What is a Cyber Ecosystem?
Published
Oct 3, 2023
Updated
Jan 27, 2026
Authors
Black Kite
Much like a physical ecosystem, a cyber ecosystem is composed of entities that interact with each other to form one functioning unit—only these ecosystems are linked to each other digitally rather than physically. Your organization sits at the core, while the entities surrounding it are your vendors, suppliers, and other third parties.
Also similar to the natural world, the ways in which cyber entities interact constantly evolve and become more dependent on each other. A cyber ecosystem thereby creates a target-rich environment for cyber criminals to exploit vulnerabilities to steal personal data and identities, and even company secrets. We’re seeing this play out in real-time, with frequent announcements of data breaches in the news.
It’s important to have a comprehensive view of your entire cyber ecosystem—including the risk each individual vendor introduces— to help you make more informed, strategic decisions around your cybersecurity strategy.
The Ripple Effect Within Your Cyber Ecosystem
The biggest difference between physical and virtual communities is that the digital landscape evolves at a much more rapid pace. Threat actors have proved to be more adaptable than complex supply chains and have diverted their focus to prey on weaker links that can create a ripple effect reaching larger, more sought-after organizations.
Consider the SolarWinds attack that fueled the shift in the conversation around third-party risk management (TPRM). Through one shared vendor, the cybercriminal group potentially accessed 85% of the U.S. Fortune 500, all five branches of the military, hundreds of universities and colleges, and many more… and that’s just one supply chain attack.
Since the SolarWinds incident, we’ve recorded dozens of major third-party data breaches each year.
Major Attacks Against Supply Chains in Recent Years
- In 2021, bad actors leveraged Accellion’s third-party transfer application, obtaining patient health information (PHI), customer and stakeholder data, personally identifiable information (PII), and more from hundreds of organizations, including Shell, University of Miami Health, and Kroger.
- In 2022, Toyota was forced to stop production when Kojima Industries—a vendor with access to Toyota’s Kanban just-in-time production system—experienced a data breach that spilled over into the automaker’s ecosystem.
- In 2023, a third vulnerability was uncovered in the file transfer software, MOVEit, which allowed hackers to escalate their privileges through SQL injections. Victims included the U.S. Department of Energy, British Airways, and the BBC, among many others.
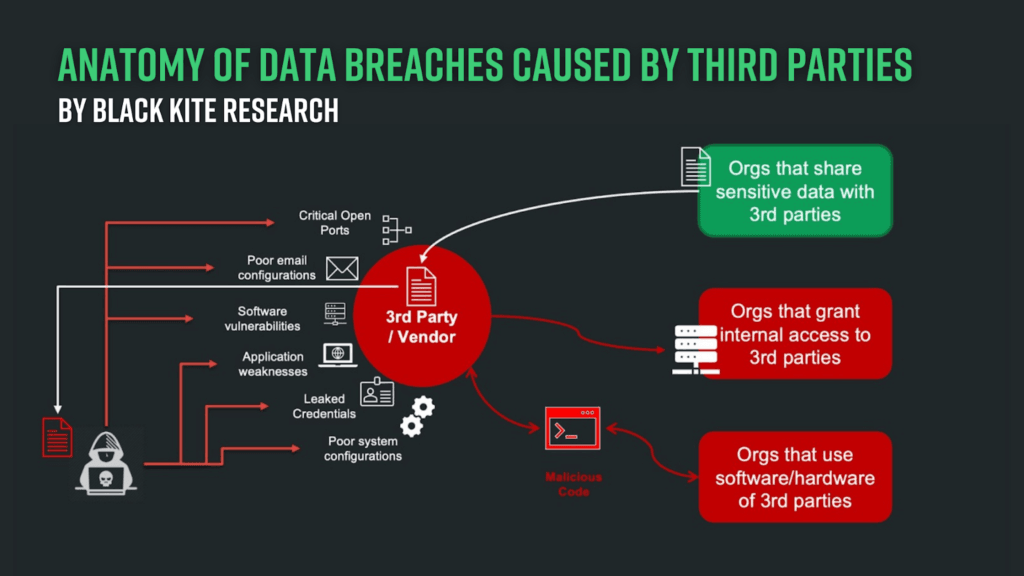
Growing Threats on Digital Supply Chains
Threat landscapes continue to transform alongside their digital supply chains. Now sitting at the top of the digital “killchain,” ransomware attacks have become top-of-mind for organizations across the globe.
In our Ransomware Threat Landscape Report, we found that ransomware victims almost doubled between April 2022 and March 2023. The most common targets were organizations with an annual revenue of $50 to $60 million, as well as those in the manufacturing and professional, scientific, and technical services industries.
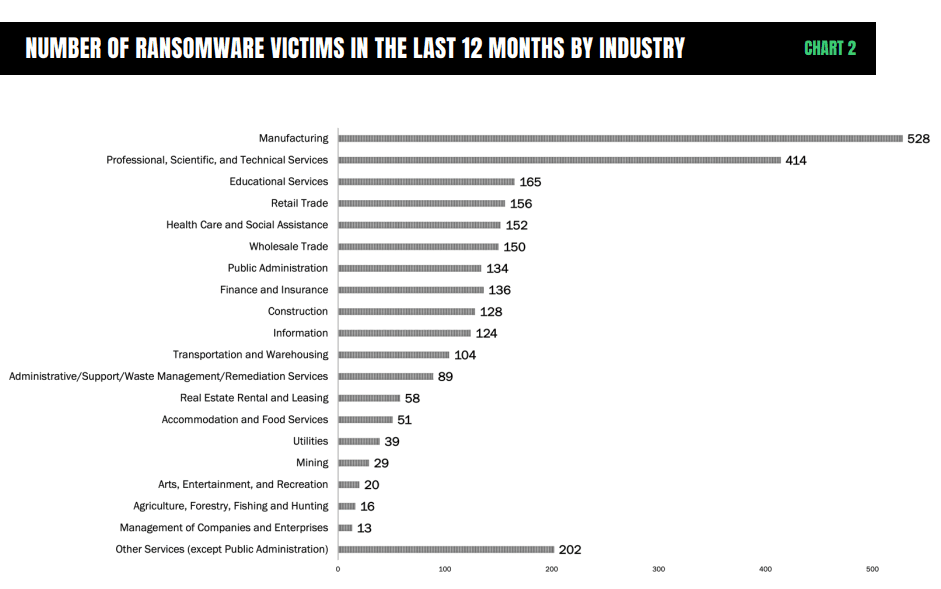
Learn more about the evolving threat of ransomware in our 2023 Ransomware Threat Landscape Report.
Security professionals across industries are struggling to keep pace with these evolving threats, due in part to the outdated tools and methods they’re currently using to evaluate risk in their cyber ecosystem. Manual processes are time-consuming and prone to human error, and there’s simply no way they can keep up with the rate of change in the modern threat landscape. Traditional solutions, such as questionnaires and security rating services, often struggle to provide organizations with the contextual insights businesses require to make effective business decisions.
As a result, many organizations remain vulnerable to supply chain threats. And, unfortunately, the true magnitude of a cyber incident is devastating, especially when you consider both primary losses, such as ransom payouts and the cost of investigation, and secondary losses, like regulatory fines and damage to the brand.
How to Protect Your Cyber Ecosystem
During periods of disruption, adaptation is critical to survival. Implement modern cybersecurity best practices to ensure your digital community doesn’t find itself on the wrong side of natural selection:
1. Maintain Robust Cybersecurity Standards Across Your Supply Chain
Cybersecurity is a critical determining factor when conducting third-party transactions and business engagement. Supply chains become more complex each day. Implementing strong third-party risk management standards today creates a stronger foundation to mature supply chain security tomorrow.
Hold your vendors to the same standards you maintain internally and prepare a list of must-ask questions including.
- Do you have a formal security framework?
- What is your software security policy?
- Do you have controls in place for sharing sensitive information?
2. Know Where Your Weakest Links Are, and Address Those First
Unlike physical security, the interconnected nature of modern cyber networks makes it virtually impossible to detect and address all vulnerabilities. You don’t need everyone to be ahead of the pack, you do have to be mindful of the weaker links within your cybercommunity.
While traditional cyber ratings can provide a general sense of an organization’s cyber hygiene, they don’t provide a sense of risk to your organization specifically. By combining cyber ratings with other qualitative and real-time data, you can illuminate your cyber ecosystem and reduce exposure.
3. Adopt a Security-First Culture all the Way to the Top
A growing threat landscape inherently presents greater responsibility, so it’s no coincidence that 70% of boards of directors will include a cybersecurity leader by 2026. Bonus points will go to the cybersecurity leaders who have the ability to quantify the organization’s cyber risk in dollars and cents to help executives understand what’s really at stake. By bringing leadership and security together, organizations can improve their ability to evaluate risk and take action to protect their customers and company.
Partner with Black Kite to Enhance Your Cybersecurity Strategy
Black Kite provides a bird’s eye view of your cyber risk, including every vendor in your supply chain. Our platform is powered by AI, gathering, analyzing, and validating data from over 400 external sources, ensuring the insights are both accurate and contextualized. With Black Kite, you can make more informed and strategic decisions around your cyber ecosystem.