Windows CVE-2021-40444 MSHTML zero-day bug is finally fixed: Organizations and their software supply chain vendors must patch ASAP
Written by: ceren
Written by Ferhat Dikbiyik
Edited by Haley Williams
The Update
The Windows CVE-2021-40444 MSHTML remote-code execution vulnerability is being widely discussed and several PoCs have been released, validating exploits in the wild. Initially, on September 7, 2021, Microsoft recommended a mitigation but threat actors were able to bypass this motion and cybersecurity researchers confirmed its ineffectiveness. On September 14, 2021, a week after the vulnerability surfaced, Microsoft finally published a fix. It’s imperative for organizations and their supply chain vendors to patch this vulnerability as soon as possible to avoid cyber attacks.
The impact of not patching this vulnerability
The remote-code execution vulnerability, tracked as CVE-2021-40444, was found in the Microsoft Office Internet Explorer browser rendering engine, MSHTML. The Microsoft advisory states that the vulnerability impacts Windows 8.1 through Windows 10 and Windows Server 2008 through Windows Server 2019. The vulnerability severity level is 8.8 out of 10.0 (CVSSv3).
The Windows versions impacted by the vulnerability are widely used by corporate networks and their employees. If not patched, threat actors can generate malicious Office and RTF documents, as well as CAB files to remotely execute commands on a target system. A victimized remote worker who uses Windows 10, or a vendor who uses Windows 2008 R2, may cause a data breach and/or a ransomware attack by simply opening a Word document.
The first mitigation recommendation posted by Microsoft should have worked by blocking document previews in Explorer as well as ActiveX controls. However, both researchers and threat actors published proof-of-concepts on how to bypass the mitigation by modifying the exploit without using ActiveX control.
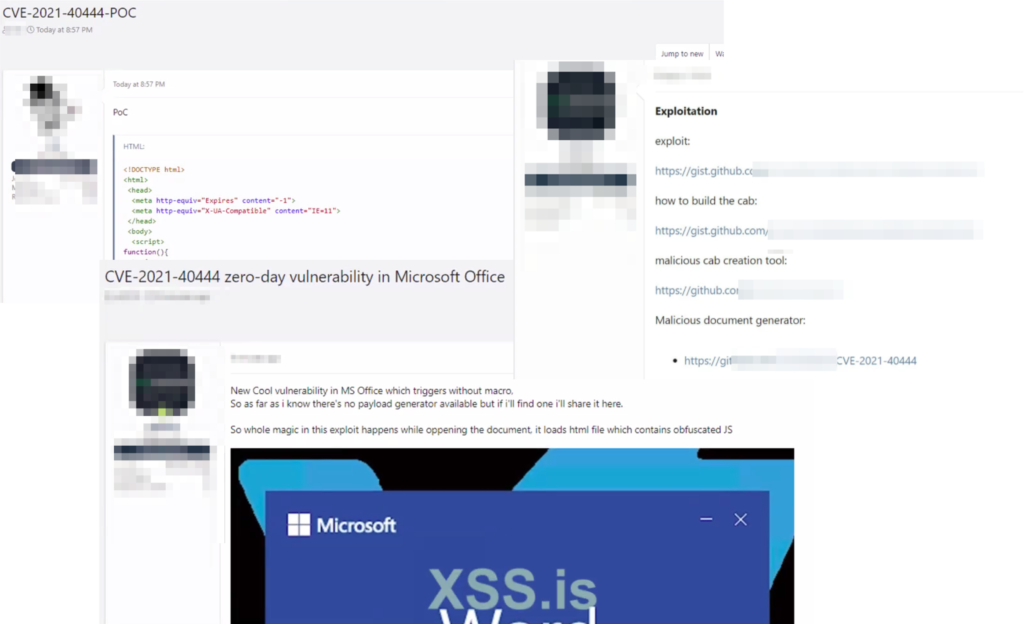
The Black Kite Research Team monitored hacker forums for PoCs for this bug and saw that PoCs spread very quickly as well as several threat actors were able to replicate the PoCs to weaponize the vulnerability. Below are some of the posts from hacker forums.
How to patch
Companies that have vulnerable products in use should download and install the security update published by Microsoft ASAP. The security update includes a Monthly Rollup for Windows 7, Windows Server 2008 R2, and Windows Server 2008. Microsoft states that “Customers who apply the Monthly Rollup do not need to apply the IE Cumulative update.”
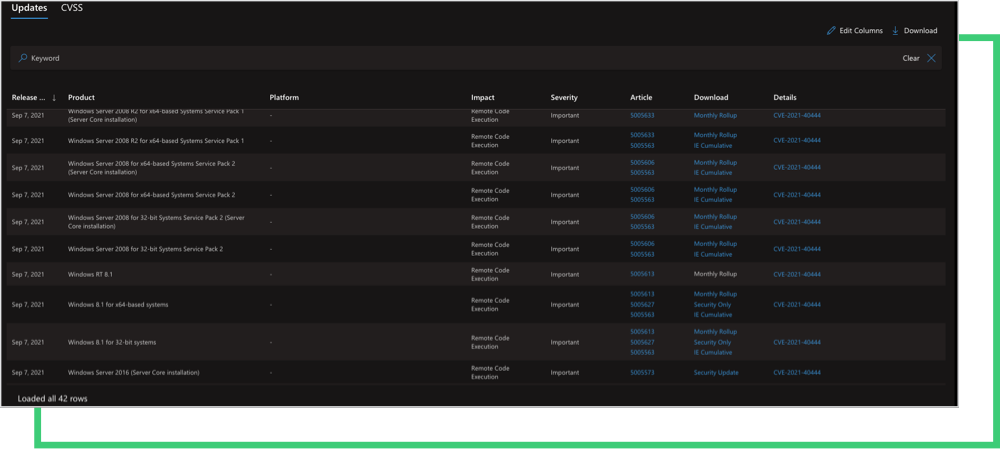
If you or your vendor(s) are not able to immediately apply the security update, you must quickly apply the workaround recommended by Microsoft to mitigate risk.
How to Discover Vendors at Risk
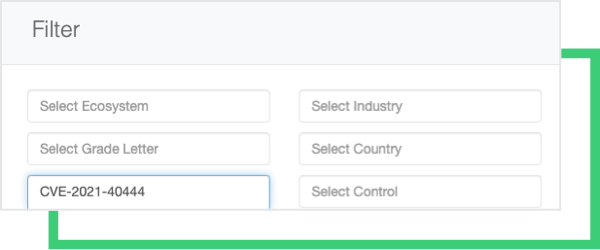
Once the CVE-2021-40444 MSHTML vulnerability is available on the NIST National Vulnerability Database, Black Kite customers can use the platform’s ecosystem page to filter on vendors who might have this vulnerability.
In Black Kite’s 6-12 month product roadmap, customers will soon be able to search what products their vendors utilize, as well as filter specific product versions in order to be better informed about the security of their supply chain.
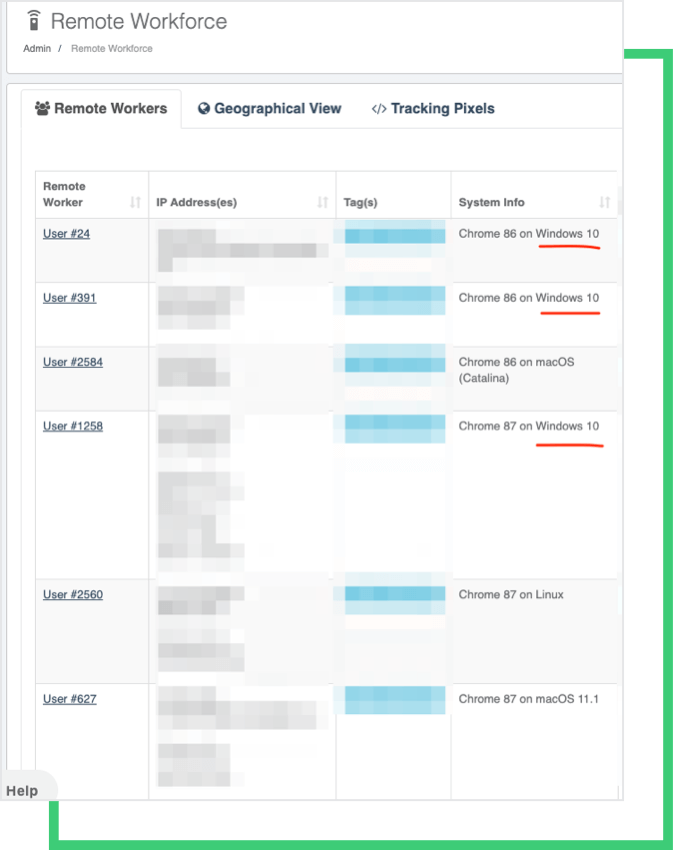
Black Kite customers who use the Remote Workforce module can also see remote workers who are using the impacted system.
This ability to monitor vendors’ vulnerability exposure enables Black Kite customers to take immediate and necessary action. This capability should be integral to any supply chain risk management plan.
Interested in understanding which of your third-party vendors is at risk?

