Black Kite’s Ransomware (RSI™) Computation Enhanced to Reflect Emerging Risk Indicators
Written by: ceren
Written by Ferhat Dikbiyik
Edited by Haley Williams
Ransomware and rapidly evolving supply chains are surging cybercrime in ecosystems worldwide. Strengthened with monetary motivation and the cyber warfare of political conflicts, threat actors have taken sides and declared their position. With the shift of TTPs of ransomware groups and their targeting mindset, we’ve calibrated the RSI™ tool to reflect the new state of ransomware attacks.
Black Kite’s Ransomware Susceptibility Index® (RSI™), a tool that uses data and machine learning to provide the likelihood an organization will experience a ransomware attack, is consistently updated with this ransomware incident data, drawn from our database, to further enhance the accuracy of our findings.
The RSI™ calculation now utilizes data analysis techniques, the cumulative cybersecurity expertise from our sources, the effects of common ransomware attack vectors, including the company’s country, industry, and their annual revenue, as well as specific risk factors (regional, industry-based, and organizational).
After US authorities shut down the infamous ransomware group REvil, other ransomware groups like Conti, Lockbit, AvosLocker, and Lapsu$ seized additional opportunities to pursue their operations. A shift has become more visible in these groups’ techniques, tactics, and procedures (TTPs) and how they choose their targets, explained throughout the article.
Discover how quickly cyber warfare worldwide has escalated in our analysis of the timeline of events.
The Methodology of Our Research
Black Kite Research analyzed 1,336 ransomware incidents in 2021 and more than 600 ransomware incidents in 2022. The team closely monitored deep web/darknet ransomware blogs, threat actors’ Telegram groups, and cyber security news feeds to identify companies that fell victim to ransomware attacks.
For comparison, the team selected a control set of 1,000 companies with “good” cybersecurity practices and posture. “Good” is typically defined as a recently scanned organization, with a cyber rating higher than 75, patch management score higher than 80, and no ransomware attacks in the last three years.
Our research utilizes data analysis techniques and the cumulative cybersecurity expertise to understand the effects of common ransomware attack vectors, now including the company’s country, industry, and their annual revenue related to current ransomware trends, as well as the risk factors detailed below.
Within the new RSI™ calculation, Ransomware’s Common Indicators Remain Consistent
The Ransomware Susceptibility Index® checks the common technical indicators of ransomware attacks, as shown below.
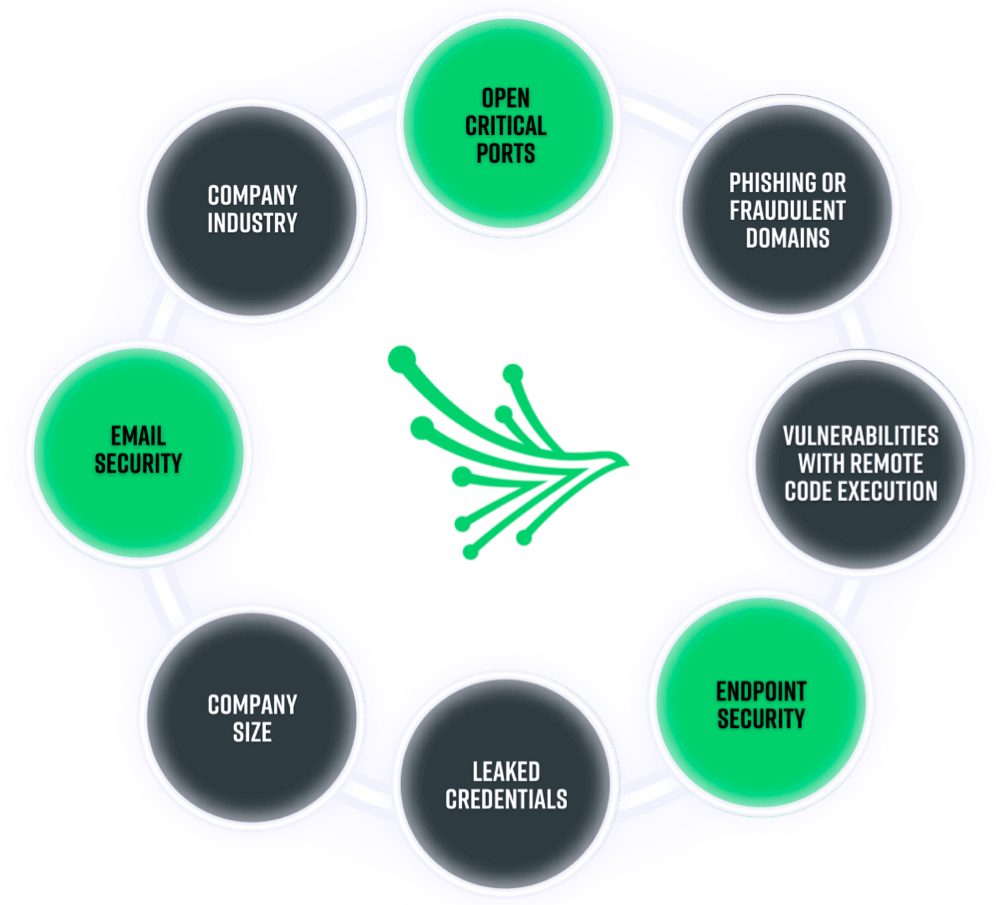
Black Kite Research completed an extensive analysis of the TTPs (tactics, techniques and procedures) of ransomware groups. The detailed study on Conti’s playbook, AvosLocker’s victims, and Lapsu$’s posts show that while they use complicated techniques, their initial access is usually granted through exploiting a critical vulnerability allowing remote code execution.
Despite reports in previous years revealing email phishing attacks as most common, recent critical vulnerabilities such as Zerologon (Windows Netlogon), PrintNightmare, MS17_010 (Windows Server SMB), and the discovered Fortinet vulnerabilities have given threat actors increased opportunities for initial access. These actors can now automate the process of searching for companies with these vulnerabilities and in turn, exploit the companies. This automated process is an easier lift than traditional phishing attacks.
The technical analysis of ransomware victims also confirms this finding when we compare incidents from 2021 and 2022. Companies that operate on up-to-date products that prioritize regular patching become less likely to experience a ransomware attack. In addition, having a certain number of critical vulnerabilities with high exploitability is correlated with being a target of ransomware groups.

Within the new RSI™ calculation, Regional Risk is now more thoroughly accounted for
Black Kite Research identified the threat actors from Russia and its allies are primarily targeting companies in the US and Europe, which is also reflected in increasing RSI™ ratings for companies in these regions.
Moreover, with the Russian government’s reduction of pressure on cybercriminals, they have more flexibility to attack. This motivates the adversaries to attack SMBs and target companies with higher revenue sizes.
After the shutdown of Revil’s servers, ransomware groups united to disrupt US operations. Some groups, such as Groove, publicly declared this interest on their deep web blogs.
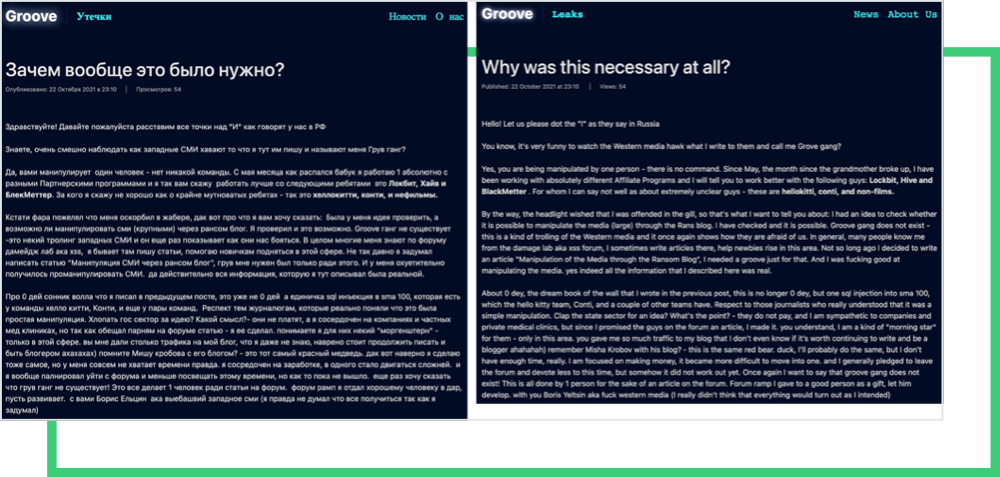
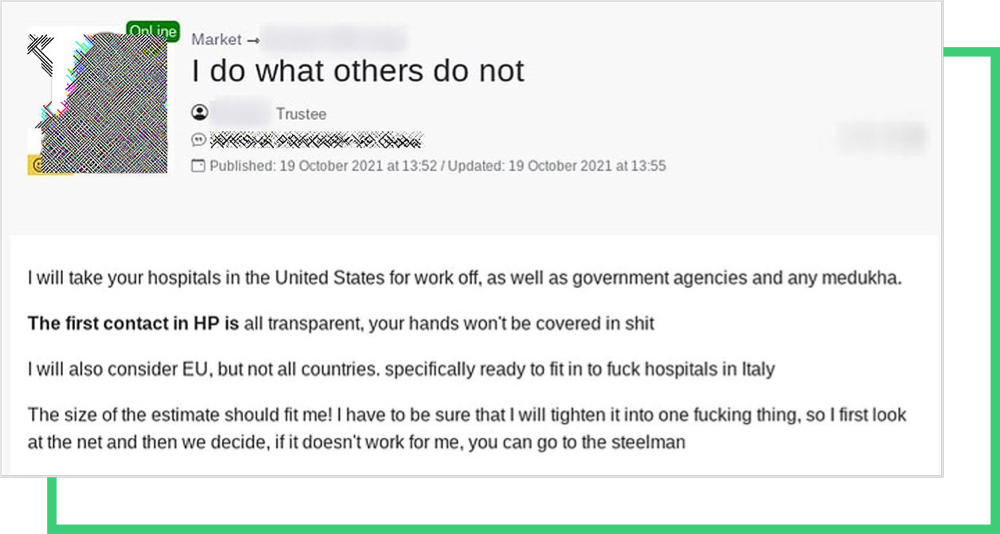
The Russian invasion of Ukraine fueled the situation, and the state-sponsored groups started to frequently target Western countries, as well as countries publicly supporting Ukraine.
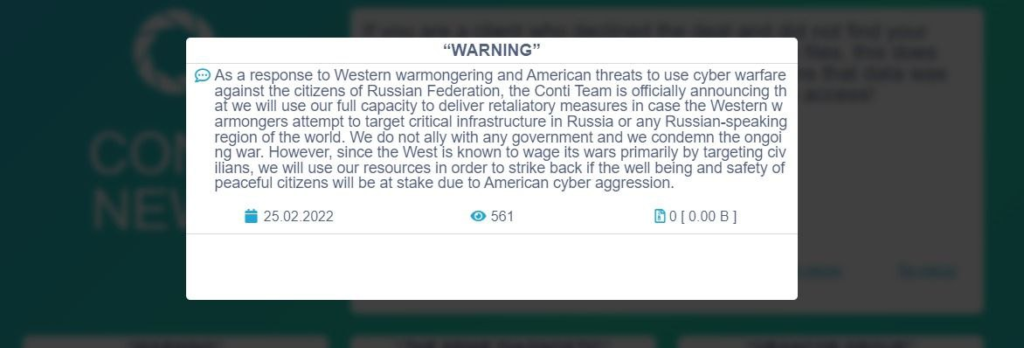
Even before this increase of cyber warfare, the ransomware groups mentioned in their posts that they would not target post-Soviet-Union countries. We can see this targeting mindset confirmed in different ads posted to hacker forums by ransomware groups.
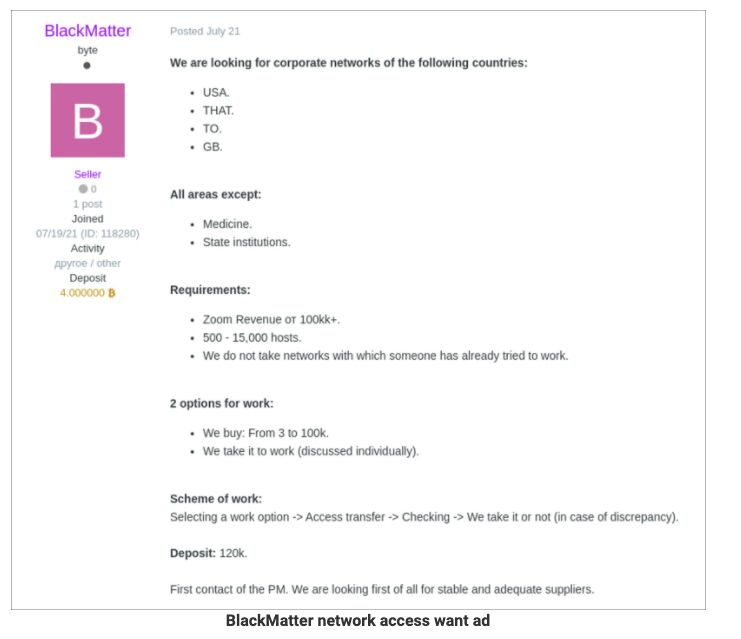
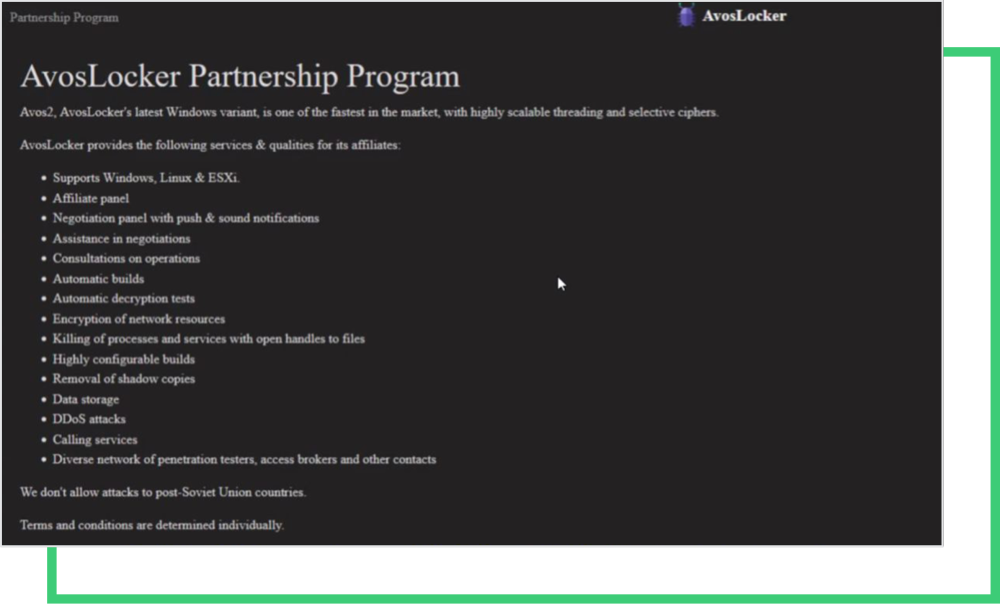
Outside of political interest, money is the largest motivator for these groups. Thus, they target wealthy countries both in the West and in the East (e.g., Japan).
The analyzed data confirms this trend. Looking at Sophos’s survey-based State of Ransomware 2022 report, our research shows similar results.
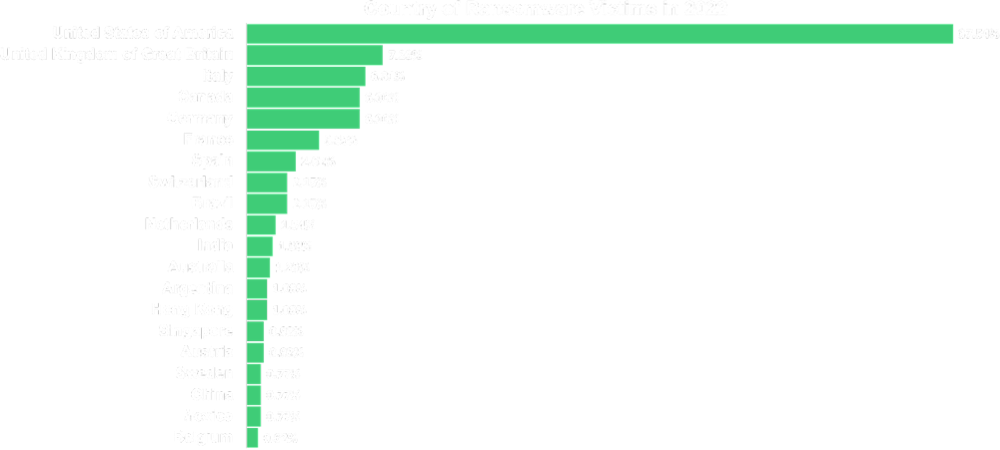
While calculating the RSI™ value for a company, Black Kite now considers its country’s targeting possibility and the nominal GDP value to better reflect the data. A company in a target country with a high GDP is more likely to become a ransomware victim than a company in a low-GDP country.
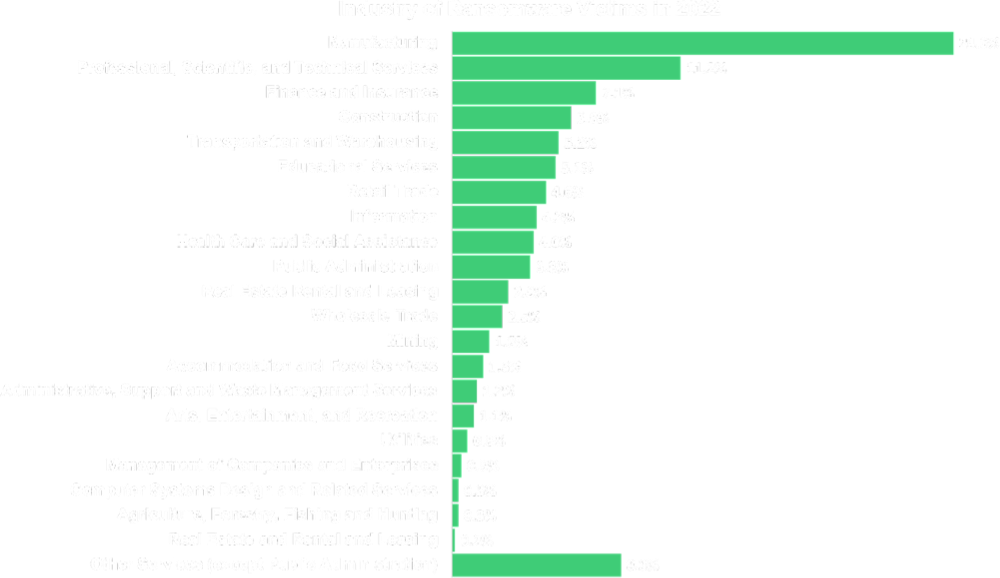
Industry-based Risk is now more thoroughly accounted for
Ransomware groups attack companies in every sector. However, depending on the group’s agenda, some industries are more appealing targets than others.
For instance, healthcare institutions were avoided during the pandemic’s peak due to ransomware groups’ so-called humanitarian reasons. But in an act against big pharma, pharmaceutical companies were still a prime target.
In 2022, we can see that threat actors have shifted their focus to manufacturing for various reasons:
- Generally low cybersecurity matureness (compared to financial institutions)
- A number of high-revenue, high-production companies
- Low tolerance for downtime, increasing the likelihood of paying the ransom to regain control more quickly
Organizational Risk is now more thoroughly accounted for
Ransomware groups target companies based on their industry, size, digital footprint, annual revenue and more. For example, mid-to-enterprise level companies are more enticing due to the increased assurance in the victim’s ability to pay the ransom.
However, larger companies often have more defensible cyber security measures, such as data backups. Ransomware groups are always searching for the easiest way into the highest yielding return – data or financial value. However, the ongoing cyber warfare is changing the opportunity for cybercriminals to effectively target larger organizations.
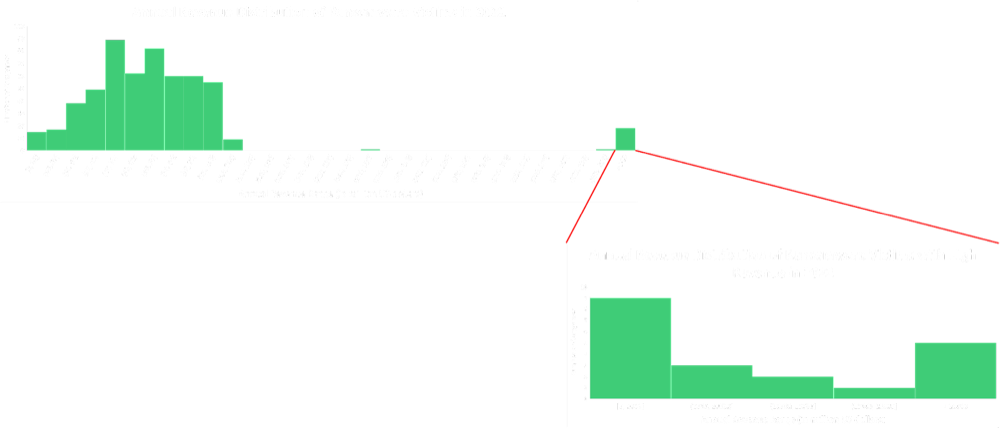
How will the RSI™ update affect the values given?
The enhancements to the RSI™ calculation includes data from each pattern identified throughout this article. Whether it is industry-related risk, or high-profile cyber events, these factors will now be reflected in the overall rating. Due to the widespread data being considered into the calculation, this update will impact many monitored companies, including an increase in RSI™ values.
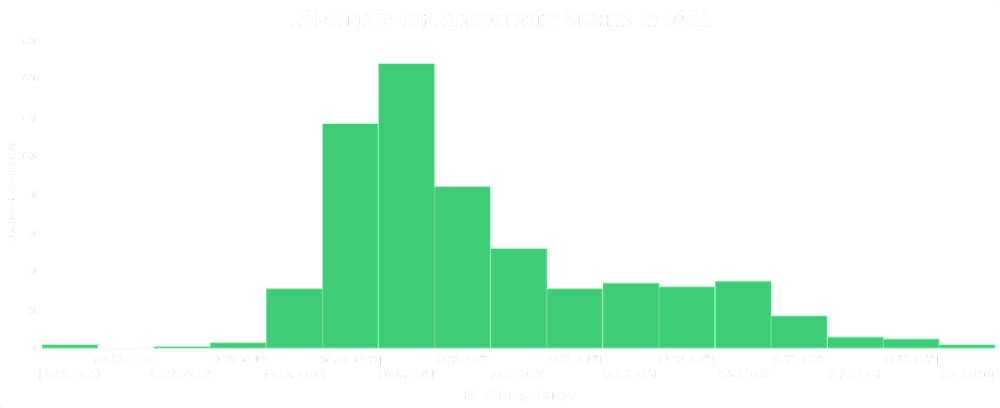
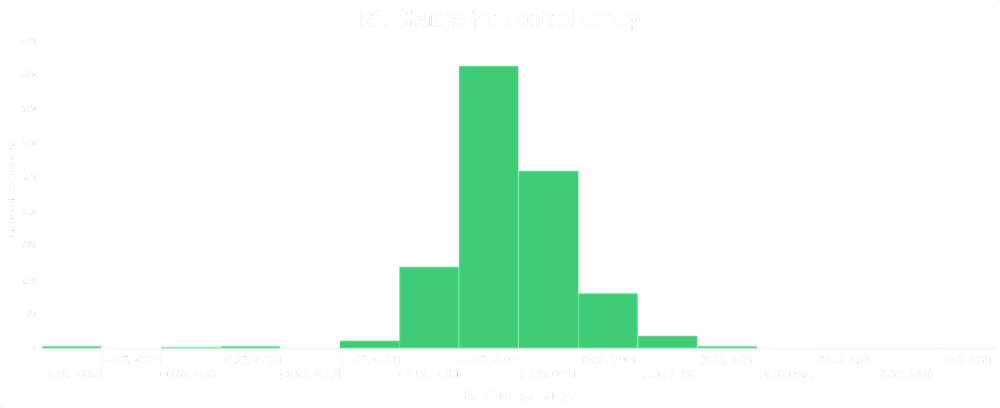
In addition to the technical indicators, the regional, organizational and industry-specific risk will improve the accuracy of ransomware attack susceptibility for organizations and vendors.
New to discovering your ransomware susceptibility? Claim a free RSI™ rating for ANY vendor in your supply chain.
Get a Free RSITM Rating