The Critical Infrastructure for Food Supply Chain Hit by Ransomware Attack
Written by: ceren
Written by Ferhat Dikbiyik
Edited by Haley Williams
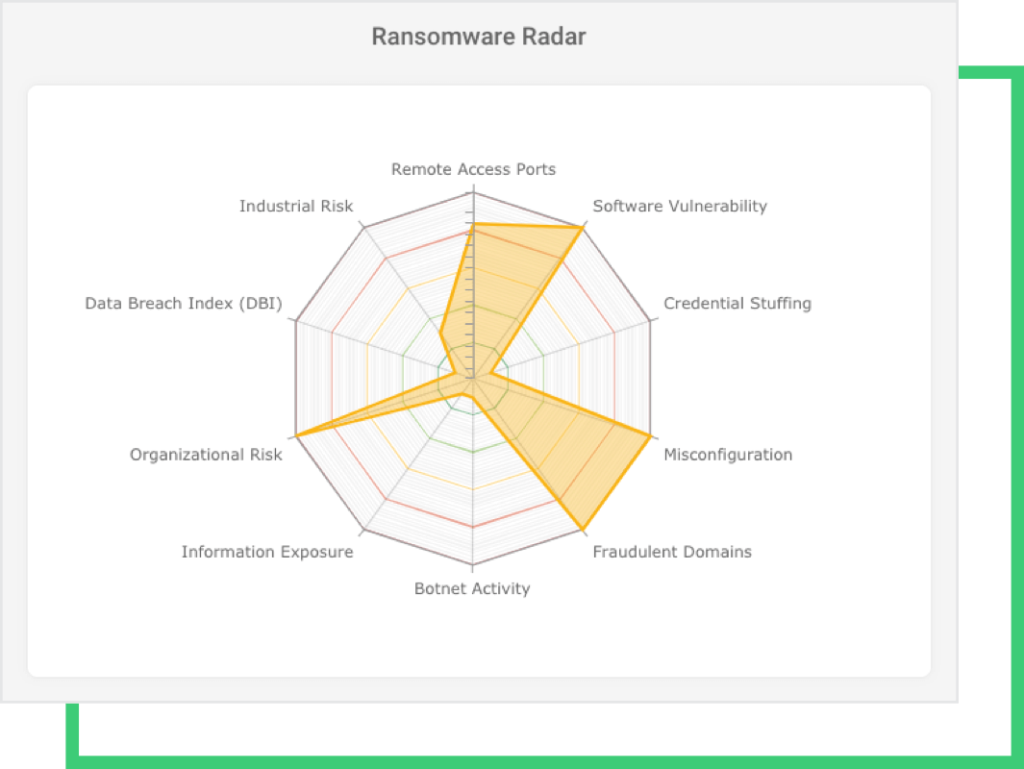
This past weekend, NEW Cooperative, a US farmers’ feed and grain cooperative in Iowa, was hit by a ransomware attack executed by the BlackMatter group. After the attack surfaced on the deep web and hacker chatters, Black Kite Research analyzed NEW Cooperative’s cybersecurity posture. The analysis found that the organization was 29% more susceptible to ransomware than the industry average, as shown by the ransomware indicators below.
What happened
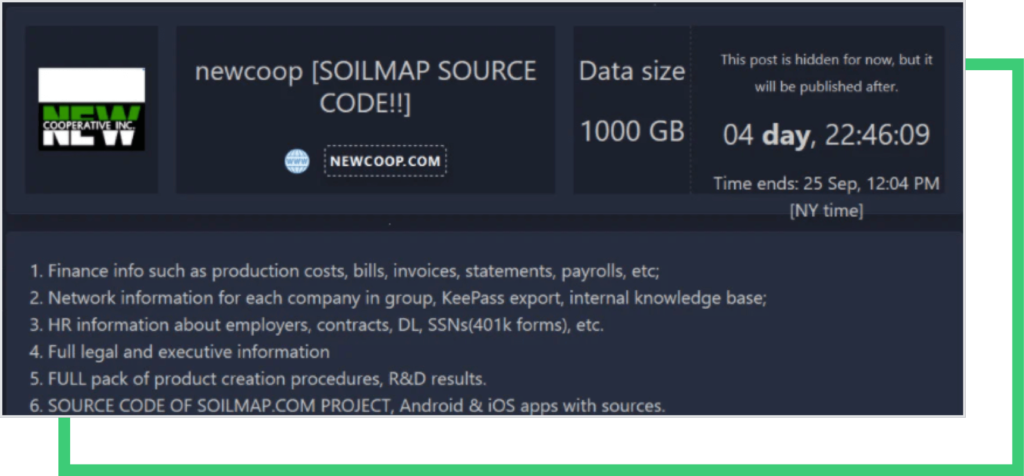
The BlackMatter ransomware group posts victim information to its blog as a threat to leak stolen data and not provide a decryptor. NEW Cooperative’s name appeared in this blog last week, with a countdown that ends on September 25 at 12:04 PM. To prevent BlackMatter from leaking 1000GB of stolen sensitive data, the initial ransom demand is $5.9 million. If the ransom is not paid by the deadline, the group threatens to increase the ransom to $11.8 million. Past ransomware negotiations show, however, that the paid ransom is usually significantly lower than the starting point. If NEW Cooperative decides to pay the ransom, it might be much lower than the initial amount requested.
The attack became public knowledge when a ransomware sample was uploaded to a public malware site yesterday. The ransom note, the post of the extortion on the BlackMatter deep web page, and the negotiation page are all now available to researchers.
In a statement, NEW Cooperative Inc. confirmed the attack. According to the statement, “NEW Cooperative recently identified a cybersecurity incident that is impacting some of our company’s devices and systems. Out of an abundance of caution, we have proactively taken our systems offline to contain the threat, and we can confirm it has been successfully contained.” The cooperative also mentioned that they notified relevant law enforcement about the incident.
Negotiations
The post above is no longer available, indicating negotiations are underway. Current negotiation details are exposed on Twitter by a user called Dark Feed [3] and some other Twitter users [4] to a more general audience. The message exchange between the threat actors and negotiator on behalf of the company focuses more on whether NEW Cooperative can be considered an off-limit critical infrastructure by BlackMatter’s own standards.
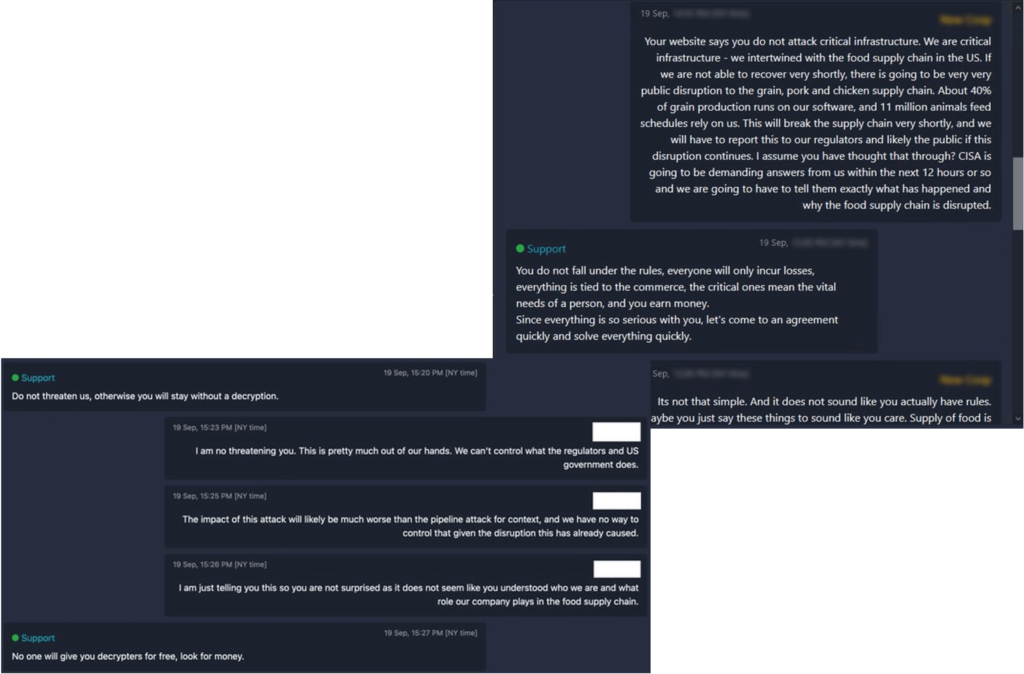
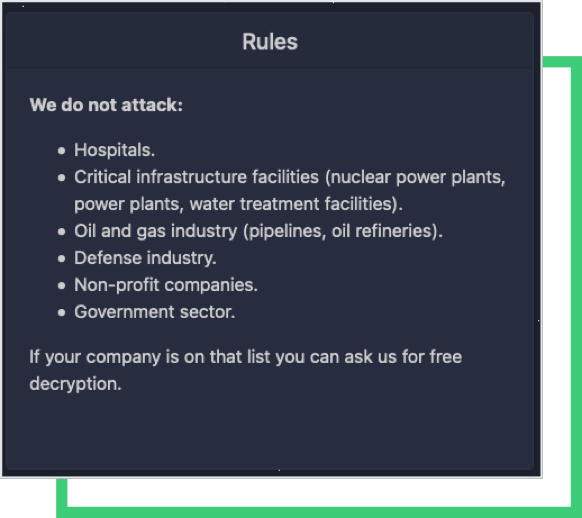
The rules posted on BlackMatter’s blog state that they do not attack hospitals, critical infrastructures, oil and gas, defense, NPOs, and government. The group gives examples of the critical infrastructure as “nuclear power plants, power plants, water treatment facilities” and examples of the oil and gas industry as “pipelines, oil refineries.” The group also ensures that they give free decryption keys if the targeted company falls under these categories. NEW Cooperative considers itself as critical infrastructure (for the food supply chain) and has asked for free decryption. However, BlackMatter feels otherwise and has still asked for the ransom to be paid.
BlackMatter, DarkSide, and Colonial Pipeline Attack
DarkSide, the ransomware group behind the Colonial Pipeline Attack, disappeared after the cybercriminals lost access to their servers. The severe damage caused by this attack led law enforcement to take immediate action against the group, seizing its servers. After a series of ransomware attacks in the first half of 2021, including the Colonial Pipeline attack, the Biden administration publicly warned Russia that Russia-based hacking groups should not attack critical sectors of the US economy [2].
BlackMatter is believed to be the rebranding of the DarkSide group based on similar operations and their specific mention that they will not attack pipelines. When BlackMatter first appeared, the group stated that they would not target “critical infrastructure facilities (nuclear power plants, power plants, water treatment facilities).” With the attack on NEW Cooperative, however, it seems that BlackMatter changed the rules as they see fit.
NEW Cooperative’s Ransomware Indicators
Black Kite Research analyzed hundreds of ransomware events and related reports in order to generate a list of ransomware indicators for a company, as well as identified the eight most common indicators to be used for ransomware risk management. Black Kite’s patent-pending Ransomware Susceptibility Index® follows a process of inspecting, transforming, and modeling data collected from a variety of OSINT sources (internet-wide scanners, hacker forums, the deep/dark web and more). Using data and machine learning, the correlation between control items is identified to provide a ransomware susceptibility rating on a scale from 0.0 (less susceptible) to 1.0 (more susceptible)*. Contact us for your free RSI™.
NEW Cooperative’s RSI™ is 0.59, almost reaching the critical threshold of 0.6. Black Kite Research determined this threshold based on historical and statistical data of past ransomware attacks. NEW Cooperative’s RSI™ of 0.59 indicates that it is 29% more susceptible to ransomware than the industry average.

The exploitation of any one of these ransomware indicators shown below can provide access to ransomware groups. This notion has proven true with many recent ransomware attacks that leverage vulnerabilities in widely used business software products. For example, MS Exchange or Windows Server vulnerabilities dubbed as ProxyShell, ProxyLogon, PetitPotam, and PrintNightmare are used by different ransomware groups such as Conti, Magniber, Lockflle, Black Kingdom, and DearCry.
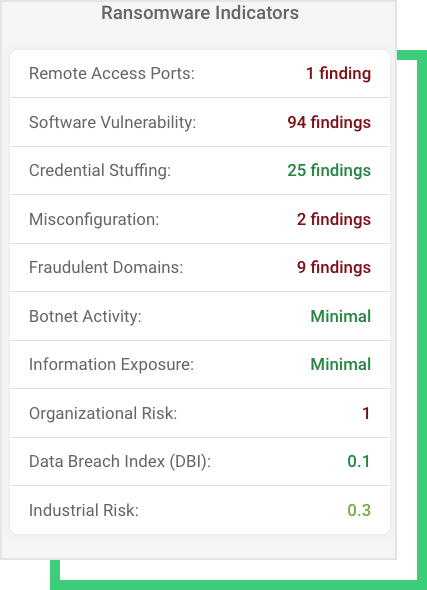
It’s still undecided if BlackMatter used a recent vulnerability, such as MSHTML flaw, to access the NEW Cooperative’s systems. The organization’s visible out-of-date systems are another component threat actors consider when determining the company’s criticality in the food supply chain.
Common Access Methods
Stolen credentials are another avenue for threat actors to gain access to systems. Recent credentials leaked from various platforms do, in fact, contain email addresses of NEW Cooperative employees. Combo lists shared on the dark web and tools that automate the attacking process could create a ripple effect and increase credential-stuffing attacks.
Black Kite Research also identified fraudulent domains recently registered, as well as several missing configurations on the email systems (such as missing DMARC and DKIM records).
How can you be proactive?
While the daily barrage of ransomware attacks can seem like a daunting challenge, there are proactive measures that companies can take to reduce their threat surface and limit the susceptibility to attacks. Planning for potential attacks begins with knowing the ransomware risk exposure.
Free RSI™
