Third-Party Data Breaches in July 2021, Revealed: Ransomware Continues Its Reign
Written by: Black Kite
Last month was yet another reminder of how critical supply chain security is to business operations. While the repercussions of Kaseya— the most significant ransomware attack recorded to date—continue to unravel, it was not the only data breach caused by a third party that came to light. Let’s recap the top security incidents from July 2021:
1. “Ransomware Day” striked again as the REvil ransomware gang initially demanded $70 million from Kaseya.
Users of Kaseya’s VSA servers were feeling anything but celebratory after servers and workstations provided by the software company were infiltrated by a ransomware attack on America’s Independence Day. At the heart of the VSA software supply chain, the strike against Kaseya rippled down to an estimated 1,500 downstream businesses.
The Black Kite platform has been actively monitoring the Kaseya platform for the past 12 months. Prior to the incident, Kaseya’s Ransomware Susceptibility Index® (RSI™) was 0.651, indicating a high susceptibility to a ransomware attack. According to our analysis, any company over 0.50 RSI™ is highly likely to become a victim.

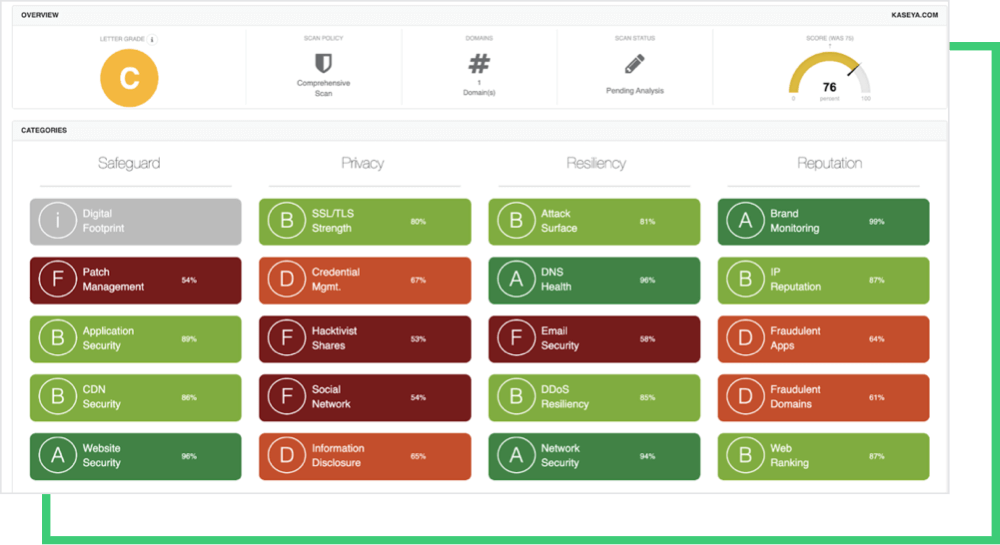
The Black Kite Research Team dug further into Kaseya’s posture for changes and emerging vulnerabilities, similar to those in the SolarWinds cyber attack that occurred late 2020, that may have also suggested it was vulnerable to an attack. In the investigation, the Black Kite Research Team found that Kaseya’s cyber rating fell from a ‘B’ to ‘C’ on our A-to-F rating scale.
Key factors behind the decline included rating decreases due to poor category grades for Patch Management, Credential Management, Application Security, and SSL/TLS Strength. These signals indicate the threat actors might have accessed some of Kaseya’s systems through unpatched systems, leaked credentials, phishing attacks, and/ or SQL injection attacks on web applications.
MSPs and MSSPs seem to be a prime target for the REvil ransomware gang because of the sensitivity of information shared by its high-value customers. In the near future, it’s likely that software ecosystems will experience more of these attacks, as this model is financially effective.
2. Millions of patients were impacted by one of the largest healthcare attacks of 2021.
Healthcare continues to dominate the majority of cyber attacks each month. This month, PracticeFirst reported a ransomware attack to HIPAA that took place at the tailend of 2020. Over 1.2 million patients were impacted after the New York-based medical management services provider was attacked.
The company claimed it shut down its systems, changed passwords, notified enforcement and hired a privacy consulting firm immediately after coming across the incident. PracticeFirst also had to pay a ransom in exchange for deletion of the files that included sensitive patient and payment information.
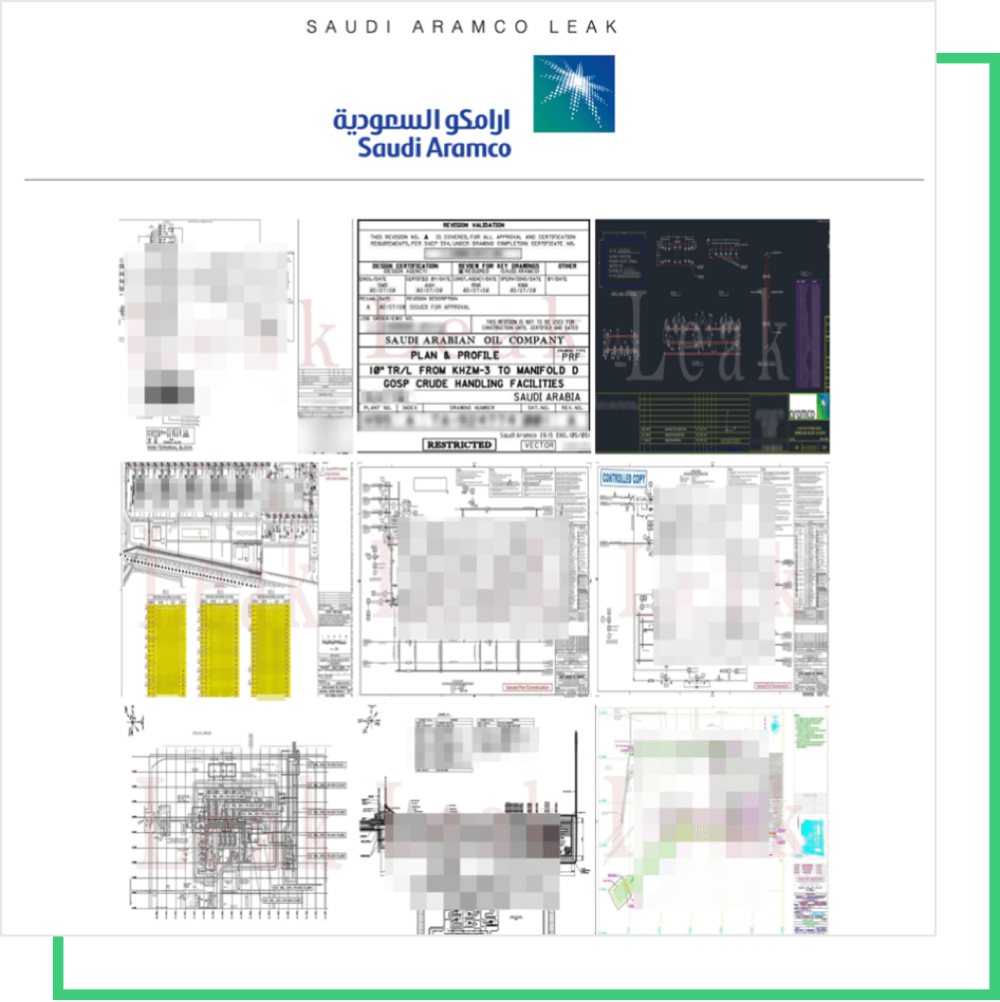
3. Cybercriminals sought after a substantial cryptocurrency payout from Saudi Aramco.
While there’s still much information to be disclosed, it’s confirmed that ZeroX has demanded $50 million in monero cryptocurrency from Saudi Aramco, the world’s largest oil and natural gas firm. It’s not yet clear which supplier that was breached nor the method of intrusion, but hackers allegedly stole one terabyte of sensitive information, including:
- Employee data: Names, photos, passport copies, emails, phone numbers, residence permit numbers, job titles, ID numbers, family information, etc.
- Project specification for systems related to electrical/power, architectural, engineering, civil, construction management, environmental, machinery, vessels, telecom, etc.
- Internal analysis reports, agreements, letters, pricing sheets, etc.
- Network layout mapping out the IP addresses
- Scada points, WiFi access points, IP cameras, and IoT devices, including location maps and precise coordinates
- A list of Aramco’s clients, along with invoices and contracts
Although the energy sector has been a prime target over the past few months, as witnessed in the recent Colonial Pipeline attack, it’s still wrong to assume that bad actors should have a long checklist of reasons when selecting their targets. What does sit on top of a bad actor’s checklist, however, the ability to access high-value accounts through weaker networks.
4. The ripple effect continues as the Accellion attack continues to claim its victims.
The year kicked off with the infamous Accellion supply chain attack that has affected 3,000 companies worldwide (and counting). Continuing to make the news headlines, Guidehouse stepped forward as another victim. The third-party billing vendor revealed it has also notified two of its beneficiaries, Morgan Stanley and Memorial Health System.
Providing investment banking, securities, wealth and investment management services in 41 countries worldwide, Morgan Stanley’s client files were leaked as a result of the third-party (Guidehouse) and fourth party vendor (Accellion). The data stolen included last known addresses, birth dates, social security numbers and corporate company names.
While preparing this blog, the world was shaken up once again with the Pegasus spyware news that allegedly infected 50,000 phones. The general rule of thumb is unique in cybersecurity nowadays. Regardless of the nature of attack, whether its against a supply chain, or targeting end users, organizations must adopt a “breach prevention” mindset.
According to MeriTalk, 89% of cybersecurity leaders agree prioritizing platform security is an integral part of protecting their organization against data breaches caused by third parties. The best offense is a strong line of defense, and it’s time companies get ahead of the game. Get started today with a free cyber risk rating.