “plague” as they mention. As far as Black Kite data is concerned, 5% of its victims constitute healthcare and healthcare-related sectors.
Conti’s infamous healthcare attack against Ireland’s Health Service Executive (HSE) affected the information systems that regulate all local and national health services, despite preventive measures taken to shut down systems. the information systems that regulate all local and national health services were affected. The Conti Ransomware group explicitly claimed responsibility for the attack, and according to the media, hackers demanded $20 million.
How to Prevent Unrecognized Ransomware Risk
An assume-a-breach approach concentrates on the aftermath of an attack and tries to limit the damage. On the other hand, a prepare-for-breach approach focuses on the utmost prevention techniques, from phishing to patch management to multi-factor authentication, and hidden backups. Thinking proactively about your risk management approach rather than reactively, constantly improves things.
It’s always a good idea to follow the practices published by authorities. One such recommendation is in relation to what CISA recently released for organizations to defend against ransomware and prevent data breaches. The info sheet named “Protecting Sensitive and Personal Information from Ransomware-Caused Data Breaches” is a generalized set of best practices and recommendations and sector-free. Therefore, any sector can adapt these set of control items to increase its cybersecurity maturity and immunity to ransomware attacks. Read our blog for more information on CISA’s recommendation.
Black Kite investigates ransomware attacks, as well as third-party breaches on its platform. For every incident, Black Kite Research records the Ransomware Susceptibility Index® (RSI™) and the cyber security posture of the breached company. Built from a hacker’s perspective, Black Kite’s RSI™ collects data from various open-source intelligence (OSINT) sources including internet-wide scanners, hacker forums, the deep/dark web, and more to determine how susceptible a company and its’ third parties are to a ransomware attack.
Free RSITM Rating
