Your Friendly Neighborhood Ransomware Syndicate Will See You Now
Written by: Dr. Ferhat Dikbiyik, Chief Research & Intelligence Officer
From corporate-sounding breach statements to templated negotiations and ESXi support, LockBit blurred the line between cybercrime and customer service — until they were hacked themselves.
If you’ve ever imagined ransomware gangs as chaotic bands of hoodie-wearing hackers launching attacks from the shadows, LockBit would like a word — preferably via encrypted chat, with structured pricing, timezone-aware support, and test decrypts to elp you “experience the product” before buying.
LockBit operates with a surprising level of business sophistication, offering structured pricing, customer support, and even test decrypts. This article details their corporate-like breach announcement after being hacked themselves, their tiered negotiation tactics, and their understanding of enterprise IT environments like ESXi. Ultimately, defenders need to recognize this business-like approach to ransomware in order to better anticipate and prevent future attacks.
LockBit Is All Business
After being hacked themselves on May 7, 2025, LockBit released a statement so polished it could’ve been run through a corporate PR team:
“I’m currently investigating how the breach happened and rebuilding the system… no decryptors or any stolen company data were harmed. The full panel and blog are still operational.”
They even offered to pay for intel on the perpetrator (“xoxo” from Prague) — a move eerily reminiscent of a bug bounty program, though they may have just misread a cheeky “hugs and kisses from Prague” sign-off as a hacker’s handle.
Yes, you read that correctly.
This isn’t just ransomware. It’s ransomware-as-a-business.
And if LockBit had an investor pitch deck, I wouldn’t be surprised if it included growth charts and an affiliate referral program.
But that’s the thing: LockBit wasn’t just a criminal enterprise. It was a business. A brand. A platform.
And just like any startup past its prime, it had structured pricing, technical documentation, customer onboarding…and a spectacular fall.
From Peak Power to a Platform Breach
Before Operation Cronos dismantled parts of its infrastructure earlier this year, LockBit was the reigning king of ransomware. They leaked data from over 200 victims per month, supported hundreds of affiliates, and ran a criminal operation with all the polish of a B2B tech firm.
After Cronos, that number dropped to single digits per month. Many affiliates walked away. And when LockBit got breached themselves, the mask slipped, revealing not just their systems, but their business logic.
The leaked negotiation chats read less like ransom demands and more like CRM transcripts.

How to Sell a Ransom, LockBit Style
LockBit’s chats followed a consistent rhythm: name your price, offer a taste, apply pressure, close the deal. Sound familiar?
1. Negotiation, But Make It Tiered
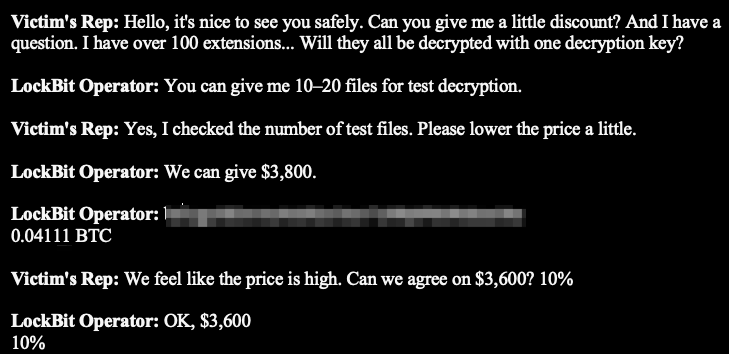
One small business pleads:
“We feel like the price is high. Can we agree on $3,600?”
LockBit’s response?
“Ok, $3600” (reduced from $4,000)
But after an initial discount, they’re not here for haggling:
“no”
“There will be no more talk about discounts.”
Ransom pricing was neatly aligned with perceived company size:
- Small businesses: $1,500–$4,000
- Mid-sized companies: $30K–$70K
- Large enterprises: $100K–$150K+
Total across all negotiations: $767,800
Average ask: $40,410
This isn’t chaos. It’s value-based pricing.
2. Customer Service Scripts, with Encryption
“You can attach a few files for test decryption by packing them into an archive…”
“Please wait for a reply, sometimes it takes several hours due to possible time zone differences.”
These lines appear over and over — clearly copy-pasted.
We’re not dealing with improvisation here. We’re dealing with internal playbooks and canned responses. Like Zendesk, but for extortion.
3. Trust-Building with Freemium Tactics
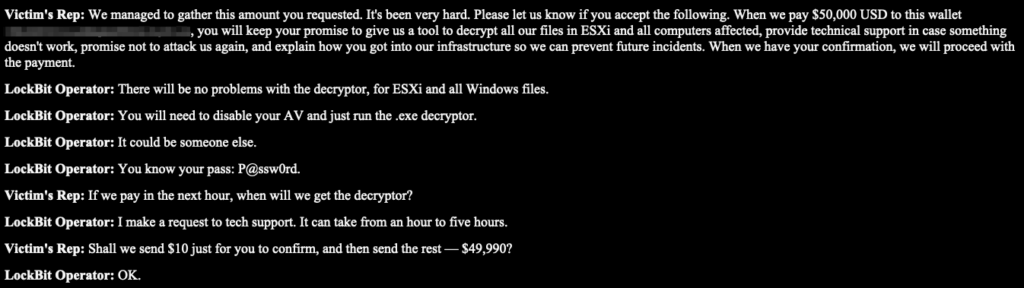
Need proof that the decryptor works? No problem.
“We can decrypt few random files for FREE.”
“You will need to disable your AV and just run the .exe decryptor.”
That’s not just social engineering. That’s product-led growth.
4. Fear, Shame, and a Bit of Taunting
In one case, a desperate employee begs:
“Please don’t spoil my life… My company will file a case on me… My family will be suffered.”
LockBit replies coldly: “I can’t help you, it’s to end this dialog.”
Elsewhere, they mock:
“You know your pass: P@ssw0rd”
They don’t just threaten. They undermine your confidence.
5. Targeted Pressure, Personalized Pricing
LockBit tailors its tactics to your environment:
“We found a lot of contact information of your employees, clients, partners…”
“We will try to convey information about the leak to each of these contacts.”
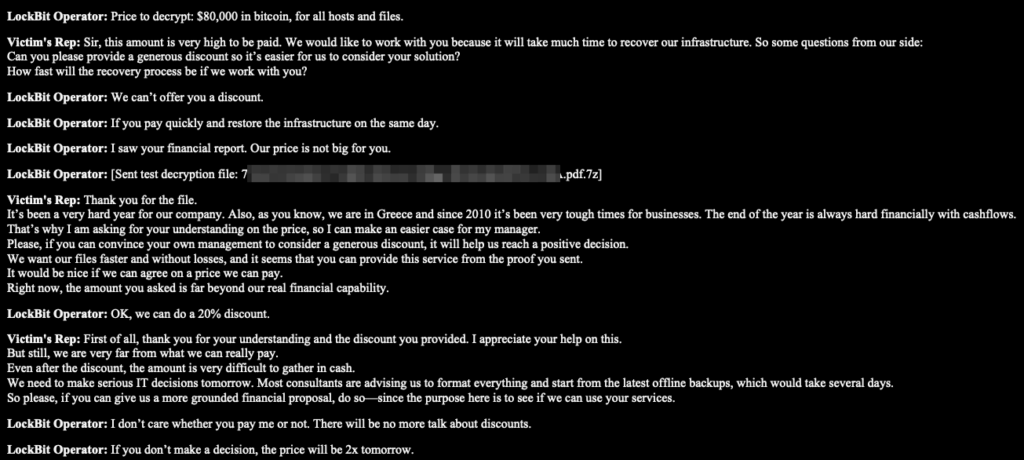
And if you’re rich?
“I saw your financial report. Our price is not big for you.”
“The price…was formed based on the indicators of your company.”
This is market segmentation, but for criminal revenue.
6. Enterprise IT Support… from Criminals
Need to decrypt an ESXi cluster? LockBit’s got you.
“Log in to vCenter, enable SSH, upload decryptor… run ./decrypt… check decrypt.llg log…”
“Do not run multiple decryptors simultaneously… or files may be corrupted.”
We’ve seen fewer steps in vendor documentation.
These actors understand virtualization, backup systems, and endpoint behavior.
This isn’t script kiddie territory. This is ransomware with release notes.
The Breach Heard Around the Dark Web
When LockBit got breached, the illusion cracked.
They scrambled to assure “customers” that nothing critical was lost, systems were being rebuilt, and operations were ongoing. The message, minus the extortion and anonymity, would be right at home in an AWS status update.
The offer to pay for intel on “xoxo from Prague” (which again, might’ve just been a sarcastic sign-off) cemented the absurdity: even ransomware groups are vulnerable to phishing and misinterpretation.
They were so committed to acting like a business… they ended up reacting like one too.
Lessons for Defenders
So what now?
LockBit may be on the decline, but the playbook they wrote will outlive them. And the next ransomware “startup” will come with better UX, faster support, and cleaner infrastructure.
To stay ahead, we need to:
- Monitor for ransomware susceptibility, not just breaches
- Assess vendor-level risk posture, continuously
- Recognize criminal operations behaving like product teams
At Black Kite, we’ve developed tools like the Ransomware Susceptibility Index® (RSI™) and FocusTags™ to help our clients and their vendors stay ahead of this evolution — not just after an incident, but before they become one.
Because if ransomware syndicates are going to act like businesses, it’s time we start treating them like competitors — not just criminals.
Read our full 2025 Supply Chain Vulnerability Report: Navigating a New Era of Managing Vulnerability Risk in Third Parties – accessible instantly, no download required.

