Clop Ransomware Group Strikes Hundreds of Companies, Raising Concerns for Cascading Breaches
Written by: ceren
Written by Ferhat Dikbiyik
Additional Contributors Yavuz Han and Ekrem Celik
Edited by Haley Williams
Clop (stylized as C|0p), a notorious ransomware group, has recently struck dozens of companies worldwide in a new mass-ransomware campaign targeting GoAnywhere Managed File Transfer (MFT) servers.
While it is unclear whether the victims have paid the demanded ransoms, several high-profile companies initially denied the attacks. Still, they later acknowledged them, raising concerns about the potential data breaches that may have occurred in the meantime. The attack on GoAnywhere resellers and service providers highlights the risks of third-party vendor breaches and their potential impact on organizations’ sensitive data.
In this article, we’ll examine the Clop ransomware group, their recent attack, and the data breach risks posed by third-party vendors like GoAnywhere. We’ll also discuss what organizations can do to protect themselves from ransomware threats to mitigate the risks of data breaches.
Recent mass-ransomware attacks executed by Clop
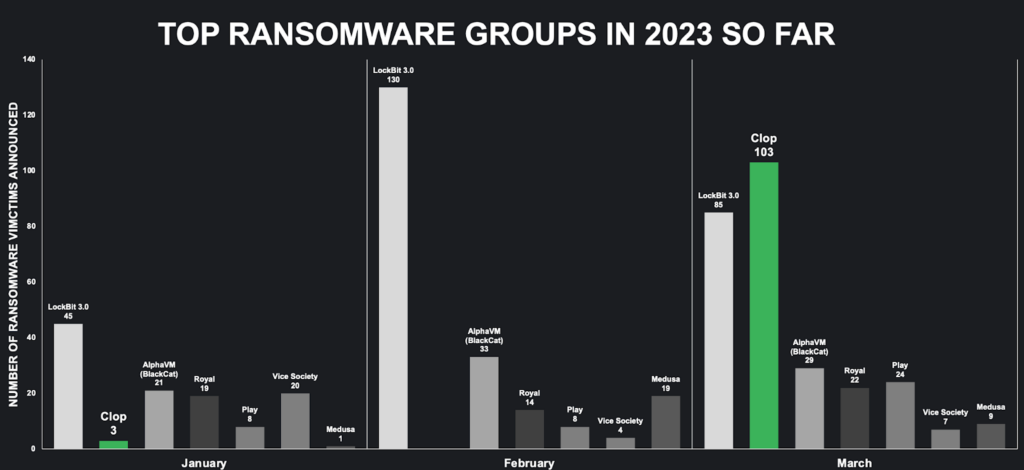
On March 21st, 2023, researchers discovered that Cl0p ransomware group was actively exploiting a high-severity vulnerability (CVE-2023-0669), using it to execute ransomware attacks on several companies, including Saks Fifth Avenue. Over 100 victims have been identified on Clop’s underground blog site, with more added periodically. Notably, major names such as P&G, have been affected. The cybersecurity company Rubrik and energy company Hitachi also responded to the data breach caused by this vulnerability.
The threat actor responsible for the attack claims to have targeted 130 victims, with half of them being hit through the vulnerability on GoAnywhere MFT servers. Our findings have confirmed that the stated vulnerability was indeed used in the attack. Some victims had publicly visible GoAnywhere MFT servers, which made them vulnerable. More than half of the victims are U.S.-based, suggesting that the attack primarily focused on American companies and organizations.
Our investigation also discovered that some victims were resellers, service providers, and partners for GoAnywhere MFT servers. Clop may have also gained access to their client’s information. As a result, we expect that there may be eventual third-party data breaches due to these ransomware attacks.
Rather than releasing information on their victims one at a time, the Clop group chose to disclose all of them at once, making March a particularly devastating month for those affected. The companies affected by these attacks have reportedly generated more than $100 billion in revenue.
Source: Black Kite Research
Let’s discuss the GoAnywhere vulnerability (CVE-2023-0669) used in these mass-ransomware attacks
Forta announced on February 1, 2023, that a zero-day exploit affecting GoAnywhere Managed File Transfer (MFT) application could lead to remote code execution. The announcement was released behind an authentication wall, but investigative journalist Brian Krebs shared it on his Mastodon account on February 2, 2023.
An exploit for the vulnerability was released on February 6, 2023, which may have prompted the Cl0p ransomware group to act quickly and take advantage of the vulnerability before patches could be applied.
Forta released version 7.1.2 of GoAnywhere MFT to address the vulnerability on February 7, 2023 and assigned the CVE-2023-0669 identifier to this zero-day vulnerability.
The CVE-2023-0669 vulnerability is a remote code execution flaw due to insufficient sanitization of serialized data. An attacker would need to gain access to the administrative console, typically available only within a private company network, via VPN, or by allowing specific IP addresses (in cloud environments like Azure or AWS) to exploit this vulnerability.
How many assets are at risk?
Despite the patch release, many organizations failed to update their systems promptly. According to OSINT sources, almost 1,200 assets host vulnerable GoAnywhere MFT publicly visible servers, most of which are in the U.S. This means these assets are at risk of being targeted by threat actors like Clop, who can easily discover them and exploit the vulnerability.
Moreover, as previously mentioned, some of Clop’s victims were resellers, service providers, and partners for GoAnywhere MFT servers. This raises the possibility that Clop may have gained access to their clients’ information, potentially expanding the number of digital assets at risk. Companies and organizations should take immediate steps to secure their systems and monitor their third-party vendors, particularly those using vulnerable GoAnywhere MFT servers, to minimize the risks of further data breaches.
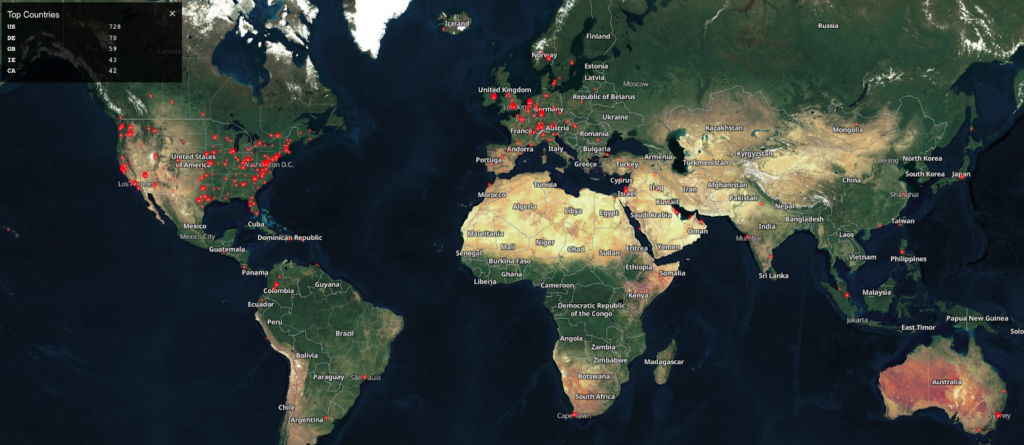
Shodan search that reveals the possible vulnerable GoAnywhere MFT servers
To ensure that their systems are secure, companies and organizations should monitor their third-party vendors (and even fourth parties) that may be using vulnerable GoAnywhere servers. CVE-2023-0669 is a vulnerability that has been exploited extensively since March of this year. While it remains unclear how long this group will continue to operate with such high efficiency, the damage they have already caused is substantial.
Who is the Clop ransomware group?
Clop is a malicious software that falls under the Cryptomix ransomware family. It targets vulnerable systems and encrypts saved files using the “.Clop” extension. The name Clop is derived from the Russian word “klop,” which means “bed bug,” a blood-sucking insect. One of Clop’s distinct features is the message “Don’t Worry C|0P,” commonly found in ransom notes.
Clop has been notoriously hard to contain and combat. However, Ukrainian law enforcement successfully arrested some people working with the Clop ransomware group following an international operation in conjunction with law enforcement in the United States and South Korea. Let’s dive into the last 4 years of Clop.
Clop’s underground blog (victim names are redacted)
Clop ransomware was first detected in February 2019, when it was used in a series of attacks against businesses in Europe and Asia. The group accessed victim networks using brute-force tactics on Remote Desktop Protocol (RDP) endpoints. In March 2020, it was reported that Clop had joined forces with the notorious cybercrime group TA505 to distribute ransomware. This partnership gave Clop access to a vast network of compromised systems, enabling them to increase the scale and impact of their attacks.
Throughout 2020, Clop’s attacks became more sophisticated. They began using double-extortion tactics, which involved encrypting the victim’s files and stealing sensitive data, and threatening to release it if the ransom was not paid. They also started targeting larger organizations, including universities, healthcare providers, and government agencies.
In 2021, Clop stole large amounts of data from high-profile companies using the File Transfer Tool (FTA), which is Accellion’s legacy. In these attacks, the group only stole the data instead of encrypting it.
Clop also launched attacks in 2021 by exploiting a known and patched vulnerability in the SolarWinds Serv-U file server software. The group exploited versions of SolarWinds Serv-U software that were not updated to the latest version, which fixed the remote code execution flaw (CVE-2021-35211).
The HHS cybersecurity program, Office of Information Security, published an analyst note about Clop’s attacks on HPH organizations on March 23, 2021. The note identified Clop as a ransomware variant associated with the FIN11 threat actor group and the double extortion tactic. It also highlighted that Clop operators had used both a “spray and pray” approach and a more targeted approach, suggesting they have some discretion when selecting victims. The analyst noted that Clop operators discovered multiple zero-day vulnerabilities affecting the Accellion File Transfer Appliance (FTA) product in December 2020 and began targeting its users. Mitigations for the HPH sector can be found at the end of the report.

Cl0p’s TTPs within the MITRE ATT&CK Framework
How to determine vendors that have vulnerable GoAnywhere MFT servers
Black Kite offers a powerful solution for companies looking to manage third-party risk proactively. By leveraging our unique focus tags, which identify vendors with vulnerable GoAnywhere MFT servers, our users can quickly and easily identify at-risk vendors and take action to mitigate potential threats.
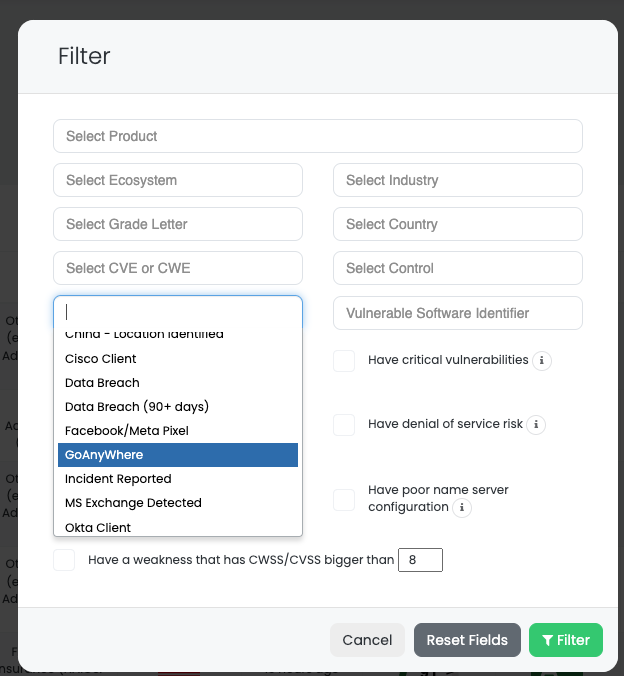
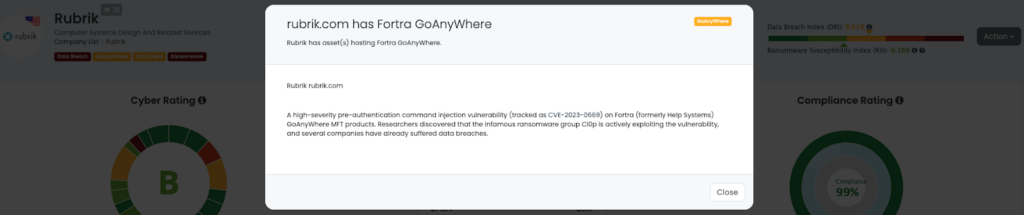
Our platform allows users to filter their vendor list using Ransomware tags, providing real-time visibility into any recent attacks that may have impacted their vendors. With Black Kite, companies can stay one step ahead of potential threats, safeguard their data, and protect their bottom line.
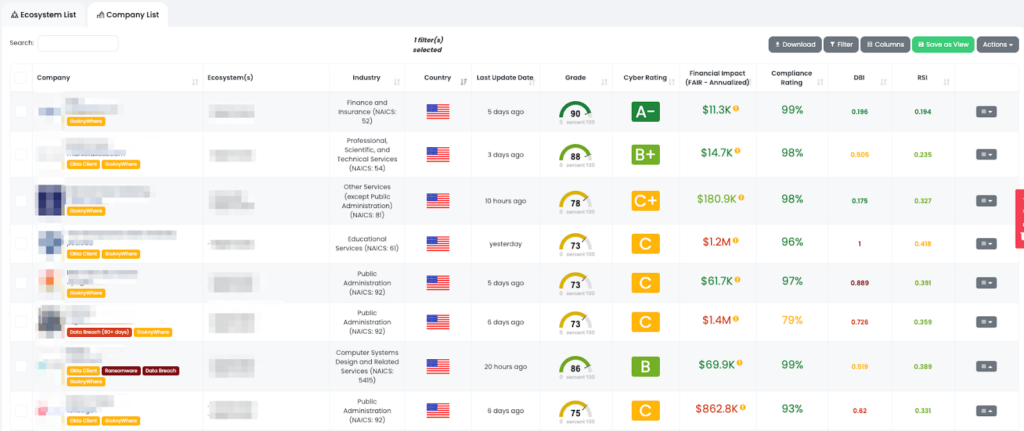
Don’t wait until it’s too late – sign up for Black Kite today and start taking control of your third-party risk management strategy.