T-Mobile Hacked 6 Times in Last 4 Years
Written by: Black Kite
More than 40 million customers are now scrambling after the global communications giant T-Mobile disclosed that its servers were compromised by hackers, leaking 106 GBs of PII data. The news broke late last week through the twitter account @und0xxed, and was later confirmed by the telecom company on Monday afternoon – 48 hours after the attack.
Victim of history repeating itself
This attack is the sixth major data breach suffered by T-Mobile during the last four years, according to BleepingComputer, which indicates a high Data Breach Index on Black Kite platform. Cybercriminals target organizations that do not consistently deploy due diligence and make cybersecurity a priority within the business, as they anticipate vulnerabilities to remain present for exploitation if the cybersecurity investment is not adequate.
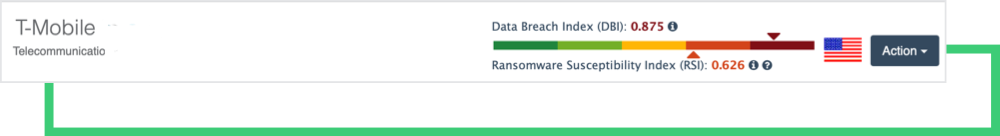
Although the T-Mobile breach is not a ransomware incident, the Black Kite RSI displays a .633 out of 1.0, indicating a high susceptibility to a ransomware attack.
Black Kite’s Ransomware Susceptibility IndexTM determines how susceptible a company and its third parties are to a ransomware attack. Data is collected from various open source intelligence (OSINT) sources including internet-wide scanners, hacker forums, the deep/dark web, and more. Black Kite correlates each finding with 26 control items using data and machine learning in order to provide approximations. Black Kite’s RSITM scores range on a scale from 0.0 (least susceptible) to 1.0 (most susceptible).
Although T-mobile continues to make headlines, none of the previous breaches surmount to the quantity of data leaked in the latest breach. Hackers infiltrated into the Oracle CRM, which stored a trove of customer data, potentially leaking PII for two weeks before the disclosure of the attack. The hackers also infiltrated the telecom provider’s production, staging, and development servers, which was immediately closed upon detection.
It’s unclear what caused the data breach, as the attack is still being investigated by the company’s cybersecurity team.
What PII data was accessed?
40 million of the records turned out to be PII data of former customers AND prospective customers who had applied for credit with the carrier. The remaining 7.8 million affected are current subscribers. As a result, the roughly 48 million users exposed their:
- full names
- dates of birth
- social security numbers
- driver’s license information
- IMEI
- PINS
- IMSI numbers
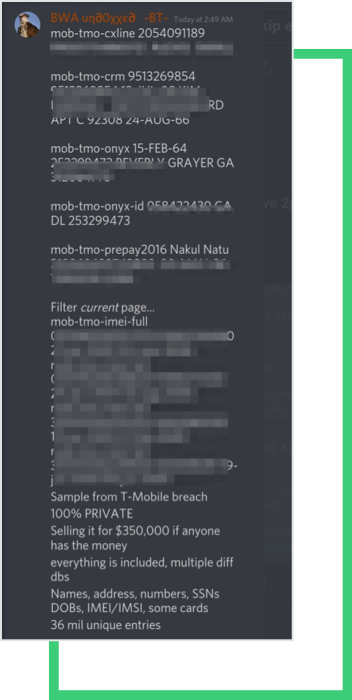
The names, phone numbers, and PINs exposed of an additional 850,000 prepaid customers were also leaked. According to the database, IMEI records (unique numbers used to identify devices globally) date back to 2004.
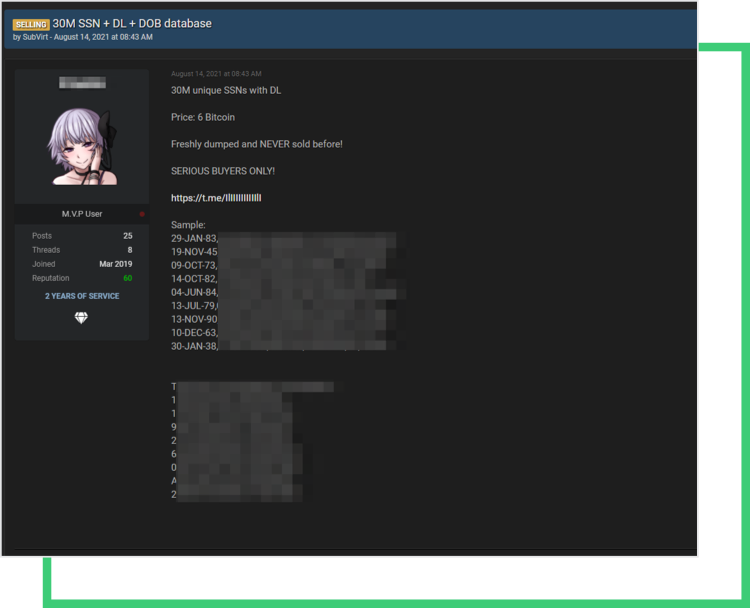
The seller is currently seeking 6 Bitcoin (about $270,000) on the underground site for a chunk of the data, which contains 30 million social security numbers and driver licenses. According to the forum, the rest of the data is currently being sold privately.
What’s at risk?
Unlike GDPR, there is no state-level privacy policy in the U.S that enforces data minimization. Incidents like these raise concerns over large database leaks and the ripple effect of those involved. It’s not uncommon for scammers to utilize some of this information to send phishing messages, take over accounts, and harass customers following an incident.
T-Mobile, like other mobile providers, already battles scammers who use SIM swapping attacks and other techniques to get control of staff accounts. SIM swapping techniques allow backdoor access to user data and are leveraged when hackers try to access the ”second-factor” in MFA enabled applications.
Action Items
On behalf of victims, T-Mobile has already started implementing safeguards. McAfee’s ID Theft Protection Service is providing two years of protection, and has already reset the PINs of the 850,000 prepaid clients whose PINs were disclosed. McAfee strongly recommends that all subscribed customers update their PINs as well, but is not requiring any action.
A T-Mobile customer can also change his/her PIN and password from their online account. Two-factor authentication is recommended to all customers wherever possible.
Moving forward, McAfee is offering a program called Account Takeover Protection to help thwart SIM-swap attempts. The program also aims to launch a “one-stop information” website on August 25th, however it hasn’t said whether it would include a discovery tool to see if you’ve been impacted by the incident.
In Other Recent News
While the impact of the T-Mobile breach is still evolving, another hacker now allegedly claims to have access to data of 40 million AT&T customers, a T-Mobile competitor.
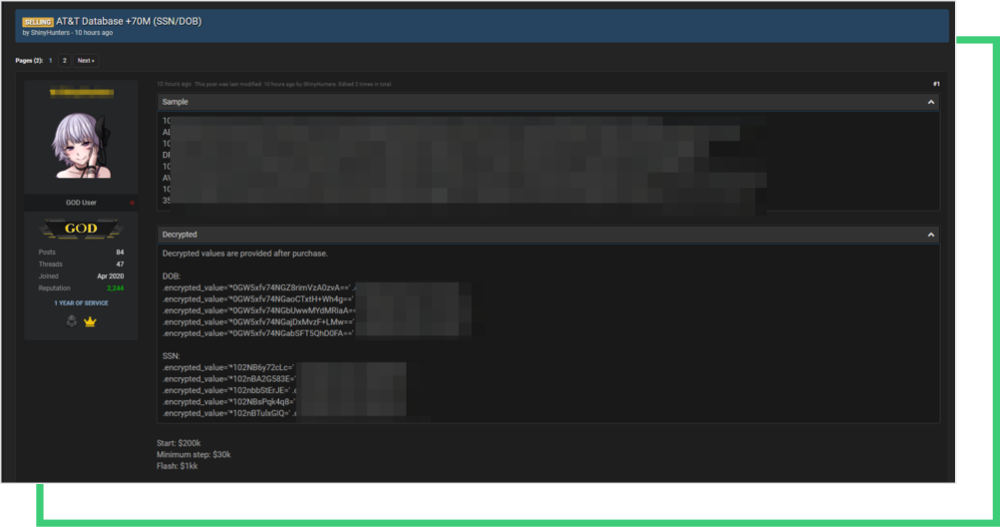
The data advertised on the forum includes SSN, e-mails, personal addresses and dates of birth as proof of the leak. The bid price starts at $200K, but can go up to $1M on demand. AT&T published a statement on the 19th of August stating that the data does not appear to have come from their systems.
The Black Kite research team will continue to issue updates as new information becomes available.

