Understanding CVE-2023-25690 on Apache Servers: Protecting Your Vendor Ecosystem
Written by: ceren
Written by Ferhat Dikbiyik
Edited by Haley Williams
In the vast cyber landscape, vulnerabilities often act as ticking time bombs. They lie in wait, providing lucrative opportunities for potential exploiters. One such ticking time bomb is CVE-2023-25690, a recently discovered vulnerability in Apache HTTP Servers. Classified as an “HTTP Request Smuggling” vulnerability, this flaw poses a potential threat to millions of servers worldwide.
Though it’s not currently known to be actively exploited by ransomware gangs or Advanced Persistent Threat (APT) groups, the sheer scale of its reach makes it an appealing target. In this blog post, we delve into the details of this vulnerability, its potential impact, and, crucially, how organizations can secure themselves and their third-party ecosystems against it.
What is the CVE-2023-25690 Vulnerability and Its Potential Impact?
CVE-2023-25690 is a critical vulnerability discovered in Apache HTTP Server versions 2.4.0 through 2.4.55 [1]. This critical vulnerability, boasting a high Common Vulnerability Scoring System (CVSS) base score of 9.8, necessitates immediate remediation and mitigation strategies [2].
Further exacerbating the threat, an exploit proof-of-concept (PoC) has been made public [3], making it increasingly likely that it will be leveraged by malicious threat actors in the near future. The exploit PoC allows an attacker to execute HTTP Request Smuggling attacks. These are powerful techniques often used to bypass security mechanisms, allowing attackers to perform unauthorized operations on a target server [3].
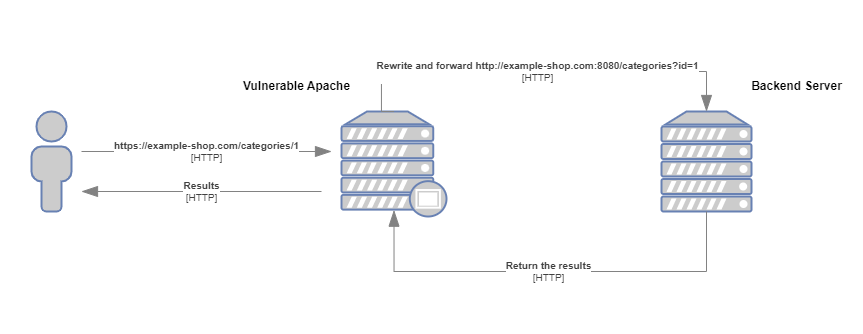
Which Products Are Affected by the CVE-2023-25690 Vulnerability?
As stated earlier, the CVE-2023-25690 vulnerability directly impacts Apache HTTP Server versions 2.4.0 to 2.4.55. The software is widely adopted, serving as the backbone of numerous websites globally. If your organization or vendors in your network are using one of these versions, immediate action should be taken to update the server to at least version 2.4.56.
What Could Be the Potential Impact of the CVE-2023-25690 Vulnerability?
Should a threat actor exploit CVE-2023-25690, they can perform actions that could result in considerable harm. They could bypass access controls in the proxy server, leading to potential unauthorized access to sensitive data. They might proxy unintended URLs to existing origin servers, causing misdirection or misuse of resources. And, in a worst-case scenario, they could cause cache poisoning, a sophisticated attack that could manipulate the responses sent to legitimate users [3].
The potential impact of this vulnerability is concerning, considering that Apache HTTP Server is one of the most widely used web server software, powering a significant portion of websites on the internet. If leveraged successfully, this vulnerability could potentially affect millions of servers globally and the businesses relying on them. That’s why it’s recommended that users of the impacted Apache versions update their servers to at least version 2.4.56.
Given the seriousness of this vulnerability, it’s crucial to understand its prevalence, how it can be identified, and what can be done to mitigate its risks – which we will discuss in the following sections.
How Widespread is the CVE-2023-25690 Vulnerability?
Due to the Apache HTTP Server’s wide adoption, the CVE-2023-25690 vulnerability represents a global issue. According to a recent Shodan search, there are over 6 million potentially vulnerable servers worldwide. The United States, with nearly 2 million vulnerable servers, tops the list. However, the issue spans across continents, with countries like Germany, France, Japan, and the United Kingdom also reporting high numbers of potentially affected servers.
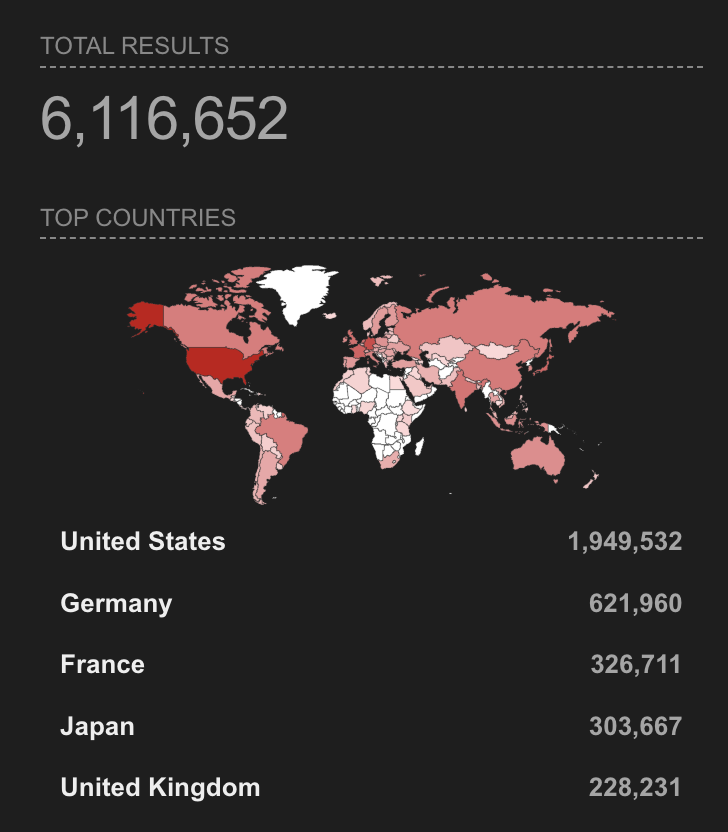
This widespread presence of the vulnerability illustrates the scope of the risk that businesses and their vendor ecosystems face. The potential for cybercriminals to exploit this vulnerability and infiltrate systems is considerable, heightening the need for immediate remediation.
The Third-Party Cyber Risk Due to CVE-2023-25690
The CVE-2023-25690 vulnerability is particularly concerning from a third-party risk management (TPRM) perspective. The widespread use of Apache Servers and the high number of vulnerable servers globally indicate a substantial potential risk within your vendor ecosystem. A single unpatched server could be an entry point for threat actors into not only the affected company but also the businesses associated with it, including your own.
It’s important to note that this vulnerability has a significant impact in two ways. First, it can be exploited directly, allowing attackers to access hidden internal applications behind the reverse proxy, which could lead to unauthorized access, data leakage, or further exploitation [3].
Secondly, this vulnerability could be a stepping stone for other attacks, including ransomware and APT group activities, given its potential to bypass access controls and perform actions that would otherwise be restricted.
Given the scale and severity of this issue, it is crucial for organizations to adopt a proactive stance to safeguard their operations and ensure the security of their vendor ecosystem. But how can you ascertain which of your vendors might be using vulnerable servers? Let’s explore this in the next section.
How Can You Identify Vendors Using Vulnerable Servers?
Identifying which of your vendors are using potentially vulnerable servers is a crucial step in managing this risk. Here, in-platform capabilities like those provided by Black Kite can greatly facilitate this process.
Black Kite customers have the ability to filter vendors using vulnerable servers via the CVE filtering feature found on the Company List page. Below is a step-by-step guide on how to utilize this feature within the platform:
- Navigate to the Company List page.
- Click on the Filter button.
- Select the CVE field and type ‘CVE-2023-25690’.
- Add any other filter options as needed.
- Click on the filter.
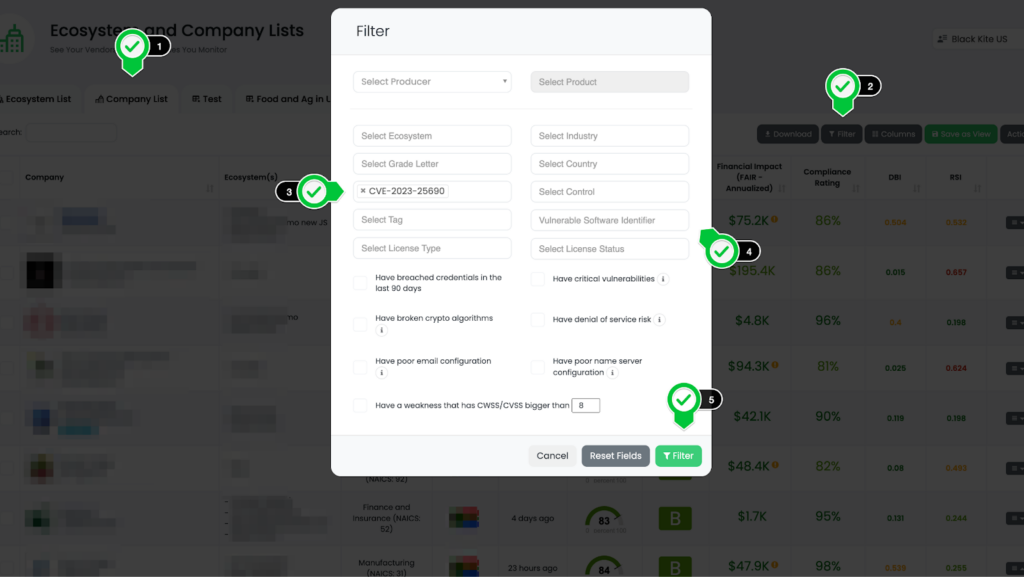
After executing these steps, the platform will display a list of companies that may be using vulnerable servers. For better prioritization, you can sort the results by various metrics, such as companies’ cyber rating, Cyber Risk Quantification (FAIR™) scores, or Ransomware Susceptibility Index™ (RSI™) scores.
This efficient identification process will allow you to better manage and mitigate the risks associated with this vulnerability in your vendor ecosystem.
Remediation and Recommendations
In dealing with the CVE-2023-25690 vulnerability, both from a self-risk and third-party risk management perspective, there are critical steps to follow.
Self-risk management:
- First and foremost, update your Apache HTTP Server. Apache has already provided a patch for this vulnerability in the 2.4.56 version. Applying this update will protect your server from the vulnerability [2].
- Regularly conduct vulnerability scanning. This practice will help in detecting any new vulnerabilities that could be present in your system. As CVE-2023-25690 showed, even widely trusted software like Apache HTTP Server can have vulnerabilities, and it’s crucial to stay updated.
- Provide training to your IT staff about the nature and impact of such vulnerabilities. Ensuring that your team understands the potential risks associated with software vulnerabilities can help in quickly identifying and mitigating them.
Third-party risk management:
- Utilize vendor risk management tools, like Black Kite, that can aid in identifying vendors who might be using vulnerable servers. Black Kite provides a CVE filtering capability allowing you to quickly isolate vendors who may be using Apache HTTP Server versions susceptible to this vulnerability.
- Engage in regular communication with your vendors about their cybersecurity practices. Make sure they’re aware of vulnerabilities like CVE-2023-25690 and the steps they need to take to address them. Encourage vendors to regularly update their software and conduct vulnerability assessments.
- Include cybersecurity standards in your vendor contracts. If it’s not already there, incorporate a clause requiring vendors to adhere to specific cybersecurity standards, including regular patching and updates.
While these steps can significantly reduce the risk, remember that cybersecurity is a continuous effort. With the evolving threat landscape, staying proactive and vigilant is key to ensuring the security of your business and vendor ecosystem.
Conclusion
In an increasingly interconnected digital ecosystem, the importance of robust cybersecurity measures cannot be overstated. Vulnerabilities like CVE-2023-25690 in the Apache HTTP Server underscore the potential risks that can arise from even the most trusted software. It’s not just an individual company’s risk but extends to the entire vendor ecosystem, highlighting the significance of comprehensive third-party risk management.
By staying proactive with updates, conducting regular vulnerability assessments, and leveraging advanced tools like Black Kite, businesses can significantly mitigate these risks. In doing so, they safeguard not only their own infrastructure but also contribute to a safer and more secure digital landscape for all.
As we continue to rely on technology and third-party services in our daily operations, the mutual understanding and joint effort in handling these vulnerabilities are crucial. CVE-2023-25690 is a timely reminder of this fact, providing an opportunity to re-evaluate and strengthen our cybersecurity measures.
Let us take it as a reminder that in our interconnected world, cybersecurity is not just an IT issue, but a business-wide responsibility that requires ongoing attention, investment, and vigilance.

