CMMC 2.0: Compliance Made Simpler for DoD Contractors
Written by: Black Kite
The US Defense Industrial Base (DIB) has already gone down a few paths on its journey to achieving national digital supply chain security. Although the original Cybersecurity Maturity Model Certification (CMMC) framework took nearly two years to develop, the introduction brought with it many concerns over its stringency and complexity.
The latest version, “CMMC 2.0” includes a few major revisions that will alleviate some of the stringent requirements mandated in the previous model. The overarching goal for CMMC, however, remains the same: implement basic cyber hygiene standards to safeguard sensitive data and champion cyber resilience on a national scale.
What’s new in CMMC 2.0?
The new-and-improved CMMC 2.0 map suggests a simpler, less expensive road ahead. According to the U.S. Department of Defense (DoD) changes include:
- Simplifying the CMMC standard and providing additional clarity on cybersecurity regulatory, policy, and contracting requirements;
- Focusing the most advanced cybersecurity standards and third-party assessment requirements on companies supporting the highest priority programs; and
- Increasing Department oversight of professional and ethical standards in the assessment ecosystem.
Source: https://www.acq.osd.mil/cmmc/assessments.html
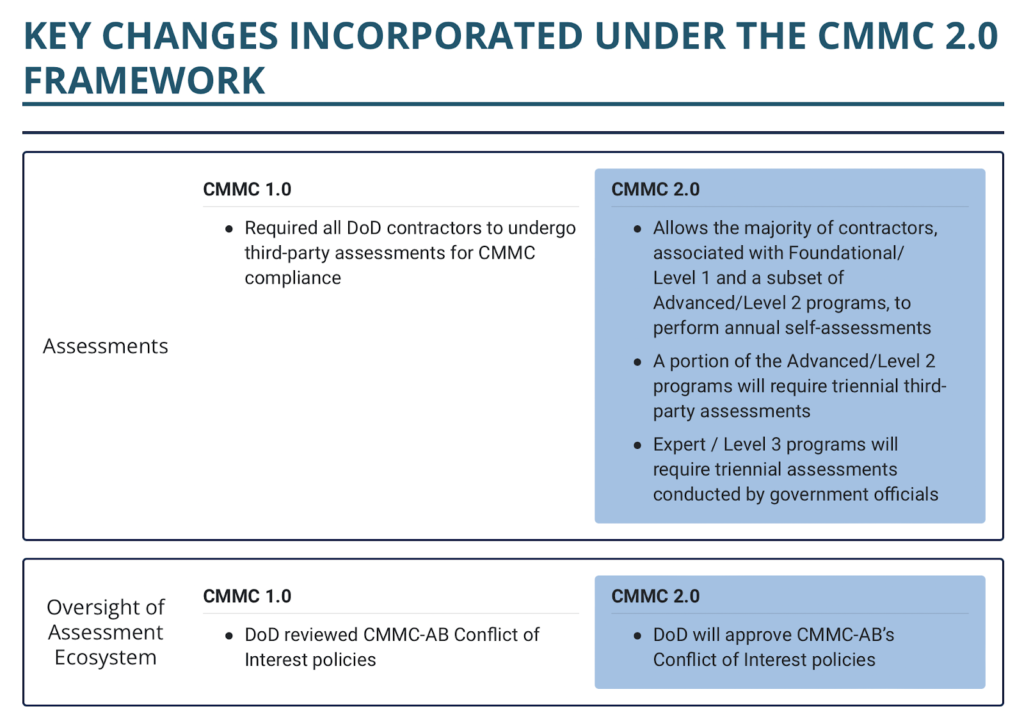
The CMMC 2.0 Framework Makes it Easier with 1-2-3.
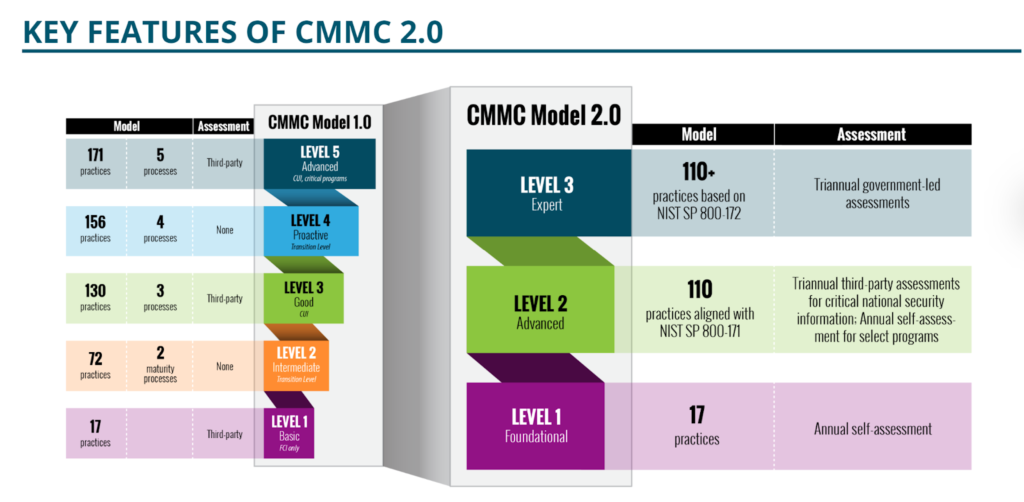
Transition levels for DIB contractors are no longer a part of the CMMC framework. Instead of the five compliance levels presented in CMMC 1.0, CMMC certifications now fall under one of three scopes that are aligned with the National Institute of Standards and Technology (NIST) cybersecurity framework: Foundational (Level 1), Advanced (Level 2) and Expert (Level 3).
Source: https://www.exostar.com/solution/about-cmmc/
CMMC Level 1 Compliance:
The foundational level of 2.0 retains the same 17 practices for defense contractors that do not handle critical information. However, this basic cyber hygiene level now permits annual self risk assessments, as opposed to independent validation mandates.
CMMC Level 2 Compliance:
Similar to v1.0 Level 3, the middle tier requires triannual third-party assessments for organizations that store and share Controlled Unclassified Information. New to the modified version is the exception of annual self-assessments for select programs. Although it still aligns with 110 practices under NIST SP 800-171 framework, the middle tier has also toned back by eliminating the 20 additional security controls in v1.0.
CMMC Level 3 Compliance:
Formerly known as CMMC Level 5, the expert tier now only includes 110+ practices that fully embrace the NIST SP 800-172 guidelines. The new Level 3 requires a triennial assessment that is led by the government to optimize security.
When will CMMC 2.0 go into effect?
These changes [2] will go into effect when the title 32 CFR and title 48 CFR rulemaking processes are complete. Rulemaking can take up to 2 years to fully complete, but details on the rollout to defense contractors have not been fully released at this time.
However, what is the one thing we reiterate over and over again? Proactivity. The time to start implementing these new requirements is not months before the rulemaking completion. It is now.
“Don’t wait for this to be a requirement in your contract,” said Matthew Travis, the CMMC Accreditation Body’s CEO. “Go ahead, engage in CMMC and get certified.” [3]
Starting early and getting CMMC certified to the new standards allows you to communicate to your customers, and even the competition, that you are taking cybersecurity measures seriously. Additionally, being fully up to date with the latest security controls facilitates prioriting proactivity in your defense strategy and compliance journey – these processes take time.
“Get your assessment on schedule now, because it’s going to start getting booked up,” said Robert Teague, manager of CMMC services at Redspin, “The longer you wait, the more jeopardy you place yourself in on bidding on contracts with CMMC language.” Get ahead of the curve– the rulemaking could conclude quicker than anticipated and demand will be high.
References
[2] https://dodcio.defense.gov/CMMC/Model/
[3] https://www.nationaldefensemagazine.org/articles/2022/1/4/industry-told-not-to-wait-for-cmmc-accreditation
Black Kite allows you to measure the compliance level of any company for different regulations and standards, including NIST SP 800-171, ISO27001, PCI-DSS, HIPAA, GDPR, Shared Assessments, and others. See how our platform can help prepare for CMMC certification.
Request a demoCMMC in Six Questions: What to Know About the Cybersecurity Maturity Model Certification
As one of the one of the largest supply chains in the world, The U.S. Department of Defense (DoD) ecosystem consists of over 300,000 companies. While private companies are essential elements in these supply chains as a source of innovation and high-value solutions, they do introduce their own set of cybersecurity issues and risks.
According to the DoD, about $600 billion worth of data is stolen per year by foreign adversaries from supplier information systems. Given that many cybersecurity incidents go undetected or underreported, incidents such as SolarWinds are only the tip of the iceberg. In response, the CMMC has paced the development of its cybersecurity framework published early last year.
As an addition to new, government-wide acquisition contracts, CMMC requirements will be included on a task-order by task-order basis, specifying the required level of maturity for a specific contractor. But, what exactly does CMMC address? What are the goals and maturity levels about?
What is CMMC?
Created as a response to the evolving cyber threat landscape, the “Cybersecurity Maturity Model Certification”, or CMMC, is an overarching standard for the implementation of cybersecurity across the Defense Industrial Base (DIB) and federal contractors. It’s also backed by federal universities and institutions, cybersecurity vendors, subject matter experts, as well as research and development centers across the country.
What is the goal of CMMC?
The goal of CMMC is to heighten and unify cybersecurity standards across the U.S. DoD supply chain. Through CMMC, DIB firms and their associated suppliers, vendors and other third parties will be required to implement proper practices and processes designed to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
In addition to embracing all well-known federal cybersecurity frameworks including NIST SP 800-171, NIST SP 800-53, ISO 27001, ISO 27032, and AIA NAS9933, CMMC will also require DoD contractors to implement external security audits. This tactic is hoped to prevent cybercriminals from accessing high-value entities through weaker links across the supply chain.
Who needs to be compliant with CMMC?
CMMC will impact any company that does business with the DoD. Today, the U.S. defense supply chain is made up of thousands of companies that play either a direct or indirect role in its operations. Both primary contractors and subcontractors will be required to maintain one of the designated security levels. It is envisioned that all contractors will be assessed annually and certified by October 1, 2024.
Would compliance with CMMC prevent an attack like SolarWinds?
With the increasing complexities associated with today’s digital supply chains, completely safeguarding an entire network against cyber attacks is virtually impossible. Although CMMC compliance would not thwart an intrusion entirely, it does enable early threat detection, equipping organizations to remain vigilant and minimize disruption in the event a vulnerability is discovered.
CMMC will be one of the tools that will be employed by the federal government to help address threats against them and the private sector.
What are the five levels in CMMC?
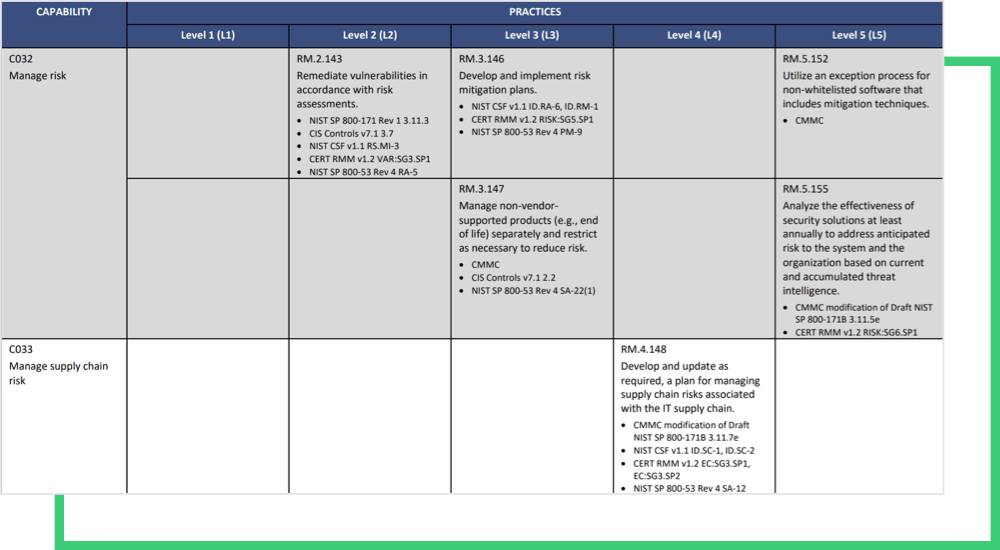
CMMC categorizes cybersecurity best practices and processes into five degrees of maturity. Processes range from basic (CMMC Level 1), to optimal, robust strategies (CMMC Level 5). Depending on the level of sensitivity of information stored in the system, as well as the particulars of the federal program being supported, organizations will be required to, at minimum, contain a novice cyber structure.
Consider the risk management process as an example. Starting at Level 2, risk management maturity begins with practices like “periodically assess the risk to organizational operations, assets”, and increases up to Level 5 with “utilization of an exception process for non-whitelisted software” and “analysis of the effectiveness of security solutions” practices.
How does CMMC address supply chain risk?
Again, CMMC was designed to harden security across the entire defense supply chain. Beginning with Level 4 Risk Management Maturity, supply chain risk management becomes an integral part of the risk management process.
CMMC compliance will be a marathon, not a sprint. Those that fall under the mandate should start assessing their preliminary maturity levels today. Not only will it help organizations by preparing them for the audit, compliance assessments can also identify any gaps in their cybersecurity that could disrupt their supply chain in the interim.
Ready to get started? Discover what Black Kite offers for CMMC compliance.
Learn more
