Navigating the MOVEit Transfer Cybersecurity Storm: A Third-Party Risk Perspective
Written by: Kat Desy
Written by: Ferhat Dikbiyik
Additional Contributors: Yavuz Han & Ekrem Celik
Edited by: Katherine Desy
[Update: June 12, 2023]
The Progress company behind the popular MOVEit file transfer product has announced a second vulnerability. As part of the ongoing investigation, cybersecurity company Huntress conducted code reviews of the MOVEit product and uncovered a new vulnerability that could potentially be exploited. This newly discovered vulnerability was stated to be different from the previously reported vulnerability shared on May 31, 2023.
The advisory states that it could allow an unauthenticated attacker to gain unauthorized access to MOVEit Transfer database. An attacker could submit a crafted payload to a MOVEit Transfer application endpoint that could result in modification and disclosure of MOVEit database content.
Cybersecurity company Rapid7 has released a complete exploit chain for MOVEit Transfer CVE-2023-34362 today. An Exploit PoC has also been published on GitHub.
[Update: June 7, 2023]
We have detected a recent announcement made by the Cl0p ransomware group claiming responsibility for the recent attacks exploiting the MOVEit vulnerability. According to their statement, the group has purportedly downloaded a significant amount of data from multiple companies due to this exploit. They are demanding contact from affected organizations to negotiate the deletion of stolen data.
The Cl0p ransomware group’s full statement can be found below for reference:
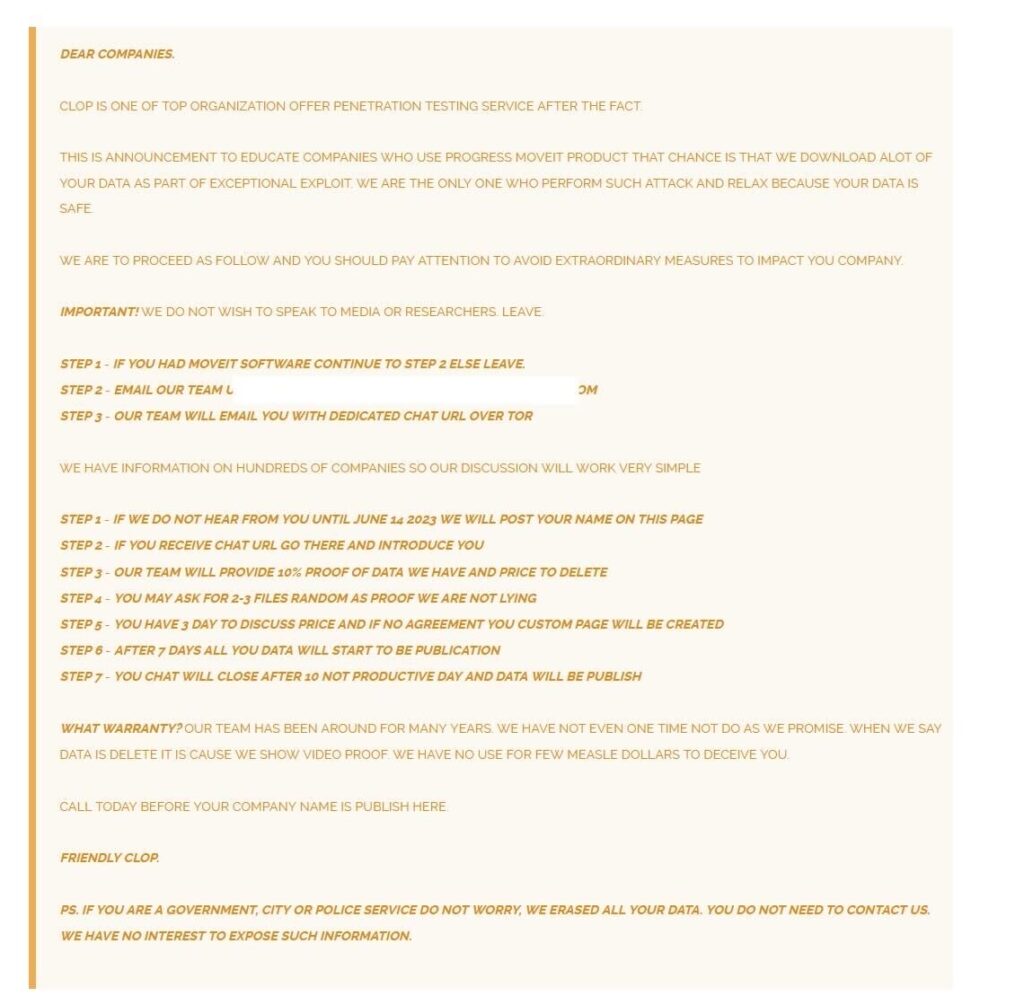
Given this development, it’s even more crucial for organizations to take immediate action. Please proceed to the Remediation Steps section of this article to learn more about what you can do to protect your organization.
Remember that timely reaction is essential when dealing with such cybersecurity threats. It’s always a good idea to stay updated and informed about the latest developments in cybersecurity. This incident is a sobering reminder of the importance of proactive third-party risk management.
Continue reading to understand more about the vulnerability, the risks associated, and how Black Kite can assist you in managing these threats.
As the interconnectedness of our digital world continues to grow, so too does the potential impact of zero-day vulnerabilities, especially in popular software products. These vulnerabilities, often exploited before a patch is available, can affect not just product users, but also ripple through the entire digital supply chain, impacting a vast array of businesses. In this context, the recent discovery of a critical zero-day vulnerability in Progress’s MOVEit software, widely used for secure file transfer, has set alarm bells ringing within the cybersecurity community and across various industries.
This SQL Injection vulnerability (CVE-2023-34362) has surfaced at a time when organizations are becoming increasingly aware of the risks they face from their third-party vendors. With incidents like the massive data breach at British Airways due to the MOVEit vulnerability, we are reminded that vendors, suppliers and partners can and often do directly impact an organization’s security.
As a leader in vendor risk intelligence, Black Kite helps organizations assess and monitor third-party cybersecurity risks in real-time. In light of the MOVEit vulnerability, our focus in this blog will be to analyze this significant vulnerability from a Third-Party Risk Management perspective, shedding light on its implications, the potential risks for your organization, and how Black Kite can assist in identifying and managing such risks.
What is the MOVEit Vulnerability?
MOVEit, developed by Progress Software, is a managed file transfer software that provides secure and compliant transfer of sensitive data among partners, customers, users, and systems. The software is widely used across various industries, which explains why it’s a prime target for cyber attackers looking to exploit critical vulnerabilities in popular software.
Description of the Vulnerability
Recently, a severe vulnerability identified in MOVEit Transfer (CVE-2023-34362) came under the spotlight. It is an SQL injection vulnerability that allows an unauthenticated attacker to gain access to the MOVEit Transfer’s database. Depending on the database engine used (MySQL, Microsoft SQL Server, or Azure SQL), an attacker can infer information about the database’s structure and contents and execute SQL statements that can alter or delete database elements. What distinguishes this vulnerability is its status as a zero-day vulnerability, meaning it was actively exploited before a patch was available. Unpatched systems can be exploited via HTTP or HTTPS, underscoring the urgency for companies using MOVEit Transfer to mitigate their risk immediately. This vulnerability became a hot topic in the cybersecurity community, primarily due to the British Airways data breach in June 2023, traced back to this zero-day vulnerability.
Products Affected
The MOVEit Transfer versions preceding 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1) are affected by this vulnerability. It’s critical to note that all versions prior to these (e.g., 2020.0 and 2019x) are also impacted, including older unsupported versions.
Companies Affected
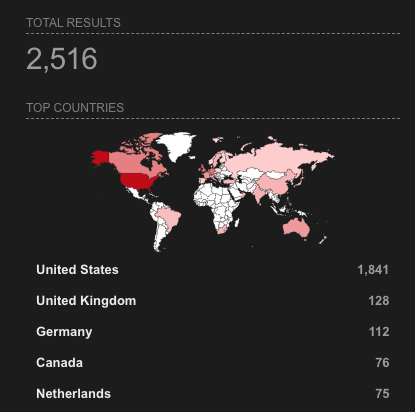
A Shodan search on June 5, 2023, revealed that 2,516 servers were vulnerable to this specific SQL injection. A substantial majority of these servers (1,800+) are located in the United States, with the United Kingdom, Germany, Canada, and the Netherlands also hosting a significant number of vulnerable servers. The specific number of companies affected may be far larger than this figure, given that a single company may own multiple servers or a server may host data for more than one company
Threat Actors: Lace Tempest and Clop Ransomware Group
Before delving into the risk from a third-party risk management perspective, it’s important to understand the threat actors exploiting the MOVEit vulnerability. Primarily, the threat actors exploiting this vulnerability belong to a notorious ransomware group known as Lace Tempest, believed to be the extortion arm of the infamous Clop ransomware group.
According to our latest research report, Clop ransomware group, active since 2019, is known for its hit-and-run mass-ransomware attacks, exploiting large-scale vulnerabilities without targeting specific organizations. The group resurfaced in March 2023, launching a mass-ransomware campaign that exploited a high-severity Fortra GoAnywhere vulnerability. This opportunistic approach, coupled with their capacity to exploit zero-day vulnerabilities, as seen in the MOVEit case, makes them a significant threat in the cybersecurity landscape.
Lace Tempest has been linked to numerous cyberattacks targeting organizations running vulnerable versions of the MOVEit software. They’ve been found exploiting the MOVEit vulnerability to gain unauthorized access to an organization’s network, subsequently deploying ransomware or performing other malicious activities.
The connection between the Lace Tempest attacks and the Clop ransomware group has been made based on the ransomware variants used in these attacks, which are nearly identical to those previously attributed to the Clop group. The tactics, techniques, and procedures (TTPs) used by Lace Tempest also closely align with those used by the Clop group in their earlier campaigns.
Understanding the threat actors behind the attacks not only helps in developing effective response strategies but also provides insight into the potential risks posed by the MOVEit vulnerability to organizations and their third-party networks. Given their history of exploiting zero-day vulnerabilities and conducting mass-ransomware campaigns, organizations and their vendors using MOVEit software should be particularly cautious.
Next, we’ll delve into the third-party risk posed by the MOVEit vulnerability, exemplified by the recent British Airways data breach.
The Risk from a Third-Party Risk Management Perspective
The MOVEit vulnerability doesn’t only affect the organizations directly using vulnerable versions, but it also presents substantial risks to their business partners and customers – a perspective that comes into sharper focus when considering third-party risk management (TPRM). TPRM is a strategic approach to managing risks associated with external parties that have access to an organization’s sensitive data or systems.
Case in Point: British Airways Data Breach
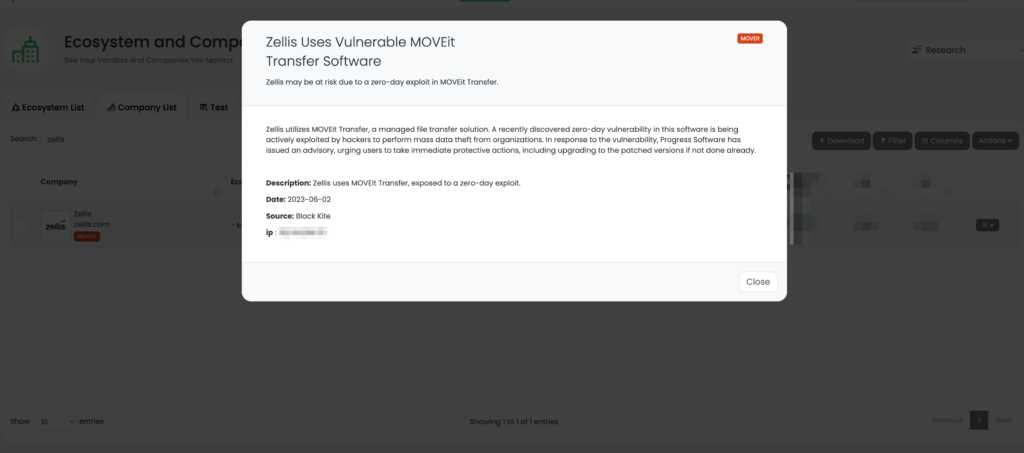
In June 2023, British Airways, one of the largest global airlines, became a victim of this critical MOVEit vulnerability when a third-party supplier of payroll support services, Zellis UK Ltd., experienced a cybersecurity incident. This incident compromised personal data of thousands of British Airways employees, including highly sensitive details such as bank account details, national security numbers, home addresses, and dates of birth.
This breach was traced back to the zero-day vulnerability in the MOVEit file transfer tool, indicating the ripple effect of such vulnerabilities in a third-party risk landscape. British Airways isn’t the only company using Zellis’ software; Many other companies use the same software for managing their payroll systems, illustrating how one vulnerable vendor could potentially impact multiple businesses.
Such incidents underscore the importance of an effective TPRM strategy. Organizations not only need to be aware of their own cybersecurity posture but also the security measures and vulnerabilities of their vendors. If a third-party vendor has access to an organization’s sensitive data, vulnerabilities in the vendor’s systems could lead to the organization’s data being compromised, as was the case with British Airways. This is why third-party risk management is crucial in today’s interconnected business ecosystem.
Understanding and managing the cybersecurity risks presented by third-party relationships, including vendors, suppliers, and partners, is a vital component of a robust cybersecurity strategy. Identifying vulnerabilities in third-party systems and mitigating the associated risks can protect organizations from potential breaches and the associated financial impact and potential damage to reputation.
Evaluating the Ransomware Risk of Companies Using MOVEit Servers
In light of the recent MOVEit vulnerability, it’s vital to understand the cyber risk landscape of companies utilizing MOVEit Managed File Transfer (MFT) servers. Our platform at Black Kite offers a comprehensive, rapid assessment of this risk landscape, allowing us to determine which vendors are most susceptible to cyber attacks, specifically ransomware.
The Ransomware Susceptibility Index® (RSI™), developed by Black Kite, is a tool that calculates event susceptibility within minutes, using data and machine learning. It discovers the likelihood that an organization will experience a ransomware attack by inspecting, transforming, and modeling data collected from a variety of OSINT sources.
Our recent analysis identified more than 600 companies that use MOVEit MFT servers. Upon assessing their cyber risk, we discovered that more than 47% of them have an RSI™ value of 0.4. This value represents the critical threshold, implying a high susceptibility to ransomware attacks. The industries most represented among these companies are:
- Finance and Insurance (NAICS: 52)
- Public Administration (NAICS: 92)
- Manufacturing (NAICS: 31)
- Professional, Scientific, and Technical Services (NAICS: 54)
- Retail Trade (NAICS: 44)
Understanding the RSI™ of these companies can help in developing effective courses of action for remediation by cross-correlating findings with Black Kite’s Cyber Risk Assessment. This allows organizations to avoid production, reputation, and financial losses by using reliable data to develop more informed policies. However, determining third parties with this vulnerability is a critical aspect of effective risk management. In the next section, we delve into how Black Kite can assist in this crucial task.
Identifying Third Parties with this Vulnerability: A Step-By-Step Guide with Black Kite
Navigating the murky waters of third-party cyber risk can be challenging, particularly when dealing with critical vulnerabilities such as MOVEit. Black Kite’s innovative cyber risk intelligence platform offers an effective solution, allowing users to filter vendors that could be susceptible to this vulnerability. Our unique feature, FocusTags™, serves as a powerful tool in this regard, enabling users to quickly identify and assess the risk of vendors within their ecosystem that use MOVEit MFT servers. Let’s walk through the steps to identify vendors with potential MOVEit vulnerability using Black Kite:
- Access the Dashboard: Log into the Black Kite platform and navigate to the dashboard.
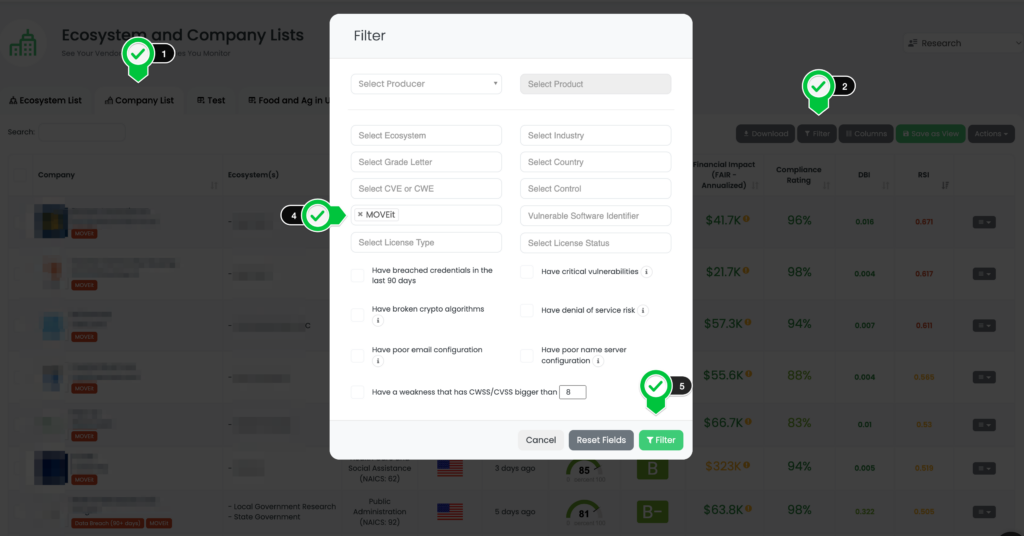
- Activate Filters: Click on the “Filter” button, which opens a drop-down menu of filter options.
- Select FocusTags™: In the filter options, click on “Focus Tags”. In the search field that appears, type “MOVEit”. This will filter your vendors by those who are using MOVEit MFT servers.
- Customize Your Search: If you want a more refined search, you can add other filter options according to your needs.
- Initiate Filtering: Once you’ve selected your desired filters, click “Filter”. This will update the company list according to your specifications.
The filtered list provides comprehensive visibility into the vendors that might be affected by the MOVEit vulnerability. Additionally, you can sort the results by companies’ cyber rating, Cyber risk quantification scores, or Ransomware Susceptibility Index® (RSI™) scores to better prioritize your response strategy.
Understanding the cyber risk profile of your third-party vendors is critical in a landscape increasingly characterized by interconnected supply chains and escalating cyber threats. With Black Kite, you can gain unprecedented visibility into your vendors’ cyber posture, enabling you to navigate third-party cyber risk more effectively. In the next section, we will discuss remediation steps and recommendations for dealing with the MOVEit vulnerability.
Remediation and Recommendations
As with any vulnerability, a swift response is key in minimizing potential damage. Actions should be taken from both a self-risk management perspective and a third-party risk management perspective.
Remediation and Recommendations for Self-Risk Management
If your organization is directly using the MOVEit MFT servers, take the following steps:
- First and foremost, download and install the latest patch provided by Progress Software for the MOVEit vulnerability. If for some reason patching is not immediately possible, it’s crucial to implement compensating controls to mitigate the risk.
- Intrusion Detection System (IDS)/Intrusion Prevention System (IPS) Rules: Update your IDS/IPS rules to detect any exploitation attempt of the MOVEit vulnerability. These tools, if properly configured, can help spot unusual activity in your network that may indicate an exploit.
- Regular Vulnerability Scanning: Conduct regular vulnerability scans on your systems to not only confirm the resolution of the MOVEit vulnerability but also to ensure that new vulnerabilities haven’t appeared.
- Improve Cybersecurity Hygiene: Maintain good cybersecurity hygiene by updating all other software regularly, training staff on threat awareness, and implementing strong access control.
Remediation and Recommendations for Third-Party Risk Management
When it comes to third-party risk management, vigilance is the key. Here are the steps you should follow:
- Third-Party Risk Assessments: Regularly assess the cybersecurity posture of your third parties. Utilize tools like Black Kite for comprehensive, data-driven cyber ratings and continuous risk monitoring.
- Vendor Patch Verification: Ensure that your vendors have patched the MOVEit vulnerability. Ask for proof of patch installation and ensure they’ve re-evaluated their security controls post-patching.
- Continuous Monitoring: Leverage tools like Black Kite that offer continuous monitoring capabilities to stay updated on your third parties’ cybersecurity stance and the emerging cyber threats that could affect them.
- Third-Party Risk Mitigation Strategies: Formulate risk mitigation strategies including contract clauses about timely patching, setting up SLAs for incident response, and incident reporting.
The MOVEit vulnerability highlights the complex and persistent nature of cybersecurity threats. Organizations need to be vigilant and proactive, continuously assessing and addressing their own cybersecurity stance and that of their third parties.
References:
- [1] https://www.bleepingcomputer.com/news/security/new-moveit-transfer-zero-day-mass-exploited-in-data-theft-attacks/
- [2] https://twitter.com/MsftSecIntel/status/1665537730946670595
- [3] https://www.cisa.gov/news-events/alerts/2023/06/01/progress-software-releases-security-advisory-moveit-transfer
- [4] https://nvd.nist.gov/vuln/detail/CVE-2023-34362
- [5] https://community.progress.com/s/article/MOVEit-Transfer-Critical-Vulnerability-31May2023
- [6] https://www.paddleyourownkanoo.com/2023/06/05/british-airways-caught-up-in-massive-payroll-data-breach-after-cybersecurity-incident-hits-supplier/

