Meet Pysa, the Latest Addition to the Ransomware Gang Community
Written by: ceren
Written by Gokcen Tapkan
Additional Contributor Yavuz Han
Edited by Haley Williams
The Biden Administration made a step forward in halting ransomware gang operations after assisting with shutting down REvil and DarkSide. However, low-profile threat actors continued to emerge and evolve despite being named among the top three ransomware groups, behind Conti and Lockbit.
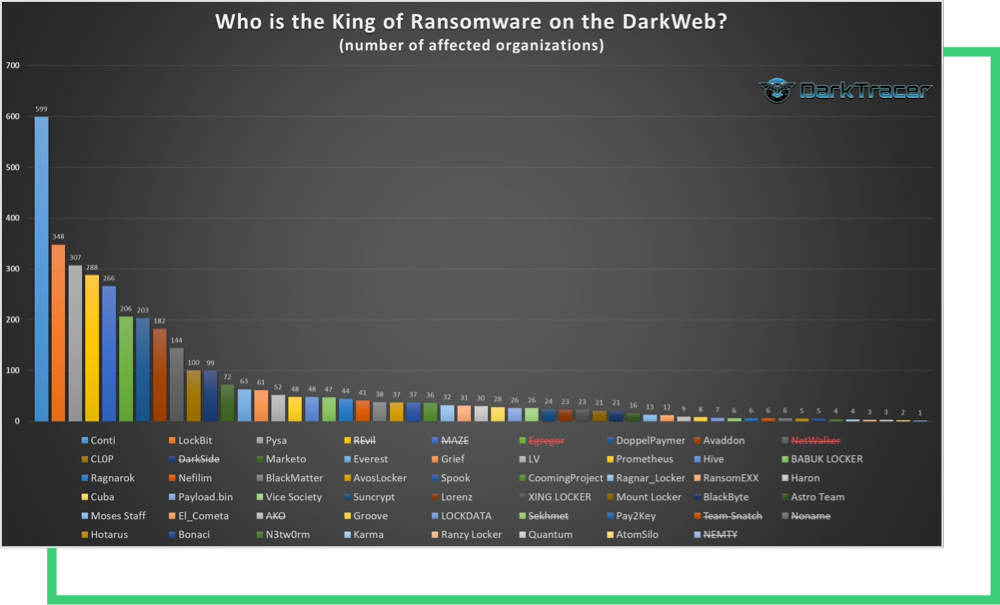
Pysa has targeted more than 300 companies to date, and the names of 52 of its victims were surfaced by members earlier this week. Since history continues to repeat itself, Black Kite Researchers took a step back to analyze the ransomware group’s tactics and targeting criteria.
The Facts About Pysa Ransomware
Pysa is a ransomware variant that originated as Mespinoza, a group that first surfaced in October 2018. According to the National Cybersecurity Agency of France, file extensions switched from “[.]locked” to “[.]pysa” in late 2019, after the group had targeted many corporations and local French authorities. Thus, giving it a new name in the ransomware community: Pysa.
Pysa ransomware first made headlines in the US after striking US government entities, educational institutions, private, and healthcare companies. The FBI issued a flash warning in March 2021, advising education institutions in particular about the Pysa threat. The incident dramatically increased ransomware’s visibility in the US cyber threat landscape.
Pysa is human-operated ransomware that’s currently incapable of self-propagation, and is actively delivered by threat actors. Initial attack vectors are carried out using phishing campaigns and open RDP ports. The gang uses an Advanced port and IP scanner by FAMATECH and PowerShell Empire, Koadic, and Mimikatz tools. The actors also use the WinScp tool to exfiltrate data from their victims.
Black Kite Researchers indicated many similarities between Pysa’s indicators of compromise (IoCs), and those of Conti ransomware and other gangs’ systems. This methodology has almost become the de-facto attack structure. Threat actors follow a double extortion model, threatening with the unavailability of the target organization’s systems and leaking the data exfiltrated before encryption.
Black Kite Research Analyzes Pysa Ransomware Victims
A Warning Sign for Pysa Ransomware Victims
Pysa ransomware victims yielded significant RSI™ ratings, capturing a mean of 0.40. Black Kite Research considers it a risky zone if a company’s RSI™ score is above 0.4. Of the victims, 41% are above the average RSI™ score, indicating a stronger probability of experiencing a ransomware attack.
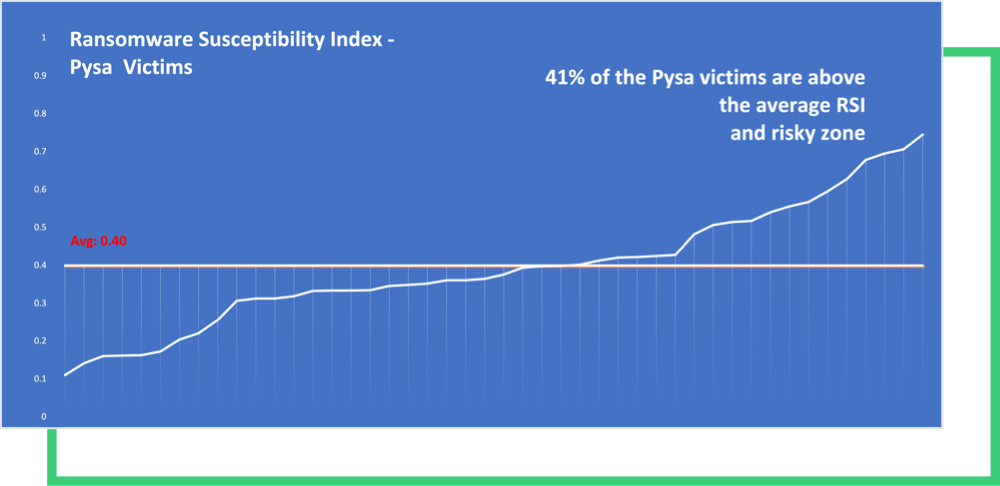
Methodology: Black Kite Research captured the Ransomware Susceptibility Index® ratings of Pysa victims listed on the deep web. An RSI™ greater than 0.4 is always a red flag for a company and its stakeholders. Black Kite Research foresees a high level of confidence in the timeliness of RSI™ scores since ransomware attacks do not involve a wide window for the sake of getting the payments as quickly as possible.
Request a Free RSITM
The US is a Hotspot for Pysa Ransomware
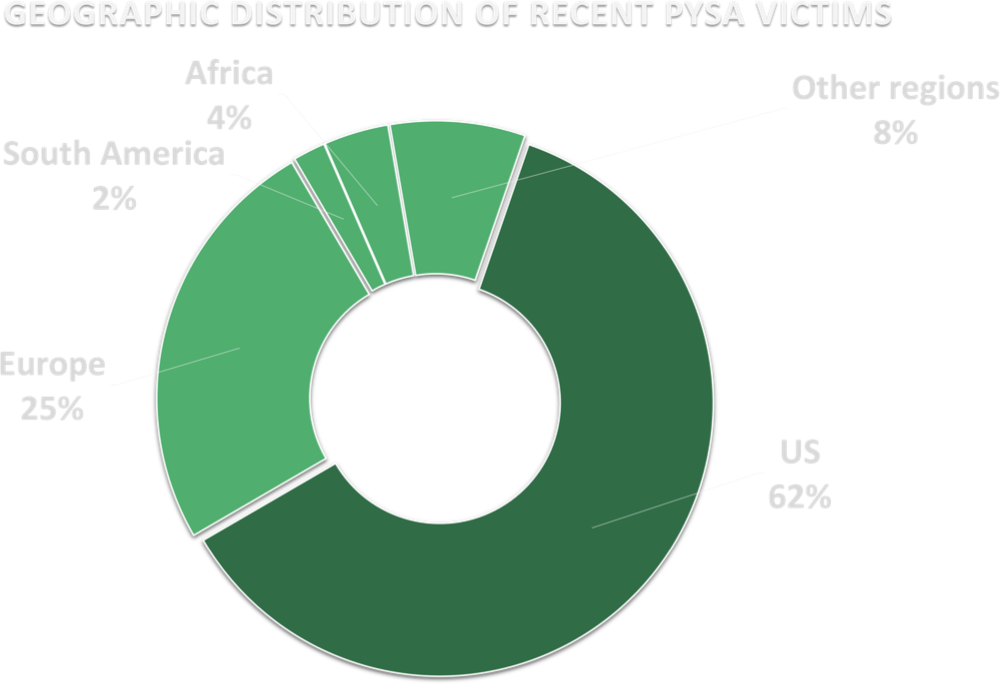
Most of Pysa’s targeted corporations are based in the US. This directly aligns with Black Kite Research’s recent analysis of ransomware gangs’ joint retaliation efforts against the US for the shutdown of REvil.
While we shouldn’t assume that Pysa deliberately targets US companies to extend Conti and Groove’s threats, we know that it’s easier for them to capitalize on the U.S. and European companies with double extortion tactics, thanks to the privacy laws enforcing the security of personal information.
Manufacturers Are the Most Common Pysa Ransomware Victims
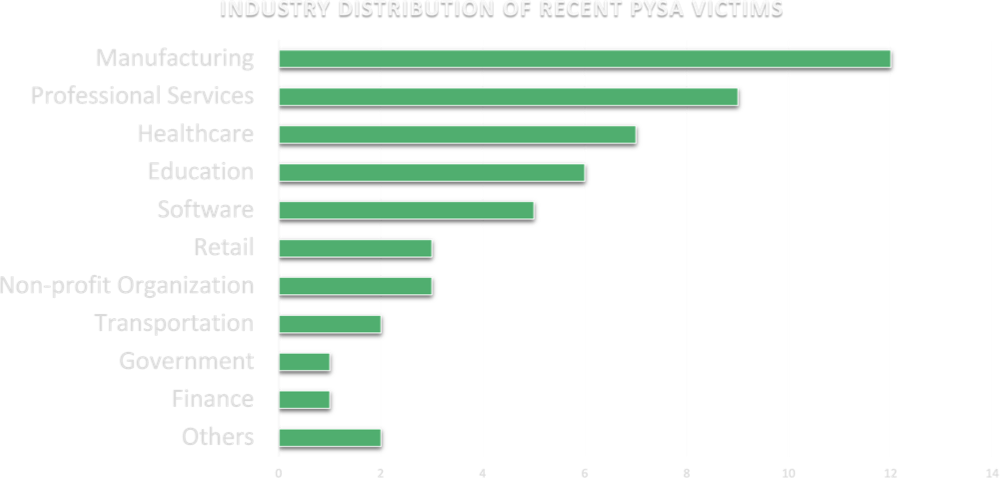
When we categorize Pysa victims by industry, it’s clear the ransomware group does not discriminate. The list includes organizations from churches to hospitals, and universities to retailers. Manufacturing, professional services, healthcare, and education are included in the list of victims as sectors that house valuable personal information and don’t have a high level of cybersecurity maturity.
The Latest in the Fight Against Ransomware Operations
The US government is more determined than ever to stop cybercriminals. Both REvil and DarkSide members have gone silent, opting out of cybercriminal forums on the Dark Web since the Kaseya and Colonial Pipeline attacks. This suggests that law enforcement across Europe and the US are uniting to mitigate cyber attacks.
Last week, a REvil member linked to the Kaseya supply-chain attack was arrested in Poland. REvil affiliates are already publicly complaining about not being paid for successful attacks on forums, which will undoubtedly have long-term consequences.
The US Department of State has also offered up to $10 million for information on key leaders of the DarkSide group, an attempt by the authorities to capitalize on the ransomware groups’ growing distrust. It’s likely that we’ll see more meltdowns in these communities.
How to Stay Protected from Ransomware
It’s not a matter of if, but when the next ransomware attack will happen. Although the successful attacks are the only ones making headlines, there are many attacks that are prevented.
Therefore, a prepare-for-breach strategy should be adopted, concentrating on the most advanced preventative tactics. This includes phishing, patch management, multi-factor authentication, and remote backups. Think about your risk management strategy proactively rather than reactively.
Companies should also follow the practices published by authorities, like CISA’s recently released recommendations. The info sheet is a generalized set of best practices and recommendations and sector-free. Any sector can adapt this set of control items to increase its cybersecurity maturity and immunity to ransomware attacks. Read our blog for more information on CISA’s recommendations.
The FBI has also recently published a set of recommendations to get prepared against ransomware attacks. Instead of meeting criminals’ demands, companies should take proactive steps to protect themselves against ransomware:
- Back up sensitive and confidential data offline on the Cloud, on an external hard drive, or another storage device. Make sure these backups are secure, and data on the system is not available for change or deletion.
- Regularly update anti-virus and anti-malware software on all hosts. Out-of-date systems are a prime gateway for malicious activity.
- Use two-factor authentication for user login credentials and replace email with authenticator apps. Actors may access victim email accounts. Do not open unsolicited attachments or click on email links.
- Enable the least privilege for file, directory, and network sharing permissions.
Fore more information, check out our latest report: The Government Called, Are You Ready to Answer?

