Manual. Inconsistent. Inefficient.
Static questionnaires and spreadsheets don’t cut it anymore. They miss risks, frustrate vendors, and drain your team’s time.

You can't afford blind spots when onboarding new vendors. One misstep can expose your organization to ransomware, data breaches, and compliance headaches. But today’s risk assessments are broken. They’re slow, generic, and out of sync with the pace of your business. It’s time for a better way to evaluate vendors.
Traditional cyber assessments take weeks to months. It doesn’t have to be this way.
Get fast, accurate risk insights that transform your vendor evaluation process.
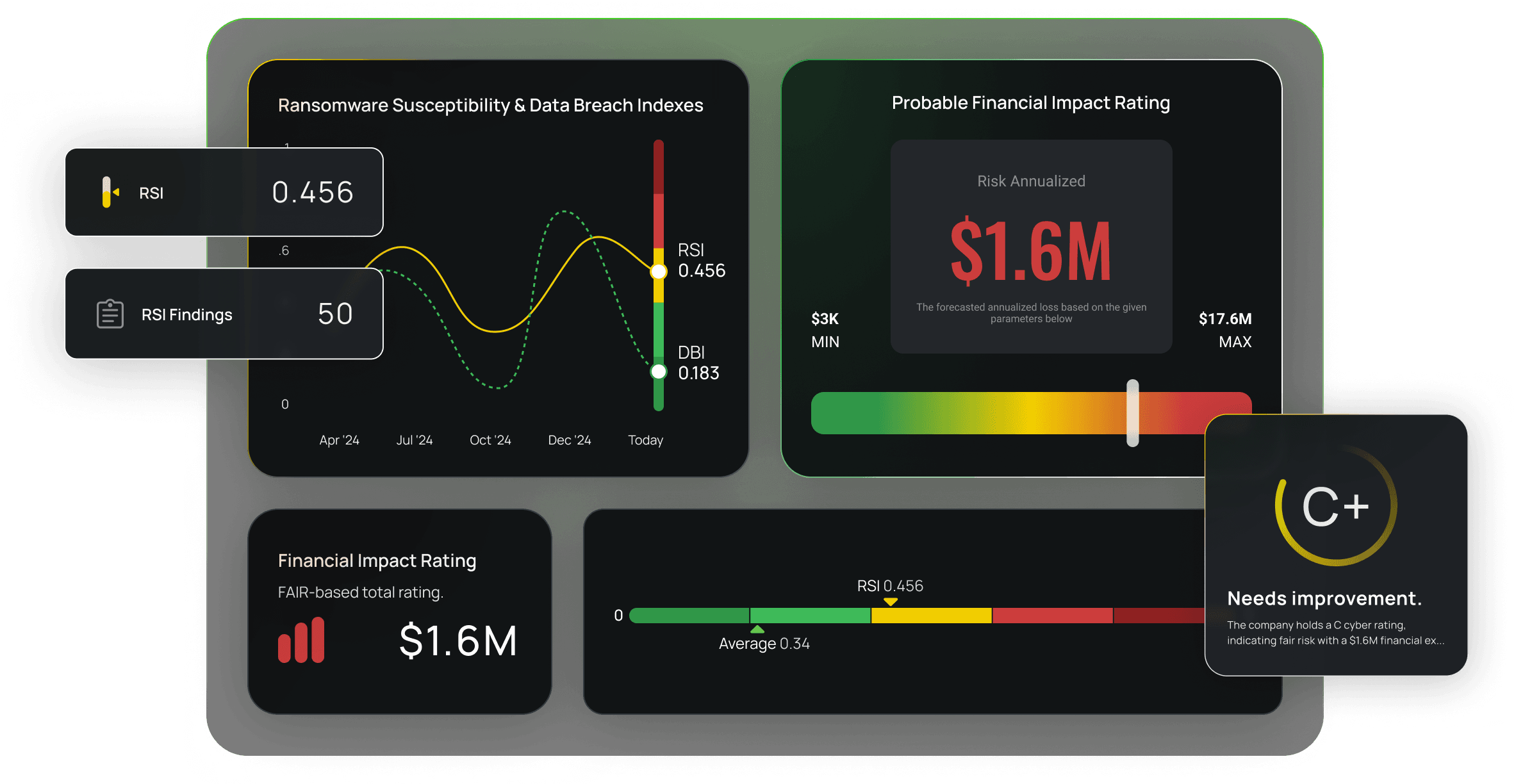
Make smarter decisions, faster. With Black Kite, you see each vendor’s true cyber risk backed by live threat data, not outdated self-reports.
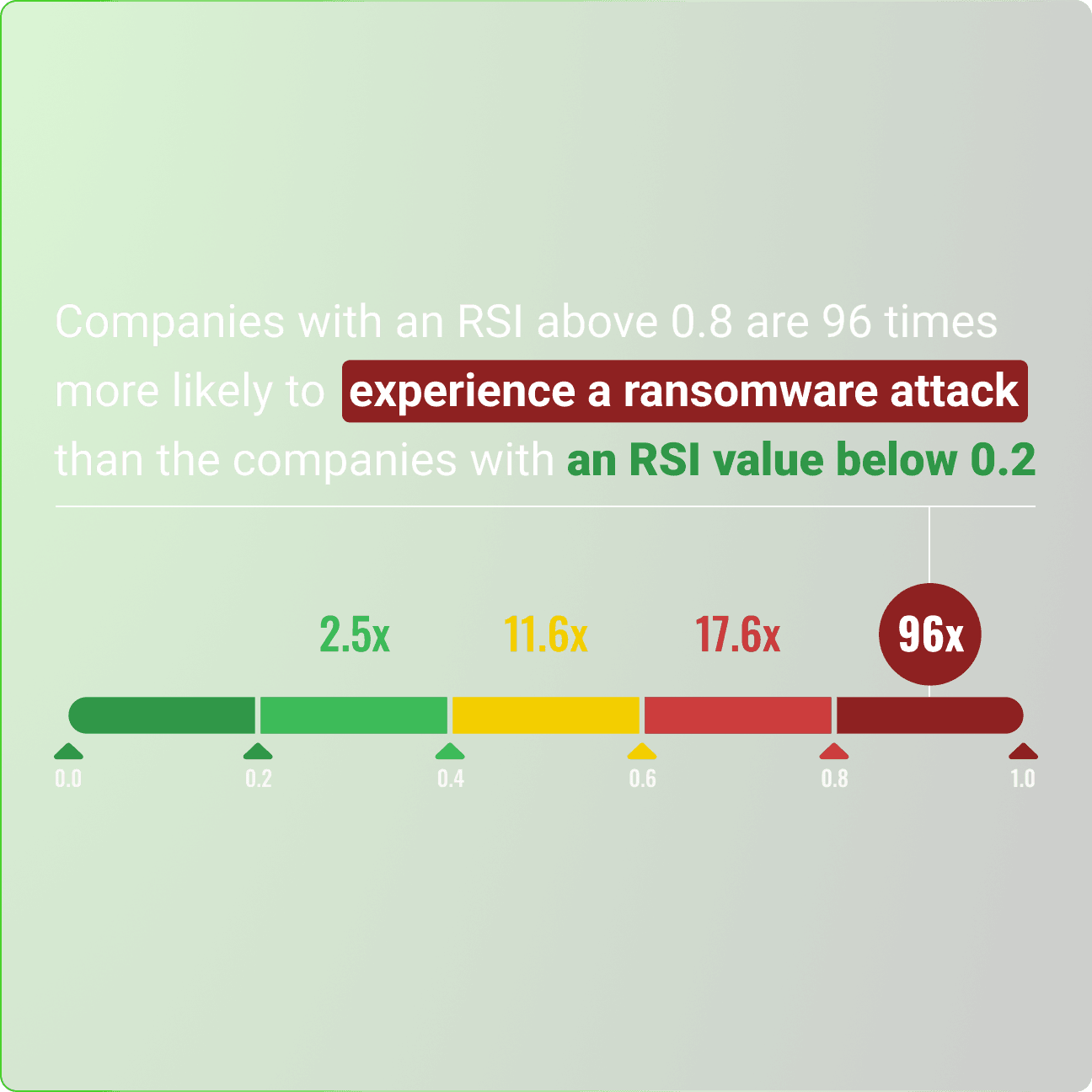
Ditch black-box scores. Black Kite uses open frameworks like NIST, MITRE, and CVSS to deliver ratings that are transparent, credible, and actionable.
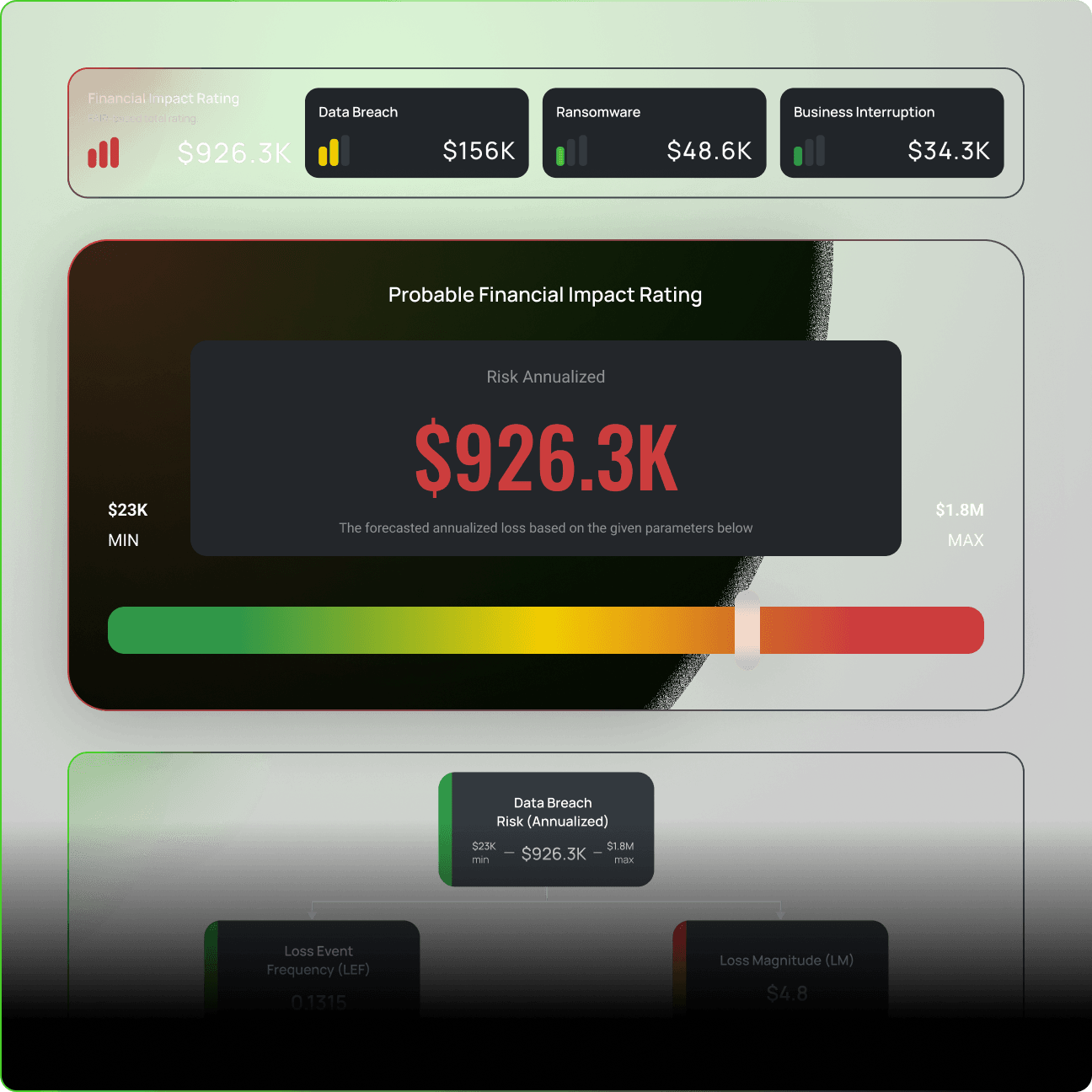
Translate cyber risk into probable financial impact using industry-standard Open FAIR™ modeling. Give execs the numbers they need to make smart decisions.
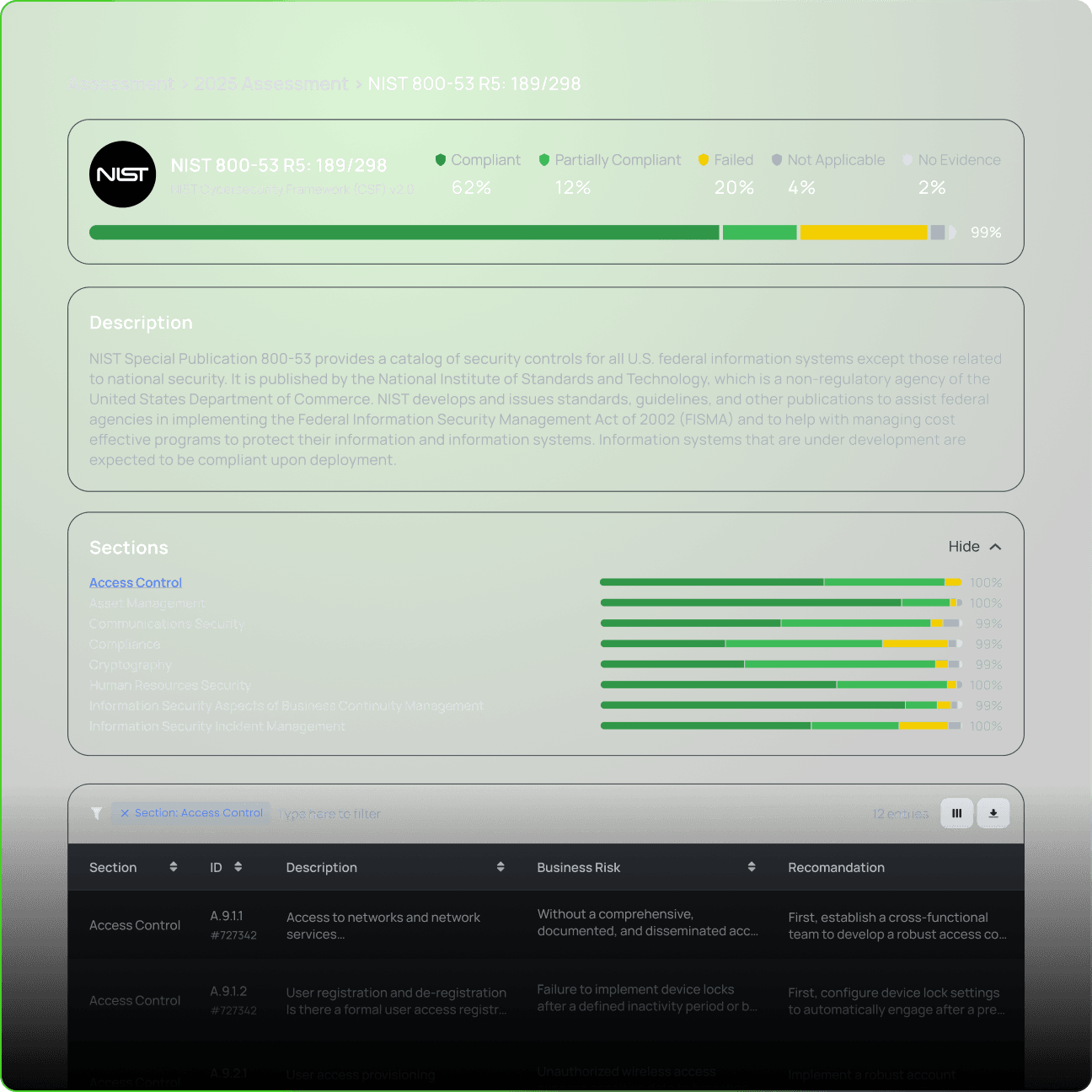
AI-powered document parsing analyzes security policies, SOC reports, and trust center artifacts in minutes, not weeks. Automatically map evidence to over 20+ global frameworks.
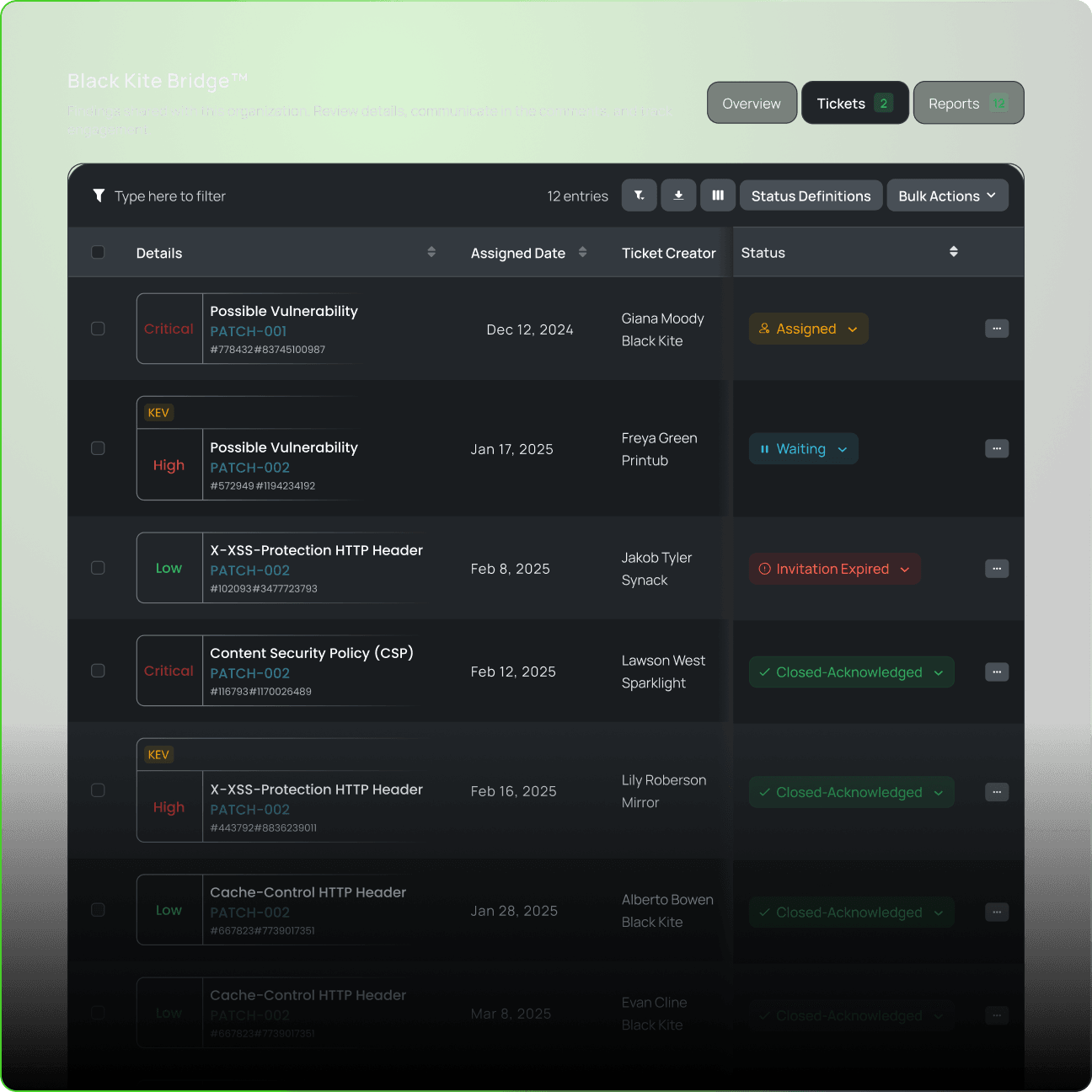
No more endless email threads. Use The Black Kite Bridge™ to share findings, assign actions, and track remediation all in one system.
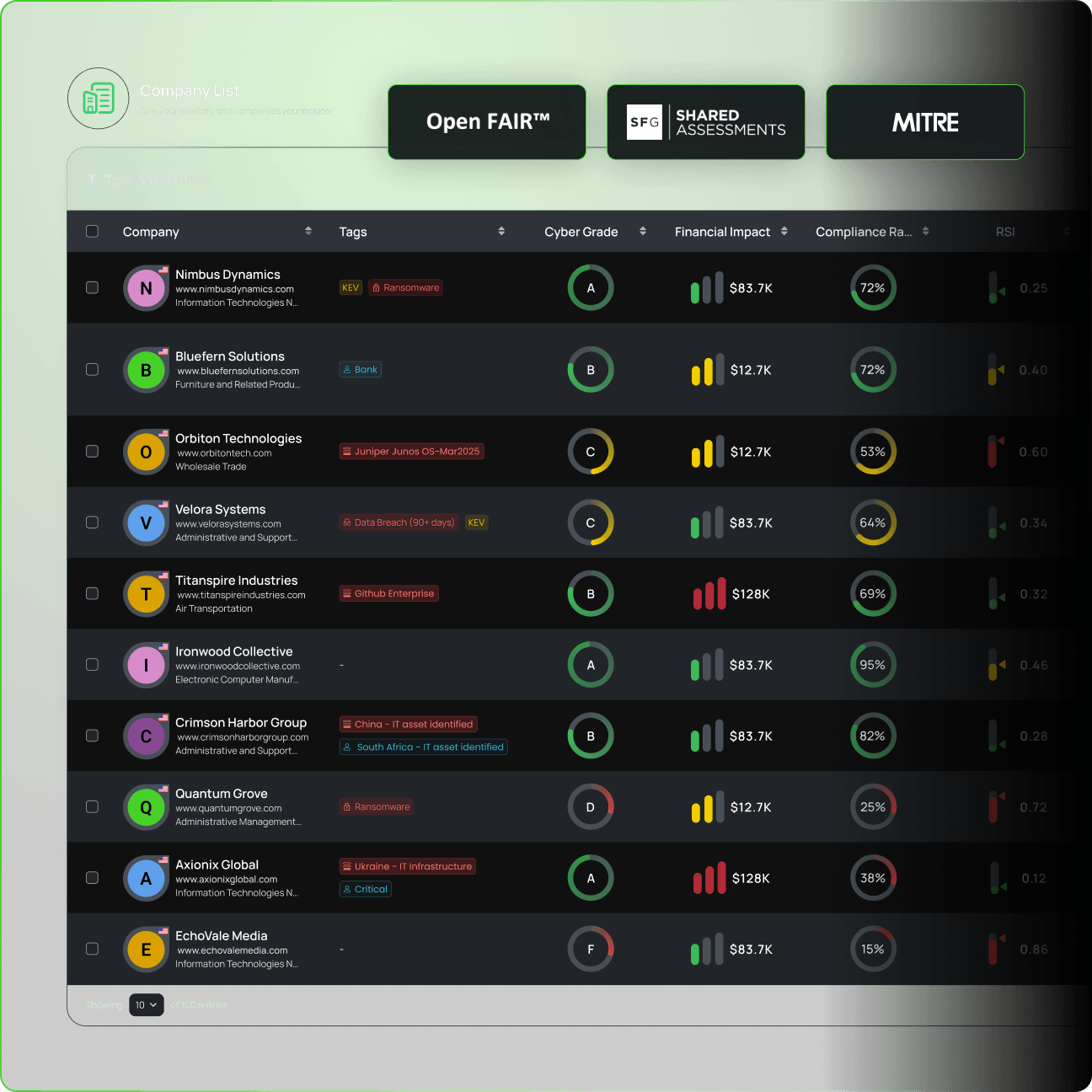
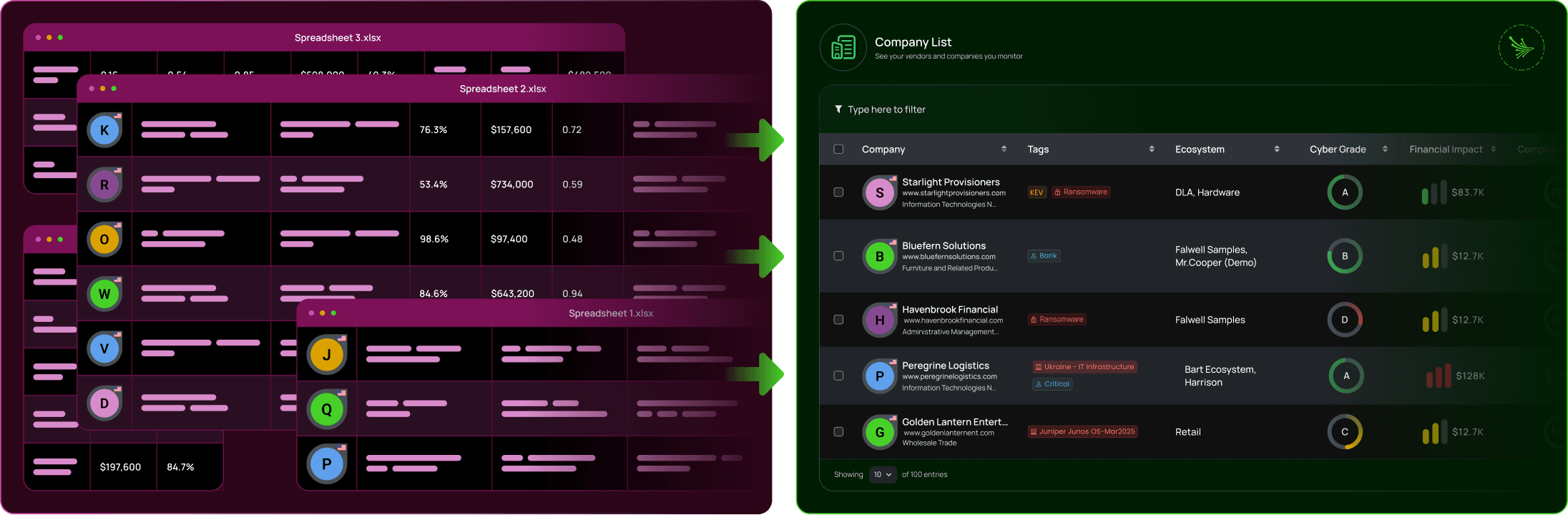
Build and maintain a clean vendor inventory. Store documentation, assessments, and compliance artifacts in one searchable workspace.
– Jennifer Blackburn, Sr. Cybersecurity Analyst, University of Kansas Health System

Join companies that use Black Kite to evaluate cyber risk up front and onboard vendors with confidence.