Extortion Threats Fueled by Release of Free Black Byte Ransomware Decryptor
Written by: ceren
Written by Gokcen Tapkan
Additional Contributor Yavuz Han
Edited by Haley Williams
Attention-catching threats aimed at companies continue to roll out from ransomware group, Black Byte, after a research lab announced the release of a free decryptor for victims to use. The decryptor, developed by Trustwave SpiderLab, is believed to work for former as well as current victims. After the development went public, Black Byte doubled down on their efforts, delivering more ransomware threats to victims.
Black Kite Research closely monitors many ransomware groups’ blogs and their victims, including Black Byte’s. Our research shows high scores on our Ransomware Susceptibility Index® (RSI™) for the victim companies. Before diving into the details of victims’ RSI™ scores, we assess encryption used by ransomware groups and how Black Byte’s encryption mechanism works.
How does Ransomware Encryption Work?
Although not all ransomware gangs use encryption, (for example, WinLock) it’s still the most common attack vector of all ransomware attacks. In 2010, WinLock was a famous ransomware trojan which trivially restricted access to the system by displaying adultery images instead of encryption.
The extortion had victims send a premium-rate SMS (costing around US$10) to unlock the system. In those days, ransomware was not targeting high-profile companies but preying upon small targets such as ordinary users. Although minor in size, the demand reached many users and is believed to have pulled in a total of $16 million.
Today, almost every ransomware encrypts business systems after the initial compromise and reconnaissance of the internal network. Perhaps the most famous ransomware among the encrypting strains was CryptoLocker. The encryption software generated a 2048-bit RSA key pair and uploaded it to a command-and-control server. It was estimated that at least $3 million was collected using the malware before it was shut down as part of Operation Tovar [1].
Encryption/decryption key hidden inside the image file
Like most other ransomware, Black Byte downloads a file called ‘forest.png’ from a remote server under their control, according to Trustwave researchers. This file appears to be an image file, but hidden inside is the seed of the AES encryption key needed to encrypt a device. In symmetric encryption systems, the same key is used both for encryption and decryption. Trustwave [2] researchers realized the ransomware used the same image file for all victims.
Key generation processes can be complicated and, usually, the keys generated are unique to every session. In this instance, Trustwave found a raw key directly used in the encryption. The decryption source code is freely available on Github.
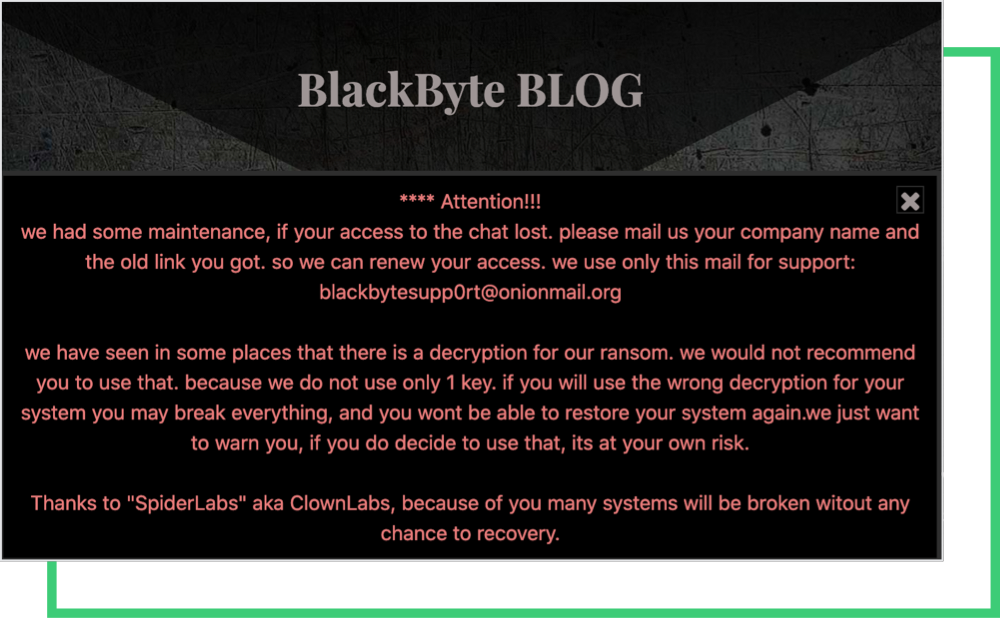
This disclosure made by Trustwave is not welcomed by the threat actor. The free decryptor almost foiled the extortion threats of Black Byte. Not long after, the group published a warning on their site stating that using the freely available decryptor would lead to corruption of the files as follows:
“[W]e have seen in some places that there is a decryption for our ransom. [W]e would not recommend you to use that. [B]ecause we do not use only 1 key. [I]f you will use the wrong decryption for your system you may break everything, and you won’t be able to restore your system again. [W]e just want to warn you, if you do decide to use that, its at your own risk.”
Before the exposure of the decryptor, Black Byte gave its victims 30 days to issue a ransom payment. According to the latest posts on Black Byte’s blog, the group has reduced the time to just 12 days, showing how furious they are about the decryptor being public.
Analysis on Black Byte Victims
Although it emerged in late July 2021, Black Byte recently made a name for itself in the cybersecurity community after high-profile attacks. Black Byte – like other gangs – often disclose its claimed victims on its dedicated site. As seen below, a food and logistics supplier (a.k.a third-party) that serves global firms allegedly became the victim of the ransomware attacks by Black Byte.
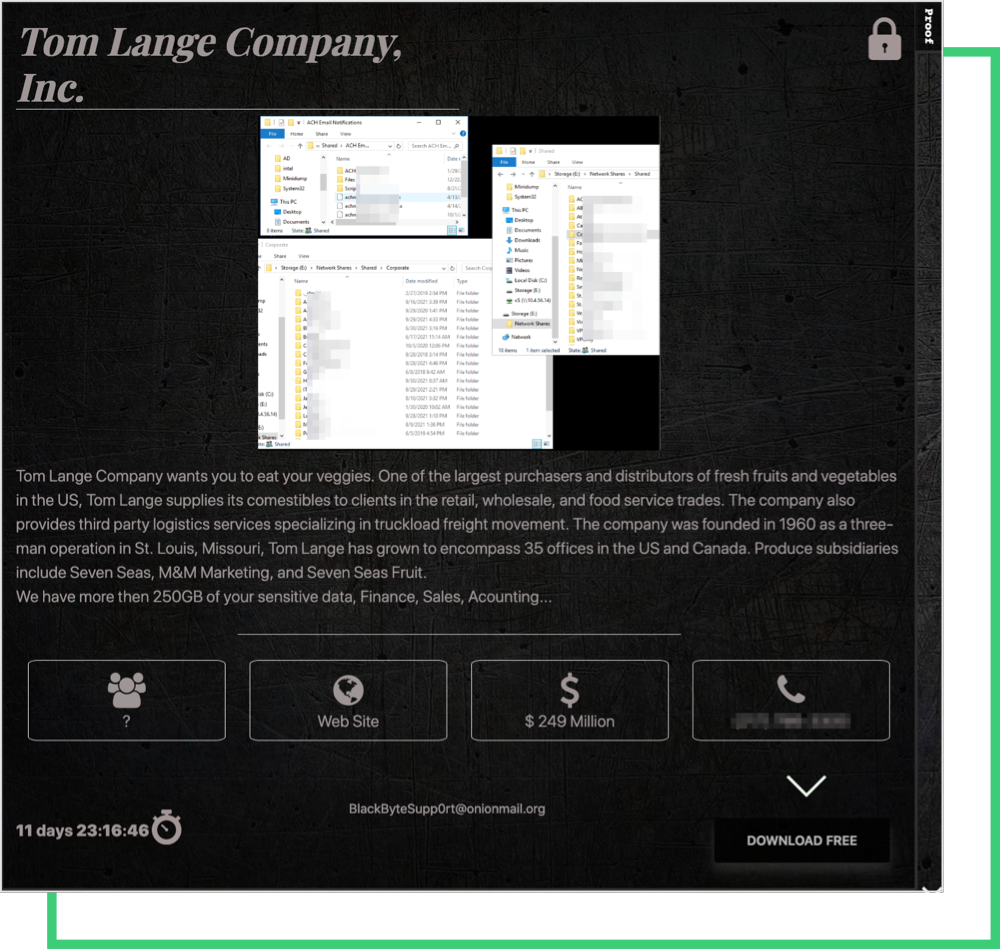
Threat actors spend the same amount of time with small businesses—as long as they are worth it— as high targets. So, it’s convenient to pursue a third party since they are critical elements of a supply chain, and have poor cybersecurity hygiene.
The victims of the Black Byte group are mainly based in the United States, but the group also targets companies in South America and Europe from different industries. This shows that the ransomware group picks its victims based on whether it is worth it to execute the attack, and the possible vulnerabilities on the victim’s systems. Targeting victims from different countries and industries usually indicates that the group has found a common vulnerability in the companies, and that they have the exploitation methodology available.
Victims’ Ransomware Susceptibility Index® (RSI™) Scores on Black Kite Platform
Black Kite researchers have closely monitored the activities of Black Byte since their emergence and assessed their victims’ cyber security posture on the Black Kite platform. Here, we’ve compiled a sampling of victims alongside their Ransomware Susceptibility Index® ( RSI™).
Note that RSI™ is a metric, developed by Black Kite, that shows how susceptible a company is to ransomware attacks based on specific attack indicators (i.e., common entry points used by threat actors.) Click here for more information about RSI™.
| Company | RSI™ | Industry | Country | Amount of Data Leaked |
|---|---|---|---|---|
| Company A | 0.369 | Transport | Australia | More than 190 GB |
| Company B | 0.544 | Beverage | US | More than 250 GB |
| Company C | 0.163 | Farming | US | More than 100 GB |
| Company D | 0.624 | Retail | Chile | Not disclosed |
| Company E | 0.334 | Medical Device | US | 100 GB |
| Company F | 0.501 | Facilities Services | US | Not disclosed |
The average RSI™ of the victims is 0.42, which is greater than the acceptable value (0.4.) An RSI™ score greater than 0.4 is always a red flag for a company itself and its suppliers. The victims with high RSI™ scores have out-of-date products with software vulnerabilities, and some have poor email configuration that can be exploited for phishing attacks.
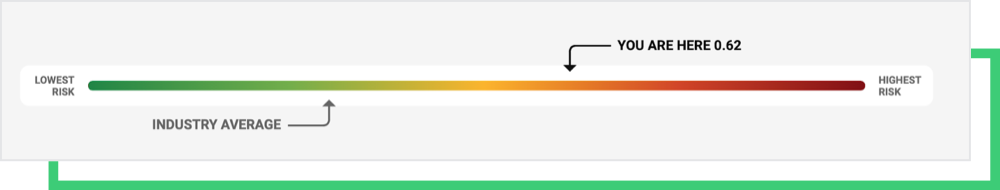
The RSI™ follows a process of inspecting, transforming, and modeling data to discover the likelihood of a ransomware incident. Black Kite’s data is collected from various OSINT (Open-source Intelligence) sources such as internet-wide scanners, hacker forums, the deep/dark web, and more. Using the data and machine learning, Black Kite identified the correlation between control items in the Cyber Risk Assessment and Ransomware Entry Methods to provide these approximations.
Get Your Free RSI™References
[1] https://en.wikipedia.org/wiki/Ransomware#Notable_software_packages
[2] https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/blackbyte-ransomware-pt-1-in-depth-analysis/

