How to Mitigate Supply Chain Cyber Risk During the China and Taiwan Conflict
Written by: ceren
Written by Ferhat Dikbiyik
Additional Contributors Yavuz Han, Ekrem Celik and Gizem Toprak
Edited by Haley Williams
Due to increasing tension between China and Taiwan after Speaker of the United States House of Representatives Nancy Pelosi’s visit, we have observed many cyber attacks between the two countries. Vendors in these countries or vendors with an IT asset in either of these countries pose an increased cyber risk within the supply chain. As a result, our customers have requested FocusTags™ dedicated to the China-Taiwan conflict.
Black Kite’s FocusTags™ are a fast and simple way for platform users to track high-profile cyber events and quickly identify which vendors have been affected within their supply chain. This capability furthers the company’s mission to provide continuous monitoring of vendors to identify and mitigate ransomware and other risks. FocusTags™ are automatically applied following high-profile cyber attacks or ongoing conflicts, but can also be added to help organize vendors in the Black Kite platform.
With this increased risk and continued tension, it is more important than ever to have a constant eye on the supply chain, monitoring any changes or increases in risk due to disclosed attacks.
The Black Kite Research team curated a list of cyber events surrounding the conflict and created a detailed timeline that can be found at the end of this article.
Cybersecurity Posture of Taiwanese Vendors
There are 250 Taiwanese companies currently being monitored by Black Kite customers. Black Kite Research also analyzed overall cybersecurity posture and Ransomware Susceptibility Index (RSI™) values for these companies. The list of Taiwanese companies are mostly chip and electronics manufacturers.
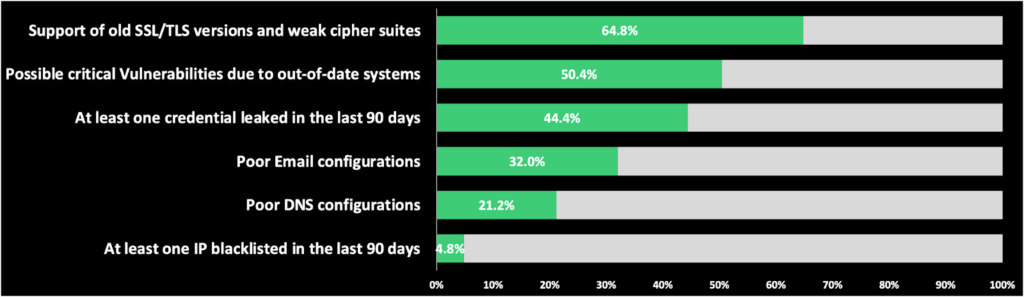
Within the 250 companies analyzed, three top vulnerabilities emerged. 64.8% of organizations currently support old SSL/TLS versions with weak cyber suites. SSL/TLS and SSH prevents intruders from tampering with communication, as well as eavesdropping on the communication that passes between the server and the user. This is especially important when sensitive data, i.e. personal information, like user credentials and payment details, are disseminated.
50.4% hold possible critical vulnerabilities due to out-of-date systems. Out-of-date systems are an obvious, but often overlooked issue, that facilitate access points for hackers to exploit. Finally, 44.4% have at least one credential leaked in the last 90 days. Once a credential is secured, leaking it on the deep web is a second step that can lead to a domino effect of risk, giving access to not only the original cyber criminal, but anyone who can find the credential.
It is also worth noting that 32% of organizations have poor email configuration, opening them up to more spoofing and phishing opportunities. A poorly-configured email service may allow an email to be delivered without authentication, appearing like it’s coming from a legitimate source. As it is the most common form of business communication, email security is critical to protect against potential breaches.
Ransomware Susceptibility
In high tension situations such as the China and Taiwan conflict, ransomware attacks become even more common toward third-parties associated with the regions in conflict. Additionally, multiple ransomware attacks towards the same company are not uncommon, particularly in situations where critical issues aren’t known or haven’t fully been resolved.
Cybercriminals target organizations that do not consistently deploy due diligence or make cybersecurity a priority within the business. Cybercriminals anticipate that security issues and vulnerabilities will remain present and exploitable if the cybersecurity investment is not adequate.
Black Kite is the only cyber ratings platform that can identify ransomware susceptibility for a
company in advance of an attack. Using data and machine learning, Black Kite’s RSI™ discovers the likelihood that an organization will experience a ransomware attack, following a process of inspecting, transforming, and modeling collected from 400+ OSINT sources (internet wide scanners, hacker forums, the deep/dark web and more).
Black Kite also utilizes data analysis techniques, the cumulative cybersecurity expertise from internal sources, specific risk factors (regional, industry-based, and organizational), and the effects of common ransomware attack vectors, including the company’s country, industry, and annual revenue.
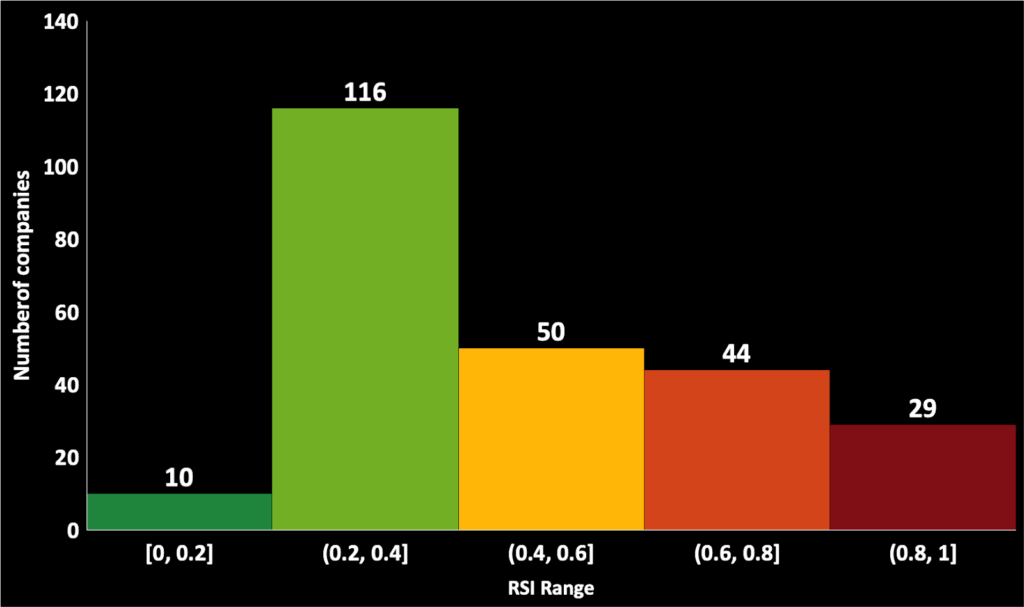
For the 250 organizations analyzed, the average RSI™ was 0.46:
- 29% had an RSI™ at or above the critical threshold of 0.6, indicating high susceptibility to a ransomware attack
- 50% had an RSI™ higher than 0.4, indicating significant susceptibility to attack
How to determine vendors that might be affected by the China-Taiwan conflict
Ongoing cybersecurity weaknesses in the supply chain further the need for continuous monitoring of high-risk vulnerabilities. Black Kite’s platform has the power to provide visibility into the cyber architecture of the supply chain and address issues that must be resolved to ensure resiliency.
More often than not, cybercriminals target your third party vendors, allowing for easier access to your internal systems and sensitive data. This includes all vendors, partners, and other third-parties, not just tier-1 or so-called ‘critical vendors’. That is why it’s imperative to monitor your entire supply chain and ensure you conduct adequate due diligence before contracting with new vendors.
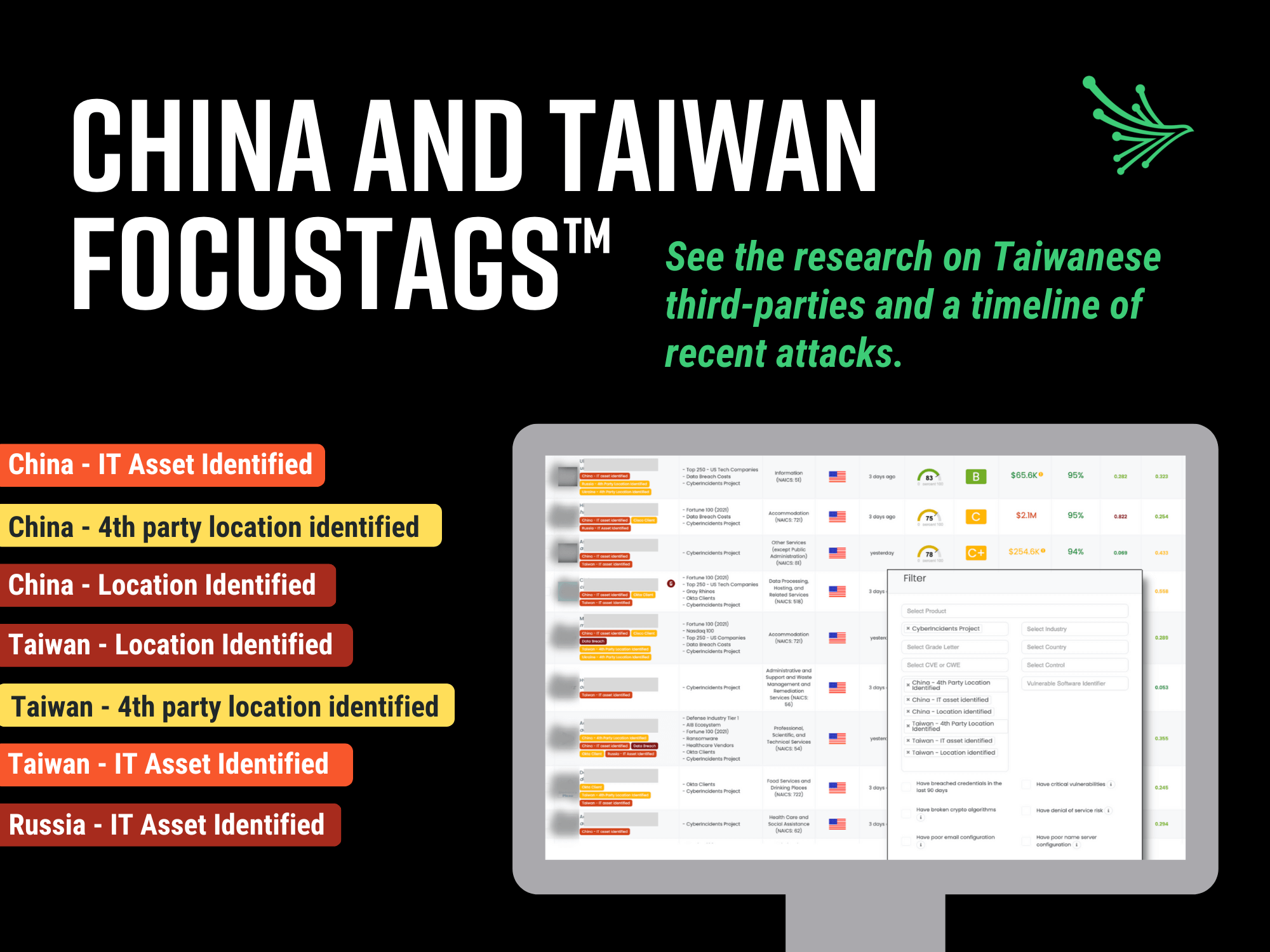
As mentioned above, we added new FocusTags™ dedicated to the China-Taiwan conflict. Similar to our geopolitical tags for the Russia/Ukraine conflict, there are six tags that have been auto-applied to affected organizations:
- China – Location identified
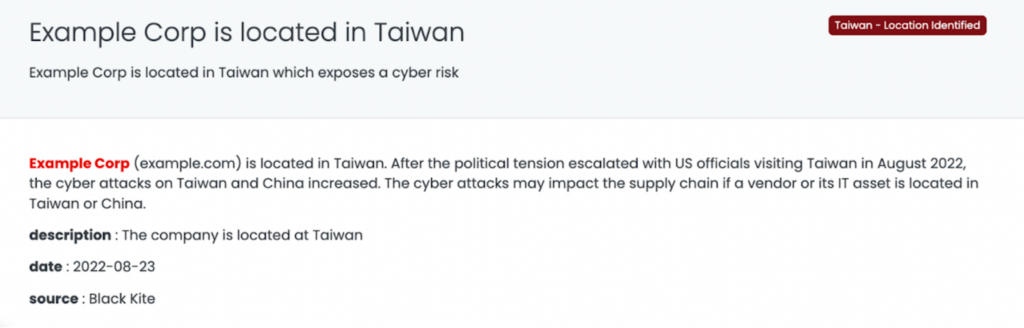
- Taiwan – Location identified
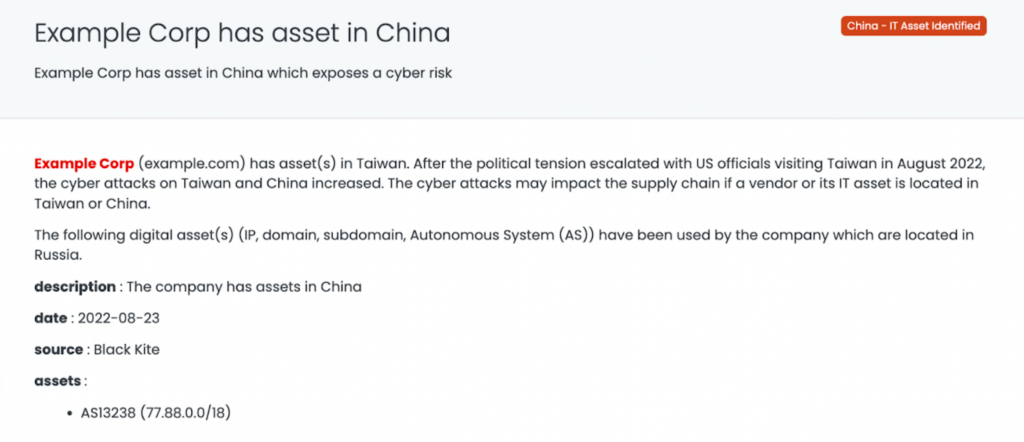
- China – IT asset identified
- Taiwan – IT asset identified
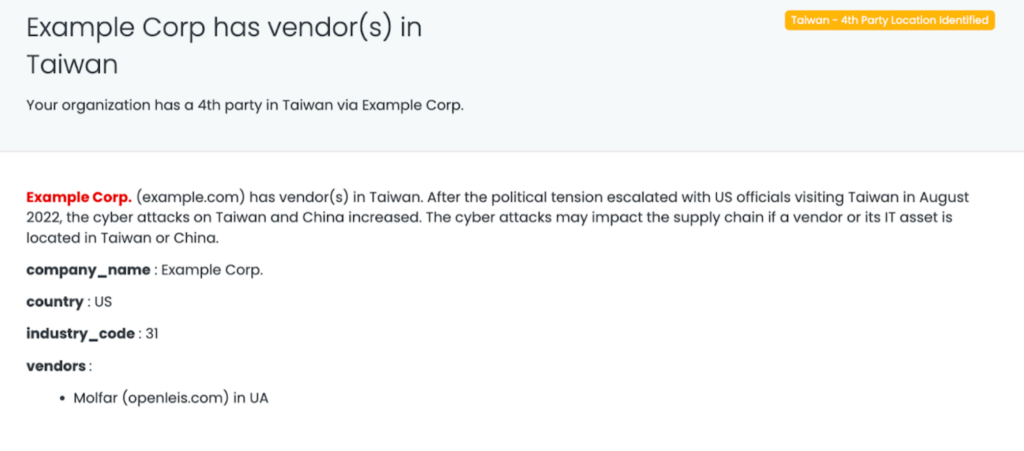
- China – 4th party location identified
- Taiwan – 4th party location identified
This tag will be used if a company’s country is China/Taiwan. These are critical-risk vendors.
This tag should be used if a company’s IT asset is in China/Taiwan. These are high-risk vendors.
This tag should be used if a vendor’s vendor is located in China/Taiwan. These are medium-risk vendors.
Reminder: Vendors in or vendors with an IT asset in either of these countries pose increased cyber risk within your supply chain.
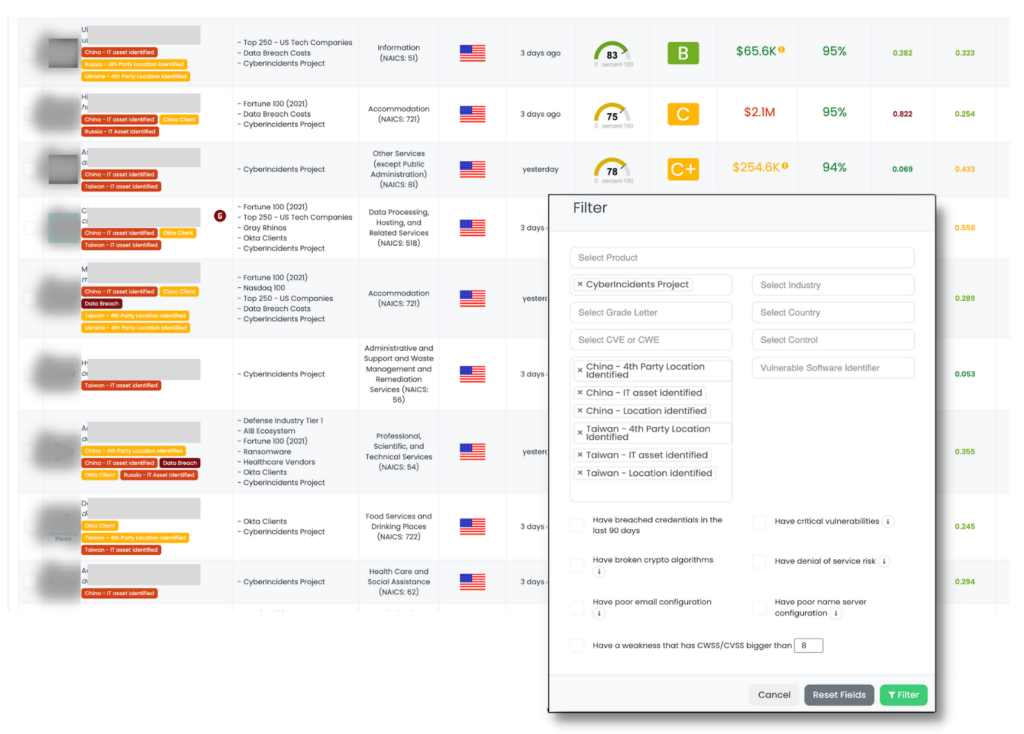
Since not all vendors will be affected, you can use the platform’s filtering functionality to narrow down which vendors have been tagged:
- Go to Ecosystems > Company List, and click on Filter
- Select the ‘Tags’ field in the pop up window
- Select any or all of the 6 China/Taiwan tags
- Click ‘Filter’
Timeline of significant cyber incidents
| Date | Target | Country | Threat Actor | Incident |
|---|---|---|---|---|
| 2022-01-04 | Heilongjiang Society Scientific Community Federation | China | Anonymous | Members of the decentralized hacktivist group Anonymous hacked into China’s Heilongjiang Society Scientific Community Federation website |
| 2022-01-14 | Polar Research Institute of China | China | Anonymous | Members of the decentralized hacktivist group Anonymous hacked into www.polar.org.cn, a Chinese government website affiliated with the Polar Research Institute |
| 2022-02-22 | Taiwan’s financial sector | Taiwan | APT10 | An advanced persistent threat (APT) group operating with objectives aligned with the Chinese government has been linked to an organized supply chain attack on Taiwan’s financial sector. |
| 2022-05-07 | Chengdu Chinese Communist Party | China | Anonymous | Hacker group Anonymous, which is primarily known for its cyberattacks, has warned China not to do anything ”stupid” against Taiwan. |
| 2022-08-02 | Taiwanese government websites | Taiwan | Unknown | Digital attacks against Taiwanese government websites ahead of U.S. House of Representatives Speaker Nancy Pelosi’s arrival in Taipei |
| 2022-08-02 | The official website of the Presidential Palace | Taiwan | Unknown | Taiwan Presidential Palace spokesperson Chang Tun-Han acknowledged this and said in a Facebook post that the official website of the Presidential Palace was attacked by an overseas DDoS attack, and the attack traffic was 200 times that of normal traffic. |
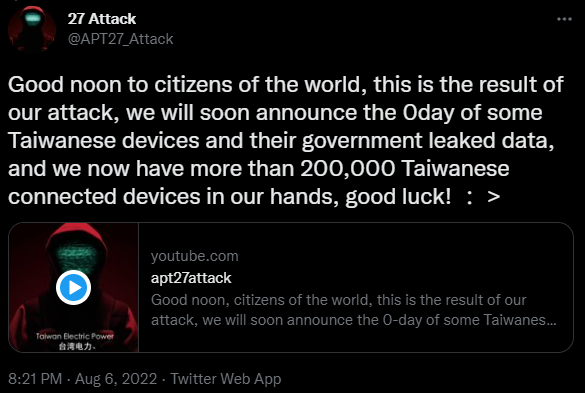
| 2022-08-03 | Taiwanese government and infrastructure systems | Taiwan | APT 27 | APT27 announced a “special cyber operation” on the Taiwanese government and infrastructure |
| 2022-08-03 | 7-Eleven | Taiwan | Unknown | Some 7-Eleven convenience stores were cyber attack |
| 2022-08-03 | Taiwan Railways Administration | Taiwan | Unknown | Cyber attack on Taiwan Railways Administration |
| 2022-08-03 | Taiwan government portal, Taiwan’s foreign ministry website | Taiwan | Unknown | Cyber attack on Taiwan government portal and Taiwan’s foreign ministry website |
| 2022-08-03 | Unknown | Taiwan | APT 27 | APT group 27 Attack claimed it had shut down 60,000 internet-connected devices in Taiwan |
| 2022-08-06 | – Taiwan Power Research Institute (source code leak) – The General Administration of Highways of the Ministry of Transportation – The Police Administration of Taiwan’s Ministry of Interior – The Presidential Office – Jinzhiyang Technology Co. Ltd (alleged) – Shennao International Co. Ltd (alleged) – Financial Information Service Co. Ltd (source code leak) – They stated that they could attack 200,000 devices connected to Taiwan | Taiwan | APT 27 | APT27 announced a new video on on August 6, 2022. They claimed that has successfully targeted the Taiwanese institutions |
| 2022-08-07 | National Taiwan University | Taiwan | Unknown | National Taiwan University hacked |
| 2022-08-10 | Formosa Television (FTV) | Taiwan | Unknown | Formosa Television (FTV) reported an intensive series of cyberattacks while China’s People’s Liberation Army conducted live-fire military exercises |
| 2022-08-08 | Taiwanese government | Taiwan | Unknown | Cyber attacks and a Chinese disinformation campaign targeting the democratic island of Taiwan throw the spotlight on Beijing’s use of hybrid warfare in the wake of Pelosi’s visit |
| 2022-08-12 | Taiwan Turns to Ethereum IPFS Tech to Thwart Chinese Cyberattacks | |||
| 2022-08-18 | Group-IB published a new report about APT41. The group’s targets include government and private organizations based in the US, Taiwan, India, Thailand, China, Hong Kong, Mongolia, Indonesia, Vietnam, Bangladesh, Ireland, Brunei, and the UK. |


Ransomware Incidents and Data Breaches Experienced by Taiwanese and Chinese Companies
Black Kite Research also discovered several ransomware attacks experienced by Taiwanese and Chinese companies. There is no solid evidence that these attacks were due to the recent conflict escalation, but they are notable attacks that should be recorded.
Ransomware Incidents
| Company | Country | Industry | Date of disclosure | Threat Actor |
|---|---|---|---|---|
| Etron Technology Inc. | Taiwan | Manufacturing | 2022-06-01 | Cuba |
| QNAP Systems | Taiwan | IT Services and IT Consulting | 2022-06-18 | ech0raix |
| Shenzhen Institute of Building Research | China | Construction Services | 2022-06-21 | Lockbit 2.0 |
| Linmark | China | Wholesale | 2022-06-22 | Lockbit 2.0 |
| SuperAlloy Industrial Co. Ltd. | Taiwan | Manufacturing | 2022-06-28 | Hive |
| Sin Sheng Terminal and Machine Inc | Taiwan | Manufacturing | 2022-07-07 | Cuba |
| Shanghai Hanbell Precise Machinery | China | Manufacturing | 2022-07-11 | Karakurt |
| Cpicfiber | China | Manufacturing | 2022-07-19 | Locbit 3.0 |
| Yong Mao Environmental Tech. Co.,Ltd | Taiwan | Manufacturing | 2022-07-23 | Locbit 3.0 |
| YMA Corporation Carbon Fiber & Composites | China | Manufacturing | 2022-07-26 | Locbit 3.0 |
| ENN Group | China | Utilities | 2022-08-04 | Hive |
| Fosun International | China | Multiple industry | 2022-08-09 | Locbit 3.0 |
| Torin Drive | China | Manufacturing | 2022-08-29 | BlackByte |
Data Leaks
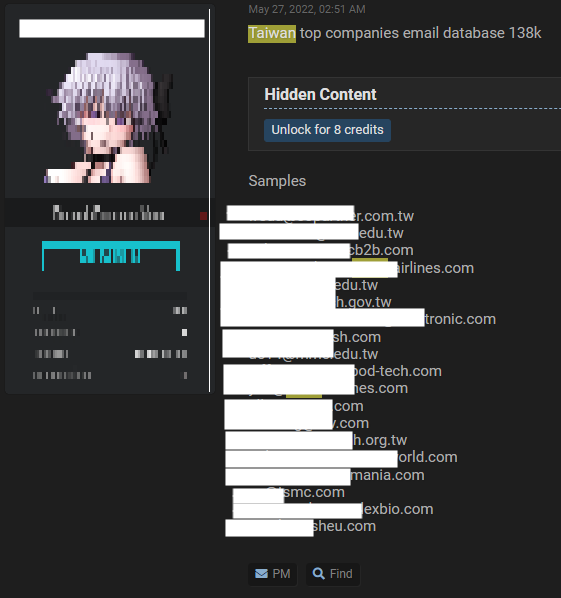
| Date | Information |
|---|---|
| 2022-05-27 | Data leak about Taiwan top companies email databases (110K) |
| 2022-06-24 | China loan information Database leak (80K records) |
| 2022-07-03 | Phone numbers and names data leak about Taiwan (100K) |
| 2022-07-10 | Data leak on Taiwan’s military leaders (783 lines) |
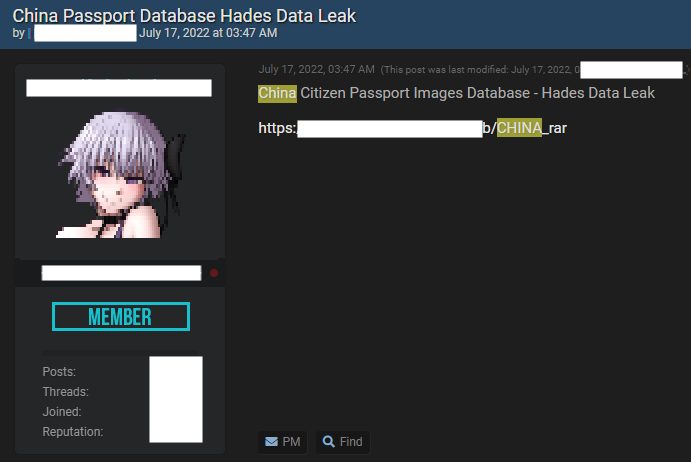
| 2022-07-17 | China Passport Database – Hades Data Leak |
| 2022-08-12 | Data leak on ZTE Corporation -China- (by AgainstTheWest) |
Get A Free Vendor Risk Assessment Today
Black Kite offers a free vendor assessment here. Act now and request your free vendor assessment to see the possible impacts of the China Taiwan tension in cyberspace on your supply chain.
Risk AssessmentReferences
- https://www.jpost.com/international/article-713896
- https://thehackernews.com/2022/02/chinese-hackers-target-taiwans.html
- https://www.wionews.com/world/dont-try-anything-stupid-against-taiwan-hacker-group-anonymous-warns-china-477038
- https://www.reuters.com/world/attacks-taiwan-websites-likely-work-chinese-hacktivists-researchers-2022-08-02/
- https://www.facebook.com/100044311095166/posts/pfbid02s2Ni3Wb24L1DPYeGhWAUd1wKBDY9GEn7hRCtx5VRZTUmFybY47ozvxNxkMgRNcFnl/?d=n
- https://www.youtube.com/watch?v=nReXcIEqNqE
- https://www.indiatoday.in/world/story/cyber-attacks-on-taiwan-china-caught-in-its-own-tangle-1984633-2022-08-06
- https://www.reuters.com/technology/7-11s-train-stations-cyber-attacks-plague-taiwan-over-pelosi-visit-2022-08-04/
- https://voi-id.translate.goog/zh/technology-zh/197227/read?_x_tr_sl=zh-CN&_x_tr_tl=en&_x_tr_hl=en&_x_tr_pto=sc
- https://www.reuters.com/technology/7-11s-train-stations-cyber-attacks-plague-taiwan-over-pelosi-visit-2022-08-04/
- https://www.youtube.com/watch?v=mOyUd85LlaM
- https://www.taiwannews.com.tw/en/news/4619255
- https://www.taipeitimes.com/News/taiwan/archives/2022/08/11/2003783346?&web_view=true
- https://www.rfa.org/english/news/china/taiwan-cyber-08082022125442.html
- https://twitter.com/DailyDarkWeb/status/1558928473418235906/photo/1