What You Need to Know About Maturing Your Third-Party Risk Management Program
Written by: Black Kite
Mismanaged or unmanaged vendor risks have an adverse impact on a company’s bottom line. Still, most third-party risk management programs aren’t as mature as we’d anticipate given the interconnectedness of today’s digital ecosystems. If mitigated, Third-party cyber incidents weigh astronomically on a company’s finances and reputation.
Cybercriminals constantly update their approach and create new malware based on existing security measures to infiltrate networks. As with anything pertaining to cybersecurity, third-party risk management (TPRM) isn’t something you can “set and forget”. Supply chains must join forces and evolve their TPRM programs to combat the uptick in threat complexity.
Growing Supply Chains Demand More from Today’s Cyber Risk Management Programs
Legal and compliance professionals have identified a 2.5x increase in high-risk third parties over the past four years alone. As companies ramp up the number of organizations in their supply chains, existing and emerging privacy regulations such as GDPR and Canada’s Digital Charter Implementation Act are implementing greater third-party risk monitoring expectations from organizations.
Cyber risk management tools have evolved from a simple letter grade to a conglomerate of information. The increase of components provides a highly accurate view of risk. Therefore, those who are still functioning on legacy risk management systems may not have a holistic view of the critical risks within their supply chain.

How to Take Vendor Due Diligence to the Next Level
Fifty-nine percent of companies are not actively monitoring third-party risks during each stage of the vendor lifecycle. Initial due diligence when onboarding a new vendor is important, but taking it to the next level with constant cyber risk monitoring is what will keep organizations from becoming the next data breach victim.
For example, if a vendor was assessed pre-COVID-19, their security posture has the potential to be drastically different than originally assessed. Cyber risk monitoring is a critical part of the maturity process at all stages, especially when it comes to those organizations with access to sensitive data.
Although the amount of resources required will vary depending on the size of your cyber ecosystem, developing an asset-focused mindset to create your roadmap for vendor risk assessments (VRAs) will prioritize specific aspects of risk to simplify the process. To simplify VRAs, teams should focus on the following steps:
- Start with domain specifics and analyze the vendor
- Identify the goal of the vendor security assessment
- Determine the methodology
- Allocate the appropriate resources
- Minimize disruption
If notified of a vendor vulnerability, action can be taken to reassess and update them within your third-party risk report. This can also reduce assessment costs because the process will be scaled and only completed when necessary.
The Role of Compliance in Third-Party Risk
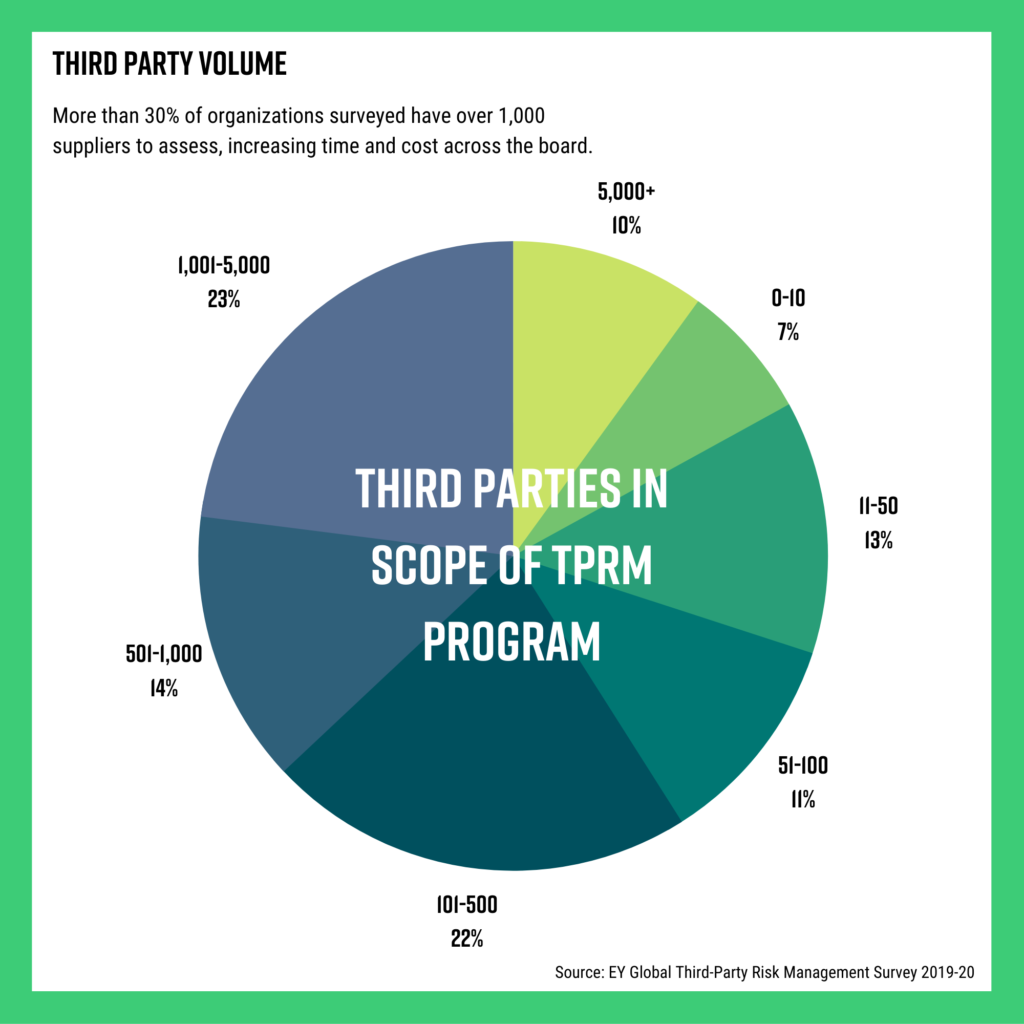
Forty-two percent of companies are using spreadsheet-based questionnaires to review compliance standards among their third parties, and most (65%) are unsatisfied with the process they have in place. Maturing your third-party risk management program with new systems and processes can alleviate stress among your team, especially with more than 30% of organizations having 1,000+ suppliers.
Consider an automated approach to analyzing compliance questionnaires. Automation greatly reduces the amount of time spent reading and analyzing questionnaires and produces accurate standards-based results. Sophisticated cyber risk monitoring solutions, such as those offered by Black Kite, can streamline TPRM program maturity.
Three ways Black Kite can help mature your third-party risk management:
1. Findings Filter:
The findings filter will help narrow the scope of cyber vulnerabilities by prioritizing severity based on specific vendors that may put you more at risk for a third-party breach.
2. Strategy Report:
The strategy report outlines the most effective strategy for attack remediation. It analyses each component of a cyber rating to put the data into comprehensible context. The report is downloadable and easy to share across a company and with vendors. The strategy report is a great resource to determine the next steps in your cyber risk management process.
3. Workflow engine:
The workflow engine automates alerts to specific findings from the Black Kite platform. Workflows are customizable to the triggers and conditions you want to be notified of. The automated workflow scales how your team manages cyber risk because there is no need to enter the platform on a daily basis with notifications set for critical vulnerabilities.
Request a Demo: To understand how Black Kite can help scale your TPRM program.
Additional Resources
- Read: Four Ways Automation can Transform your Third-Party Cyber Risk Management Strategy
- Learn: How Outdated Servers led to Vulnerable Atlassian-Confluence Customers
- Watch: How Black Kite Compares to Competitors

