Understand Supply Chain Risk Susceptibility to Prevent New Microsoft Exchange Server Ransomware Attacks
Written by: Black Kite
Microsoft Exchange Server’s large market share makes it a popular target for constantly evolving threat actors and ransomware gangs. LockFile is one of the most recent threat actors, or ransomware families, to take advantage of new Microsoft Exchange Server vulnerabilities.
August 25th Advisory
Microsoft issued an advisory on the aforementioned Exchange Server vulnerabilities stating that if customers installed the May 2021 security updates or the July 2021 security updates on the servers, they are protected from these vulnerabilities. According to the Microsoft Exchange team, customers with any of the below security issues are vulnerable:
- The server is running an older, unsupported CU (without May 2021 SU)
- The server is running security updates for older, unsupported versions of Exchange that were released in March 2021
- The server is running an older, unsupported CU, with the March 2021 EOMT mitigations applied
The advisory states it is always critical to keep the Exchange servers updated with the latest available Cumulative Update (CU) and Security Update (SU to be protected against the recent threats.
What we know about new threat actor LockFile
LockFile ransomware attacks are focusing on organizations in financial services, manufacturing, legal, business services, engineering, travel, and tourism. Recent activities show that LockFile is taking advantage of its victims by leveraging the new Microsoft Exchange Server vulnerabilities ProxyShell and PetitPotam.
More on the ProxyShell Vulnerability / Black Hat as Catalyst
ProxyShell consists of three vulnerabilities chained together that result in unauthenticated remote code execution (RCE) on Microsoft Exchange servers. These vulnerabilities are being tracked as:
- CVE-2021-34473 – ACL Bypass (Patched in April by KB5001779)
- CVE-2021-34523 – Elevation of Privilege (Patched in April by KB5001779)
- CVE-2021-31207 – Arbitrary-File-Write causes RCE (Patched in May by KB5003435)
Microsoft fully patched these vulnerabilities in May 2021. However, once the details of the ProxyShell attack were disclosed at Black Hat this past August, honeypots observed hackers scanning the internet for these vulnerabilities.
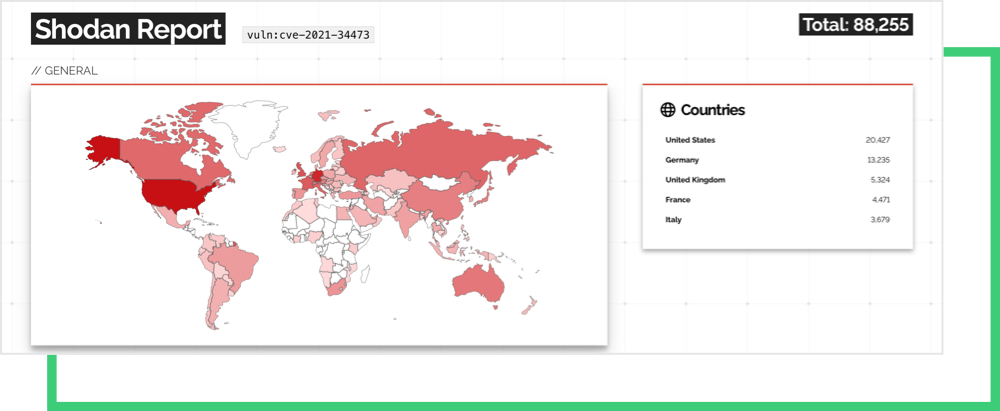
The recent advisory issued by Cybersecurity Infrastructure & Security Agency (CISA) was flagged as “urgent” and for good reason. According to Shodan.io, there are over 88,000 devices worldwide open to the public with this vulnerability, with about 20,000 of them based in the U.S.
Opening the Door for PetitPotam Vulnerability
Once Microsoft Exchange Server is successfully breached via ProxyShell, threat actors like LockFile drop in web shells to upload and run other applications, like the PetitPotam payload. A relatively new vulnerability released by the French researcher Gilles Lionel a.k.a topotam, PetitPotam is a type of NTLM relay attack and is hitting organizations across manufacturing, financial services, engineering, legal, business services, and travel and tourism. PetitPotam, being tracked as CVE-2021-36942, appears to be copied from https://github.com/zcgonvh/EfsPotato.
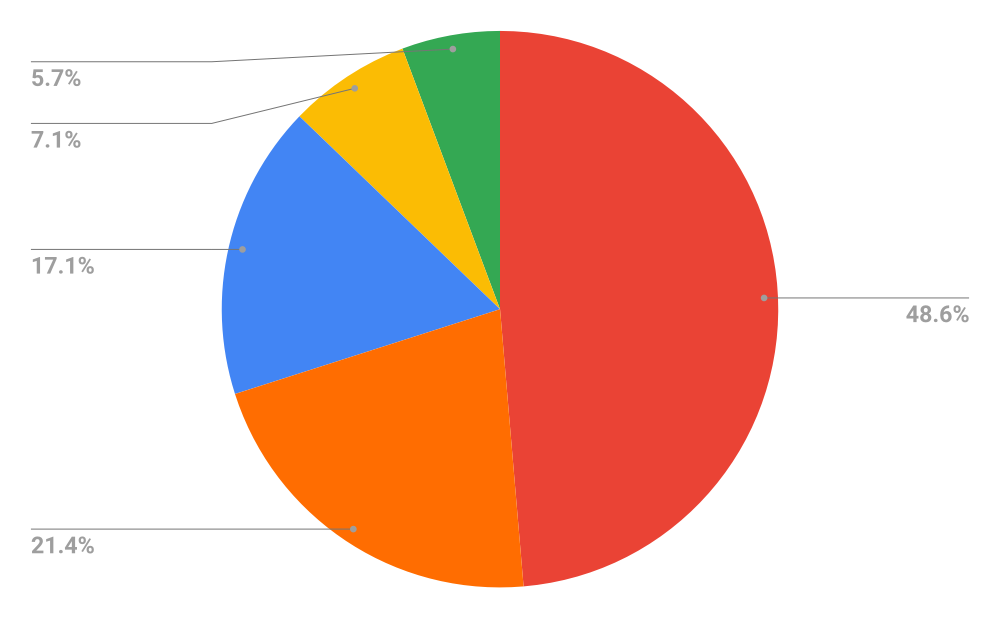
Upon the initial analysis in the Black Kite platform, 12% of the companies scanned were exposed to the PetitPotam vulnerability, a surprisingly high amount. This result is likely due to the immediacy of the findings, as the majority of the companies were not yet aware of the issue, much less had time to mitigate the problem.
Black Kite researchers discovered the technology and finance sectors were the most vulnerable sectors, as seen in the following chart. Both of these industries are known for large quantities of digital assets exposed to the internet, therefore requiring more vulnerabilities to be managed. Nevertheless, cyber trends indicate hackers do not discriminate among sectors, rather they behave opportunistically.
Using PetitPotam, attackers take over the domain control to obtain elevated access in the victim’s network, forcing authentication to a remote NTLM relay. Once the attackers gain access to the domain controller, they have absolute ownership of the Windows domain and can execute any command they want.
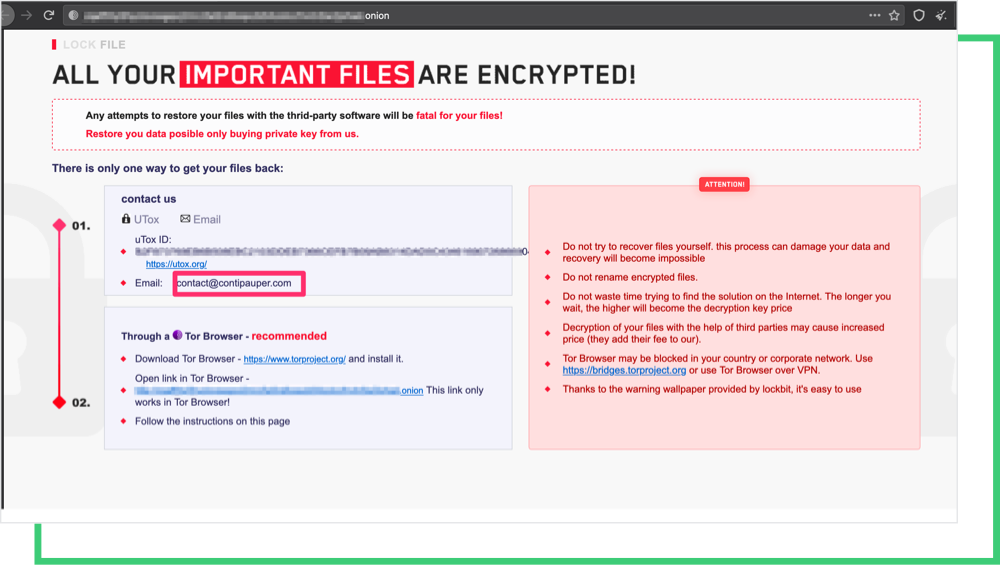
Microsoft published an advisory here to mitigate the effects of the attack, including making use of Extended Protection for Authentication (EPA) and features such as SMB signing. Black Kite researchers recommend disabling NTLM altogether.
How Can You Protect Your Organization?
Given the number of possible attack victims due to the wide deployment of Microsoft Exchange Server, it’s critical to take proactive and pre-emptive action now to prevent ransomware attacks including:
- Update Microsoft Exchange Server. Today.
- Understand your ransomware susceptibility and that of your third-party suppliers. Adapt a defense-in-depth strategy to stay safe from ransomware attacks. Black Kite’s new Ransomware Susceptibility Index® (RSI™) uses data and machine learning to discover the likelihood that an organization will experience a ransomware attack. Within minutes, RSI™ will provide an approximation for each company’s susceptibility to ransomware, and cross-correlate findings to their technical and financial ratings. The RSI™ follows a process of inspecting, transforming, and modeling data with the goal of discovering the likelihood of a ransomware incident.
- Implement third-party supply chain risk monitoring. With Black Kite, you can easily search third parties, or the organization itself, for exposure to freshly disclosed or existing vulnerabilities.
Understanding the vulnerability exposure of your organization and supply chain vendors will help you take proactive action for the most effective ransomware prevention.
Interested in the ransomware susceptibility of your company, or one of your third-party vendors?
Get a Free RSI™ RatingReferences
[1] ProxyShell vulnerabilities and your Exchange Server, https://techcommunity.microsoft.com/t5/exchange-team-blog/proxyshell-vulnerabilities-and-your-exchange-server/ba-p/2684705

