Third-Party Cyber Risk: A Guide to Your First Steps in Managing It
Written by: Black Kite
Regardless of company size, working with third-party organizations can help streamline operations and reduce expenses. These organizations include vendors, suppliers, brokers, and contractors. Companies frequently use third parties to hire new employees, buy operational resources, and add facilities.
However, as a company’s network expands, so does its cyber risk. Each additional third-party vendor introduces new hidden security risks. It’s okay to rely on third parties, but maintaining a solid cyber security posture across your ecosystem is key to ensuring the sensitive data safety of your company. Third parties should be taken into consideration when assessing strategic risk.
What is Third-Party Risk?
Third-party risk is the possibility of a company encountering an unwanted event (e.g., data breach, ransomware attack, phishing) due to working with third-party organizations with access to privileged information. As a result, a company can be exposed to risks through weaknesses in the cybersecurity of its third-party vendors. This means that a company may have to share the full financial, legal, and reputational implications of that risk. The three categories of risk that a parent company may be exposed to include:
- Financial/Reputational Risk – the third party will have a damaging effect on the financial success or reputation of the parent company
- Operational Risk – the third party will disrupt the operations of the parent company
- Legal/Regulatory Risk – the third party will impact the parent company by failing to meet compliance legislation, regulation, or the agreements

Managing Third-Party Risk
To get a handle on your company’s third-party risk, you must assess the risk of each third party in your supply chain and develop a cybersecurity strategy around mitigating that risk. Whether you’re building your cybersecurity strategy for the first time or addressing a cyber breach, the process for vendor risk management remains relatively the same.
How to get started in assessing vendor risk
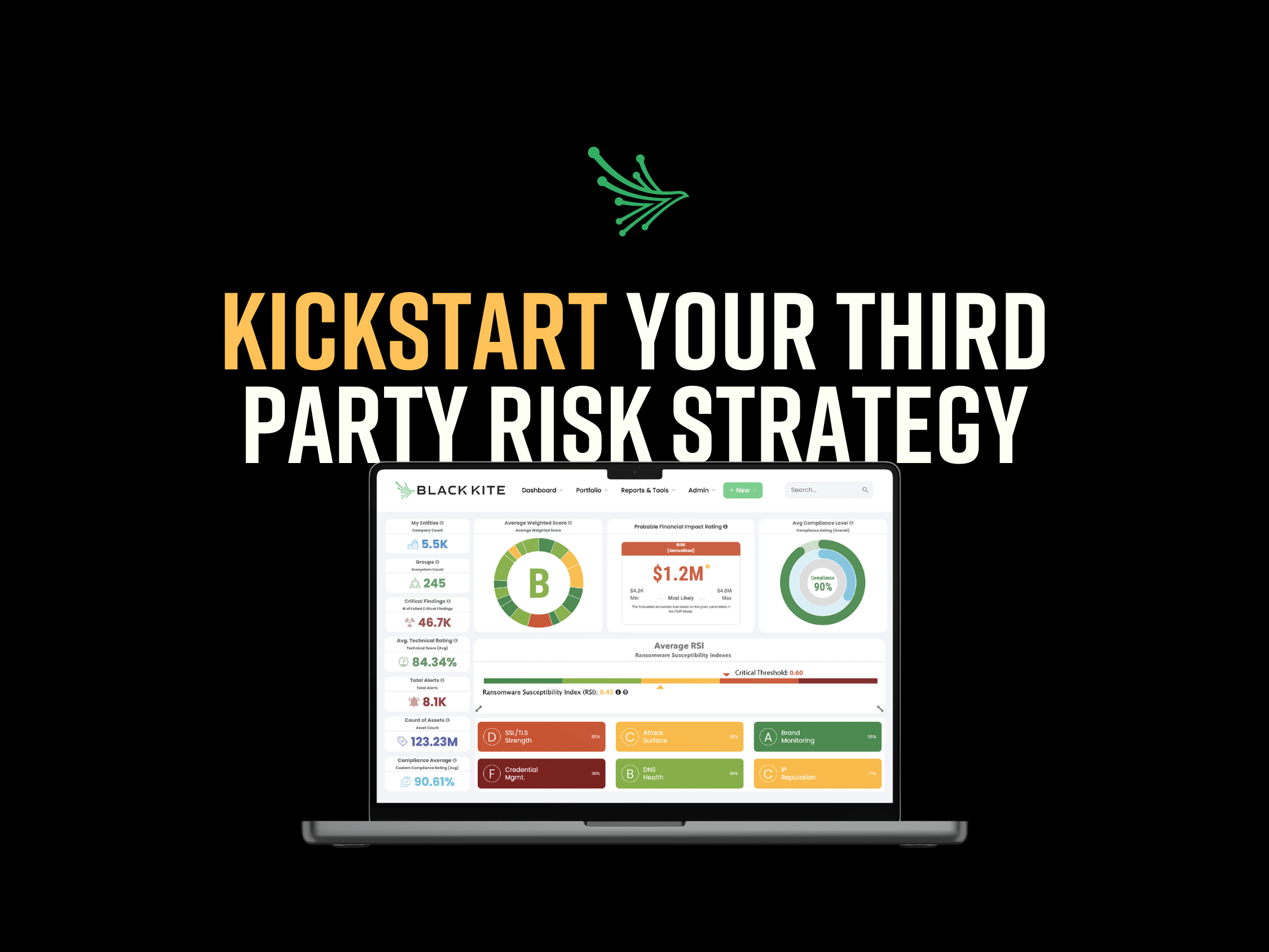
Step 1: Obtain a technical cyber rating of your company’s third parties. This rating provides a letter grade based on the current software weaknesses of a company. This will explain where a given third party stands regarding its cybersecurity.
Step 2: Put your cyber risk into financial terms. The Open FAIR™ model calculates the total financial impact (in dollars) if a third-party vendor, partner, or supplier experiences a breach. This step will help you prepare how much money it would cost your company in the event of a breach and shows you how to lower that dollar amount.
Step 3: Measure your company’s third-party compliance level. This measurement will reveal whether or not a third-party organization is following the standards and regulatory requirements set forth by corresponding agencies, laws, and authority groups. Organizations must achieve compliance by establishing risk-based controls that protect the confidentiality, integrity, and availability of sensitive information to maintain a legal operation level.
By regularly following a due diligence process, your company keeps its reputational risk in its control. A due diligence process should incorporate the steps above. The process should be a part of both your business’s development plan and business continuity plan. To save time and money, the best way to manage these steps is to have an automated process in place for your third-party ecosystem.
How can Black Kite be a partner for companies in this process?
Black Kite is the only company that can provide this automated process all on the same platform using the level of high-quality data needed for a comprehensive summary of risk. Black Kite engineers the largest data lake in the world – continuously updated and cross verified data – providing visibility into over 34 million companies and counting, with 20+ risk categories and 290 controls.
This intelligence fuels our other functions, including the world’s first and only Ransomware Susceptibility Index®. This index can measure the likelihood that an organization will experience a ransomware attack.
There is no one way to manage the cybersecurity of your third-party ecosystem, but some processes are more effective than others. Whether developing a process or renovating an existing one, understanding third-party cyber risk is a key piece of protecting your company’s critical infrastructure.
Request a demo