What is Patch Management, and How Does it Impact Cyber Risk Management?
Written by: Black Kite
More than 50% of common security vulnerabilities exploited by threat actors are more than a year old. As soon as a security update is released, cybercriminals are already on the move to exploit outdated and unpatched systems and devices. Patch management is a critical step in the cyber risk management process because of its direct association with infiltration methods leveraged by threat actors.
What is Patch Management and Why is it Important?
A software patch is a piece of code specifically to fix a bug or to add new features to an application. Patch management is the process of managing a network of computers by regularly performing updates for patch deployment.
Patch management aims to implement strategies for effecting, controlling and adapting to change. It helps IT teams keep patches up to date by ensuring that they are installed properly, systems are tested after installation and all associated procedures are documented.

The Rise of Vulnerabilities Around Patch Management
Over 230,000 computers in 150 countries were attacked by the WannaCry ransomware gang who targeted unpatched systems. The attack took place 2 months after the updated patch was released. The aftermath could have remained minimal, had the victims updated their systems promptly.
Vulnerabilities within Windows, Oracle, Atlassian Confluence and Cisco are on the rise, especially as remote-working environments continue to grow as a result of the pandemic. IT teams are applying patches or work-arounds to evade any critical cyberattacks to their systems.
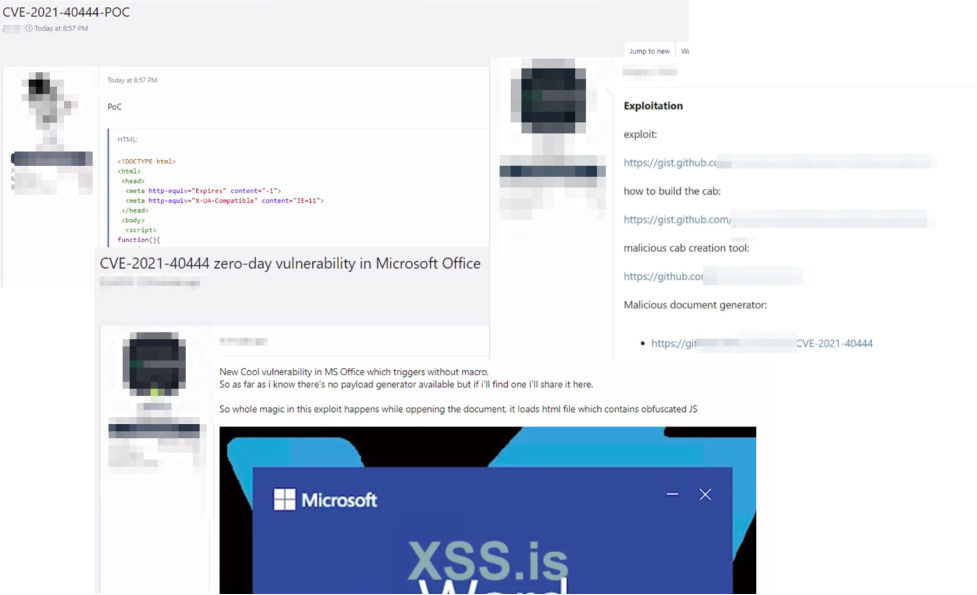
WINDOWS CVE-2021-40444 MSHTML ZERO-DAY BUG
The remote-code execution vulnerability, tracked as CVE-2021-40444, was found in the Microsoft Office Internet Explorer browser rendering engine, MSHTML. The Microsoft advisory states that the vulnerability impacts Windows 8.1 through 10 and Windows Server 2008 through 2019. The vulnerability severity level is 8.8 out of 10.0 (CVSSv3).
The Windows versions impacted by the vulnerability are widely used by supply chain networks and their employees. Threat actors can generate malicious Office and RTF documents to remotely execute commands on a target system if not patched. A remote worker who uses Windows 10, or a vendor who uses Windows 2008 R2, may fall victim to a data breach and/or a ransomware attack by simply opening a Word document.
On September 14, 2021, a week after the vulnerability surfaced, Microsoft published a fix. It’s critical for organizations and their supply chain vendors to patch this vulnerability as soon as possible to avoid a cyberattack.
The Black Kite Research Team monitored hacker forums for PoCs regarding this bug and saw that PoCs spread very quickly and several threat actors were able to replicate the PoCs to weaponize the vulnerability. Below are some of the posts from hacker forums.
ATLASSIAN CONFLUENCE RCE VULNERABILITY CVE-2021-26084
Atlassian Confluence is a web-based team collaboration platform written in Java for managing workspaces and projects that organizations can run locally on their servers. CVE-2021-26084 is a vulnerability in Confluence that allows an unauthenticated attacker to execute remote codes using the OGNL language, a simplified version of Java’s expression language. The vulnerability is classified as “critical” with a 9.8 out of 10 CVSSv3 severity score.
Atlassian released an advisory to its customers on August 25, 2021 to patch the CVE-2021-26084 vulnerability in the enterprise Wiki tool Confluence. Since then, the Black Kite research team has seen widespread searches for active exploit attempts of vulnerable Confluence servers that have not been patched.
In September, the U.S. Cyber Command, a subunit of the U.S. Department of Defense, tweeted a statement that the use of the existing CVE-2021-26084 vulnerability in Atlassian is expected to increase. US Cyber Command communicated the urgency to implement effective patch management for outdated systems and informed organizations who have not yet done so to patch immediately.
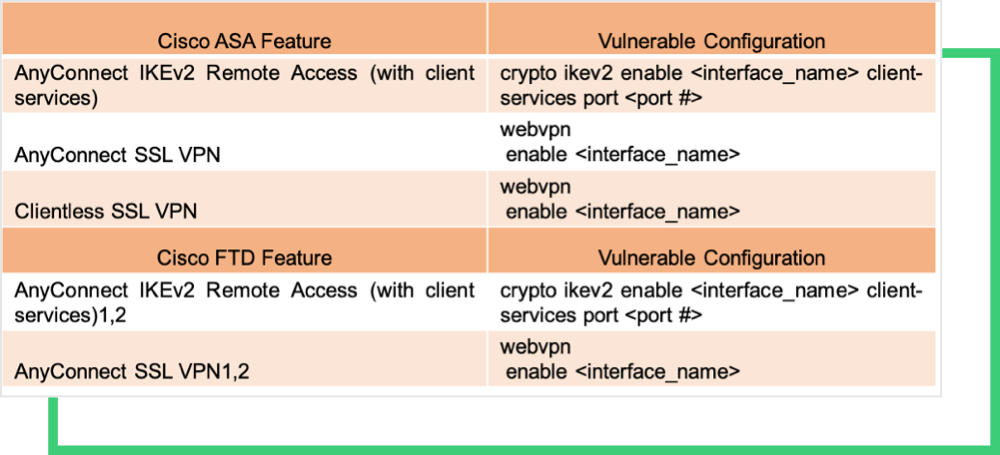
CISCO ADAPTIVE SECURITY APPLIANCE SOFTWARE AND FIREPOWER THREAT DEFENSE SOFTWARE WEB SERVICES READ-ONLY PATH TRAVERSAL
Using this vulnerability, an unauthenticated remote attacker could carry out a direct traversal attack and gain access to sensitive credentials on the targeted devices. The access is scoped to the web services file system only, and does not apply to the ASA (Adaptive Security Appliance) and FTD (Firepower Threat Defense) system files or underlying operating system (OS) files.
This vulnerability affects Cisco products running Cisco ASA Software or Cisco FTD Software with a vulnerable AnyConnect or WebVPN configuration. Below are the affected configurations of ASA and FTD software in need of patch management.The vulnerability stems from lack of proper input validation of URLs in HTTP requests processed by the affected devices.
WINDOWS DNS SERVER, CVE-2020-1350
This vulnerability applies to the “Windows DNS Server,” which is an essential part of a Windows Domain environment. Dubbed SIGRed CVE-2020-1350 is wormable (can spread between vulnerable computers through malware without user interaction), earning the highest possible score of 10.0 on the Common Vulnerability Scoring System (CVSS) severity scale.
DNS, also known as the “Internet phonebook,” is a network protocol for translating the IP addresses to human-friendly hostnames. As an integral component of the internet, there are a number of solutions and DNS server implementations, but only few are commonly used.
In this CVE, the bug stems from the utilization of a forwarded query from a DNS server. By nature, DNS is hierarchical, and decentralized. It means that when a DNS server does not know an answer to a query, it is redirected in the hierarchy to a DNS server above it.
By sending a DNS response that contains a large (bigger than 64KB) SIG record, one can cause a controlled heap-based buffer overflow of roughly 64KB. Because the service operates in an elevated privileges system, domain administrator rights are given to an intruder, thus potentially compromising credentials of the entire corporate infrastructure.
ORACLE CRITICAL UPDATES
Oracle published an array of vulnerabilities for multiple security bugs in its Critical Patch Update of 2020. The record-breaking 443 security patches addressed 284 CVEs across 29 Oracle product families. By exploiting those vulnerabilities, a remote attacker can cause the application to crash or execute arbitrary operations.
The affected products leading to cyber risk include but are not limited to CVE-2020-14701 and CVE-2020-14706, which are found in the User Interface component of an Oracle Communications Application. These were marked by Oracle as easily exploitable since they allow an attacker with network access to compromise SD-WAN Aware and SD-WAN Edge via the HTTP.
How to Implement Patch Management Procedures Across Your Digital Supply Chain
With the conglomeration of CVE codes, severities, patches, and workarounds, IT teams become overwhelmed and can miss critical updates as hundreds of cyber vulnerabilities are found each month. “Anything that you do more than twice has to be automated,” says Adam Stone, and it applies to patch management perfectly. Setting automated updates helps keep your systems up to date without the hassle of managing updates for every system you operate.
Patch management requires 4 basic steps: assessment, analysis, application, and strategy.
- Assessment: The identification of relevant vulnerabilities and updates.
- Analysis: Risky vulnerabilities are detected and analyzed. Analysis of the cyber risk assessment is evaluated to determine the full scope of the development of a remediation strategy.
- Application: Completing the determined updates from step two.
- Strategy: This strategy should provide a continuous improvement through assurance.
An effective patch management process includes a combination of automation and best practices. Manual patch management is time-consuming and aspects can be easily overlooked due to human error. Black Kite collects details related to the version number of your system and software from an internet-wide scanner to determine where patches are needed from an external view as a threat actor would see it.

The details of the report are converted into the platform and correlated with NIST and MITRE CVSS databases to detect unmitigated known vulnerabilities. Black Kite ties each vulnerability on digital assets to 3 dimensions of cyber risk using:
- Black Kite technical report where findings contribute to the overall risk rating.
- Financial impact rating where findings contribute to financial cyber risk.
- Compliance module where findings correlate to regulations, standards, and best practices. (NIST 800-53, NIST CSF, HIPPA, GDPR, PCI-DSS, etc.)
Alerts are generated to inform you about the most recent vulnerabilities (and level of severity) regarding your organization and third-party assets. Black Kite’s strategy report allows you to communicate risk with your third parties and create an action plan to fix vulnerabilities and increase their cybersecurity posture through effective patch management.
Demo our Automated Continuous Cyber Risk Monitoring tool to gain a better understanding of how we can help improve your cyber ecosystem through third-party risk management.
Additional Resources
- Patch now: Windows CVE-2021-40444 MSHTML Zero-Day Bug
- Patch now: Atlassian Confluence RCE Vulnerability CVE-2021-26084
- See how our platform works: Black Kite Automated Continuous Cyber Risk Monitoring
- Learn: How to Mature your Third-Party Risk Management
- Read: The Secret to Ransomware Risk Management

