Ransomware Agents Unite to Disrupt U.S. Operations
Written by: ceren
Written by Ferhat Dikbiyik
Edited by Haley Williams
After the Colonial Pipeline attack and other major supply-chain attacks, the U.S. federal government took firm action to halt ransomware operations worldwide. However, the attempts and dialogues between countries that took place seem to only have slowed down ransomware operations temporarily. These days, ransomware actors are starting to join forces and target U.S. companies. So, what is the security posture of some of these companies, specifically their susceptibility to a ransomware attack? Let’s take a look at Black Kite’s findings.
How did it all start?
When U.S. law enforcement officials shut down REvil’s ToR servers this month, a ransomware organization called the Groove Group launched a call to action on October 22, urging other ransomware actors to merge their efforts in targeting U.S. companies. Groove Group advised the gangs not to attack Chinese companies, since China could become a safe harbor for them in the near future. Groove is infamous for leaking more than 500 thousand Fortinet credentials in September of 2021.
Earlier this month, the Biden Administration pressed the Russian government to crack down on ransomware groups. Attacks against critical infrastructures (such as the Colonial Pipeline and other acute supply chain attacks like Solarwinds, Kaseya) urged the Biden Administration to open a dialogue with Russia. The readout of the Biden Administration also implied retaliation in the event that no cooperation was achieved.
REvil Servers Shut Down Twice
REvil (aka Sodinokobi) has a full track record of attacks in 2021, the most notorious being: Kaseya, Microsoft Exchange, and Quanta Computer. REvil is also linked to the DarkSide, the ransomware agent responsible for the Colonial Pipeline attack, due to the resemblance of their source code. After the Kaseya attack, a joint operation by international law enforcement, including the FBI, shut down REvil. The group has re-appeared recently with new victims, but law enforcement was able to shut down the new REvil servers again.
Threat Actors United
After the second shutdown, the ransomware groups started to publish posts on their blogs and hacker forums to support REvil by targeting US companies.
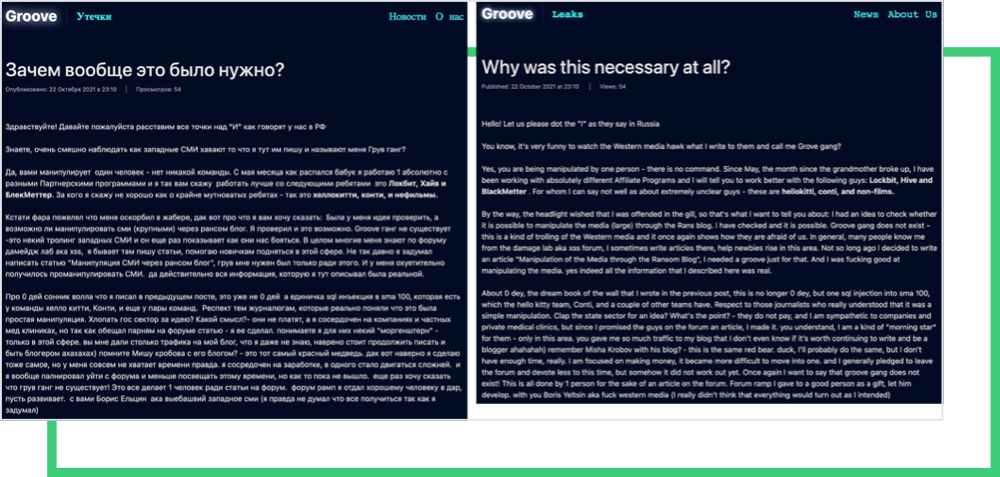
The first indication of this “unite the forces” effort appeared in the RAMP forum, in which a new group, called Orange, took hold recently. The gang currently advertises purchasing access to data from U.S. hospitals and government agencies, which seems to be in line with what Groove provokes on their blog.
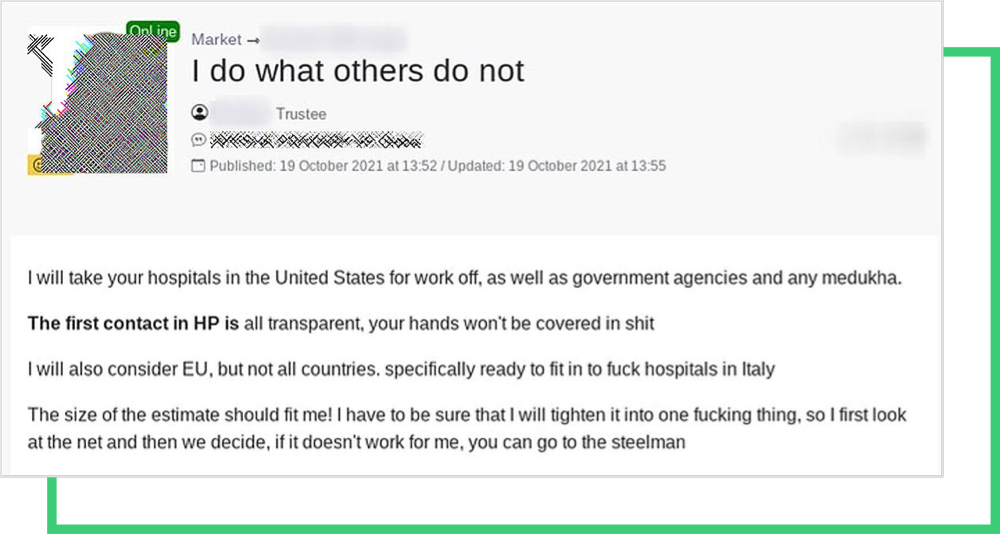
The response from other ransomware gangs was almost immediate. The post pictured below from Arvin Club’s blog shows that some groups would be happy with putting an end to REvil. But most gangs, like Conti and Groove, responded to this differently.
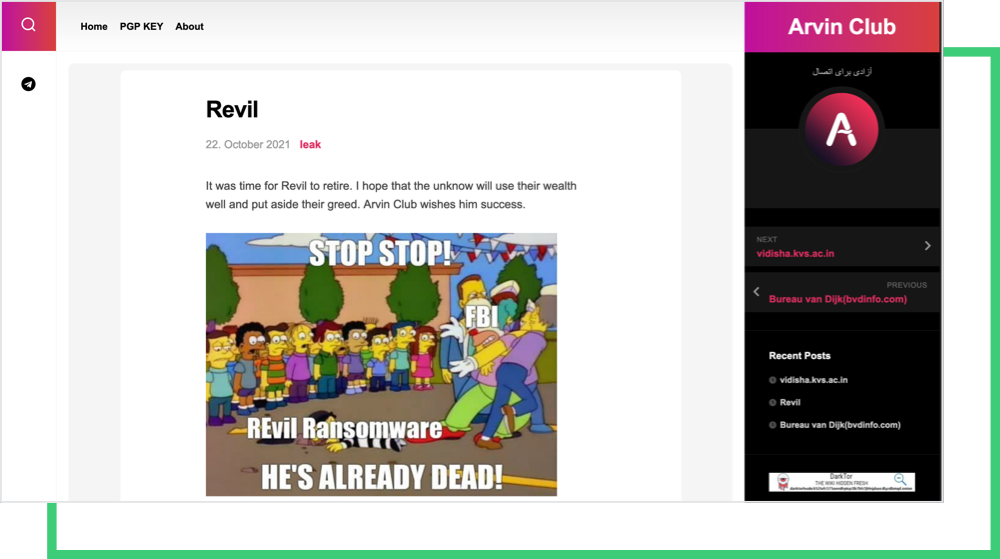
The Conti ransomware group published a supporting message to Groove on their blog. Not only does Conti articulate the ransomware attacks as “the art of pen-testing corporate data security, information systems, and network security,” they also question the legitimacy of the hack of REvil’s server.

This isn’t the first time cybercriminals have tried to justify their acts. Cyber or not, a criminal is a criminal, and using ransomware to gain funds is no different than stealing money via extortion.
The US Companies’ Ransomware Susceptibility
After these threats became public, Black Kite researchers took the initiative to analyze U.S. companies’ cyber security posture and ransomware susceptibility. We analyzed a sample size of more than 13,000 companies based in the US, with a Black Kite scan date not older than three months.
The Ransomware Susceptibility Index® (RSI™) metric used in the research is a machine learning-based parameter developed by Black Kite that shows the likelihood that an organization will experience a ransomware attack. It is a numerical value between 0.0 and 1.0, in which 1.0 indicates that a company is highly susceptible to a ransomware attack with its current cybersecurity posture. RSI™ follows a process of inspecting, transforming, and modeling data collected from various open-source intelligence sources such as internet-wide scanners, hacker forums, the deep/dark web, and more. Check our RSI™ page for more information.
Before delving into the statistics, it is worth mentioning that an RSI™ score greater than 0.4 is always a red flag for a company itself. If it reflects the score of a critical supplier, it’s also a red flag for the company’s stakeholders.
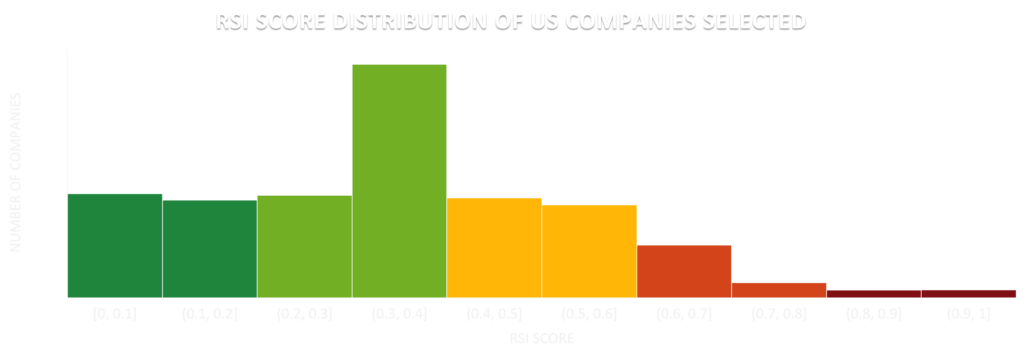
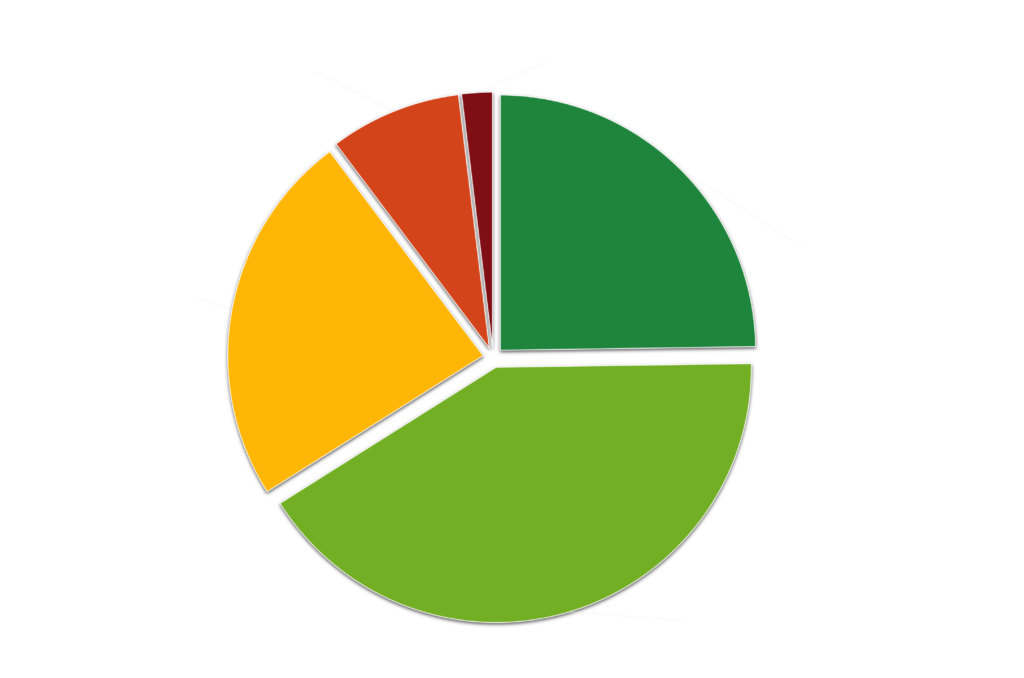
In this respect, approximately 34% of the sampled US companies are in this risky zone (RSI™ > 0.4), and more than 10% have RSI™ values of more than 0.6, indicating a critical level of ransomware susceptibility. 77 companies in this sample have the highest RSI™ score possible: 1.0.
A high RSI™ score is usually attributed to out-of-date products with software vulnerabilities, open critical ports (e.g., RDP or SMB ports), and/or poor email configuration exploited for phishing attacks.
Companies should learn from past ransomware attacks, since attack vendors and their techniques are common, and become more publicly known every day. The cybersecurity community has a culture of openly sharing indicators of compromises (IoCs), best practices, etc. Not long ago, we published some details regarding Conti’s playbook. The tools, Common Vulnerabilities and Exposures (CVEs,) and ports that threat actors leverage to gain access to companies’ critical data are not secrets anymore.
U.S. companies can avoid these incoming ransomware attacks with proper risk management procedures. Ransomware risk management starts with monitoring the indicators of ransomware susceptibility to predict the entry points of threat actors.
The key to understanding your company’s ransomware susceptibility is grasping the full-scale relationship of these controls within your organization. Black Kite’s RSI™ uses a data-driven methodology and a scalable compliance checklist to help you understand the likelihood of facing a ransomware attack.
Get Your Free RSI™References
- https://www.bloomberg.com/news/articles/2021-06-04/hackers-breached-colonial-pipeline-using-compromised-password
- https://therecord.media/revil-gang-shuts-down-for-the-second-time-after-its-tor-servers-were-hacked/
- https://heimdalsecurity.com/blog/groove-ransomware-extortion-groups-call-to-action/
- https://www.cnn.com/2021/10/13/politics/white-house-ransomware-meeting/index.html
- https://en.wikipedia.org/wiki/REvil
- https://www.technadu.com/russian-speaking-forum-ramp-fostering-new-raas-launches-affiliates/292147/
- https://us-cert.cisa.gov/ncas/alerts/aa21-265a
- https://blackkite.com/the-conti-playbook-leak-your-questions-answered/