Reduce Your Cyber Exposure to Mitigate Your Cyber Risk
Written by: Black Kite
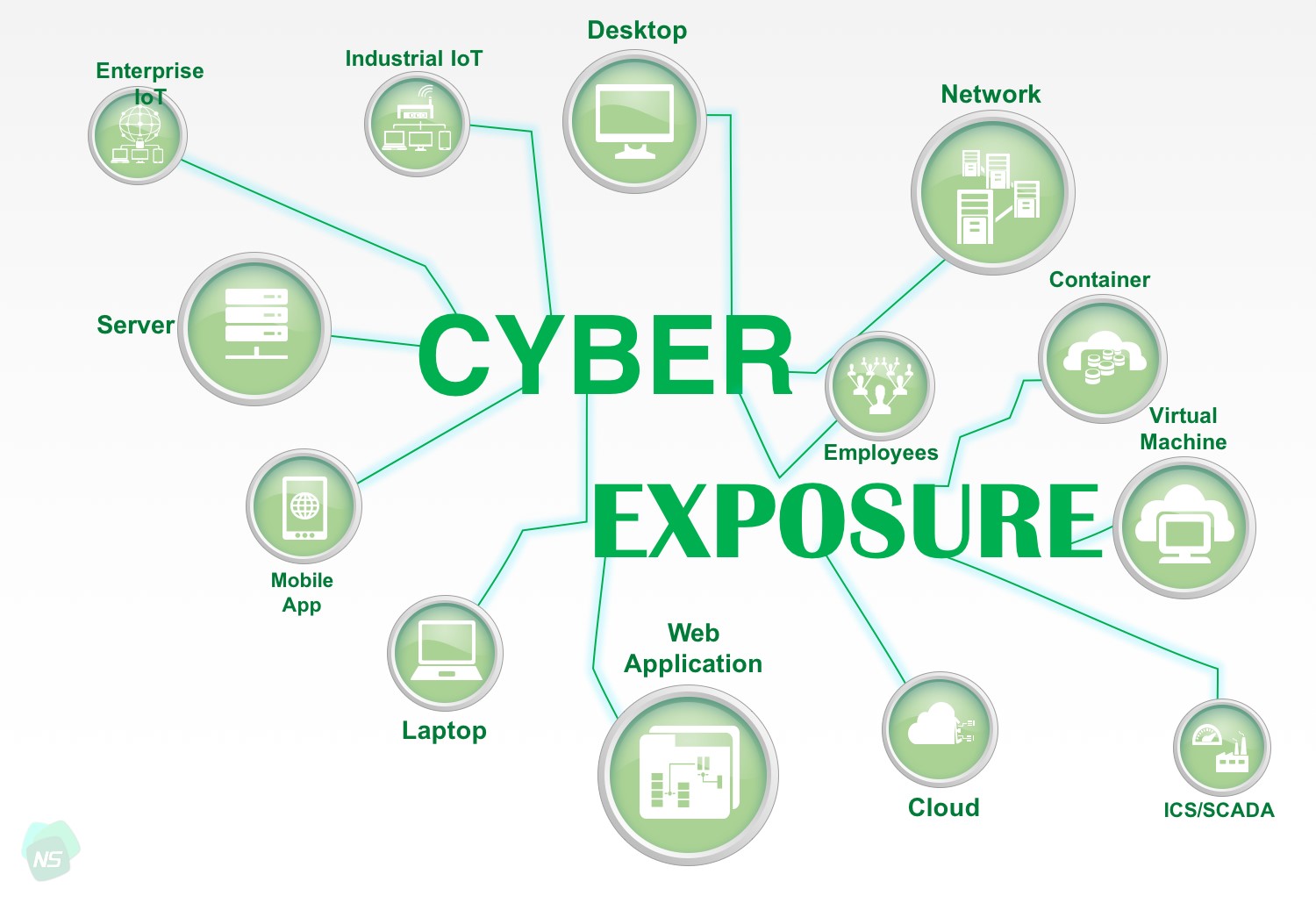
Today many companies invest in digital platforms, cloud services, Internet-of-Things (IoT) systems, Software-as-a-Service (Saas) systems, web-based applications, mobile applications, and advanced automation systems for digital transformation. With the increase in digital transformation, despite its great advantage to ease business and development processes, the cyber risk increases with the expanding cyber exposure.
The bring-your-own-device (BYOD) policies and remote-working solutions further expand the cyber exposure of a company. How much your company’s assets (including domains/subdomains, IP addresses, servers, e-mail addresses, endpoints, cloud data, and even employees themselves) are exposed to cyber world determines the attack surface, vulnerable points which hackers can exploit to infiltrate your systems. Thus, reducing your cyber exposure is vital to mitigate the cyber risk.
Simple steps to reduce cyber exposure
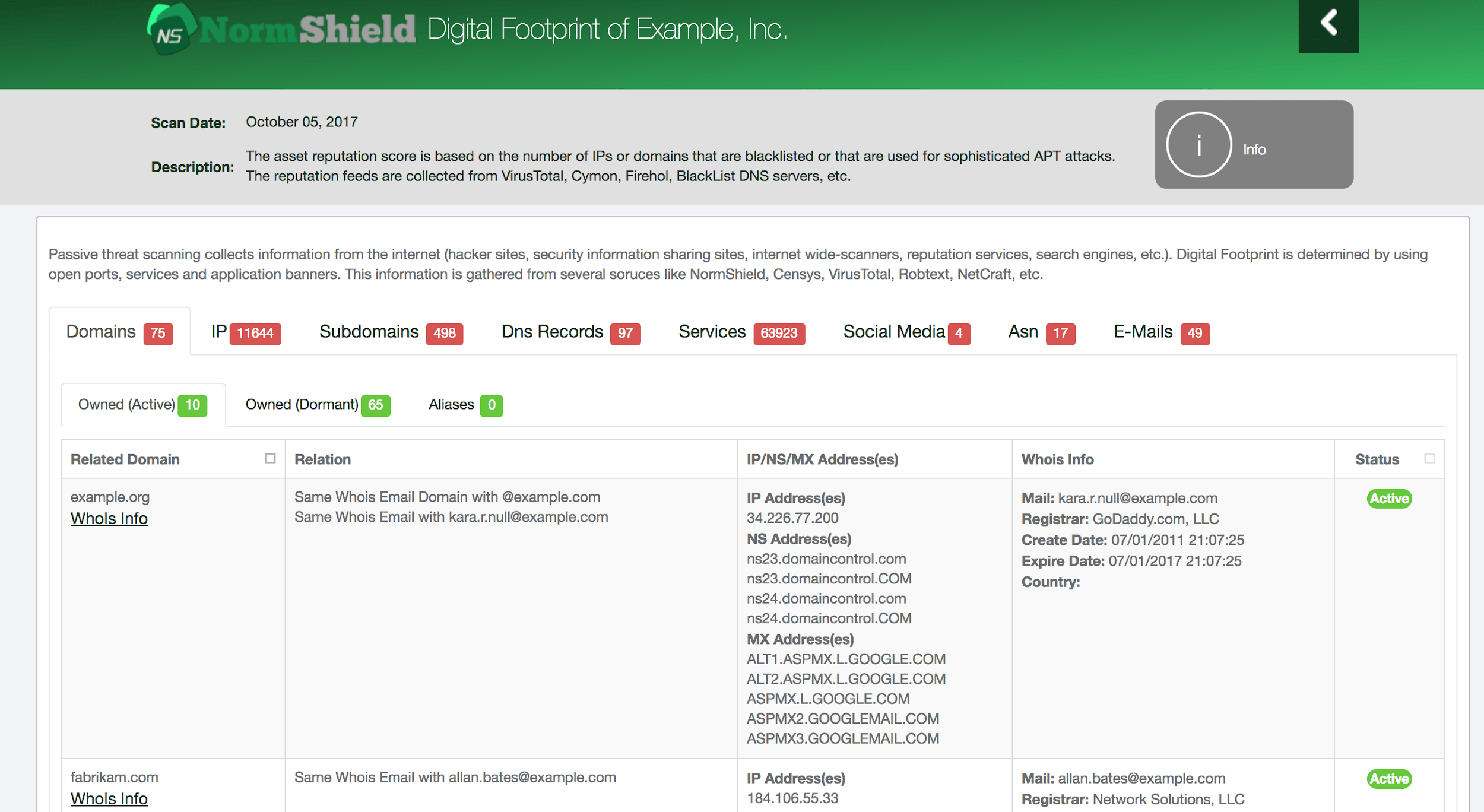
1. Determine and monitor your digital footprint. How many assets of your company are discoverable to digital world? Note that hackers first determine your digital footprint to map the attack surface.
2. Retire or disconnect any asset that is no longer needed.
3. Limit access to your systems for all parties who can access and ensure endpoint security. Even though the data are encrypted (and they should be encrypted), determine who needs to access what data.
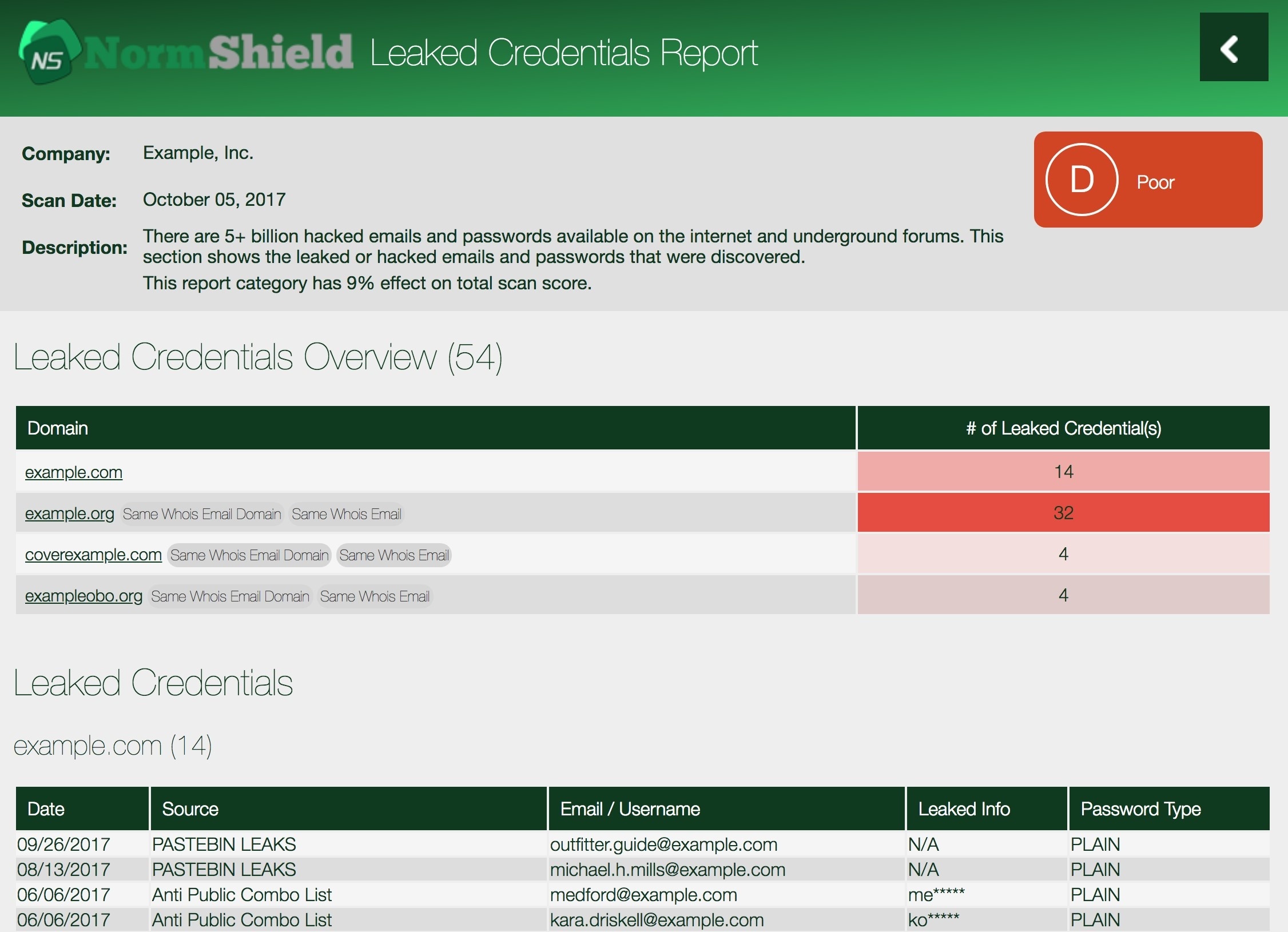
4. Make sure that you have a strong verification and authorization process (for example 2-factor authentication) to access data. Regularly monitor leaked credentials.
5. Prioritize your assets based on the their criticality and vulnerability. Monitor cyber risk of your assets. Black Kite Cyber Risk Scorecard is one of the tool to monitor your cyber risk.
6. Take third-party risk into consideration. Third-party vendors are like extensions to your digital footprint and expands your cyber exposure. So, monitor cyber risk of your third-party vendors. There are several tools for third-party cyber risk management. Check out our Guide to Select 3rd-Party Cyber-Risk Assessment Tool.
7. Use automatic vulnerability scanning tools to reduce your attack surface. One vulnerability scanner might not be sufficient, so use multiple scanners with an umbrella platform such as Black Kite’s UVM to manage them in one dashboard