Four Ways Automation Can Transform Your Third-Party Cyber Risk Management Strategy
Written by: Black Kite
Supply chains are growing at an annual rate of 11.2% and are forecasted to double in size by 2026. Growing supply chains inherently pose greater supply chain risk and require a scalable approach to vendor risk management. Cyber risk monitoring solutions not only identify 40% more threats than conventional security, they offer a handful of other benefits.
1. Automation reduces human error and helps bridge the cybersecurity skills gap
Human error accounts for over 90% of cyber breaches. It only takes one mistake to leave a lasting impact– both financially and operationally. Automated cyber risk solutions eliminate the possibility of human mistakes, taking a lot of weight off employees’ shoulders and enabling standardization, consistency, and speed during third-party risk management.
Seventy-six percent of IT executives agree automation maximizes the efficiency of their security staff. Today, there are over 465,000 unfilled cyber positions across the U.S. alone. Cyber risk automation prioritizes vulnerabilities based on the criticality of a vendor so that your third-party risk management resources are allocated accordingly. In turn, employees are able to focus on value-added tasks.
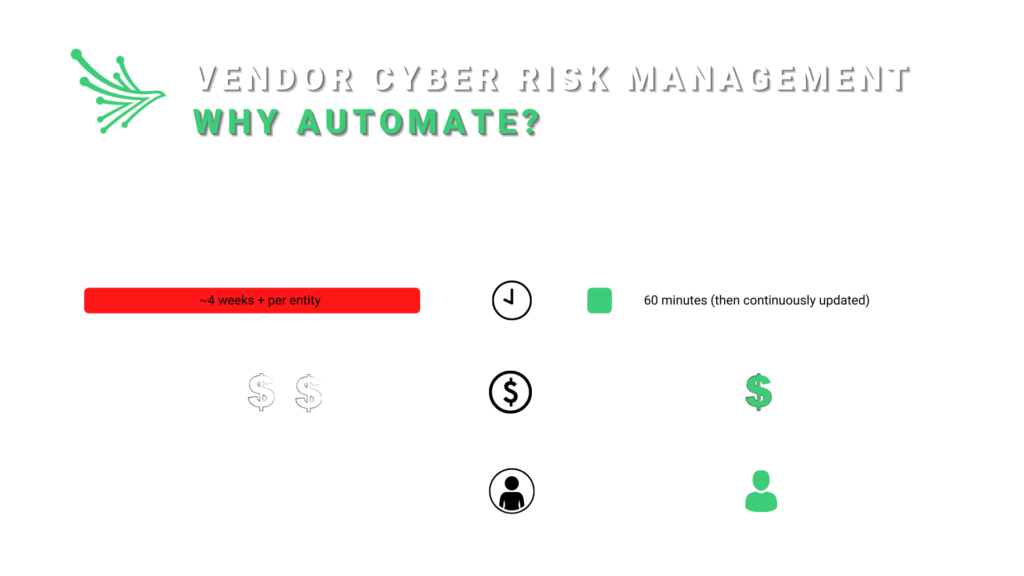
2. Automated compliance audits save time and money
Eighty-two percent of companies give third parties access to their cloud data, demonstrating the need for compliance audits outside the organization. Compliance questionnaires can range anywhere from 20 to 200 pages and take up to months to complete. Automated vendor risk assessments reduce the time it takes to complete and can also lower operational costs by 80%.
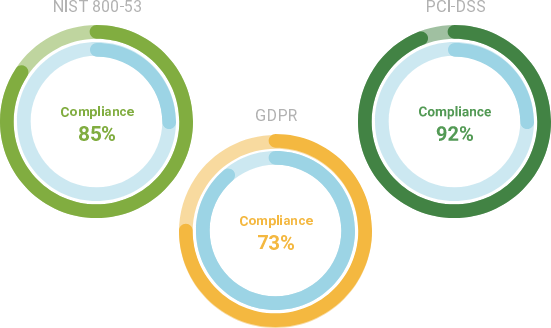
3. Automated risk assessments translate technical findings into comprehensive action plans
Generating data for your third-party risk program is one thing. Understanding what to do with it is another. Oftentimes, vendor risk assessment analyses require highly skilled compliance and risk professionals. Automated risk reports translate technical jargon into easy-to-understand business terms that can be communicated both internally and with vendors.
Through this approach, organizations can identify an effective course of action to prioritize and address vulnerabilities based on their criticality. This process eliminates weeks of tedious manpower, and also provides an unbiased snapshot of your ecosystem’s cyber posture.
4. Automation can identify vulnerabilities that may lead to a cyberattack
Sophisticated risk ratings are designed to continuously scan networks across a cyber ecosystem to identify vulnerabilities the instant they are detected. Security and compliance teams can leverage data gathered from a variety of OSINT resources to understand an organization’s susceptibility to a cyberattack.
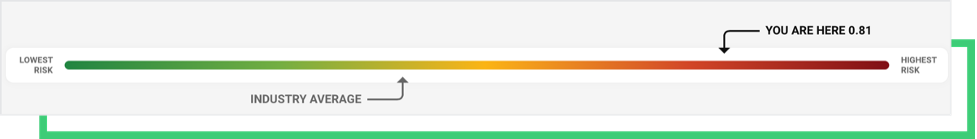
Take, for example, the recent incident involving Memorial Health, which led to canceled surgeries and diverted patients. Any organization with a Ransomware Susceptibility Index™ rating above 0.6 is considered highly likely to become a ransomware victim, and Memorial Health was at a 0.81.
Want to understand your ransomware risk exposure?
Request a Free RSICybercriminals are actively applying automated tools to infiltrate vulnerable companies that are using manual security, simply because automated technology works faster and smarter than any person can. Fight fire with fire with automated cybersecurity tools that better equip your supply chain.
See how Black Kite’s cyber ratings can transform your third-party risk management program.
Request a Demo