Is the Okta breach the next SolarWinds? [Updated: December 2022]
Written by: ceren
Written by Gokcen Tapkan
Additional Contributor Yavuz Han
Edited by Haley Williams
[Update: December 21, 2022]
Okta, the popular Identity and Access Management (IAM) solution provider, notified its customers that its private GitHub repositories were hacked in December 2022. Okta stated that only source code was stolen and that customer data has not been impacted. However, source code distributions with injected malicious code on third-party sites may appear. This may lure employees to those sites to update or patch Okta software.
Okta has experienced a couple of cyber incidents in 2022, starting with an attack in January, which became public information in March, related to the Lapsus$ ransomware group’s announcements. Read more below about the original attack and Black Kite’s response.
Okta Smart Tags
In response to the Okta breach, Black Kite customers now have access to Okta tags in the Black Kite platform, indicating which third parties are direct clients of Okta. These smart tags alert customers to the impact of cyber incidents related to the Okta breach on vendor ecosystems.
Black Kite determined Okta clients based on BI data, website crawling, subdomain discovery and team research. The tags were then inserted into the platform under each ecosystem within the system tags functionality.
Within our platform, we discovered a total of 2,000 Okta clients, tagged with the yellow tag seen below.
PLEASE NOTE: Black Kite does not directly scan or communicate with any publically-facing assets. Open Source Intelligence (OSINT) is used to detect exploits and vulnerabilities.
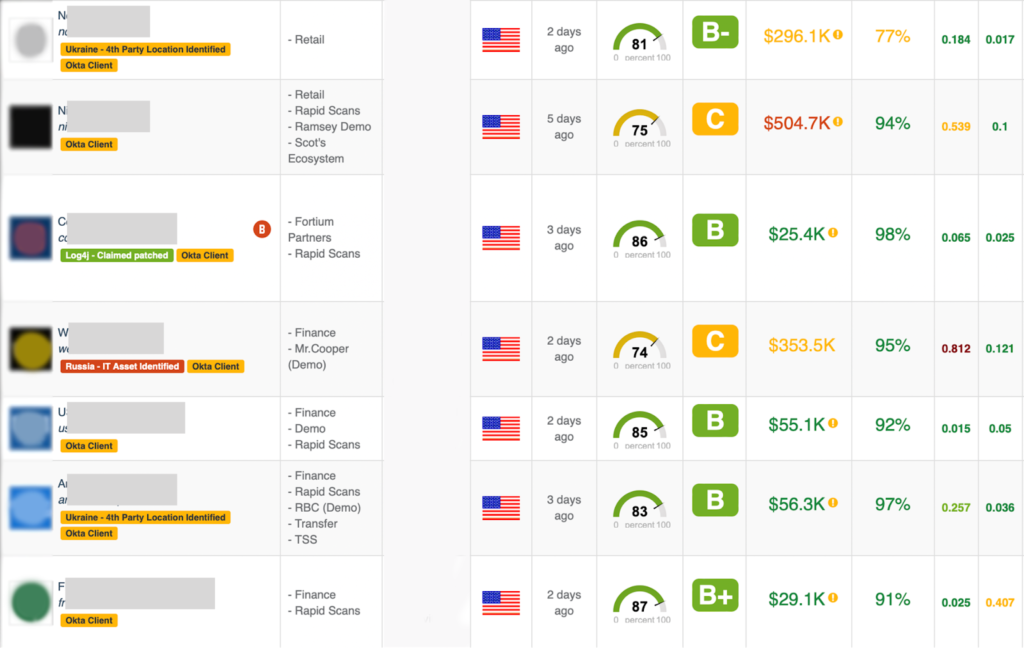
To see the vendors with Okta information,
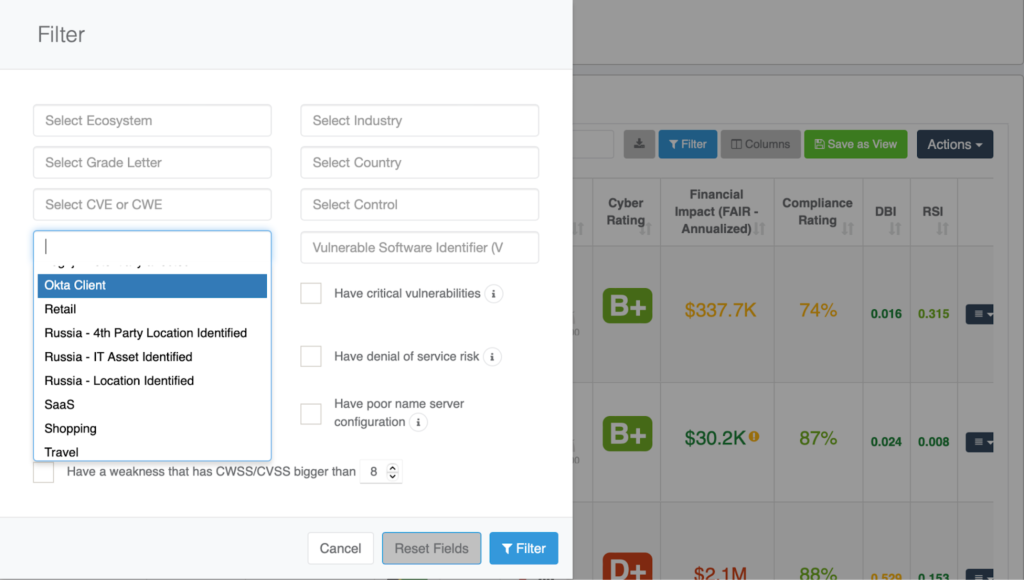
- Go to the Ecosystems > Company List, and click on the Filters button.
- On the pop-up window, click on the Tags field.
- Select the Okta tag to filter and display.
- Click on the Filter button.
Early this week, Okta was hacked by the LAPSUS$ ransomware group. On March 21st, the group shared screenshots from the Okta management platform on their Telegram channel, immediately after leaking Microsoft’s Bing source code.
The rapid series of leaks caught the attention of the cybersecurity community, quickly signaling the poor security measures of Okta and revealing their true intentions. Dates on the screenshots indicate the hackers’ presence dated back to late January 2022, alluding to a potential connection between the Microsoft and Okta breaches. So what’s the full story?
The Timeline of Events
On Monday evening, March 21st, LAPSUS$ began sharing posts and screenshots on the group’s Telegram channel, rather than the typical use of deep web blogs.
- The gang released significant source code from Microsoft’s search engine, Bing, Bing Maps, and Cortana virtual assistant.
- Microsoft confirmed, on March 22, that one of their employee’s accounts was compromised by LAPSUS$.
- The gang followed up with images dating back to January 21st, showing LAPSUS$ possession of an Okta administrator (superuser) account.
Though the order of the leaks fall in opposing order, the Microsoft leak is most likely the result of the Okta breach.
Does this breach have ties to the Russian invasion of Ukraine?
In the last few months, the LAPSUS$ gang has become more visible due to the Russian invasion of Ukraine. They gained a reputation after stealing source code from Samsung and Nvidia for the goal of extortion. However, their behavior in the Okta breach changed given the large reliance of other organizations (15,000) on Okta’s management of their networks and applications.
What did LAPSUS$ share publicly regarding their intentions?
The following screenshots, shared by LAPSUS$, give us a look into access gained throughout the duration of the attack, including access to the super admin account, and a password reset.
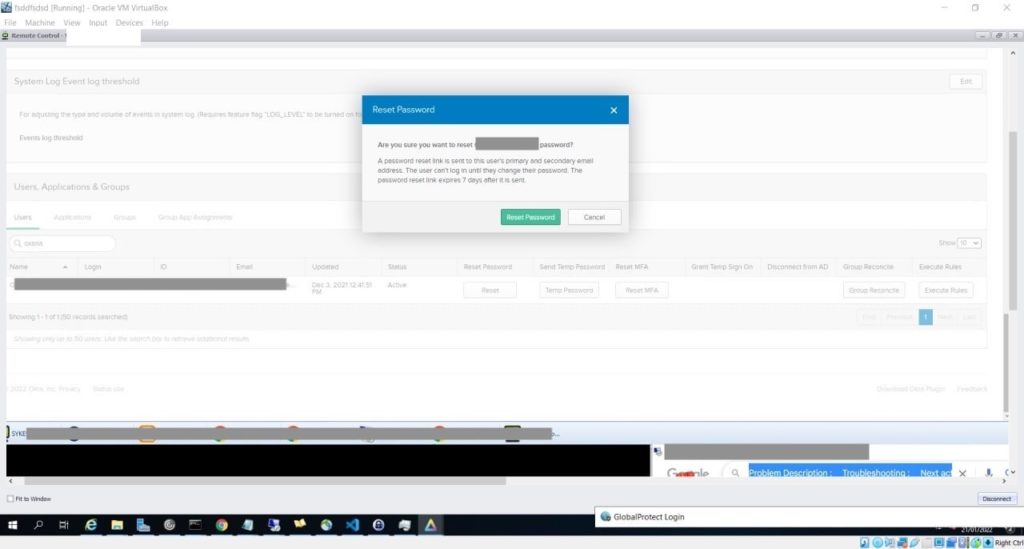
Another screenshot reveals LAPSUS$ access to Okta’s Cloudflare tenant, with the ability to reset employee passwords.
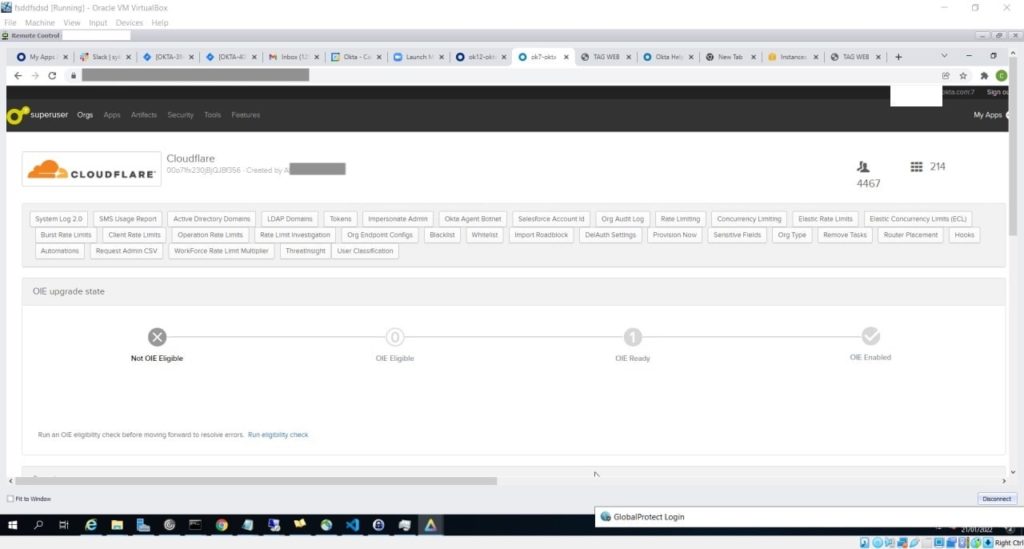
The group stated in an accompanying post that their focus was “only on Okta consumers, not the company itself,” a worrisome statement given that Okta is a third-party providing security solutions to thousands of notable companies. The screenshots appeared to be genuine, according to security experts.
The screenshots also include timestamps and dates indicating that had access starting January 21st of this year – Entry for two months. This interval aligns with the data in Black Kite’s 2021 Third-Party Breach Report: The average time elapsed between an attack and its disclosure date in 2021 was 75 days.
On March 22nd, Okta released an official statement regarding the LAPSUS$ claims:
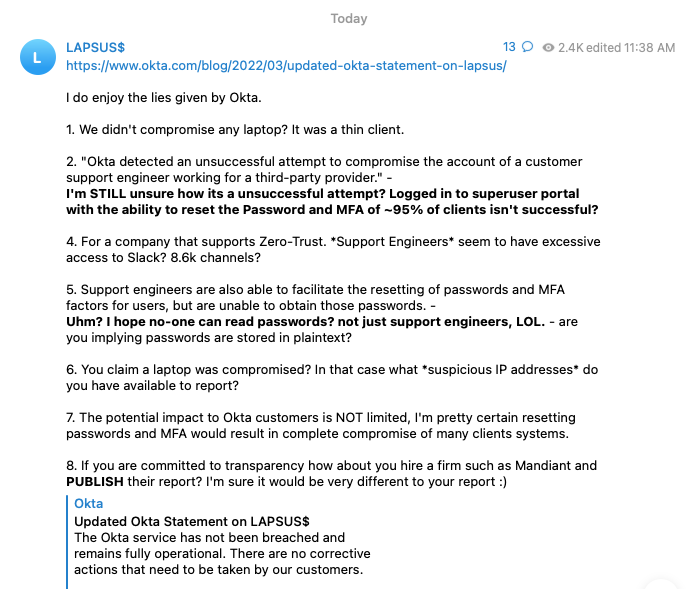
“In late January 2022, Okta detected an attempt to compromise the account of a third party customer support engineer working for one of our subprocessors. The matter was investigated and contained by the subprocessor. We believe the screenshots shared online are connected to this January event. Based on our investigation to date, there is no evidence of ongoing malicious activity beyond the activity detected in January.”
Since then, they have provided additional updates to the official statement. LAPSUS$ quickly shared a response, discussing the accessed password and MFA reset.
The Cascading Nth-Party Risk on the Digital Supply Chain
The statement from LAPSUS$ suggests that their access to Okta could be through a third-party vendor. Thus, through the eyes of Okta’s customers, this entire incident is actually caused by a 4th party. In a situation where Okta, a vendor in a digital supply chain, has thousands of customers that rely on their services, extensive cascading risk occurs.
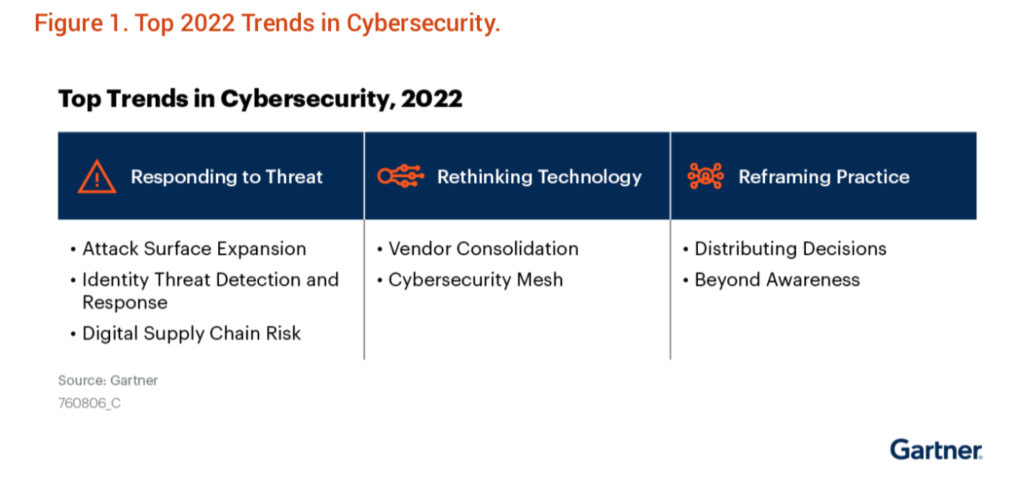
In Gartner’s Top Trends in Cybersecurity, 2022 report, Gartner recognizes the digital supply chain risk trends for the year.
Black Kite Research on Okta
In response to a breach of this size, Black Kite Research gathered and analyzed data on Okta’s technical report, searching for risk indicators that could have led to this attack.
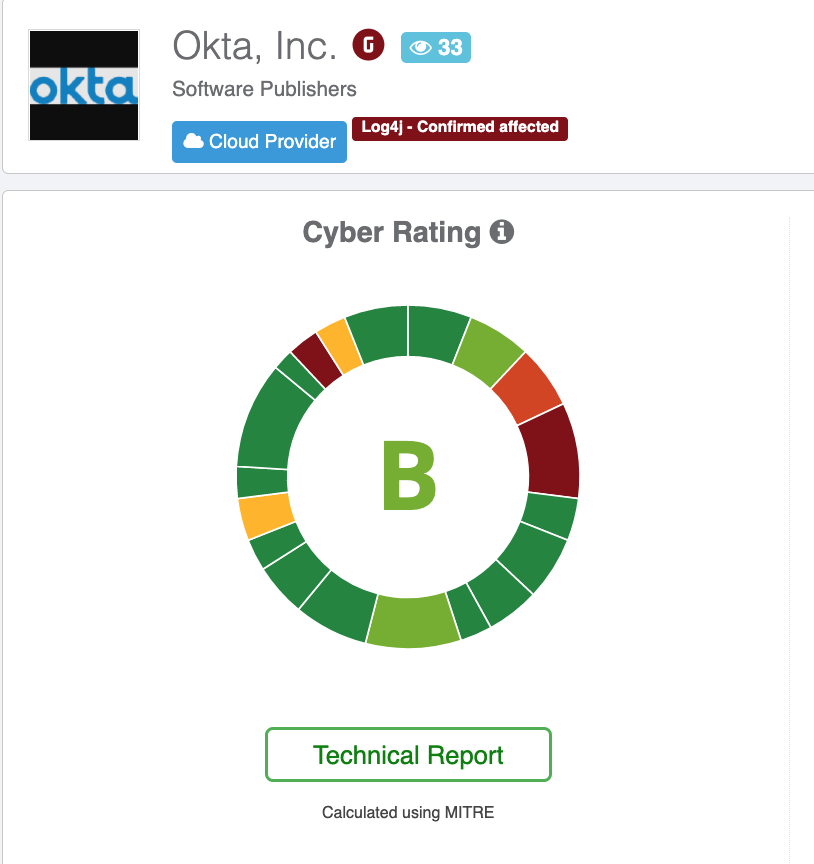
Okta, one of the continuously monitored vendors on the Black Kite platform, has a grade of B, which can be considered a good grade overall. However, Black Kite identifies the Okta as vulnerable software, and there are many other red flags behind the grade itself.
Vulnerability Software Identifier (VSI) and Gray Rhinos
One prominent signal on the Black Kite Platform, which gives a quantified risk assessment over a vendor, is the Vulnerability Software Identifier, or VSI. Black Kite identifies the vulnerable software with the impact analysis of a software vendor by estimating the probability and impact of a cyber incident on your organization due to said vendor.
On top of the technical rating, VSI produces an easy-to-understand classification of software vendors to determine the vulnerable software more efficiently. Based on the impact and probability of an incident caused by a vendor, the analyzed software vendor falls into one of the four quadrants in the Impact Matrix.
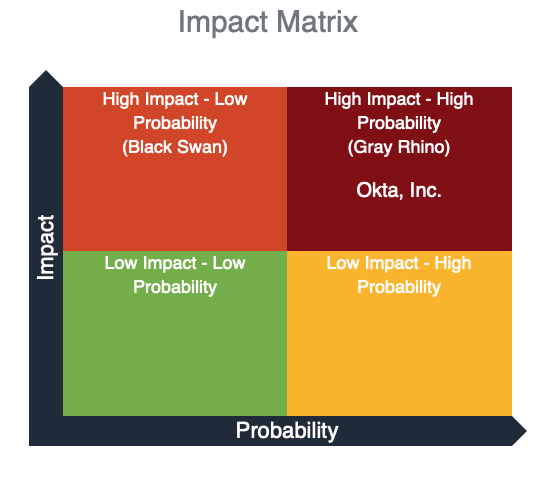
According to the Black Kite findings, Okta is considered a High Impact – High Probability (Gray Rhino) vendor. Here, both the probability of experiencing a cyber event and the total impact, is high. Any software vendors that fall into this category are critical to the organization.
These highly probable, high-impact threats are called Gray Rhinos, “like a two-ton rhinoceros aiming its horn in our direction and preparing to charge.” A Gray Rhino is a slowly emerging, obvious threat often ignored or minimized. At the same time, the potential impact of the event itself is dismissed, as it happened in the SolarWinds breach.
The breach, rather than a combination of complex attack vectors, is thought to result from a simple phishing scam and/or a leaked credential. The URL here suggests that the superuser account was compromised, though currently the details are still unknown.
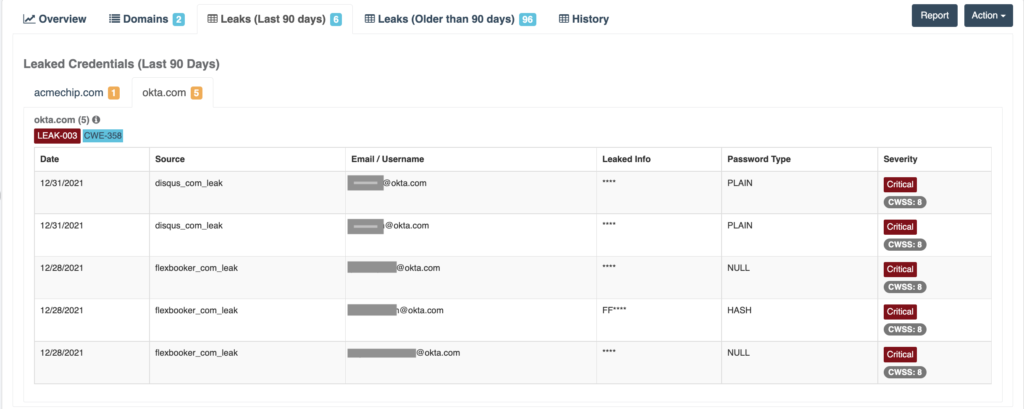
As we looked further into the breakdown of the rating, we found that there have been six credential leaks in the last 90 days and 96 leaks older than 90 days. Some of them have been leaked as plain text.
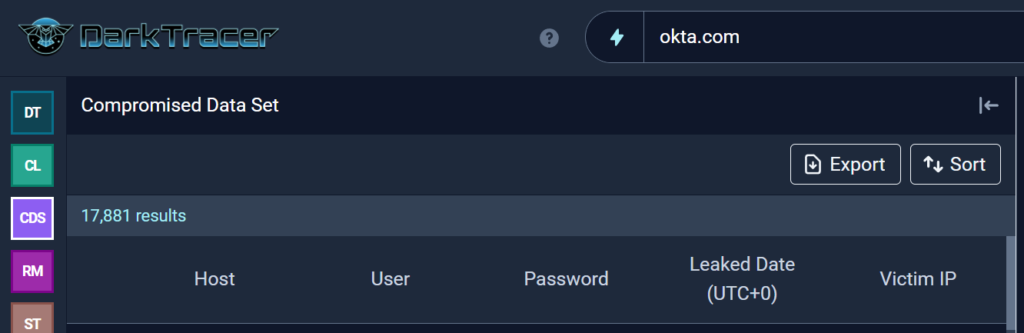
Hacker groups often use leaked credentials for credential stuffing attacks, where they try username and password combinations in an automated fashion. These combinations have dynamically changing proxy IP addresses to avoid detection. This method is one of the primary attack vectors used by ransomware groups. The initial investigations of cybersecurity researchers, plus statements from both parties, suggest that the initial access might have been obtained through credential stuffing attacks.
On March 23, DarkTracer posted on Twitter that “More than 10K of okta(.)com login credentials are leaked from infected users with Redline stealer malware to the dark web/deep web.” In February, DarkTracer published the Global Stealer Malware Intelligence Report, analyzing stealer logs from ~142 thousand infected users by Redline Stealer Malware. According to DarkTracer, more than 10,000 of the logs are Okta credentials.
Okta Breach Relationship to the Log4j Vulnerability
In December, many companies suffered security incidents from the critical Log4Shell vulnerability, Log4j. At the time, Black Kite tagged monitored companies with their current status on the Log4j vulnerability. Okta was one of the vendors tagged as “Confirmed Affected” based on public research reports and company statements.
At this point, it is uncertain whether the initial gained access to Okta was obtained by LAPSUS$ exploitation of Log4j-related vulnerabilities. However, it is a possibility that should not be overlooked, considering the initial entry was around January.
Lessons learned from breached third-party software
Although the timeline of the LAPSUS$ attack on Okta might seem surprising, this is not new to the third-party risk domain. The Okta incident has the potential to become a Solarwind-level incident if companies do not take necessary actions right away. Microsoft released a set of recommendations as a part of their LAPSUS$ announcement:
- Strengthen MFA implementation
- Require healthy and trusted endpoints
- Leverage modern authentication options for VPNs
- Strengthen and monitor cloud security posture
- Improve awareness of social engineering attacks
- Establish operational security processes in response to LAPSUS$ intrusions
Threat actors prey on prominent companies through third and fourth parties. In this case, access to Okta was through a third-party support engineer. This engineer was a third party of Okta, the third-party of Microsoft, a domino effect of the digital supply chain.
- Employees are still the weakest link in Security Risk Management and Supply-Chain Risk Management.
- Companies must pay attention to Gray Rhinos in their supply chain.
- No matter the security policies in place, rely on quantifiable metrics such as Quantified Cyber Risk.