3CX Supply Chain Attack: The Risks and How to Protect Yourself
Written by: ceren
Written by Ferhat Dikbiyik
Additional Contributors Yavuz Han and Ekrem Celik
Edited by Haley Williams
Updated on April 6, 2023, with more information about Lazarus’s related attacks, CVE assignment of MITRE, and alerts by CISA
Update on the threat actor behind the attack and their campaign on cryptocurrency companies using 3CX DesktopApp
Now, it is widely accepted that North Korean APT Group Lazarus is behind the attacks. The group has also been linked to a recent supply chain attack that targeted cryptocurrency companies related to vulnerability on 3CX DesktopApp. The attack exploited a vulnerability in the 3CX DesktopApp to install a malicious DLL on the victim’s computer, which then downloaded and installed the Gopuram backdoor. This modular backdoor can steal data, install additional malware, and interact with the victim’s computer.
The Lazarus Group is a well-known and sophisticated hacking group that has been associated with a number of high-profile attacks, including the WannaCry ransomware attack and the Sony Pictures hack. Known for its advanced techniques, such as supply chain attacks, the group is believed to be sponsored by the North Korean government.
The recent attacks on cryptocurrency companies highlight the seriousness of the threat posed by the Gopuram backdoor. To protect themselves from such attacks, organizations should take steps such as using strong passwords, keeping software up to date, and using a firewall.
Updates on MITRE
MITRE has assigned CVE-2023-29059 to the 3CX supply chain attack linked to CWE-506 for Embedded Malicious Code. This enables organizations to track and manage vulnerability and threat exposure.
Updates on CISA advisory
CISA also published an alert on March 20, 2023, about the 3CX supply chain attack. The alert recommends uninstalling the 3CX DesktopApp and switching to the PWA client.
BREAKING NEWS. News has just emerged about the discovery of “Smooth Operator,” a massive supply chain attack that has infiltrated tens of thousands of companies via a popular voice and video conferencing software product. It is categorized as a Private Automatic Branch Exchange (PABX) platform, known as 3CX DesktopApp. Identified only yesterday (March 29, 2023), this infostealer malware is now recognized as one of the largest recent supply chain attacks, posing unprecedented security risks for businesses and raising concerns about the integrity of their third-party vendors.
This incident has the potential to cause a ripple effect of data breaches across the vendor ecosystem, significantly disrupting organizations’ operations. In light of these revelations, it is crucial for organizations to quickly identify vendors that may be using 3CX DesktopApp and engage with them to mitigate cyber risk associated with this alarming threat. This article aims to provide valuable insights on how to address this challenge and effectively safeguard businesses from the widespread impact of the Smooth Operator campaign.
Smooth Operator: Infostealer Targets 3CX DesktopApp
The cybersecurity community is currently buzzing with numerous technical articles and analyses on the breaking news of the Smooth Operator infostealer. In this section, we provide a concise summary of the key discoveries, insights shared by various security vendors, and indicators raised by concerned customers.
Discovery Timeline and Vendor Statements
On March 29, 2023, multiple vendors released advisories concerning an ongoing campaign that trojanizes the 3CX DesktopApp in a large-scale supply chain attack. The issue initially surfaced on CrowdStrike’s Reddit channel before being published on their website. SentinelOne and Sophos subsequently provided their insights on the unfolding situation. Notably, some customers on 3CX’s forums reported receiving alerts from their A/V vendors as early as March 22, indicating malicious activity detected by SentinelOne, Palo Alto Networks, CrowdStrike, ESET, and SonicWall security providers.
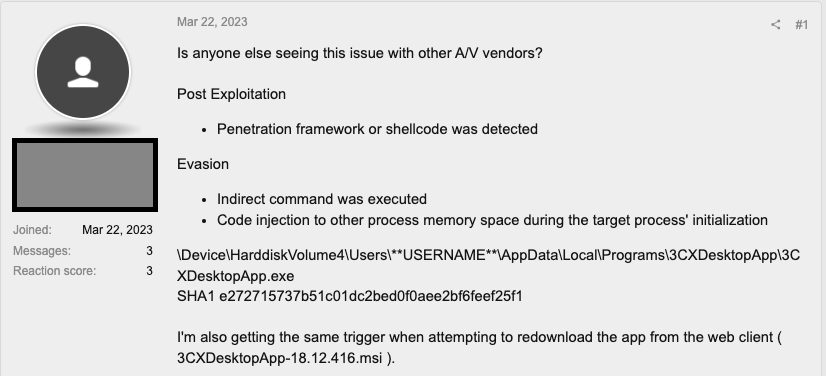
CrowdStrike: The malicious activity reported includes beaconing to threat actor-controlled infrastructure, the deployment of second-stage payloads, and hands-on-keyboard activity in a few cases. CrowdStrike suspects nation-state involvement by the threat actor LABYRINTH CHOLLIMA and states that the malware targets both Windows and MacOS operating systems.
Sophos:According to Sophos, only the 3CX client on Windows machines appears to be currently compromised. The malware is also capable of stealing sensitive information from web browsers.
SentinelOne: Dubbed as “Smooth Operator” by SentinelOne, the attack begins when the MSI installer is downloaded from the 3CX website or when an update is pushed to an existing desktop application. The malware primarily targets the Windows operating system.
What is 3CX DesktopApp?
3CX DesktopApp is a software-based PBX (private branch exchange) solution designed for businesses, offering VoIP (Voice over Internet Protocol) services that enable users to make and receive phone calls via the internet. This approach provides cost savings on phone bills and enhances flexibility. The app, available for Windows, Mac, and Linux operating systems, integrates with the 3CX PBX system and includes features like call forwarding, call transfer, voicemail, and a chat function for instant messaging among users on the same PBX. Widely used across the industry, 3CX supports a variety of VoIP phones and headsets and can also utilize a computer’s built-in microphone and speaker.
Details of the Smooth Operator Attack
The Smooth Operator attack commences when the 3CX desktop application is installed from the website or when an existing application is updated. For Windows OS, the process begins with 3CXDesktopApp.exe loading the ffmpeg.dll file. Next, ffmpeg.dll reads and decrypts the encrypted code from a second .dll file, d3dcompiler_47.dll. This multi-stage infection process allows the malware to remain stealthy and evade detection by many security solutions.
Following this, the malware downloads icon files from a GitHub repository, appending Base64 encoded strings to the end of the images. Using legitimate hosting platforms like GitHub helps blend malicious traffic with normal traffic, making it more difficult for security systems to identify and block the threat.
In the final stage of the attack, the malware exhibits an info-stealing function. It can harvest system information, such as hardware and software configurations, network settings, and user account details. It can also steal data and stored credentials from user profiles of browsers such as Chrome, Edge, Brave, and Firefox. Threat actors can use this information for various malicious activities, including identity theft, financial fraud, and targeted spear-phishing campaigns.
As part of its attack routine, the malware communicates with server addresses specified in the risk indicators (IOCs) list. We provide the list of IOCs at the end of the article.
Supply Chain Risk from the Smooth Operator Attack
The Smooth Operator attack highlights the significant supply chain risk that organizations face due to the interconnected nature of today’s digital ecosystems. In this section, we discuss the potential implications of the attack on the supply chain and the importance of understanding and managing these risks.
- Third-party dependencies: Many businesses rely on third-party software and services like 3CX DesktopApp to support their operations. A compromise in the security of one of these applications can have a cascading effect, potentially affecting not only the directly impacted organization but also its partners, customers, and suppliers. The Smooth Operator attack serves as a reminder of the importance of assessing the security posture of third-party providers and understanding the potential risks that can arise from these dependencies.
- Wide-ranging impact: As the 3CX DesktopApp is widely used across various industries and sectors, the attack’s scope is extensive. The infostealer can potentially access sensitive data from numerous organizations and their customers, leading to a significant risk of data breaches, financial losses, and reputational damage.
- Increased complexity: Supply chain attacks, like the Smooth Operator campaign, are often more complex and challenging to detect and mitigate than traditional attacks. They exploit trusted relationships between organizations and their vendors, making it difficult for security solutions to discern malicious activities from legitimate ones.
- Business continuity risks: A successful supply chain attack can disrupt an organization’s operations and those of its partners. As a result, businesses must proactively identify and address supply chain risks to ensure continuity in the face of such threats.
Mitigation Strategies for Smooth Operator Attack and Supply Chain Risk
To effectively respond to and mitigate the risks posed by the Smooth Operator attack and related supply chain threats, organizations should consider implementing the following recommendations for both internal security and vendor management:
Internal Security Measures
- Stop using the vulnerable version: Organizations that may be affected by the Smooth Operator attack should cease using the compromised version of the 3CX DesktopApp immediately.
- Apply patches or workarounds: If patches or mitigation workarounds are available, organizations should apply them as soon as possible to reduce the risk of exploitation.
- Uninstall/Reinstall the app: According to 3CX’s Founder and CEO, the best course of action for affected organizations is to uninstall and reinstall the compromised application.
- Use alternative solutions: 3CX strongly recommends using a Progressive Web App (PWA) client as an alternative until the release of a new, secure build of the desktop app.
Mitigating Supply Chain Risk
- Vendor risk assessment: Organizations should perform thorough risk assessments of their vendors, focusing on their security posture and potential exposure to the Smooth Operator attack. This includes evaluating their use of 3CX DesktopApp and other potentially vulnerable software.
- Communication and collaboration: Establish open lines of communication with vendors to share information about potential threats, vulnerabilities, and best practices. Encourage vendors to notify your organization promptly if they suspect they have been affected by the Smooth Operator attack or similar incidents.
- Monitor vendor activity: Implement ongoing monitoring of vendors’ activities and the security of their systems. This includes regularly reviewing their security policies and practices, assessing their compliance with industry standards and regulations, and monitoring their network traffic for signs of malicious activity.
- Diversify your vendor portfolio: Consider diversifying your vendor portfolio to reduce the risks of relying on a single provider (concentration risk.) This can help mitigate the impact of a vendor compromise and increase your organization’s overall resilience to supply chain attacks.
- Implement contractual safeguards: Organizations should include contractual provisions that require vendors to maintain an appropriate level of security, including monitoring and reporting requirements. This can help ensure that vendors actively manage their risks and promptly notify your organization of any incidents.
The Smooth Operator attack highlights the significant risks associated with supply chain attacks and the importance of managing these risks effectively. By implementing these recommendations, organizations can reduce their exposure to threats, enhance their security posture, and ensure business continuity in the face of evolving cyber threats.
Identifying Vendors Potentially Exposed to Smooth Operator Attack
Identifying vendors that use 3CX DesktopApp can be challenging, especially given the wide-ranging impact of the Smooth Operator attack. However, Black Kite has developed a unique solution called FocusTags™ to help organizations identify potential risks associated with their vendors.
As a vendor risk intelligence solution, the Black Kite platform, by using OSINT sources, automatically tags companies with a publicly visible 3CX Phone System Management Console, indicating the potential use of 3CX DesktopApp. By filtering vendors based on this tag, our customers can quickly identify which vendors may be at risk of exposure to the Smooth Operator attack or similar incidents.
As the only vendor risk intelligence company providing this level of insight, we offer a critical tool for organizations looking to proactively manage their supply chain risks. Black Kite allows customers to focus their risk management efforts where it matters most, ensuring they can respond quickly and effectively to evolving cyber threats.
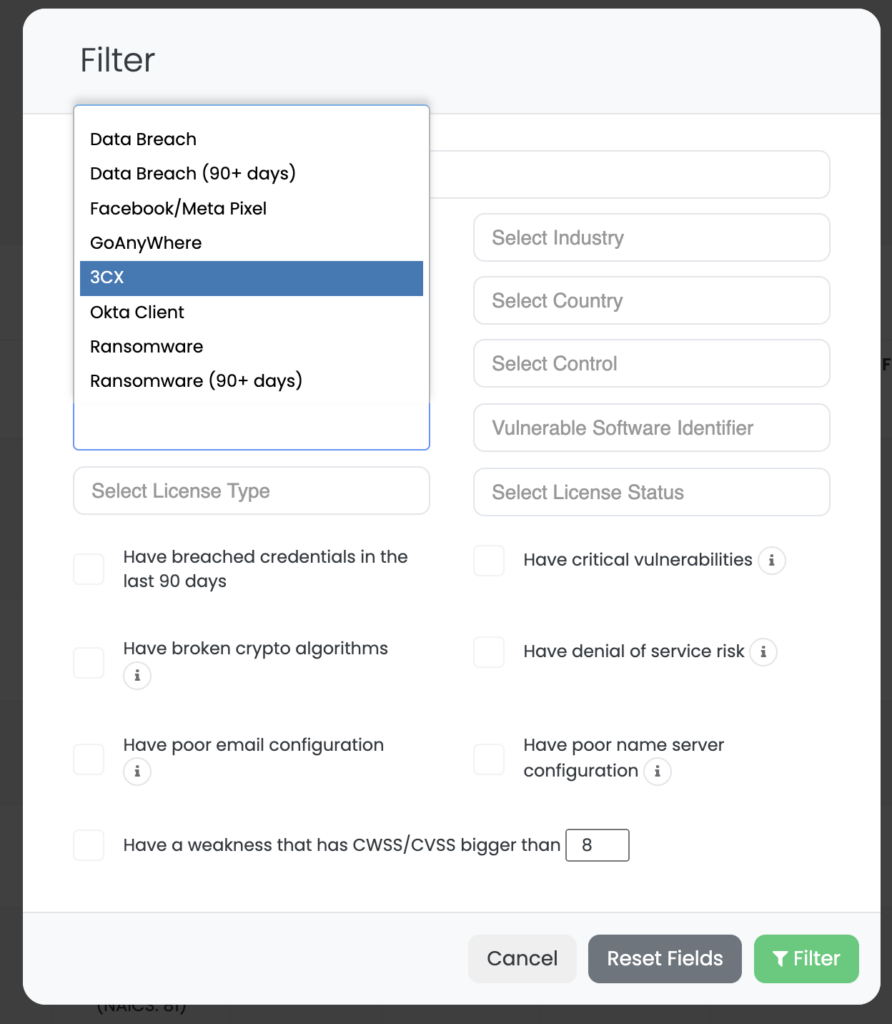
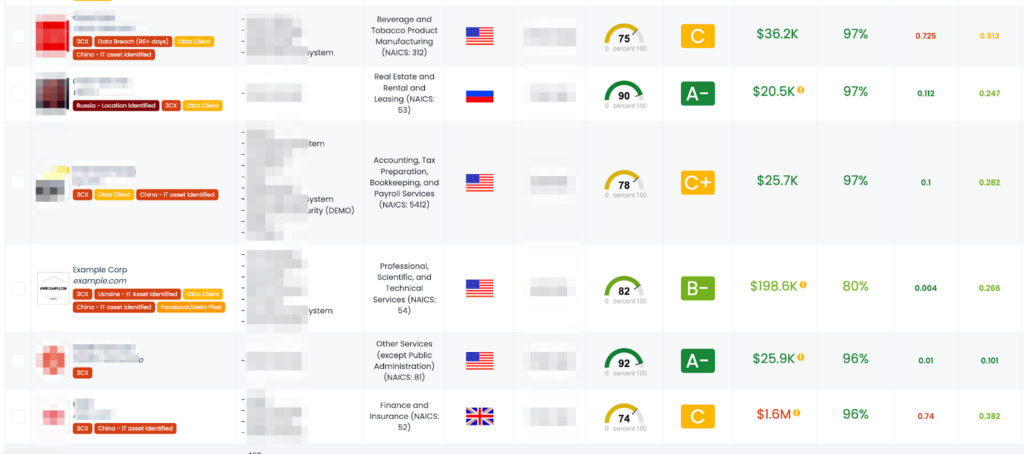
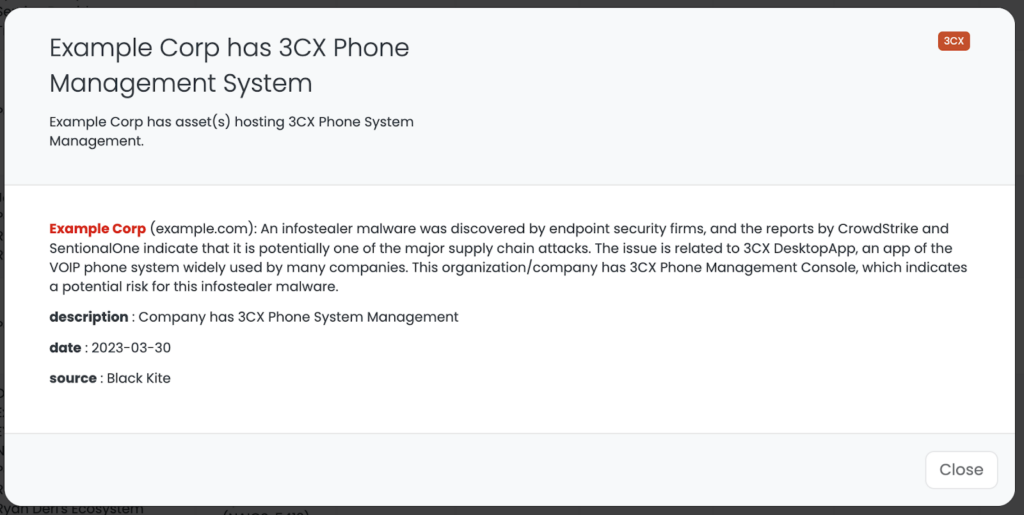
By leveraging the Black Kite platform, organizations can gain a more comprehensive understanding of their supply chain risks and take the necessary steps to protect their business continuity, reputation, and the bottom line.
Conclusion
The Smooth Operator attack highlights the growing threat posed by supply chain attacks and the need for effective risk management strategies to protect against them. The attack on 3CX DesktopApp can potentially affect tens of thousands of organizations, underscoring the need for swift and decisive action to mitigate the risks posed by this threat.
In this article, we have concisely summarized the key discoveries and insights shared by various security vendors regarding the Smooth Operator attack. We have also discussed the potential impact of this attack on organizations’ vendor ecosystem and provided recommendations for mitigating these risks.
Black Kite offers a unique solution for identifying vendors potentially exposed to the Smooth Operator attack. By leveraging our solution, organizations can gain critical insight into their supply chain risks and take the necessary steps to protect against this threat.
Coupled with the implementation of these recommendations, Black Kite can provide organizations with the ability to proactively manage their supply chain risks and put business needs first.
IoC list regarding the Smooth Operator campaign that trojanized 3CX DesktopApp
URL github[.]com/IconStorages/images
Email cliego.garcia@proton[.]me
Email philip.je@proton[.]me
SHA-1 cad1120d91b812acafef7175f949dd1b09c6c21a
SHA-1 bf939c9c261d27ee7bb92325cc588624fca75429
SHA-1 20d554a80d759c50d6537dd7097fed84dd258b3e
URI https://www.3cx[.]com/blog/event-trainings/
URI https://akamaitechcloudservices[.]com/v2/storage
URI https://azureonlinestorage[.]com/azure/storage
URI https://msedgepackageinfo[.]com/microsoft-edge
URI https://glcloudservice[.]com/v1/console
URI https://pbxsources[.]com/exchange
URI https://msstorageazure[.]com/window
URI https://officestoragebox[.]com/api/session
URI https://visualstudiofactory[.]com/workload
URI https://azuredeploystore[.]com/cloud/services
URI https://msstorageboxes[.]com/office
URI https://officeaddons[.]com/technologies
URI https://sourceslabs[.]com/downloads
URI https://zacharryblogs[.]com/feed
URI https://pbxcloudeservices[.]com/phonesystem
URI https://pbxphonenetwork[.]com/voip
URI https://msedgeupdate[.]net/Windows

