Conti Ransomware Gang Takes Sides in Ongoing Cyberwar
Written by: ceren
Written by Gokcen Tapkan
Edited by Haley Williams
As tensions escalate between Russia and Ukraine, cyber gangs are taking a stand. At the beginning of the conflict, the notorious ransomware group, Conti, posted their explicit support for the Russian president on their dedicated site. As of February 28th, CISA published an advisory indicating that Conti ransomware attacks against U.S. organizations have risen to 1,000 incidents. Some notable attack vectors utilized in Conti attacks are the exploitation of Trickbot and Cobalt Strike, remote administration ports, and unpatched vulnerabilities.
The Methodology
A sample set of 20,000 U.S. organizations were randomly selected. All companies are already continuously monitored on the Black Kite platform. Each entity includes the following information:
- Cyber Rating (Letter Grade A-F, with a +/- scale)
- RSI™ (Ransomware Susceptibility Index®)
- Rating for 20 Technical Categories
- Industry Information
Key Findings in this Research
- 791 of the organizations have critical ransomware levels on the Black Kite platform, indicating a high level of ransomware susceptibility
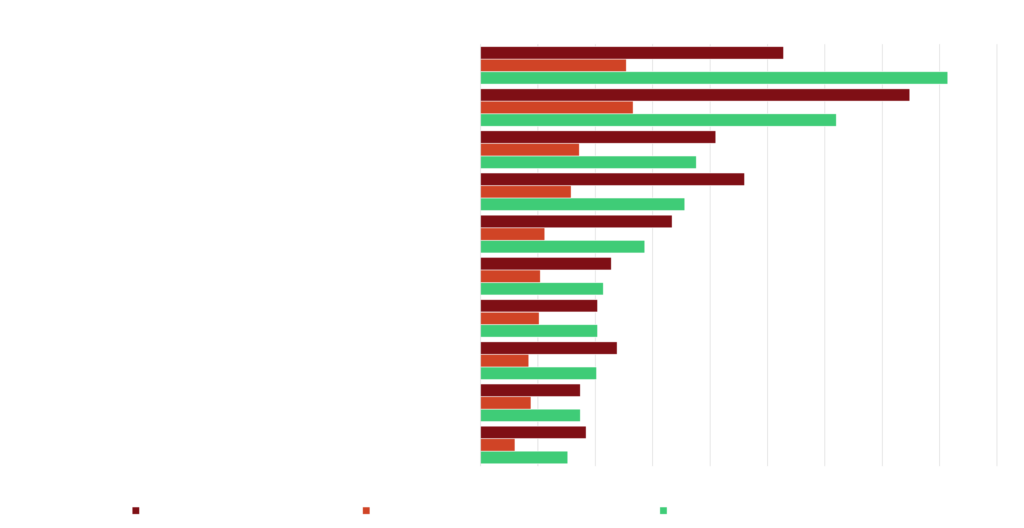
- Those with heightened susceptibility to ransomware also have bad ratings in Patch Management. Approximately 90% of these companies have C and lower grades in Patch Management. For Email Security, this ratio decreases to 33.6%, and for Credential Management, to 32%.
- Public Administration, Technology Companies, Healthcare and Manufacturing rank in the top 10 industries most susceptible to ransomware.
- 93% of the companies have at least one vulnerability that Conti uses as a TTP.
- 73 % of the companies are vulnerable to a phishing attack that Conti leverages in initial access.
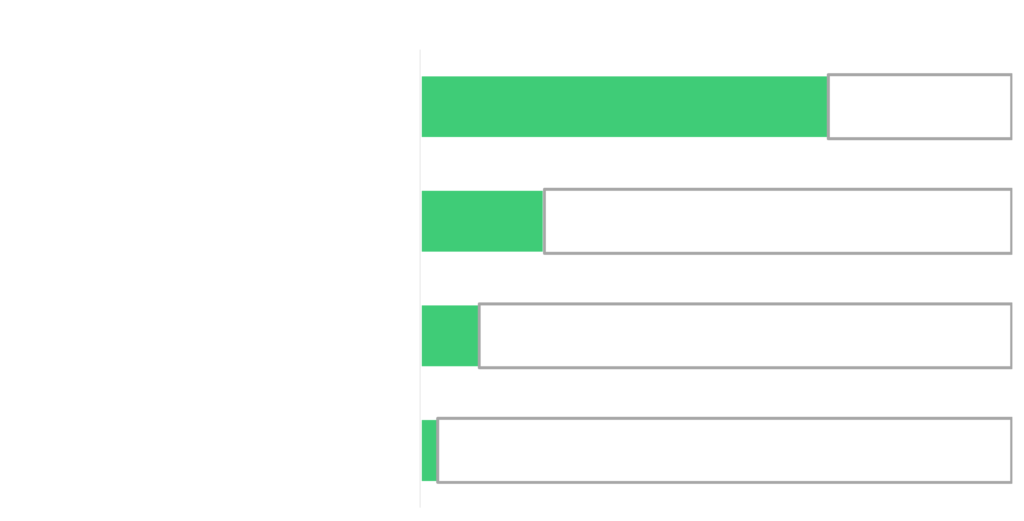
- 64% of the companies had previous breaches, a high-risk indicator of a possible future breach.
- 30% of companies have vulnerable remote administration ports, leveraged often by Conti.
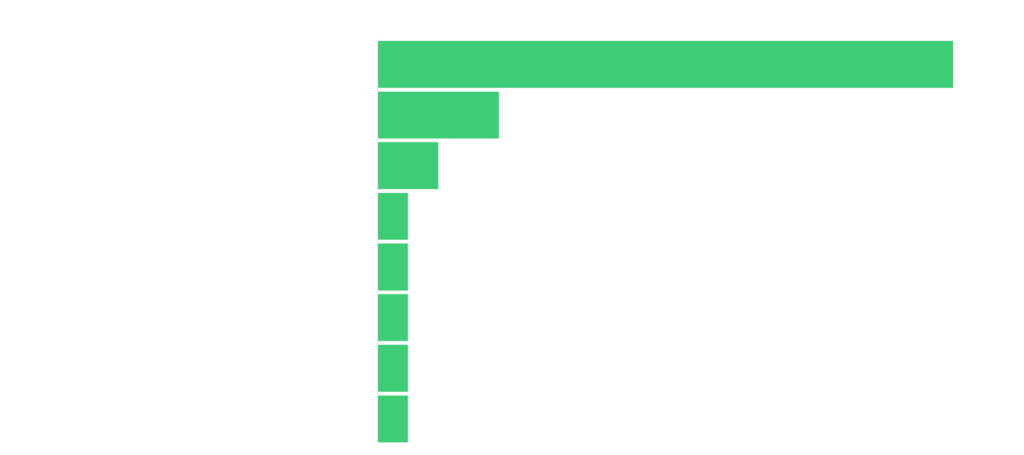
- Among the unpatched vulnerabilities that Conti often exploits, Zerologon is the most commonly occurring issue spanning 69% of all the vulnerable organizations.
CONTI Gang Recap
Making a considerable reputation quickly, Conti is perhaps one of the most ruthless and greediest ransomware groups of all time, with its ransomware demands surging as high as $25 million. Its 2021 revenue reached as high as $180 million. The well-known gang certainly hasn’t discriminated against its 400+ targets either, as attacks linked to the group are connected to hospitals, government organizations, and law enforcement agencies. Check out our detailed report on Conti’s playbook.
CONTI Chats Leaked
Conti publicly supported Russia’s invasion of Ukraine, costing the gang leakage of the internal chats. The leaks are associated with several aggressive affiliates supporting Ukraine indicating:
- Conti has close ties to the TrickBot and Emotet malware gangs, from which they frequently rented access to infected systems to spread their software.
- There have been ransom talks and payments from businesses that had not previously declared a data breach or ransomware event.
- The possibility that law enforcement might utilize the Bitcoin addresses where the Conti gang received money to trace down the gang’s gains.
- Demonstrations were arranged with security companies, such as CarbonBlack and Sophos, to test their technologies and find ways to escape detection.
CONTI Susceptibility
Black Kite Research compiled a list of CONTI TTPs and IoC in this research article. Based on this article and CISA’s recent advisory, Black Kite has derived the following susceptibility to an attack by Conti for U.S organizations.
Ransomware Susceptibility
Black Kite is the only cyber ratings solution with a tool to detect ransomware susceptibility in advance of an attack. The patented Ransomware Susceptibility Index® (RSI™) evaluates data from various open-source intelligence (ONIST) sources and machine learning to correlate 26 control items and provide an estimated ransomware rating. Black Kite’s RSI™ ratings range on a scale of 0.0 (less susceptible) to 1.0 (more susceptible), with a critical threshold of 0.6 that indicates high susceptibility.
Among our sample set, 791 companies were found to have critical RSI™ levels, indicating a heightened level of ransomware susceptibility.
An industry deep-dive reveals that the Public Administration, Technology (Professional, Scientific, and Technical Services), Healthcare, and Manufacturing are currently the most vulnerable industries to ransomware.
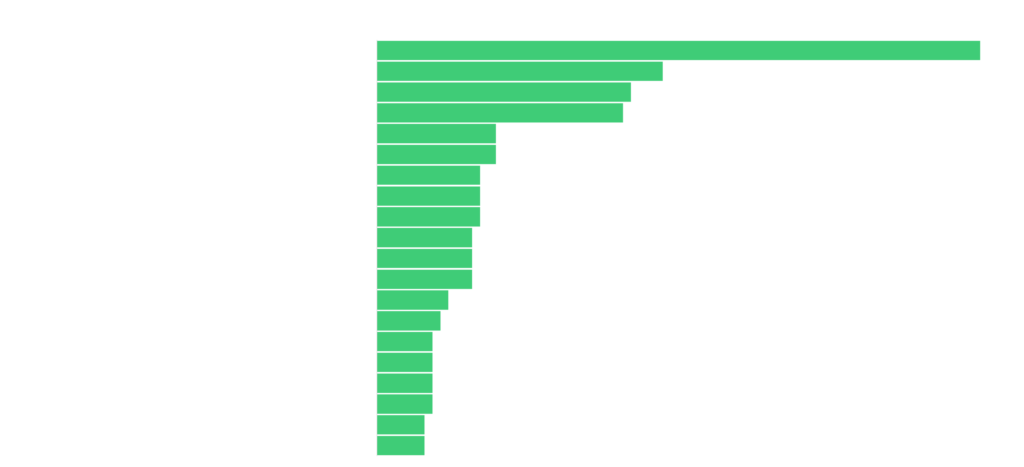
Category Grades
Patching, Credential Management, and Email Security are common indicators of ransomware susceptibility. 90% of the companies have C or lower grades in Patch Management. For Email Security, this ratio decreases to 33.6%, and for credential management, to 32%.
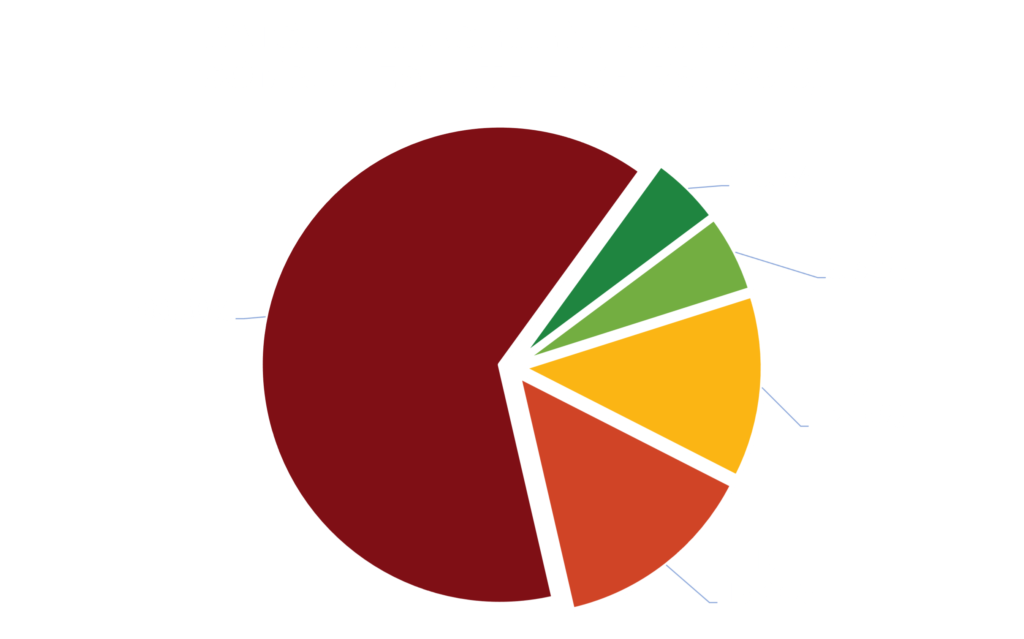
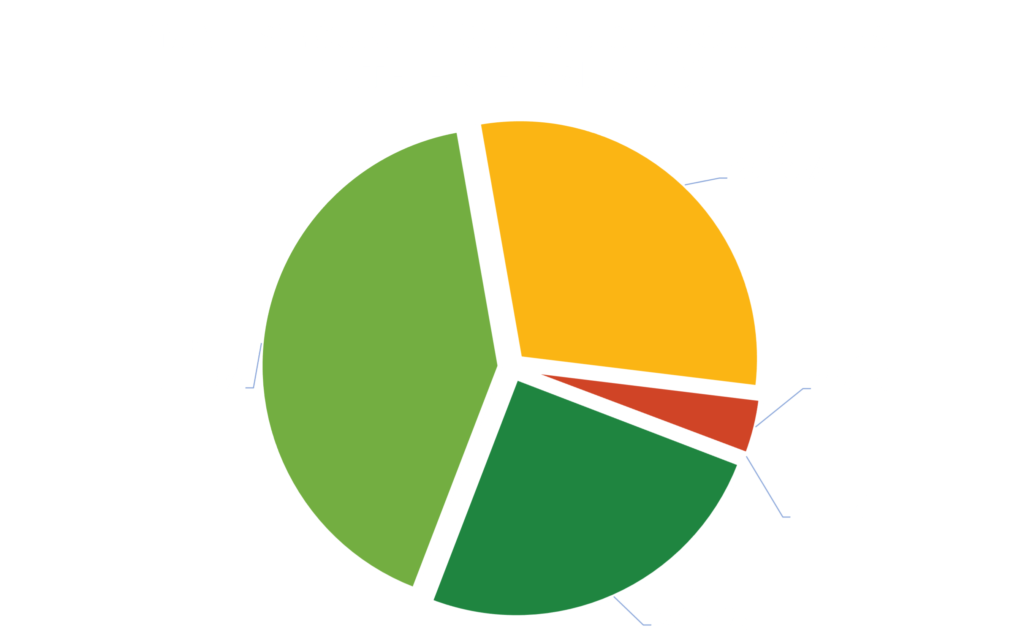
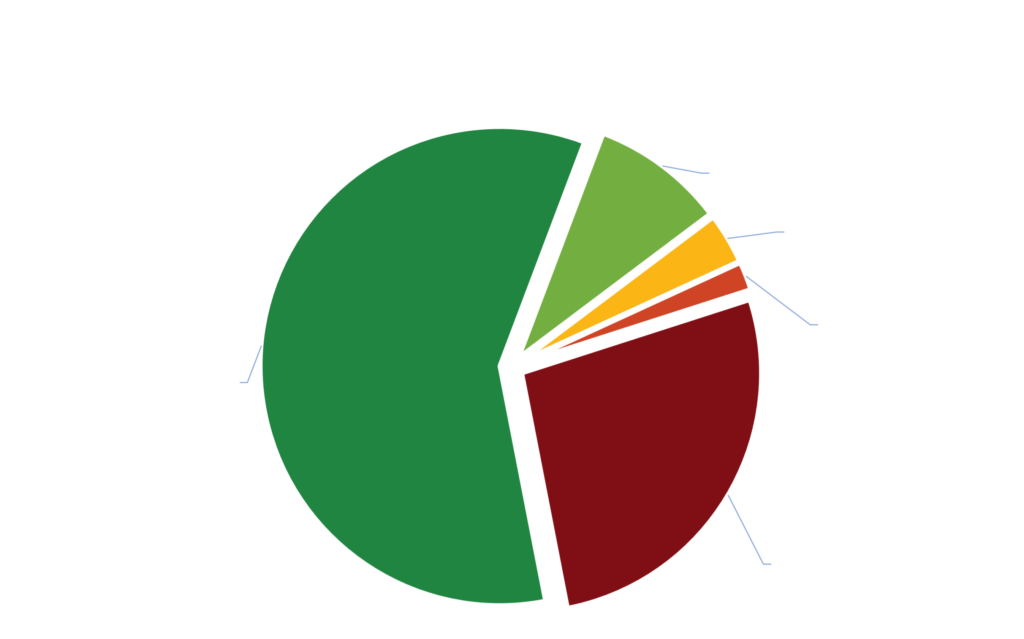
A Deep Dive into Conti TTPs
CISA lists every TTP Conti gains initial access through. Some are as follows:
- Spear Phishing campaigns that contain malicious attachments [T1566.001] or malicious links [T1566.002];
- Stolen or weak Remote Desktop Protocol (RDP) credentials [T1078].[4]
- Phone calls
- Fake software promoted via search engine optimization
- Other malware distribution networks (e.g., ZLoader)
- Common vulnerabilities in external assets
Black Kite Research identified which Black Kite control items correlated to the above TTPs and derived phishing, remote administration port, and previous breach vulnerabilities of the companies. An initial analysis revealed 93% of the companies in this research set have at least one vulnerability that Conti uses as a TTP.
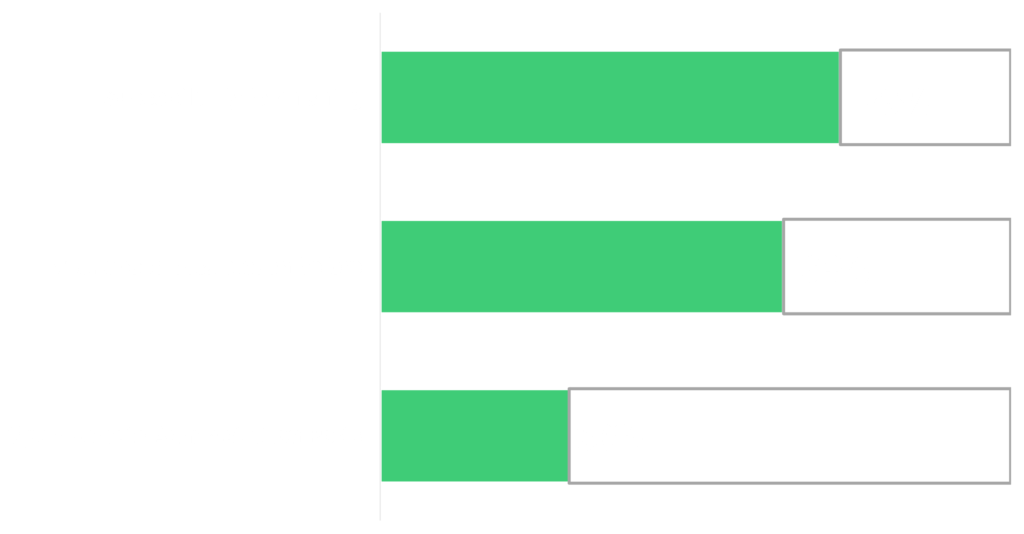
Most frequent vulnerability: Zerologon
Conti actors also exploit vulnerabilities in unpatched assets to escalate privileges, such as:
- “Zerologon” vulnerability (CVE-2020-1472) in Microsoft Active Directory Domain Controller systems
- “PrintNightmare” vulnerability (CVE-2021-34527) in Windows Print spooler service,
- Apache Log4J vulnerability, (CVE-2021-44228)
- Windows LSA spoofing CVE-2021-36942, here an unauthenticated attacker could call a method on the LSARPC interface and coerce the domain controller to authenticate against another server using NTLM
Zerologon
The Zerologon vulnerability begins with downloading a file so that a remote attacker can gain privileged credential material or become a domain admin from an unpatched Windows Domain Controller with just one click. A mimikatz addition is also referenced in the Conti playbook.
Zerologon is the most common occurring vulnerability in our sample set, spanning 69% of all the vulnerable organizations, followed by Log4J and Windows LSA spoofing vulnerabilities.
PrintNightMare
The PrintNightMare vulnerability gives an authenticated attacker a way to gain system level access on vulnerable systems, which includes core domain controllers and active directory administrative servers. The vulnerability with the CVE -2021-34527 code allows anyone to create a local administrator, as long as an agent has the initial rights of a simple user.
Best Practices for Ransomware Attacks
- Make regular external backups. External means there cannot be access from the main network. There should be an air gap between the enterprise and the backup network.
- Security awareness training is the key to combating phishing attacks, no matter how secure your email network is. Threat actors often reach employees through other channels, such as LinkedIn or text messages.
- Use reputable antivirus software and a firewall. Give refreshers on firewall rules often, and push antivirus software updates regularly.
- Patch, patch, patch. Timely patching is the key to preventing cyber attacks, including ransomware. Companies and employees that let time linger between vulnerabilities and patches allow access opportunities for threat actors. Check out CISA’s recent advisory on “Understanding and Mitigating Russian State-Sponsored Cyber Threats to U.S. Critical Infrastructure” and see which vulnerabilities they often leverage.
UNCOVER YOUR RANSOMWARE SUSCEPTIBILITY
The Ransomware Susceptibility Index® collects data from various open-source intelligence (OSINT) sources, including internet-wide scanners, hacker forums, the deep/dark web, and more to determine how susceptible a company and its third parties are to a ransomware attack.
Request a free RSI™ rating of any five vendors in your cyber ecosystem today.
Get a Free RSITM Rating
