The Most Common Cybersecurity Threats Facing Supply Chains in 2021
Written by: Black Kite
As we enter the second half of 2021 and reflect back on the previous six months, it’s clear that all eyes are now on supply chain security. With hackers switching up their focus to go after weaker vendors and suppliers in business ecosystems, a spotlight has been placed on poor cybersecurity procedures caused by lower-tier suppliers.
In the past 12 months alone, more than half of organizations in North America have suffered a data breach as a result of a third party. Ranging in magnitude, these incidents can result in detrimental consequences for all involved. Along with the increase in frequency comes the ability to detect trends, or signals to prevent future disruption.
What causes supply chain attacks?
To better understand today’s cyber threat landscape, the Black Kite Research Team analyzed the root causes of the 64 unique supply chain attacks observed. Behind 23% of the attacks, ransomware is the most common threat to today’s business ecosystems. Malware and misconfigured/ unauthorized servers are also prominent threats, and human error remains a factor in cyber breaches.

I. Ransomware
By the time it takes you to read this sentence, another ransomware attack will have taken place. Multiplying in frequency over the past year, ransomware has also evolved to have its own business model, known as Ransomware as a Service (RaaS). During these attacks, cyber criminals leverage vulnerabilities to infiltrate systems and hold data hostage until ransom is paid.
Ransomware groups all tend to follow a common methodology for choosing its victims: They look for the weakest link that will turn around the highest return. The size of a company and its industry are all factors that can increase susceptibility to ransomware, as well as technical flaws such as leaked credentials and email security.
Using machine learning, the Ransomware Susceptibility Index™ combines these common factors with the data from a variety of OSINT sources to uncover the likelihood that a company will experience a ransomware attack within minutes.
Free RSITM Rating
“To pay, or not to pay?”— It’s a common question looming over security and risk management teams as the rate of ransomware continues to rise. While the FBI advises victims to not pay the demand, there are other key factors to consider before handing over the money:
- The data will not be necessarily destroyed. It is always best to assume it will be exchanged with other threat actors, or held for a second/future extortion attempt.
- Since most ransomware groups follow an affiliate model, it is likely that even if one affiliate deletes the data, other affiliates will keep it. Cybercriminals should not be trusted.
- The data may be published before a victim pays the demand.
- Complete records of what was taken may not be delivered by the threat actor, even if they explicitly promise to provide such artifacts after payment.
II. Malware
Despite falling back from its spot as the No. 1 threat among today’s supply chains in previous years, malware continues to claim its own set of victims. Defined as any file or harmful code that is designed to harm a user’s computer or network, the main difference from ransomware is the intent, whereas ransomware groups shut down systems until they’re paid.
The attack vectors are extremely similar to those prevalent in ransomware, as malware victims are usually targeted through phishing emails or vulnerabilities in out-of-date systems. Email credentials, traffic and espionage are leveraged most, making it even more so critical to educate employees and vendors about phishing attacks and credential management.
III. Misconfigured Servers
Rounding out the top 3, misconfigured servers are essentially an open invitation for hackers. Leveraged to access unprotected customer information that can be used again down the road in phishing campaigns. In some cases, these criminals use the stolen data to crack down even further into encrypted passwords.
Proactive monitoring for misconfiguration of cloud storage servers is the most effective way to close this gateway, as well as creating a system to regularly configure your systems. For more information on keeping your servers protected, check out our full list of common misconfigurations and steps to prevent them.
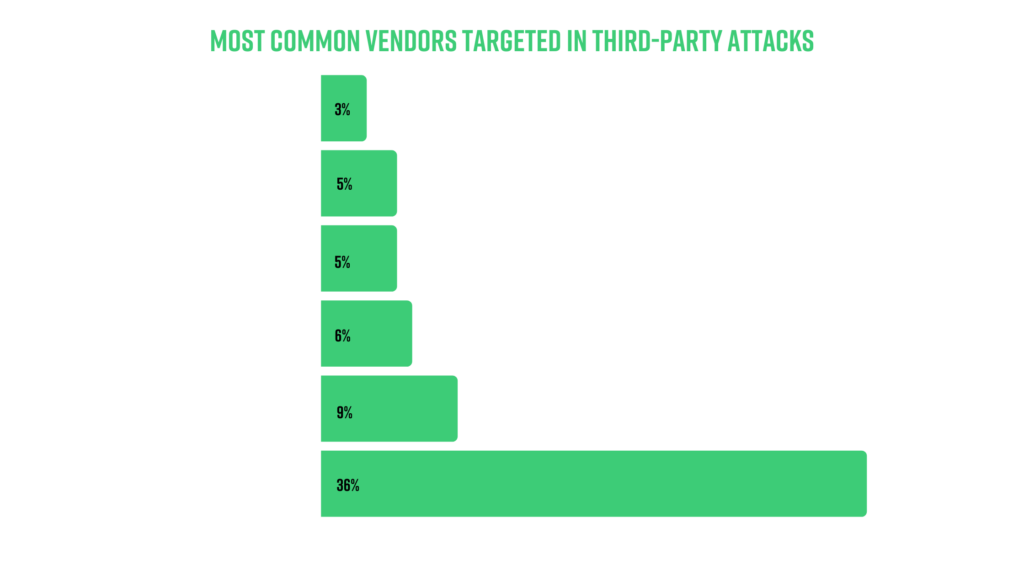
Which vendors are targeted most?
Cybercriminals determine the value of a company based on the amount of sensitive information that is stored across its network. Therefore, it comes as no surprise that software vendors are by far the most sought after by attackers, as one malicious update can impact hundreds, even thousands of companies.
As threats continue to evolve, it’s important for every organization within a supply chain to remain vigilant about their cyber security procedures. While a “good” cyber hygiene score does not promise immunity to an attack, going beneath the surface to understand the landscape and remain aware of which signals to look for makes all the difference.
For more information on handling today’s cyber threats, watch our webinar: “Reinventing the Ransomware Playbook”.
Watch On-Demand
