Why Supply Chain Risk Assessments are Critical to Cybersecurity
Written by: Black Kite
The average cost of a third-party data breach is $4.33 million. The year-over-year increase is directly correlated with growing supply chains and more third-party vendors being utilized in business processes.
A successful supply chain risk management strategy is just as important as internal risk programs as supply chains grow and expand attack surfaces.
Why are Cyber Criminals Targeting Supply Chains?
Cybercriminals recognize the opportunity they have to target organizations with poor cyber posture to make their way into larger, more secure companies that hold confidential data and are willing to pay higher ransoms.
Digital systems become more interdependent with each year, creating a jungle gym for cybercriminals to crawl through connected systems. Threat actors often have the advantage of knowing where a company’s vulnerabilities are before the connected supply chain vendor, which lets them sneak into digital assets.
Continuous supply chain risk assessments alert teams when vulnerabilities are detected to mitigate potential access points before a cybercriminal has the chance to. Critical vendors of a company that have access to sensitive data are often the most sought after by cybercriminals.
How Ransomware Can Put Entire Supply Chains at a Standstill
The Colonial Pipeline company was breached in May 2021 causing major fuel transfers to be disabled. Colonial Pipeline is responsible for distributing nearly half of all oil-related fuels on the East Coast of America, resulting in major supply chain disruptions.
In addition to halted business operations, over 6,000 personally identifiable information (PII) records of individuals were compromised including names, contact information, social security numbers and health insurance information.
The repercussions of ransomware do not simply end when the ransom is paid, the supply chains continue to suffer until all business processes are restored. Colonial pipeline lost over $3 million in ransom payment and their supply chain was not fully recovered for several weeks.
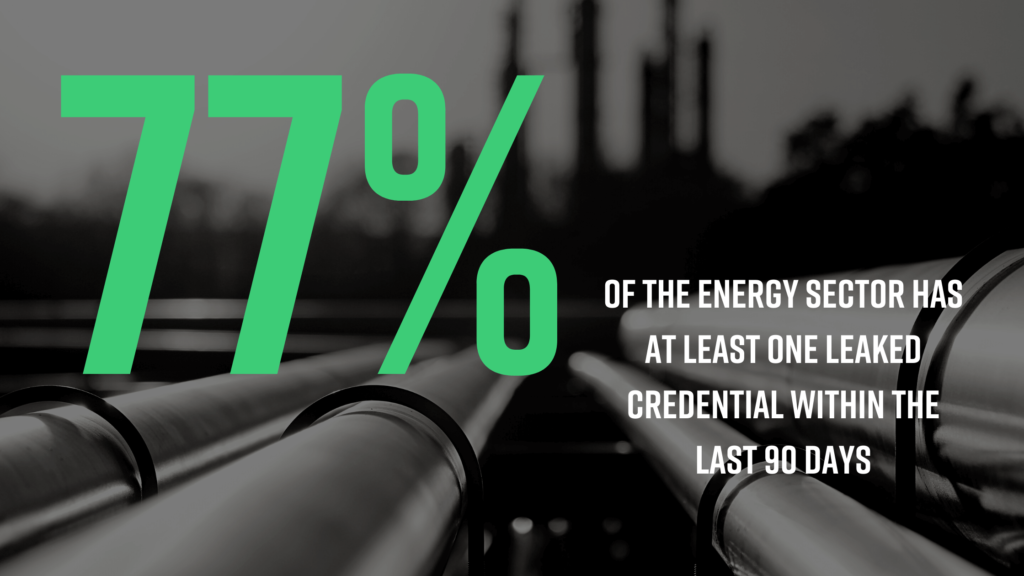
The attack on Colonial Pipeline resulted from poor credential management as the cybercriminals infiltrated the system using a compromised username and password. Black Kite research found that 77% of energy companies have had at least one compromised credential in the last 90 days.
A thorough risk assessment process will show which vendors associated with an organization have compromised credentials, as well as details of the specific credential. Enabling multi-factor authentication (MFA) for employees across a workforce makes it extremely difficult for threat actors to breach accounts with a single password.
Best practices such as using strong passwords and MFA will strengthen credential management by adding an extra layer of security that threat actors may not be able to go through.
Once compromised credentials are found among a supply chain, they can be communicated with the vendor and properly fixed. The process of monitoring supply chain risk strengthens the global cyber ecosystem through a process of reliable data and clear communication.
The Supply Chain Risk Assessment Lifecycle
1. Source and vet vendors, suppliers and partners.
It is important to evaluate each vendor prior to sharing company data with them. Constructing a due diligence report creates a view into the controls and measures they have in place for defending against and responding to cyberattacks. Continuous monitoring from then on keeps organizations up to date with changes to their supply chain risk.
2. Prioritize and allocate necessary resources to critical threats across the supply chain.
Cybercriminals determine the value of a company based on the amount of sensitive information that is stored across its network. All vendors within a supply chain hold a different level of risk. For example, an office supply vendor will hold much less third-party risk than a payroll vendor because of the difference in the amount of information being shared.
3. Raise cybersecurity standards across your digital supply chain.
Assessing vendors based on their level of risk allows an organization to scale its approach by focusing resources on the areas of a supply chain that need it the most. The power of automation simplifies continuous cyber risk assessments throughout the duration of a business relationship by assessing individual risk for the user.
Another way to scale third-party risk management is to use a standard questionnaire when onboarding vendors. This removes the hassle of creating a custom questionnaire for each vendor and analyzing new information with each case. Check out Black Kite’s compliance correlation to combine the ease of automation with how compliance questionnaires are evaluated.
Combining efforts and utilizing digital resources will provide organizations with the most accurate data for assessing risk. Industrial grade technology is fueling supply chains and expanding markets for global reach. With immense growth comes heightened risk, making supply chain risk assessments even more important for vendors that have access to critical information.

