Cascading and Concentration Risk: How do they impact your digital supply chain?
Written by: Black Kite
By Haley Williams, from the perspective of Jeffrey Wheatman, Cyber Risk Evangelist
Within the world of third party risk, cascading and concentration risk have been the buzz of conversation as large events are frequently tied back to this explanation of risk. It is becoming increasingly important to actively manage and reduce vendor risk to maintain a healthy cyber posture in 2023.
What exactly is concentration risk?
In its most basic form, concentration risk is the concentration of value or assets in a single entity.
When it comes to concentration risk in the third-party space, the question you must ask your organization is this: “have we concentrated a particular critical service to a single vendor, creating a single point of failure?”
For example, customer service is considered a critical service to a company, and customer service workers rely heavily on call centers. In order for their concentration risk to be reduced, multiple call centers are utilized to fulfill the service. This might be outsourced global call centers, centers in various locations and time zones, etc. If only one call center was used, then full business failure would occur if that center went down.
The bottom line is: if you rely on one single vendor to provide a critical service and that vendor loses the ability to provide it, your operation is severely impacted.
This concept also applies to your larger supply chain. You might be aware enough to diversify your cloud providers, placing no more than 50% of critical business processes in a single provider. But imagine that nine of your ten most critical partners all use the same cloud provider company and trust 100% of their services to that provider? If that one provider or software company gets breached, goes down, etc, suddenly you are exposed to the same degree that your partners are exposed.
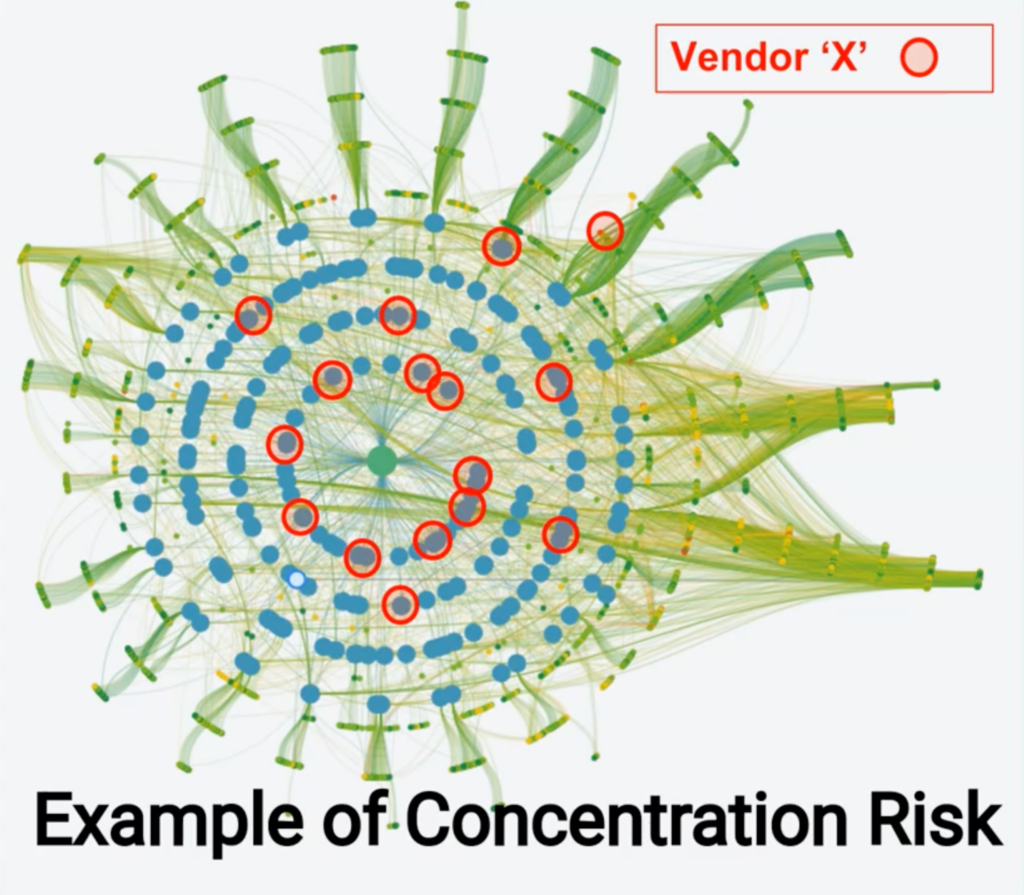
In this diagram, the intensity of concentration risk is visualized in a map of vendors across digital supply chains. Take Vendor X for example. The more frequently Vendor X appears in the map, the more concentrated the risk becomes on that particular vendor. While this may seem complex, an ecosystem that looks like this is quite common across medium/large organizations.
Deloitte explains it well: “Typically defined as the probability of loss likely to arise due to over-dependence on a single vendor, concentration risk is further exacerbated when such a vendor specializes in a specific industry. The more well-established these companies are, the more likely they are to have privileged access into networks that house extremely confidential and often classified information. They are part of the fabric and are inherently trusted. This makes them particularly tempting targets for sophisticated threat actors.”
What exactly is cascading risk?
Cascading risk is the chain of causality that emerges when risk and accumulated vulnerabilities connect to increase the chance of attack. In simpler terms, cascading risk is the domino effect that occurs when one vendor in a digital supply chain cascades risk and exposure to the rest of their connected vendors (including your organization) in the case of a cyber incident.
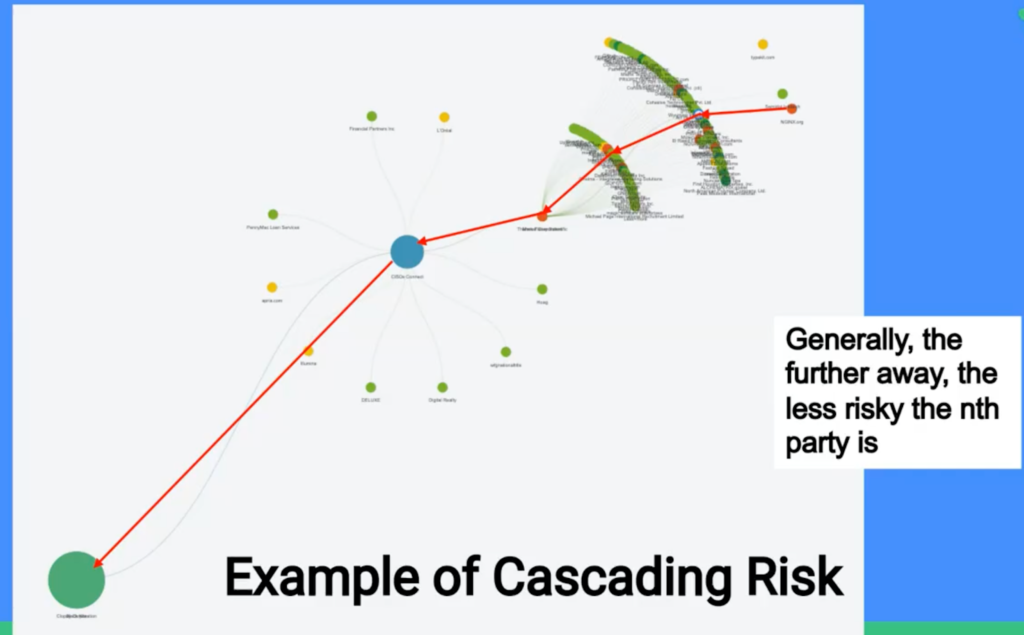
Take this visual for example, assuming your organization is the green circle on the bottom left. You do business with the blue circle to your right, and they do business with the orange circle to their right in the chart. Each individual vendor then shows a waterfall of 4th, 5th, 6th, nth, etc. parties to represent their ecosystem.
Now say that the blue circle has a cyber incident and they experience a data breach. Suddenly, that risk can cascade down the red line all the way to you, as well as towards every other vendor associated with the blue circle. As stated above, generally, the further away the vendor is from you directly, the less risk the party is. This is why 4th, 5th, and nth party risk monitoring is important in addition to merely third-party risk monitoring.
What’s the best practice to deal with this kind of risk?
In order to reduce concentration risk, many larger companies today will actually place particular departments/teams on different cloud providers, such as splitting up production, development and testing. That way if one ship goes down, the remaining fleet stays afloat. But what else can you do?
1. Have greater visibility – what does your expanded ecosystem look like?
One big step is to understand the elements of your ecosystem’s interconnectedness between vendors and companies. While the visual of a large and vast ecosystem may appear extremely complicated – it is actually quite typical. A big first action here is to work with an automated third-party risk monitoring program, like Black Kite, that can manage and organize your full vendor ecosystem in a short period of time, with room to scale and grow.
When you can monitor your third parties on a continuous basis, your team is able to see the points of failure and struggle for your most critical vendors (and the least critical ones). Perhaps patch management or stolen credentials are the biggest red flags for your vendors. You can then communicate with your vendors to begin to make important changes and improvements for the future.
2. Prioritize the most important vendors and understand where the biggest exposure gaps lie.
While it is essential to monitor and ensure the cyber health of all vendors is acceptable, everyone has to start somewhere. Beginning with selecting and prioritizing the most important partners to your business operation is a strong second step.
3. Start the conversation with a critical partner.
If one of your most important vendors is placing 100% of their data and services in the hands of only one or two providers, be willing to have a chat with them. Keeping the conversation open allows for improvement all around – your data and business operations become more secure, and so does the partner and their partners.
While the higher risk reliance on a single entity is easier to manage, the much harder to manage diversified process reduces risk tenfold. It may be a tradeoff, but it is a good one.
How does ransomware play into cascading risk?
In the last several years, ransomware has moved from merely locking up data for a ransom, to pulling the plug and shutting down an entire business. Now, threat actors are even going to the partners of a breached company and threatening them alongside the initially breached organization. And while losing data is impactful, losing business processes is truly the bigger issue, particularly for critical infrastructure.
When it comes to cascading risk, ransomware shutting down one vendor in an ecosystem or exposing data for one vendor can easily cascade down to your company, leaving your data vulnerable and interrupting successful operations.
As Kevin Mitnick put it, “You can never protect yourself 100%. What you do is protect yourself as much as possible and mitigate risk to an acceptable degree.” What you can do is assess the risk, make smart decisions, and invest in programs that further mitigate the discovered risk.
The best way to mitigate against ransomware threats is to stay aware. Black Kite is the only cyber risk rating platform with a ransomware indication tool. Using data and machine learning, Black Kite’s RSI™ discovers the likelihood that an organization will experience a ransomware attack, before the attack itself.
Know the likelihood of a ransomware attack to your organization by completing a Black Kite RSI™ assessment.
Claim Your Free RSITM Rating
