How Concerned Should Organizations Be on the VMWare ESXIArgs Threats?
Written by: ceren
Written by Ferhat Dikbiyik
Additional Contributor Ekrem Celik
Edited by Haley Williams
Over 2,000 servers worldwide were suddenly affected with ransomware due to a 2-year-old vulnerability (CVE-2021-21974). This exploited vulnerability lives within VMWare ESXi hypervisor.
While only 2,000 servers have been affected, there is a greater potential of up to 66,000 possible targets, which are internet-connected computers, according to Bloomberg.
What is the vulnerability in VMWare? Have most organizations patched it?
This is a 2-old vulnerability on VMWare ESXi’s specific versions (7.0 before ESXi70U1c-17325551, 6.7 before ESXi670-202102401-SG, 6.5 before ESXi650-202102101-SG) . Suppose the attacker resides within the same network segment as the ESXi hypervisor and has access to a particular port (port 427). In that case, the threat actor can exploit this vulnerability to trigger a heap-overflow issue resulting in remote code execution (RCE).
Since it is an old vulnerability, organizations with a strict patching cadence would have already patched it. However, companies with a slow patching cadence or waiting for cloud providers to act on the vulnerability may still be vulnerable. The fixed version of VMWare ESXi has been available on the vendor’s advisory since Feb. 2021, and all organizations need to do is update the system to a fixed version.
The good news is there are guides available for victims that may allow admins to rebuild the VMs and recover their data without paying the ransom. Besides the guides provided by independent researchers, CISA also provided a script to recover encrypted files.
How do the threat actors use the vulnerability?
If the conditions are right, threat actors use this vulnerability to encrypt the VMWare ESXi files. VMWare ESXi is an enterprise-level hypervisor that allows partitioning and virtualization of IT hardware resources. It is mainly used by cloud providers that provide these virtual resources as services. Encryption of VMWare ESXi files may not immediately cause a data breach but can seriously cripple the operations.
This issue potentially impacts cloud providers more, but organizations getting services on top of VMWare ESXi can also be affected.
Who discovered the first use of the vulnerability?
The use of vulnerability for ransomware was first mentioned in a tweet by CERT of France, and French cloud providers also published reports about it. The ransomware group behind it left a file called ransom.html entitled How to Restore Your Files after encrypting .vmxf, .vmx, .vmdk, .vmsd, and .nvram files and creating a .args file for each encrypted document on target systems. Thus researchers dubbed the ransomware campaign as ESXiArgs.
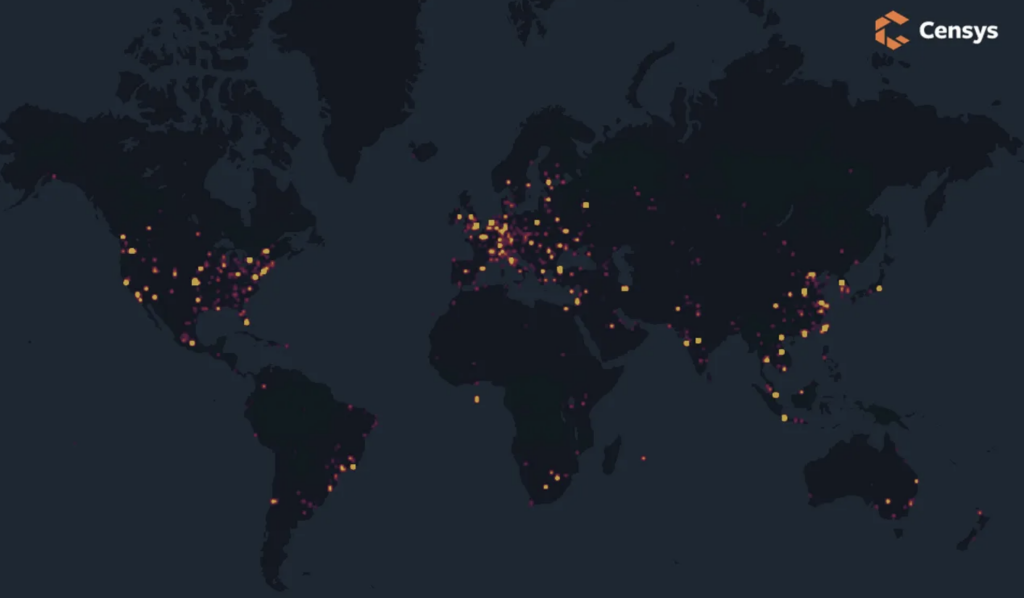
When we searched for the files with this title on OSINT resources, we could see that more than 2,400 VMWare ESXi servers worldwide were compromised in the ESXiArgs campaign. This number was around 3,200 on Feb. 4th.
Most compromised servers (more than 900) are located in France. It is followed by the US (360), Germany (321), Canada (240), and the UK (98). It is safe to assume that the campaign started as France-focused attacks and moved to other countries.
Is the infamous Ransomware group Lockbit behind the operations?
There are rumors around that the infamous ransomware group Lockbit was supposedly recently responsible for a similar attack in the U.K. The ransom notes and TTPs (techniques, tactics, and procedures) do not directly indicate a connection to LockBit.
French cloud provider OVH linked the operations to Nevada ransomware. Nevada ransomware is a ransomware group that emerged on the dark web in late 2021. In December 2021, they announced a partnership program with an 85/15 split on the ransom. They provide RaaS (Ransomware-as-a-Service), providing a cyber weapon to affiliates who execute attacks on targets.
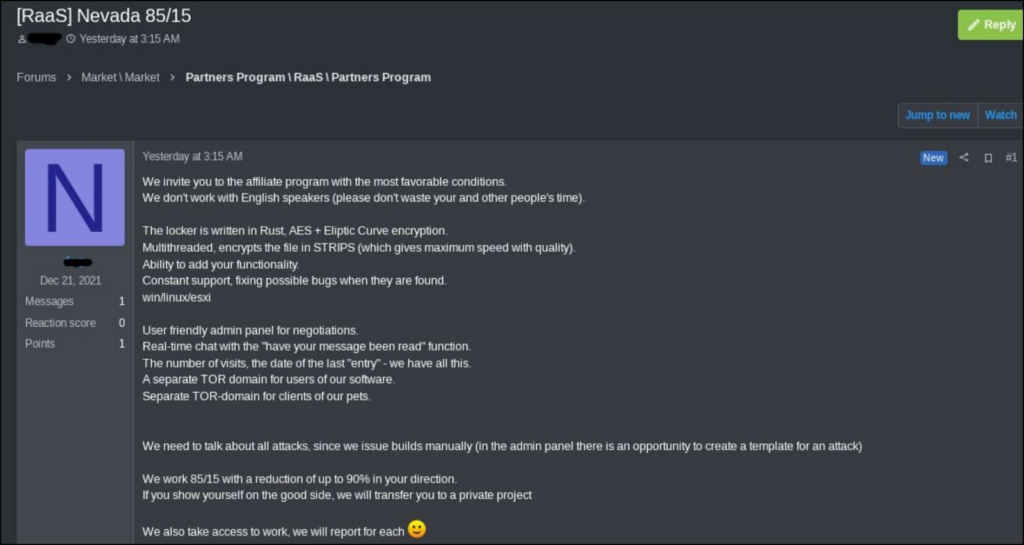
Further research shows that the ransom notes appear to be from a new ransomware family. No well-known ransomware group, such as Lockbit, has claimed the attacks yet.
Lockbit is a well-known ransomware gang, and their MOs and TTPs are highly investigated. The group covers ample space in the cybercrime business ecosystem with a ransom collection that reaches multi-billions.
According to our research on more than 2,500 ransomware incidents and victims in 2022, Lockbit published more than 800 victims on their dark web blog, which makes them the most active group, followed by Conti. Even though their victims are in different industries, Manufacturing (134) and IT (97) are the most targeted industries by Lockbit. The U.S. and Europe are the most targeted regions, as Lockbit has ties to Russian groups.
Lockbit also exploits well-known vulnerabilities to obtain access to target systems, but the use of such vulnerability has not been linked to Lockbit so far. However, after the disclosure of the potential of such a vulnerability on VMWare ESXi, it is possible that some Lockbit affiliates also surf on the wave created by others.
What steps should my team take?
-
- Update your VMWare ESXi version to the fixed version or ask your cloud provider to do so.
-
- If your files are encrypted, use this script provided by CISA to recover your files.
-
- Watch out for third (and fourth) party risk. Monitor your third and fourth parties for the use of vulnerable versions of VMWare.
-
- Reach out to your third party vendors that use vulnerable VMWare ESXi versions and ensure that they have upgraded to the fixed versions.
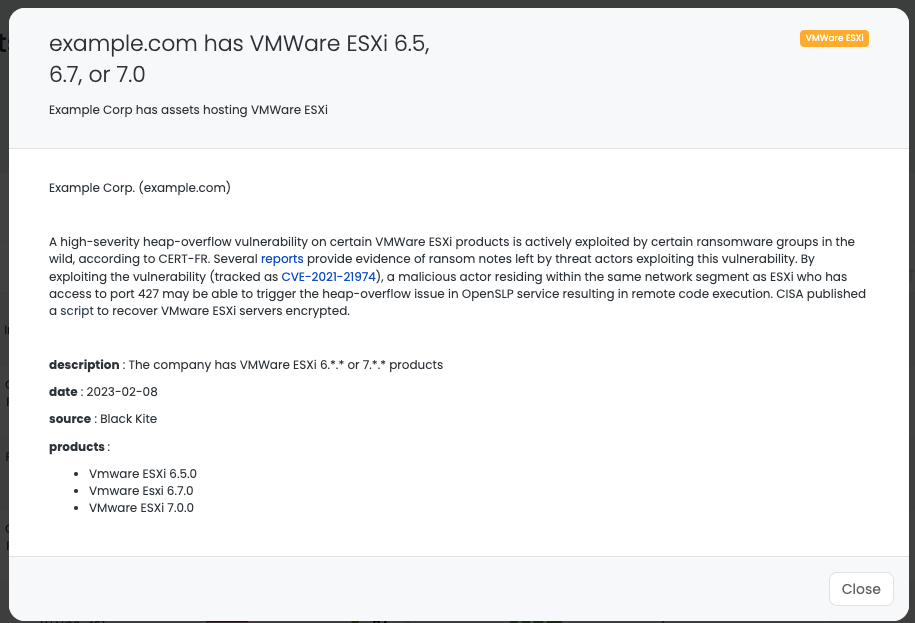
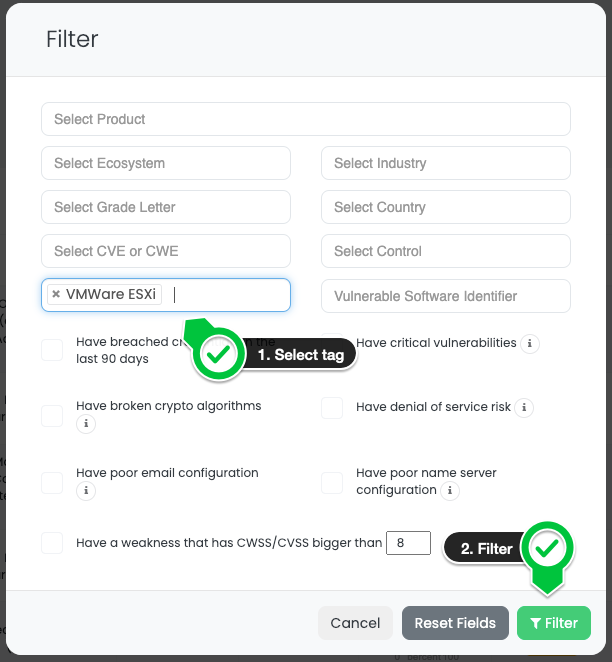
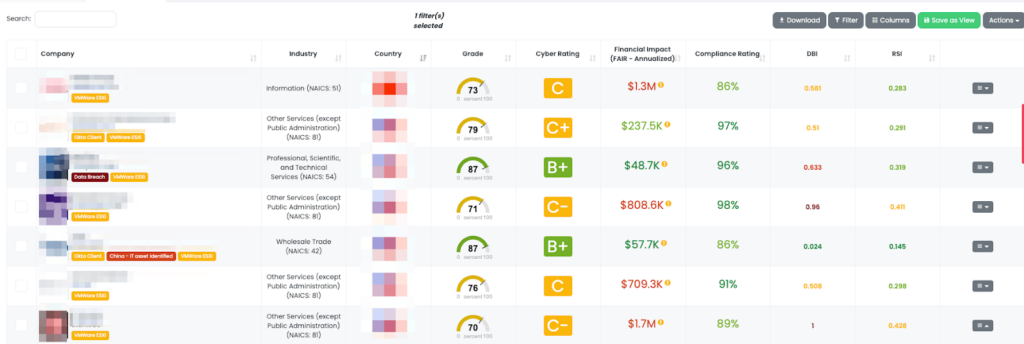
How to search vendors that use VMWare ESXi with Black Kite?
IT vendors such as VMWare are usually Gray Rhinos, apparent risk with high impact and high probability as marked by Black Kite.
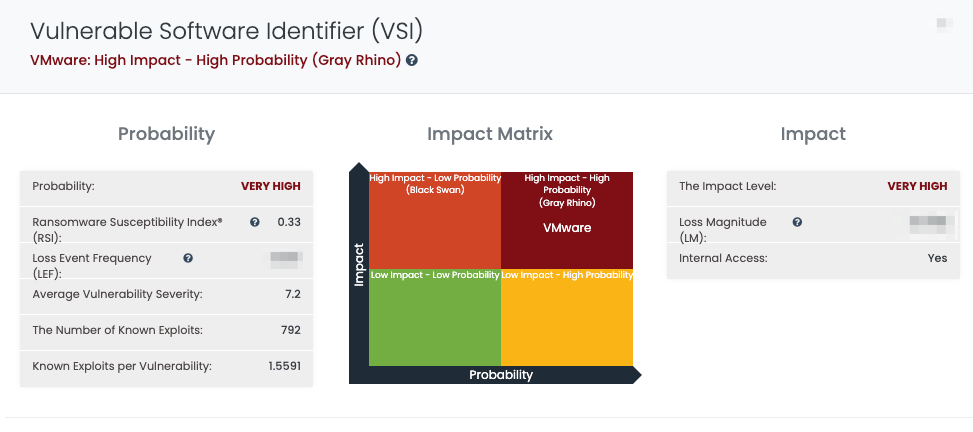
Thus, it is important to identify third or fourth parties. We have created a specific Focus Tag for companies that use VMWare ESXi 6.5, 6.7, and 7.0. Black Kite users can easily filter out the companies with VMWare ESXi tags.