Ransomware Infects Third-Party Manufacturer Twice
Written by: ceren
Written by Gokcen Tapkan
Edited by Haley Williams
Gigabyte Technology, a third-party computer manufacturer, was hit twice by ransomware actors in the last three months. Today, it’s not unusual for a company to be attacked multiple times by threat actors. However, when the interval between two attacks is this short, it’s worth looking at the details.
Following the initial attack in mid-August, launched by RansomEXX, the second attack is claimed by a different ransomware group called AvosLocker, which now threatens to publish 112GB of leaked data if the company does not fulfill their demands. Systems have been shut down as a result of the attack in order to prevent a spread. This manufacturer is a major supplier of graphics cards, data center servers, laptops, and monitors to AMD, Intel, American MegaCards Ice Lake, and Barracuda.
Using the Ransomware Susceptibility Index® (RSI™) ratings on the Black Kite platform, the Black Kite Research team is able to detect the timing of the increase in ransomware susceptibility since the first attack. Was this a Groundhog Day for Gigabyte Technology?
August Attack
When Gigabyte technology was hit in mid-August, Black Kite Research started to monitor the company closely. We took a snapshot of its cybersecurity posture along with the Ransomware Susceptibility Index® (RSI™), which indicated a high RSI™ score of 0.655 at the time.
RSI™ is a metric between 0.0 and 1.0, the likelihood that an organization will experience a ransomware attack. It follows a process of inspecting, transforming, and modeling data collected from various OSINT sources (internet-wide scanners, hacker forums, the deep/dark web, and more).
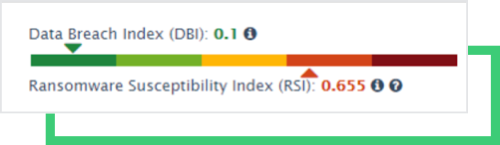
An RSI™ score greater than 0.4 is always a red flag for a company itself, and, if it reflects the score of a critical supplier, for its stakeholders as well. A high RSI™ score is usually attributed to out-of-date products with software vulnerabilities, and/or poor email configuration that can be exploited for phishing attacks. Both of these were true for Gigabyte Technology. We expected, over time, to see improvements in their cybersecurity posture and susceptibility to ransomware. However, this was not the case.
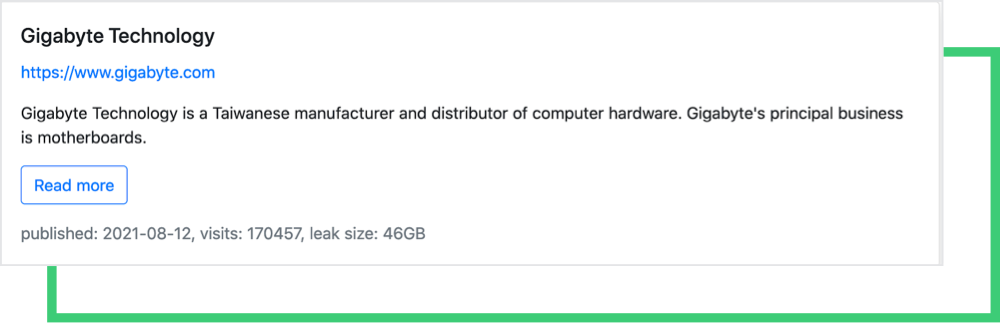
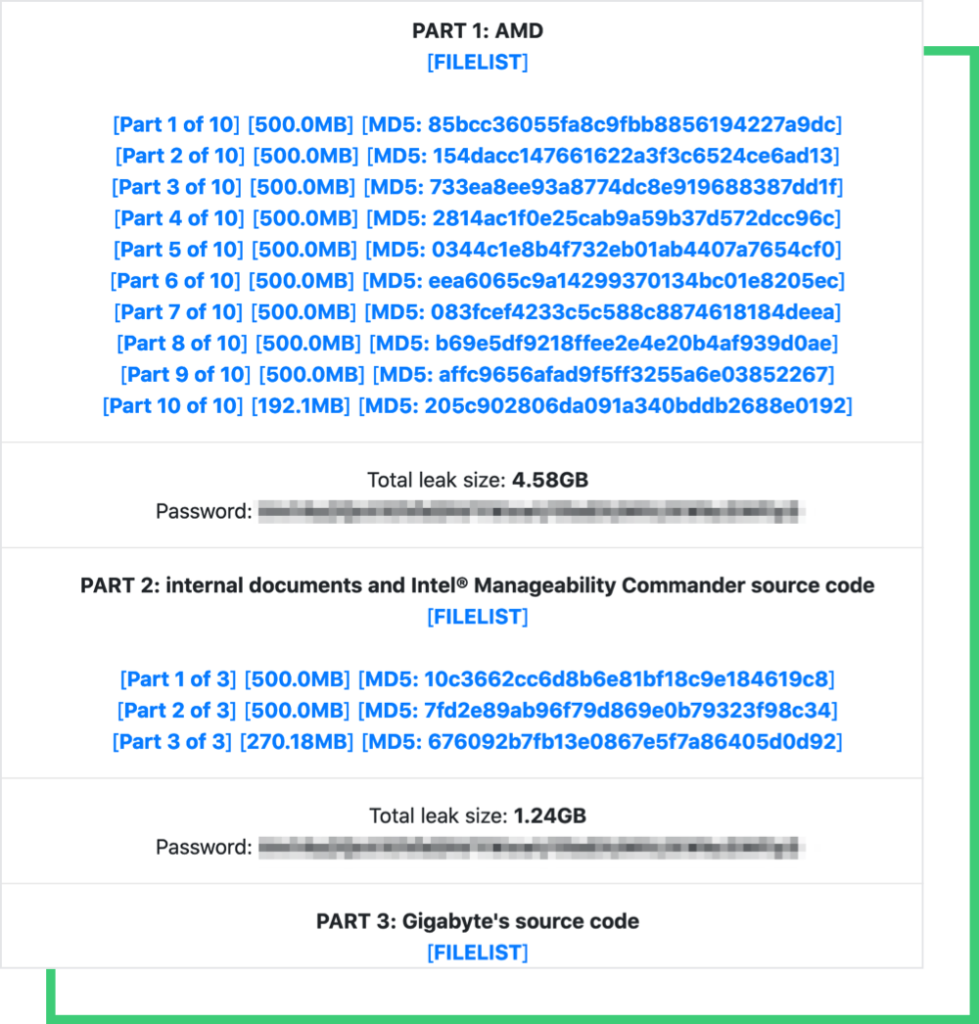
The data leaked from the August hack is still available on RansomEXX’s site, totaling 46 GB, and includes Intel and AMD’s product data.
Today
Today, the third-party manufacturer has the highest possible RSI™ score of 1.0.
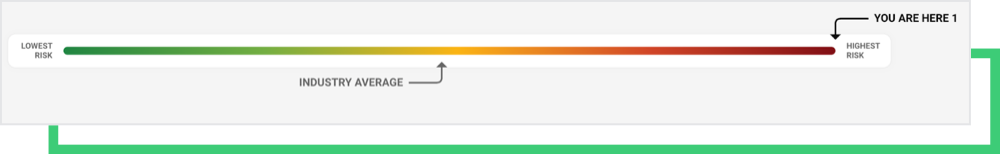
Source: Black Kite Platform
The Black Kite platform’s findings show that the third-party supplier is 50% more susceptible to a potential ransomware attack compared to other computer manufacturers in the industry.
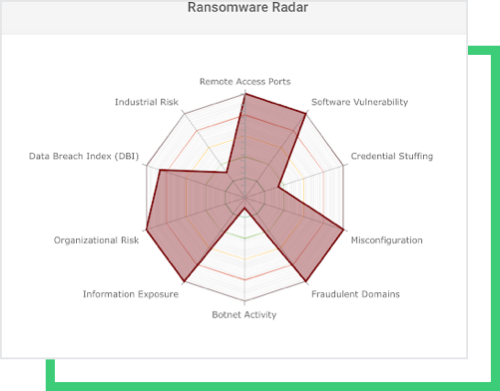
Cascading Effect of the Past Breach
The company has high-risk issues in Remote Access Ports, Software Vulnerability, Email Misconfiguration, Fraudulent Domains, and Credential Stuffing indicators.
Remote access ports have become popular entry points for external, malicious actors. Although the use of these ports is declining each year, it remains the easiest way to upload a ransomware kit. With vulnerable services in these ports, remote access points have historically been leveraged in large-scale ransomware attacks like WannaCry and NotPetya. Cybercriminals can easily scan open ports with autonomous tools.
Leaked credentials usually serve as an avenue for phishing and stuffing campaigns. Once hackers have the emails through compromised credentials, this allows for robust resource development to aid in potential attacks.
Software vulnerabilities due to out-of-date systems have become the most leveraged entry points by ransomware actors.
The August hack also gave rise to a high Data Breach Index score due to data disclosure. The disclosure might have a cascading effect on today’s hack, assuming a trove of internal data was leaked and circulated in hacker forums.
All of the above indicators eventually gave rise to a high RSI™ score, despite a three-month time period of post-attack.
Technical Report
Today, Gigabyte Technology still shows poor cyber security posture according to the current technical report provided by Black Kite. The report shows low grades in Patch Management, Application Security, and Credential Management, with only average grades in some others. See Black Kite’s Methodology for details on the technical categories.
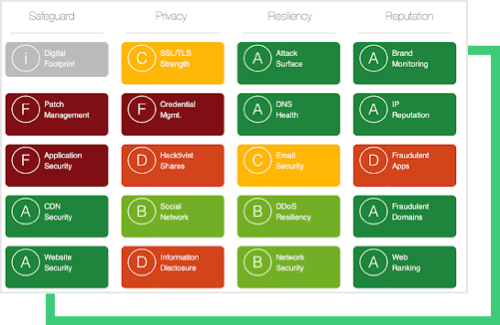
Although a poor cyber hygiene score is not a sole indicator that a company will experience a cyber incident, a technical report that has many F and D grades in critical categories calls for a cybersecurity action plan.
Stakeholders’ Data Might be a Leverage Factor
This is not the first time a ransomware attack has hit a third-party manufacturer. While the full details of this attack have not yet come to light, it is not uncommon for stakeholders’ data to be a leveraged factor. The threat actors that hit Quanta in April demanded the ransom from Apple instead, threatening to publish the new MacBook’s blueprints. AvosLocker gang, for the time being, has disclosed an NDA belonging to the Barracuda networks that might be a leverage factor in the negotiations.
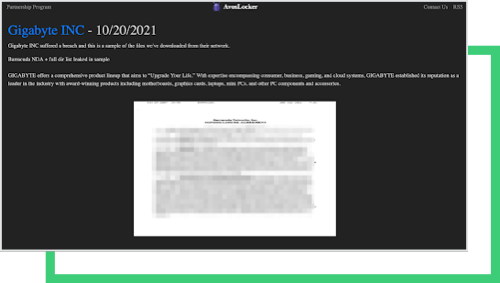
History tends to repeat itself. Cybercriminals target organizations that do not consistently deploy due diligence and make cybersecurity a priority within the business. Cybercriminals anticipate that security issues and vulnerabilities will remain present and exploitatable if the cybersecurity investment is not adequate.
Get Your Free RSI™References
- https://securelist.com/ransomexx-trojan-attacks-linux-systems/99279/
- https://en.wikipedia.org/wiki/WannaCry_ransomware_attack
- https://therecord.media/avoslocker-ransomware-gang-to-auction-the-data-of-victims-who-dont-pay/
- https://en.wikipedia.org/wiki/WannaCry_ransomware_attack
- https://en.wikipedia.org/wiki/Petya_(malware)

