Do GRC Requirements Truly Reduce Risk?
Written by: Black Kite
By Haley Williams, from the perspective of Black Kite CSO, Bob Maley
GRC, or governance, risk, and compliance, are concepts that have been implemented in the business setting for quite some time, particularly in information security and information technology fields.
In 2007, the official GRC system was fully formed as an integrated practice. The goal of GRC is to assist in an enterprise’s efforts of meeting governmental requirements and maintaining proper risk posture, bringing all departments together rather than keeping them separate. It predates third-party risk management, as most TPRM before GRC was procurement oriented.
The Three Elements of GRC
Governance
“The set of rules, policies, and processes that ensures corporate activities are aligned to support business goals. It encompasses ethics, resource management, accountability, and management controls.”
Risk, or Risk Management
“The process of identifying, assessing, and controlling financial, legal, strategic, and security risks to an organization. To reduce risk, an organization needs to apply resources to minimize, monitor, and control the impact of negative events while maximizing positive events.”
Compliance
“Involves adhering to rules, policies, standards, and laws set forth by industries and/or government agencies. Failing to do so could cost an organization in terms of poor performance, costly mistakes, fines, penalties, and lawsuits.”
According to IBM, “GRC’s set of practices and processes provides a structured approach to aligning IT with business objectives. GRC helps companies effectively manage IT and security risks, reduce costs, and meet compliance requirements. It also helps improve decision-making and performance through an integrated view of how well an organization manages its risks.”
Third Party Risk Management vs Compliance
When banks started adding third party after third party, federal regulators became more involved, encouraging the practice of third-party risk management (TPRM) within GRC. Though it is called third-party risk management, the process I most frequently observe is more like third-party compliance.
Risk management involves looking at some type of scenario. For instance, with Black Kite’s FAIR component, we are looking at the scenario of, “what is the probable financial impact to XX company if XX vendor is used to process data and a cyber breach occurs.” In that assessment, Black Kite accumulates data in a way that allows for risk to be quantified to a dollar amount.
A compliance based “TPRM” program looks a bit different. Instead of a scenario analysis or assessment, vendors are merely sent spreadsheets with 100+ questions mapped back to a framework. Once that data is received, the vendor is then determined to be compliant or not with that particular framework. Based on that yes or no, a qualitative, rather than quantitative, decision, is made. We assume that, if they are compliant, their risk must be lower.
Does Compliance Equal Risk Reduction?
That’s actually where most mistakes are made in third-party risk management: Assuming third-party compliance is equivalent to third-party risk reduction. Newsflash, it’s not.
These underlying problems are one of the contributing factors, amongst many, to increases in loss, breaches, and unawareness of risk level.
Sometimes compliance is more of a contractual function, rather than a regulatory requirement. It might be a data-security standard like PCI-DSS. Even meeting regulatory requirements is more compliance work than a true risk assessment. That is the main disconnect within GRC and risk management. Compliance is still extremely important, however it is not equal to risk reduction. A true risk assessment has to be done through the gathering of information.
Tiering vendors is additionally not equivalent to risk reduction. Tiering is merely classification. Typically, best practices have always called for this behavior, but these methods are overwhelming, difficult to manage, and ineffective. People tend to want to start with classification-based models, with tier 1, 2, and 3 vendors, etc. But risk in this model is not clearly defined.
Day to day activities in a GRC program or vendor risk management (VRM) program are often merely processes to check a box: compliance-focused actions. It is but a leap of faith to believe that a compliant company is a low-risk company.
Risk Assessments Bridge the Gap Between Hope and Confidence
True risk assessments aren’t easy. They aren’t just boxes you check absent-mindedly. They are thorough processes that take effort, time, and a large amount of data. They take knowledge and expertise. An expert guess or opinion on the likelihood of a cyber event is not sufficient anymore. Especially when the average cost of a data breach is $15 million.
Risk assessments generate enough information to allow an educated decision maker to have the confidence to make a decision regarding risk. Perhaps this facilitates the action of adding an extra control, or reducing the level of shared data access a vendor receives. At Black Kite, this is shared in the form of a Strategy Report.
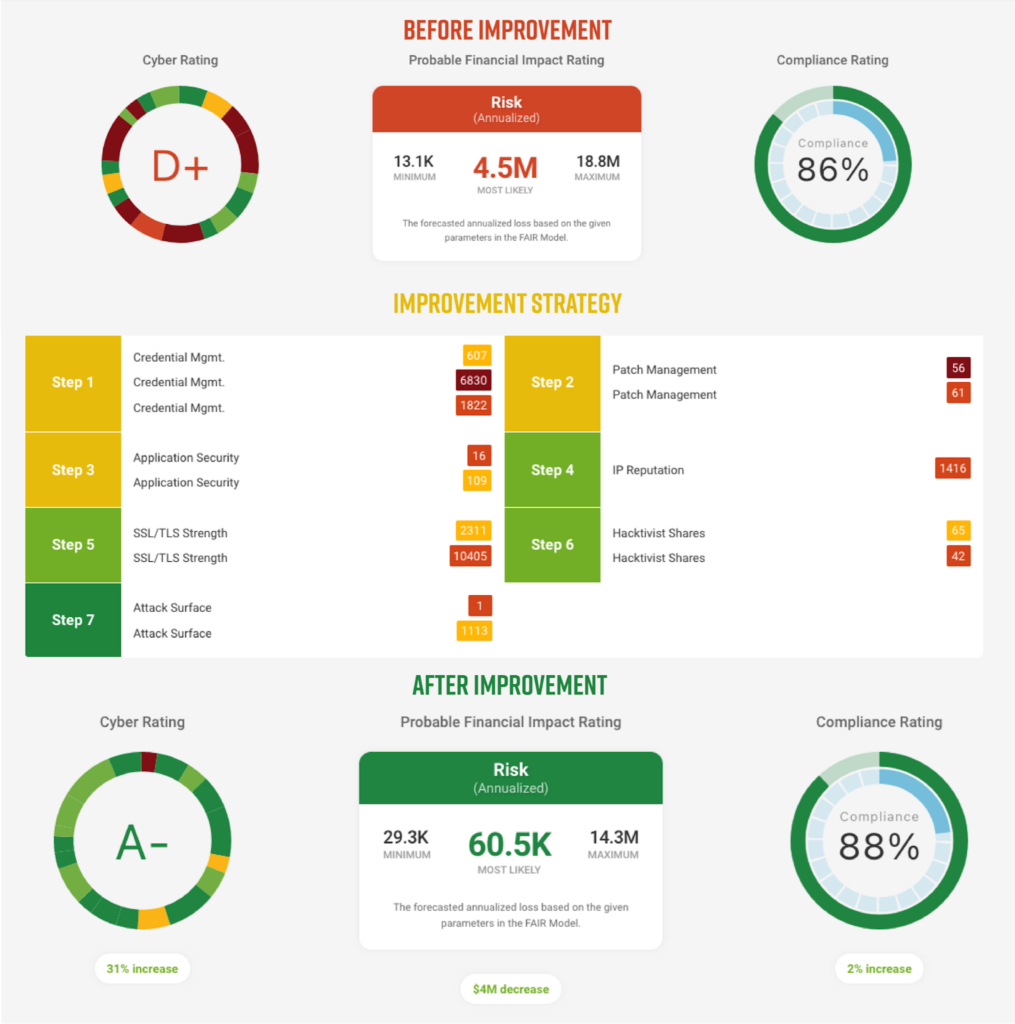
There will always be risk involved. It has always been about reducing risk rather than removing it. Reduce your risk for your business – don’t merely complete a compliance check list..
Free Risk Assessment™ Report
