AvosLocker Emerges as Next-Generation of RaaS Outpaces FBI
Written by: ceren
Written by Gokcen Tapkan
Additional Contributor Yavuz Han
Edited by Haley Williams
Continued ransomware developments on the dark web have kickstarted defensive operations, including the FBI’s recent seizure of ransomware wallets and servers. According to court files, the FBI gained custody of a Revil and GrandCrab affiliate’s crypto wallet, the latest update since a closely-connected gang called DarkSide had its servers shutdown following the Colonial Pipeline attack in May.
However, despite all of these efforts, the Ransomware as a Service (RaaS) ecosystem continues to operate at full strength, rebrands where needed, and continues to grow and regrow.
What is RaaS?
RaaS is a subscription-based membership model that allows affiliates to execute ransomware attacks using pre-developed tools. Rather than producing and immediately utilizing ransomware, ransomware groups now sell it on the dark web using the Software as a Service (SaaS) business model. Each successful ransom payment earns affiliates a commission.
Just like with SaaS, a ransomware affiliate can subscribe to the RaaS program for a lifetime, monthly, or on a project basis with profit-sharing conditions.
RaaS and the Axolotl: Regrowth and Adaptability
Axolotls may be cute on the outside, but the actors we compare them to, RaaS, often have frightening avatars on dark web forums. Both axolotls and RaaS affiliates have the ability to adapt quickly, camouflage into the environment, and perform complete regeneration.
If an Axolotl’s back becomes paralyzed, the paedomorphic salamander will grow all new neurons and connections that allow it to use its legs again. Similarly, ransomware gangs can become fully functional within a few weeks by developing new partnerships and adding new affiliates to their program.
AvosLocker Fuels RaaS Business Model Amidst Crypto and Server Seizures
One such RaaS example is AvosLocker, a newly emerged group that has found a place in double extortion gangs. The program was first discovered back in July, using “AVOS” as an alias on a dark web discussion forum called Dread.
The group’s ransom note contains information and an ID that may be used to identify victims. It directs people who have been infected to the AvosLocker Tor site for data recovery and restoration. Ransom requests reportedly range from $50,000 to $75,000 Monero.
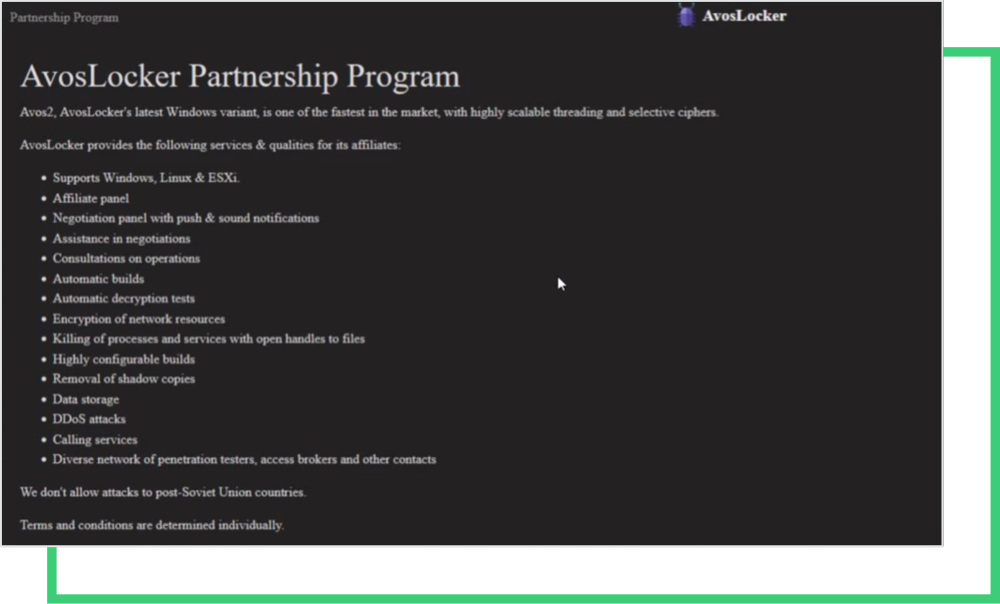
According to an ad posted on the AvosLocker site, AVOS currently seeks partnerships. To promote this to prospect affiliates, they listed the following skillsets:
- Windows, Linux, ESXi
- Affiliate panel
- Negotiation panel with push & sound notifications
- Assistance in negotiation
- Consultations on operations
- Automatic builds
- Encryption of network resources
- Killing of processes and services with open handles to files
- Highly configurable builds
- Removal of database copies
- DDoS attacks
- Calling services
- Disaster network penetration testers access brokers and other contacts.
The services listed above outline the skills required to manage a ransomware operation. Recently observed is the addition of DDoS attacks, which triple the extortion process in a ransomware attack.
Which countries are targeted by AvosLocker?
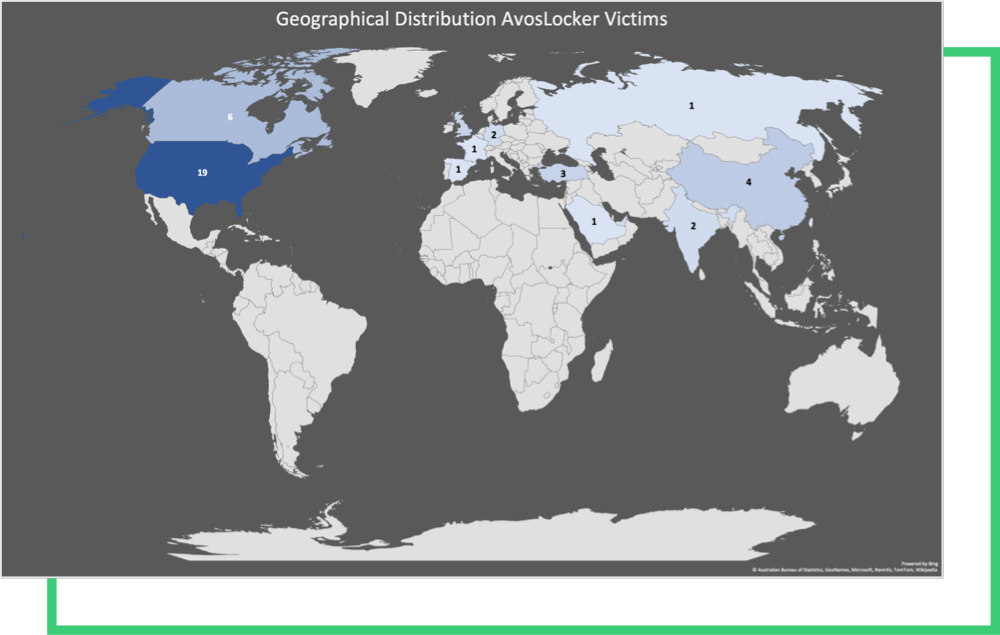
Since AvosLocker ransomware’s emergence in July 2021, Black Kite Research has closely monitored the AvosLocker gang. We know from industry distributions that ransomware groups do not discriminate against anyone, however it does favor targets in the US and Canada. Close to 40% are US based, although the affected organizations are distributed to different regions around the world.
One affected organization, possibly a branch of a US victim, is based in Russia. This contradicts their policy about not attacking Russia, their claimed hometown.
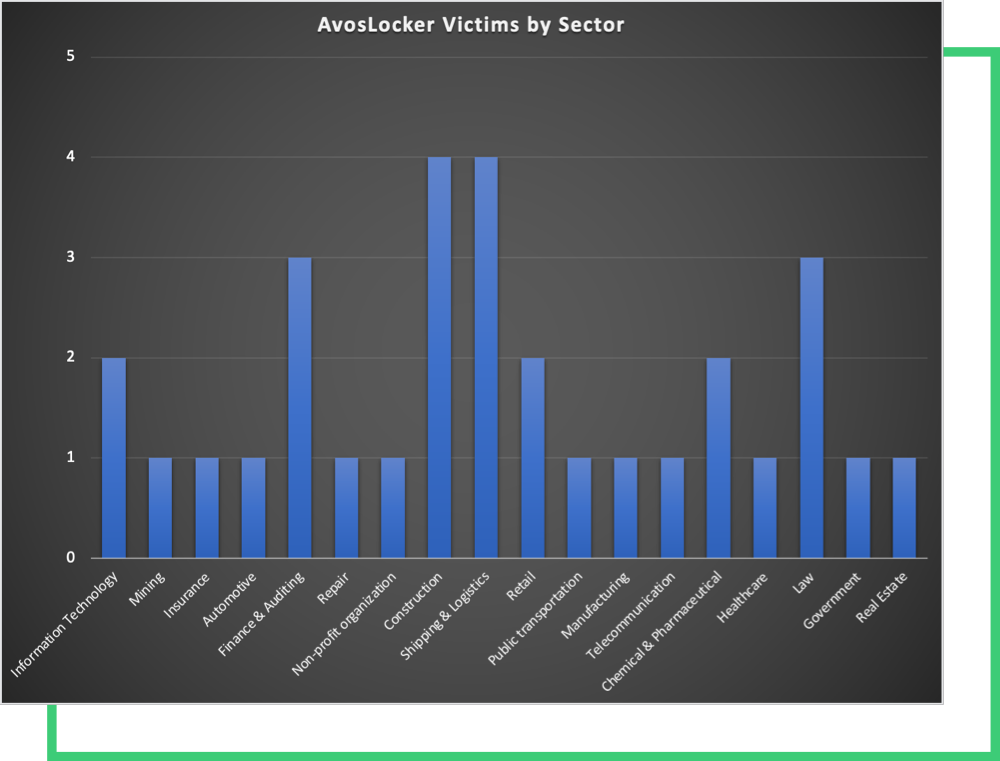
Is my sector at risk of AvosLocker ransomware?
The sectoral distribution tells a similar story. Nearly any sector could be, or already is, a target. Logistics and construction sectors are targeted slightly more often than other sectors, hinting that the gang is after quick and small wins, rather than large-scale sensational attacks.
How can I protect my organization from RaaS attacks?
The RaaS business is thriving as more profits are made in this sector, despite the substantial efforts of law enforcement. It may seem like a quick solution for victims to pay ransoms, however that can create more problems in the future.
When the ransomware gangs are funded, they grow and add more affiliates to their program, making them stronger. The good news is that there are alternative options to managing ransomware risk in today’s complex landscape.
Instead of paying for ransomware demands, the FBI urges companies to:
- Back up sensitive and confidential information in a separate network that is segmented from the main network.
- Enable multi-factor authentication to limit bad actors by increasing the amount of information necessary to access a network.
- Perform patches regularly to ensure all systems are properly installed and maintained.
- Update antivirus and anti-malware software regularly to ensure you’re keeping your organization protected even after installation.
We know how daunting it may feel to secure your sector from ransomware attacks. In addition to implementing the FBI recommended steps within your organization, see where your biggest risks lie today.
Get a Free RSITM Rating
