How to Protect your Vendor Ecosystem from the Impact of Cyber Warfare
Written by: ceren
Written by Ferhat Dikbiyik
Additional Contributor Yavuz Han
Edited by Haley Williams
In the last 24-36 hours, state-sponsored hacker groups publicly disclosed which flag they’re representing in cyber battle. The notorious Conti ransomware gang declared their support for Russia and intentions to execute cyber-attacks within their full power against countries supporting Ukraine. Additional volunteer underground hacker groups, including Anonymous, asserted their counter shortly after, supporting Ukraine and stance against Russian institutions.
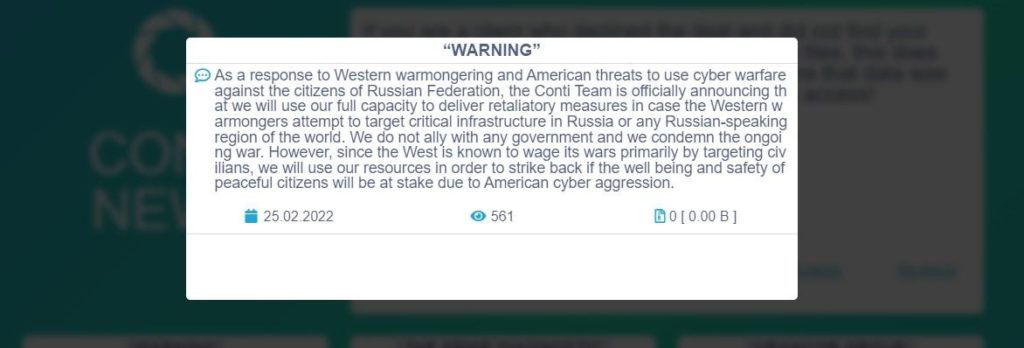
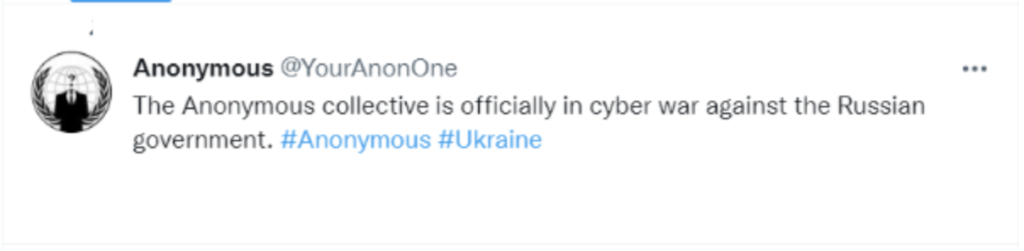
These bold escalations have increased concerns significantly for many companies worldwide about the safety of their digital supply chain. Black Kite’s platform provides visibility to its customers around the overall cyber risk of any vendor, including ransomware susceptibility and DDoS resiliency in relation to Ukrainian and Russian-based assets.
Identify Possible Targets in Your Vendor Ecosystem
With multiple attack vectors and malware used in the Russian – Ukrainian cyberattacks, such as HermeticWiper and Cyclops Blink (replacement of VPNFilter malware), there is no single way of protecting your vendor ecosystem against escalating cyber threats.
Some countries publicly stated their support for either side of the crisis, likely ranking themselves higher on threat actors’ hit lists. Vendors from these countries might be more subject to cyberattacks, especially vendors residing and owning IT assets in Ukraine and Russia.
Black Kite can determine vendor risk by identifying the location of IT assets of the companies and also their vendors (4th parties). With smart tags, Black Kite alerts customers to the impact of cyber incidents related to the Russia-Ukraine war on their vendor ecosystems.
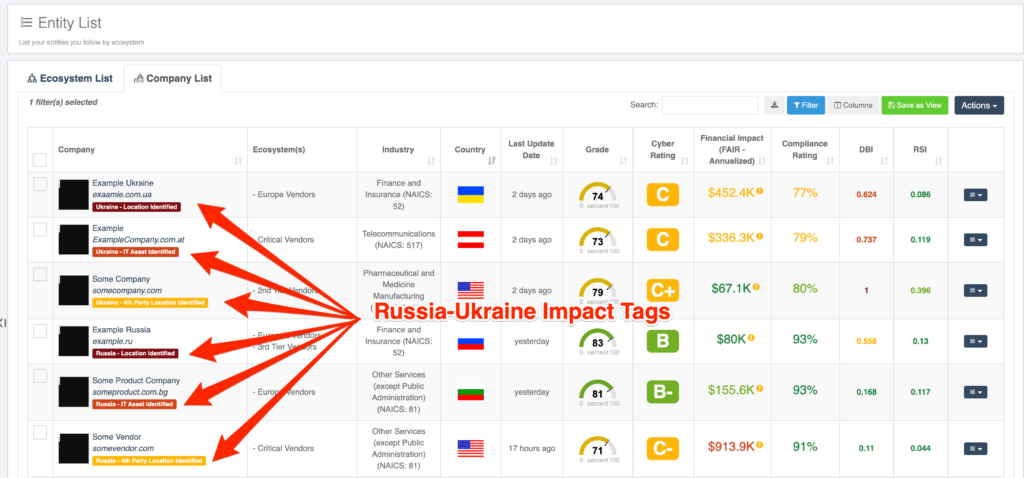
Understand the Cybersecurity Posture of Your Third and Fourth Parties
Threat actors might advance their way upwards in the supply chain by initially attacking a fourth party vendor (vendor of a vendor). Even if a vendor is not directly related to targeted countries, your company might still be impacted due to a targeted fourth party.
In addition to smart tags, Black Kite follows and applies commonly-used frameworks developed by the MITRE Corporation to score software weaknesses consistently and transparently, converting highly technical terms into simple letter grades. The vendors with lower grades can appear as easy opportunities to threat actors, and in turn, quickly be targeted. Organizations can also share technical details with their vendors with one click, alerting business partners to vulnerabilities and allowing them to improve accordingly.
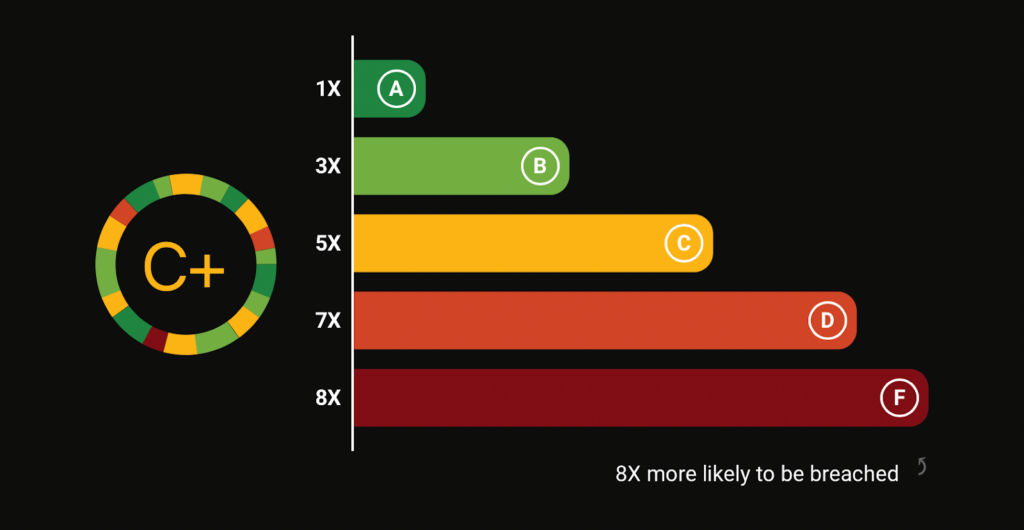
Understand the Ransomware Susceptibility of Your Vendors
The Conti ransomware group is not alone in attacking organizations they perceive as “enemies.” Methods such as weaponizing data-wiper malware to extort companies, or simply hinder their operations, emphasize the need to monitor vendor ransomware risk and the anomalies in their ecosystems.
IoC lists are available in open sources. Playbooks of infamous gangs analyzed by research groups can also help understand their TTPs. For instance, Black Kite Research recently published three different analyses of Conti’s methods, playbook, and victims. CISA also published an alert about the destructive malware targeting organizations in Ukraine, including technical details.
Black Kite’s Ransomware Susceptibility Index™ (RSI™) follows a process of inspecting, transforming, and modeling collected from various OSINT sources (internet-wide scanners, hacker forums, the deep/dark web, and more). Using the data and machine learning, the correlation between control items is identified to provide approximations.

With the RSI™, organizations can understand which vendors are most prone to ransomware and develop a practical course of action for remediation by cross-correlating findings with Black Kite’s Cyber Risk Assessment.
Monitor the DDoS Resiliency of Your Vendors
Threat actors exploit Distributed Denial of Service (DDoS) attacks to block services and interrupt business. This method has become a primary weapon used by state-sponsored hackers to paralyze the target systems.
Russian hackers used this DDoS cyber weapon to attack Ukrainian state banks and public institutions on both February 15 and 23, 2022. The attacks resulted in service disruptions for hours, creating a ripple effect throughout the government institutions as a whole.
It’s possible adversaries might use the same weapon for companies to target your vendor ecosystem. Therefore, monitoring DDoS resiliency is imperative. Begin asking vendors to block suspicious IP addresses, such as IP addresses in the blacklists due to botnet infection and IP addresses originating from Russia and other wary countries. Threat actors are suspected of using VPN and ToR services to hide their tracks, so blocking IP ranges of Free VPN and ToR services is meaningful.
One of the 20 Black Kite Cyber Risk Assessment categories is DDoS Resiliency, which results from 15 different potential DDoS checks and detects any potential DDoS amplification endpoints. The data is collected from non-intrusive scanners and other internet-wide scanners.
Organizations can filter vendors with respect to their DDoS ratings and inform vendors rating lower about the misconfiguration.
In Conclusion
- Monitor your third and fourth parties’ cyber security posture
- Identify possible targets in your vendor ecosystem (IT asset locations might help)
- Confirm vendors have the IoC list of possible malware in use by state-sponsored hackers
- Monitor the ransomware susceptibility of your vendors. Ensure they patch recent critical vulnerabilities, use up-to-date services, do not have critical open ports such as RDP or SMB, and correct email configuration to mitigate phishing attacks
- Monitor the DDoS resiliency of your vendors and make sure they block suspicious IP addresses
Get a Free Vendor Risk Assessment Today
Black Kite offers a free vendor assessment for up to five vendors here. Act now and request your free vendor assessment to see the possible impacts of the Ukraine-Russia war in cyberspace on your vendor ecosystem.
Cyber Attack Timeline
Our research team has compiled a list of cyber attacks and events that have occurred during the Russian invasion of Ukraine – this will be updated as more intelligence comes in.
| Date | Subject | Threat Actor | Supporting | Source |
|---|---|---|---|---|
| 01.11.2022 | CISA: Understanding and Mitigating Russian State-Sponsored Cyber Threats to U.S. Critical Infrastructure | Link | ||
| 01.13-14.2022 | The cyber-attack against the Ukrainian government websites | Link | ||
| 01.14.2022 | Russia takes down REvil ransomware group | Link | ||
| 01.15.2021 | Microsoft: Destructive malware targeting Ukrainian organizations | Link | ||
| 01.16.2022 | Ukraine blames Russia for cyberattack against government websites | Link | ||
| 01.18.2021 | Data of several Ukrainian government agencies is wiped in cyberattack | |||
| 01.23.2022 | DHS warns of potential Russia cyberattacks amid tensions | Link | ||
| 02.15.2022 | Russian presence in critical Ukrainian networks, according to newly declassified U.S. intelligence | Link | ||
| 02.15.2022 | Ukraine’s defense ministry hit by DDoS attack | Link | ||
| 02.16.2022 | CISA has released a new announcement: Russian State-Sponsored Actors Target Cleared Defense Contractor Networks | Link | ||
| 02.18.2022 | CISA releases guidance regarding the Russia-Ukraine conflict | Link | ||
| 02.18.2022 | White House press briefing: We believe that the Russian government is responsible for wide-scale cyberattacks on Ukrainian banks this week | Link | ||
| 02.22.2022 | TheRedBanditsRU announced their support for Russia | TheRedBanditsRU | Russia | Link |
| 02.22.2022 | Senior FBI cyber official asked US businesses and local governments to be mindful of the potential for ransomware attacks as the crisis between the Kremlin and Ukraine deepens | Link | ||
| 02.23.2022 | The US and UK agencies said the malware was developed by SandWorm, a cyber-unit of the GRU Russian military intelligence service | SandWorm | Russia | Link |
| 02.23.2022 | ESET and Broadcom’s Symantec — have reported that computer networks in the country have been hit with a new data-wiping attack | Link | ||
| 02.23.2022 | Ukrainian banking and government websites hit by DDoS attack again | Link | ||
| 02.24.2022 | Remarks by President Biden on Russia’s Unprovoked and Unjustified Attack on Ukraine | Link | ||
| 02.24.2022 | Russian websites, critical information infrastructure hit by cyberattacks | Link 1 Link 2 | ||
| 02.24.2022 | Belarusian Cyber-Partisans (hacking group) announced supporting Ukraine | Belarusian Cyber-Partisans | Ukraine | |
| 02.24.2022 | Freecivilian group announced that it has data from 50 official Ukrainian websites | Freecivilian | Russia | Link |
| 02.25.2022 | CERT-UA: We continue monitoring activities of the ‘UNC1151’ group (its members are officers of the Ministry of Defence of the Republic of Belarus) | UNC1151 | Russia | Link |
| 02.25.2022 | Conti announced their support for Russia | Conti | Russia | Link |
| 02.25.2022 | The Anonymous declared officially in cyber war against the Russian government | Anonymous | Ukraine | Link |
| 02.25.2022 | Anonymous announced that the website of the Russian Ministry of Defense was down | Anonymous | Ukraine | Link |
| 02.25.2022 | Anonymous announced that the website of the RT News was down | Anonymous | Ukraine | Link |
| 02.25.2022 | Belarusian defense contractor Tetraedr was hacked: 200 GB data leak | Anonymous Liberland & Pwn-Bar | Ukraine | Link |
| 02.25.2022 | GhostSec announced their support for Ukraine | GhostSec | Link | |
| 02.25.2022 | CoomingProject (Ransomware group) announced their support for Russia | CoomingProject | Russia | Link |
| 02.26.2022 | Ukraine government officially declared the #itarmyofukraine as their official IT army | IT army of Ukraine | Ukraine | Link |
| 02.26.2022 | The ‘IT Army’ announced by by Minister for Digital Transformation of Ukraine Mykhaylo Fedorov has released its target list | IT army of Ukraine | Ukraine | Link |
| 02.26.2022 | Black Hawk announces an operation in Russia | Black Hawk | Ukraine | Link |
| 02.27.2022 | AgainstTheWest announced their support for Ukraine | AgainstTheWest (ATW) | Ukraine | Link |
| 02.27.2022 | GNG, a hacking group affiliated with Anonymous, has gained access to SberBANK database and leaked hundreds of data files | GNG | Ukraine | Link |
| 02.27.2022 | NB65 has officially declared cyber war on Russia | NB65 | Ukraine | Link |
| 02.27.2022 | Russian government and 1,500 other websites have been taken down | 1LevelCrew | Ukraine | Link |
| 02.27.2022 | Belarusian Cyber-Partisans accessed the computers that control the Belarusian train system | Belarusian Cyber-Partisans | Ukraine | Link |
| 02.27.2022 | Announced they stand with Ukraine | kelvinsecurity | Ukraine | Link |
| 02.27.2022 | Announced they stand with Ukraine | Raidforums Admin (popular dark web forum) | Ukraine | Link |
| 02.27.2022 | They released some IOCS about Ukraine targets | Gamaredon | Russia | Link |
| 02.27.2022 | LockBit ransomware group announced official statement on the cyber threat to Russia | LockBit | None | Link |
| 02.28.2022 | The Russian Ministry of Labour and Social Protection website is down | 1LevelCrew | Ukraine | Link |
| 02.28.2022 | SHDWSec joins the movement to support Ukraine | SHDWSec | Ukraine | Link |
| 03.01.2022 | HydraUG made a clear statement via Twitter: Already 5804 websites attacked | Hydra UG | Ukraine | Link |
| 03.01.2022 | Stormous announced their support for Russia | Stormous | Russia | Link |
| 03.01.2022 | DigitalCobraGang announced their support for Russia | DigitalCobraGang | Russia | |
| 03.01.2022 | Zatoichi announced their support for Russia | Zatoichi | Russia | Link |
| 03.02.2022 | Xaknet announced their support for Russia | Xaknet | Russia | Link |
| 03.03.2022 | Targeting Russian government websites | v0g3lSec | Ukraine | Link |

