Ransomware Day Strikes Again: What Kaseya Should Teach Us
Written by: Black Kite
By Bob Maley, CSO, Black Kite
Black Kite does not utilize Kaseya servers nor work with Kaseya in any way.
After compromising Kaseya VSA servers and distributing malicious software ahead of the holiday weekend, REvil’s recent ransomware attack is still encrypting thousands of servers and workstations worldwide. The exposition, rising action – the entirety of the plot – strikes too closely to the storyline of a different American holiday, Groundhog Day. For those of you not familiar with the iconic movie starring Bill Murray, the actor finds himself stuck in a cyclical time loop repeating the same day over again.
The difference between us and Bill Murray boils down to lessons learned. Desperate to escape the never-ending loop, Murrary is forced to face the consequences of his actions, whereas ransomware events keep repeating with new victims reported daily. However, it seems the ransomware gangs are the ones truly improving their strategy, with the Kaseya attack making this notion painfully obvious. Isn’t it time we take supply chain risk seriously?
First, let’s take a look at the actions we have taken to combat Ransomware thus far:
- President Biden has signed an executive order to promote combating cybercrime, by specifying a number of initiatives to be completed over the next 60 to 90 days.
- The FBI successfully recovered a significant amount of Bitcoin that was paid by Colonial Pipeline in its bid to recover from the attack earlier this year. While the news was good for Colonial, the bad actors simply pivoted tactics, moving to a cryptocurrency called Monero.
The Department of Homeland Security prepares for policy changes in September to make hiring cybersecurity talent easier and faster, yet according to CyberSeek, there are approximately 36,000 public sector cyber security jobs open now.
Uncover Your Ransomware Susceptibility
Many of the recent ransomware attacks were foreseeable. Black Kite developed the Ransomware Susceptibility Index® or RSI™ that discovers the likelihood an organization will experience a ransomware attack on a scale of 0 (less likely) to 1 (highly likely). Our research shows that any company over .50 RSI™ is highly likely to become a victim.
Before the incident, Kaseya’s RSI™ was 0.651, indicating a high susceptibility to a ransomware attack.

You might ask, How can the RSI™ predict with such a high level of confidence? In a nutshell, the factors that are embedded in the quantification for the RSI™ are the same factors that bad actors look for when they target companies.
- Health Service Executive, 0.855 RSI™
- FujiFilm Holdings, 0.561 RSI™
- Montana Technical University, 0.776 RSI™
- Undisclosed Healthcare Organization, 0.928 RSI™
Develop an Effective Course of Action
Companies cannot simply wait for the Federal Government or law enforcement to act. They must take responsibility and act themselves. In an effort to help understand next steps, Black Kite is offering free access to the RSI™report here.
Companies should also evaluate their supply chain strategy in order to know the amount of risk exposure a third party poses. Areas to improve internal cyber hygiene include:
- Secure email using DKIM, DMAC, SPF
- Require multi factor authentication on all systems, and audit and monitor privileged account access
- Secure any Internet facing services such as RDP or SMB
- Engage users in phishing campaigns as part of your security awareness training
- Be prepared in the event you do become a victim. Bad actors are constantly improving their strategy and there is no such thing as full-proof safety.
A company should also evaluate how they are looking for compromises internally and externally. Are indicators of compromise (IOC) the primary focus? If so, a chance to prevent the compromise is being missed. An effective vendor risk management program should focus on what a bad actor would do, and look for indicators of attack (IOA) which could mitigate or reduce the damage of an attack in progress. Assets exposed on the Internet should be observed from the same perspective of a bad actor, which starts with looking for the easiest targets.
Mutual Responsibility to Drive a Solution
In addition to companies taking responsibility for their own ecosystems (which includes supply chain), it will be extremely important for federal attempts to improve agility (like the DHS hiring initiative), and not get bogged down in bureaucratic red tape and political maneuverings. If the attacks are, in fact, being driven by nation states, the government must respond accordingly. The full weight of law enforcement must be brought to bear as well. After all, if the criminals have more incentive to commit the crime than deterrents from law enforcement, ransomware attacks will continue.
July 5th, 2021
What happened?
On July 2, 2021, researchers discovered that more than 1,500 Kaseya Virtual System/Server Administrator (VSA) servers were compromised by the REvil ransomware group by exploiting an authentication bypass, an arbitrary file upload, and code injection vulnerabilities. Kaseya provides remote management solutions with these on-premise VSA servers to Managed Service Providers (MSPs) all around the world. These MSPs support and supply IT services to many businesses including enterprise organizations, SMBs, local and state governments.
The REvil ransomware gang is infamous for targeting MSPs and MSSPs in the past to attack these companies’ customer organizations, therefore it’s no surprise they found a supply chain access point to multiple MSPs by leveraging the on-prem Kaseya VSA servers with admin privileges.
Who is at the risk of cascaded and correlated attacks?
This is a one-to-many type of supply chain attack where not only MSPs that use Kaseya on-prem VSA servers are at risk, but also the customers of those MSPs. Any MSP customer could experience a data breach caused by an Nth-party organization following this attack.
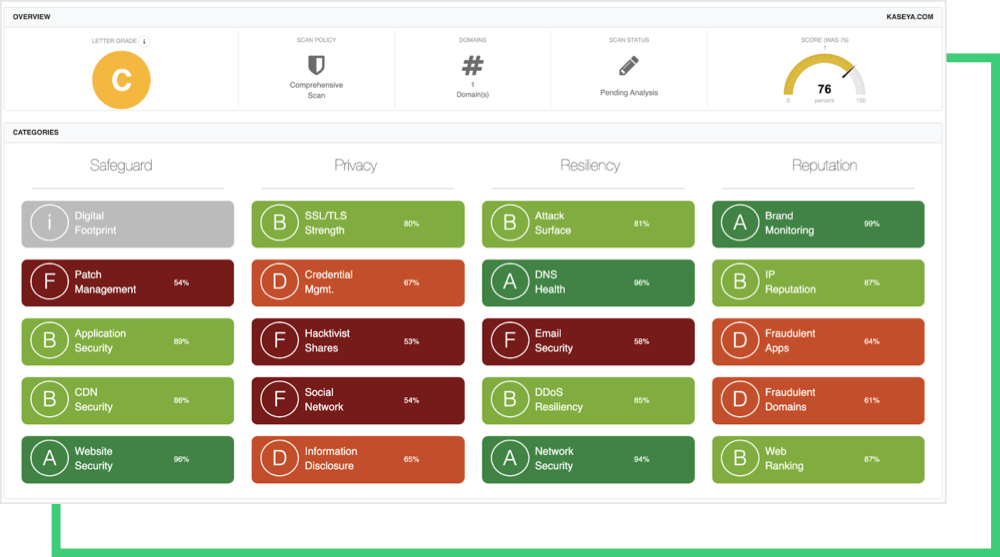
What are Black Kite’s cyber ratings for Kaseya?
Even though the exact initial access method used by threat actors to discover and exploit the vulnerability on Kaseya VSA servers is not known, Black Kite discovered that there are several indicators leading to known possibilities.
After examining Kaseya’s cyber posture over the last 12 months, the Black Kite team discovered Kaseya’s cyber rating dropped from a ‘B’ to ‘C’ on an A-to-F rating scale (84 to 76 on a 0-100 numerical scale). The rating decreases mostly due to poor grades for Patch Management, Credential Management, Application Security, and SSL/TLS Strength. These ratings indicate the threat actors might have accessed some of Kaseya’s systems through:
- Exploiting unpatched vulnerabilities on out-of-date systems
- Credential-stuffing attacks by using leaked credentials
- Phishing attacks by exploiting the poor email configuration
- SQL injection types of attacks on web applications
References
Cover photo by Chris Flook – Own work, CC BY-SA 4.0, https://commons.wikimedia.org/w/index.php?curid=80320762

