Atlassian Confluence RCE Vulnerability May Create the Next Third-Party Data Breach Wave
Written by: ceren
Written by Ferhat Dikbiyik
Additional Contributor Yavuz Han
Edited by Haley Williams
Atlassian released an advisory to its customers on August 25, 2021 to fix the CVE-2021-26084 vulnerability in the enterprise Wiki tool Confluence. Since then, we have seen widespread searches for active exploit attempts for vulnerable Confluence servers.
What is the CVE-2021-26084 Vulnerability?
Atlassian Confluence is a web-based team collaboration platform written in Java for managing workspaces and projects that organizations can run locally on their servers. CVE-2021-26084 is a vulnerability in Confluence that is widely distributed. It allows an unauthenticated attacker to execute remote code using the OGNL language, a simplified version of Java’s expression language. The vulnerability is classified as “critical” with a 9.8 (out of 10) CVSSv3 severity score.
Because Confluence is used globally by software developers and teams, and that attackers can execute codes remotely, threat actors and security researchers have already published multiple proof-of-concepts (PoCs) on how to exploit the vulnerability. Hackers are using open-source intelligence (OSINT) tools to find vulnerable Confluence products, sharing their findings with the hacker community on underground forums.
The Black Kite Research Team has obtained posts from these hacker forums and discovered that approximately 600 URLs of potentially vulnerable Confluence servers have been shared.
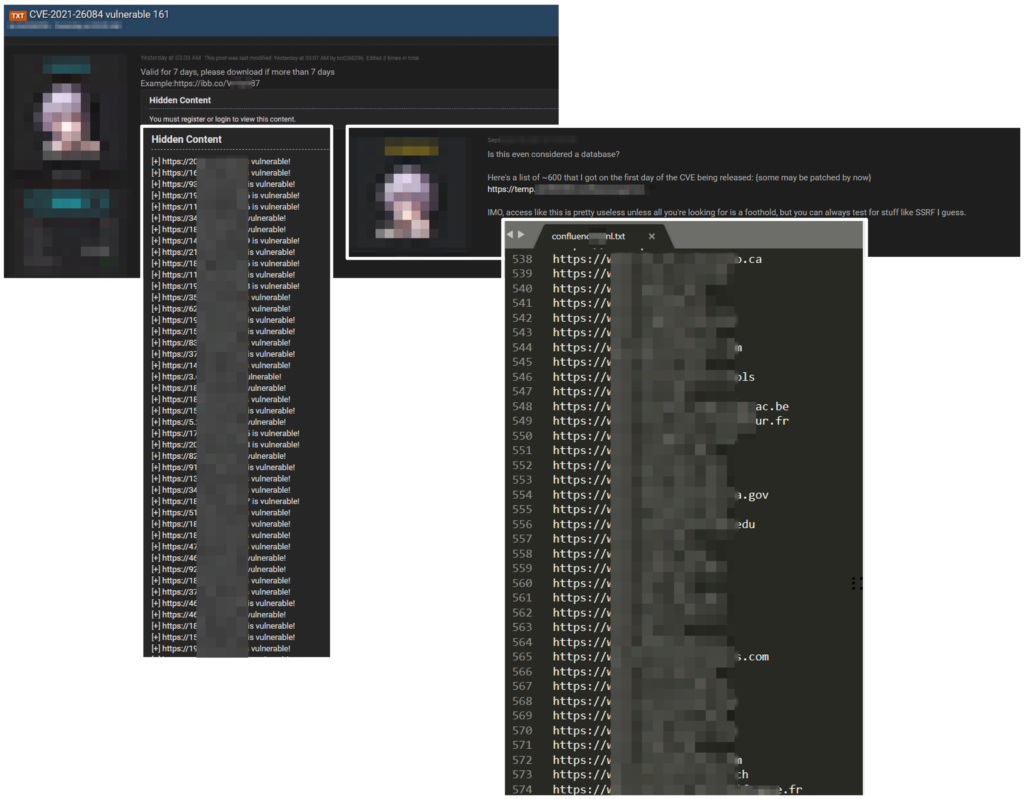
How it attacks
On August 31, GitHub published a technical write up and PoC describing the CVE-2021-26084 Vulnerability. The PoC shows a successful remote code execution that exploits the vulnerability. Hackers can execute malicious codes inside Confluence servers to get sensitive information stored in the servers, obtain credentials of users of other company systems, or simply mine crypto coins.
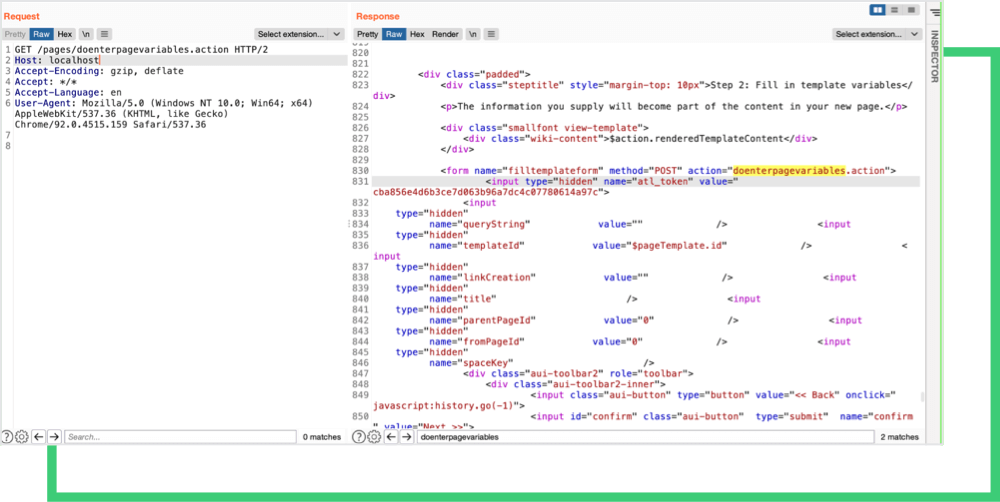
Since Confluence servers are mainly used by software developers, a threat actor may find a way to inject malicious code through a company’s source code or JavaScript code. Organizations that then use the infected product of this third-party provider may inadvertently leak sensitive information to threat actors. An example of a threat actor creating this kind of third-party breach is the Magecart group. This cybercrime syndicate injected card skimming codes to different JavaScripts used by large organizations such as Newegg and British Airways. These Magecart attacks exposed large numbers of credit card information and caused companies to pay millions of dollars in fines.
How many servers are at risk?
According to Atlassian’s official description, versions impacted by CVE-2021-26084 in Confluence Server and Confluence Data Center are:
— All versions prior to 6.13.23 — With the previous version from version 7.4.11 to 6.14.0 — Previous versions from version 7.11.6 to 7.5.0 — Previous versions from version 7.12.5 to 7.12.0
-
- All 6.14.x versions
- All 6.15.x versions
- All 7.0.x versions
- All 7.1.x versions
- All 7.2.x versions
- All 7.3.x versions
- All 7.4.x versions before 7.4.11
- All 7.5.x versions
- All 7.6.x versions
- All 7.7.x versions
- All 7.8.x versions
- All 7.9.x versions
- All 7.10.x versions
- All 7.11.x versions before 7.11.6
- All 7.12.x versions before 7.12.5
Atlassian released versions 6.13.23, 7.4.11, 7.11.6, 7.12.5, and 7.13.0 to fix the bug and recommends upgrading to the latest version in the 7.13.x branch to take advantage of long-term support. For organizations that can’t immediately upgrade Confluence, Atlassian recommends that they download and run Windows and Linux scripts published by Atlassian as a temporary solution. It should be noted that Confluence Cloud customers are not affected by this vulnerability.
On September 1, 2021 Censys identified 14,701 services that self-identified as a Confluence server. Of these, 13,596 ports and 12,876 individual IPv4 hosts are running an exploitable version of the software. After the advisory and notifications, organizations started to update their Confluence servers and the number of vulnerable servers dropped to 8,500 servers by September 5.
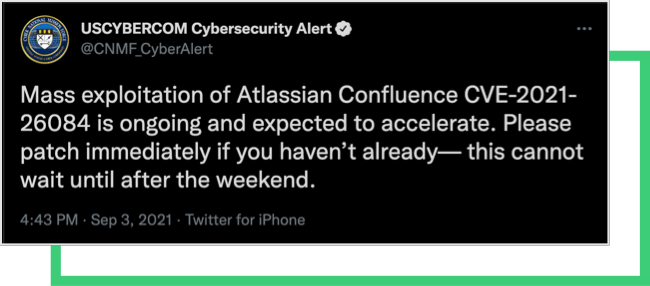
US Cyber Command: Mass exploitation of Atlassian Confluence CVE-2021-26084 is ongoing and expected to accelerate
In a September 3 tweet, US Cyber Command, a sub-unit of the US Department of Defense, stated that the use of the existing CVE-2021-26084 vulnerability in Atlassian is expected to increase. US Cyber Command underscored the urgency to implement patches and that those organizations who have not yet done so must patch immediately. The cybersecurity entity also warned that threat actors may be preparing for a larger campaign against the private sector.
Some servers have already been hacked
On September 4, the Jenkins project blog announced the exploitation of the CVE-2021-26084 vulnerability to install an open-source, cross-platform XMRig Monero cryptocurrency miner. Jenkins stated that at this time, “[they] have no reason to believe that any Jenkins releases, plugins, or source code have been affected.”
While Jenkins, a popular open-source server for automating parts of software development, fell victim to one of these attacks, the attackers may leverage this RCE vulnerability for more dangerous attacks. The recent cyber attacks against SolarWinds, Accellion, and Kaseya show that vulnerabilities on widely used software may cause data breaches for multiple organizations. If not updated immediately, vulnerable Confluence servers may create similar situations.
How can these be avoided?
With breaches continuing to highlight how critical supply chain security is to business operations, it’s becoming a must-have to understand the cyber risk susceptibility of both your organization and those that provide you with third-party software. The best offense is a strong line of defense. Get started today with a free cyber risk rating.

