NEW-GENERATION RANSOMWARE GROUPS ARE A GROWING THREAT
New ransomware groups are often perceived as amateurish or unsophisticated in their early days.However, this perception is becoming increasingly outdated. At Black Kite, we continue to monitor how emerging threat actors quickly evolve, sharpen their tactics, and adopt tools previously unseen in the ransomware landscape. We expect this trend to accelerate in the coming months, as more actors experiment with unorthodox techniques to bypass defenses and maximize damage.
The Fog ransomware group is a prime example of this evolution. When it first appeared, it wasn’t even clear whether Fog was a fully-fledged ransomware operation or something else. Over time, the group refined its capabilities and became one of the most aggressive emerging ransomware actors.
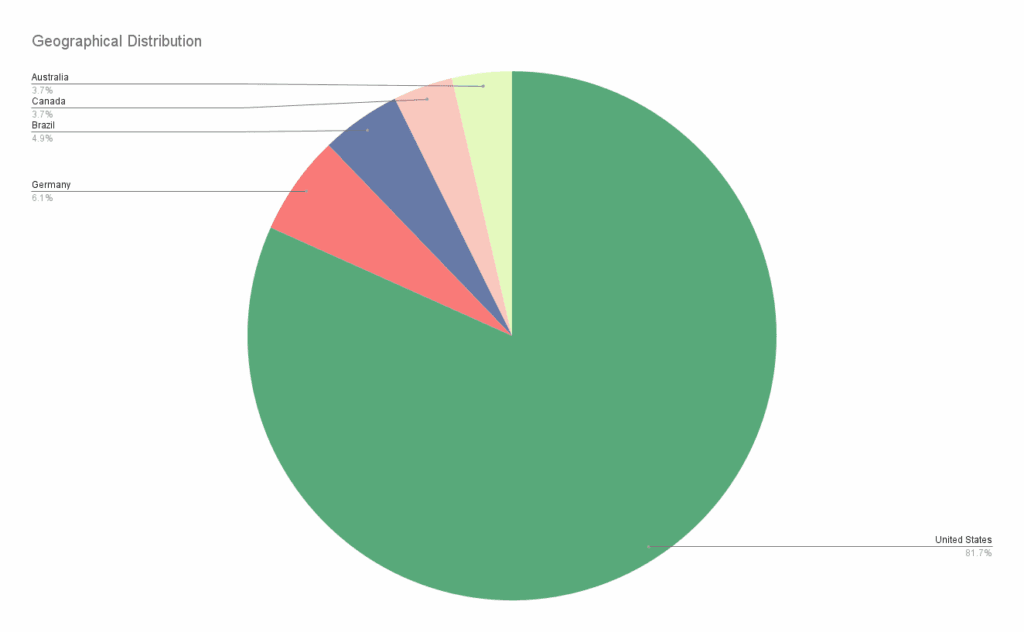
According to data tracked by the Black Kite Research & Intelligence Team (BRITE), we have identified 103 Fog-related ransomware victims to date. The geographical breakdown is telling:
United States: 67 victims
Germany: 5 victims
Brazil: 4 victims
Canada: 3 victims
Australia: 3 victims
Sector-wise, the pattern reveals a strong initial focus on education but a widening footprint into more complex and higher-value targets:

20 educational institutions (including 13 elementary schools and 7 universities)
20 manufacturing companies
16 professional and technical services organizations
8 wholesale trade companies
6 retail businesses
The impact of these attacks goes well beyond downtime or data encryption. Our analysis shows that:
- 45% of Fog victims were also affected by stealer malware, suggesting credential harvesting was a deliberate and coordinated part of the campaign.
- In 65 out of 103 cases, stolen user credentials were leaked or sold.
- Combined, the victim organizations represent $14 billion in total annual revenue, with an average company valuation of $80 million.
These findings reveal a highly opportunistic and dangerous actor that, despite its “newcomer” label, has already achieved significant financial and operational impact across multiple industries.
DEPARTURE FROM TYPICAL RANSOMWARE TTPS
Fog is not among the most advanced ransomware groups today, but it does show how even newer actors are beginning to rethink their methods. Rather than relying solely on standard RaaS (Ransomware-as-a-Service) kits and familiar tools, Fog has experimented with alternative approaches — including the integration of legitimate software like Syteca for surveillance purposes. This kind of deviation from typical ransomware tactics suggests a growing interest among emerging groups in exploring techniques that fall outside the conventional playbook.
USE OF LEGAL TOOLS LIKE SYTECA
Perhaps the most notable deviation from typical ransomware behavior was the use of Syteca, a legitimate employee monitoring software (formerly known as Ekran). Instead of deploying custom spyware or commodity malware, attackers silently installed Syteca to record keystrokes and capture screen activity — effectively turning a trusted enterprise tool into a surveillance weapon.
Because Syteca is a signed, commercially available product, its presence didn’t immediately trigger alarms in most environments. This tactic allowed Fog operators to collect internal credentials and map user behavior with minimal friction, giving them time to move laterally before deploying ransomware.
DEPLOYMENT OF OPEN-SOURCE TOOLS NOT COMMONLY SEEN IN RANSOMWARE
Fog also employed a mix of open-source tools that are more commonly associated with penetration testing or APT-style intrusions than with typical ransomware groups:
- GC2 (Google Command and Control): A post-exploitation backdoor that communicates via Google Sheets or SharePoint. Previously linked to APT41 activity.
- Stowaway: A proxy tool that allows attackers to build covert tunnels and transfer files across the network.
- Adaptix C2: An alternative to tools like Cobalt Strike, used to establish persistent C2 channels and run post-exploitation operations.
These tools aren’t particularly advanced by themselves, but their use in a ransomware context is relatively uncommon. Their inclusion in Fog’s arsenal reflects a growing trend: the lines between traditional cybercrime and targeted intrusion tactics are blurring, even among groups with limited resources or experience.
HOW LEGITIMATE SOFTWARE BECOMES A WEAPON
In a highly targeted cyberattack against a financial institution in Asia, the Fog ransomware group carried out a multi-stage, carefully planned operation. What made this attack unique was the use of Syteca, a legitimate employee monitoring software, for malicious purposes, and the combination of open-source tools and known security vulnerabilities in the attack.
More importantly, this situation highlights the danger that other legitimate software used for similar purposes could also be weaponized in future cyberattacks. This type of “legitimate software abuse” can bring with it not only technical but also ethical and legal debates.
Originally developed to monitor employee productivity, Syteca (formerly known as Ekran) was secretly installed on systems by attackers. It quietly performed the following actions in the background:
– Recorded keystrokes (keylogging)
– Captured screen shots
– Monitored user activity
Disguised under file names like `update.exe`, it was deployed via batch scripts and went unnoticed by both users and security software.
Attackers used various tools to silently spread Syteca across the network:
– Stowaway (an open-source proxy tool) for covert network redirection
– SMBExec (from the Impacket library) for remote command execution
– Obfuscation using legitimate process names and scheduled tasks
This high level of operational stealth made the attack nearly impossible to detect by traditional security solutions.
The collected data was exfiltrated not only through classical methods but also through highly creative and difficult-to-detect means:
– Encrypted archiving with 7-Zip
– Cloud synchronization with MegaSync / FreeFileSync
– GC2 (Google Command and Control): Receiving commands and exfiltrating data via Google Sheets or SharePoint APIs
– Adaptix C2: Alternative command and control infrastructure
Tools such as GC2, in particular, made it extremely difficult for traditional security solutions to detect because they allowed attackers to communicate through legitimate cloud services.
These methods allowed attackers to extract data without being detected by security systems within normal network traffic.
SECURITY VULNERABILITIES: WEAK POINTS EXPLOITED BY FOG
The Fog group did not need zero-day vulnerabilities for this attack. Instead, they used publicly known (n-day) security vulnerabilities that many organizations had neglected to patch.
Main Vulnerabilities Exploited
– Veeam Backup & Replication (VBR):
Through unpatched remote code execution (RCE) vulnerabilities, attackers gained authorized access to backup systems. This is a critical step for ransomware groups because they want to eliminate recovery options.
– SonicWall SSL VPN
Outdated SonicWall VPN devices allowed attackers to gain access from outside the network. It is believed that some previously identified buffer overflow and credential leakage vulnerabilities were exploited.
– Insufficient Network Segmentation & Misuse of Tools They moved around the network secretly using tools like Stowaway and SMBExec, making it easy to move between systems.
Why Did It Work?
These vulnerabilities were not zero-day, and some had been known for a long time. However, the attackers’ success stemmed from the fact that many organizations had not yet applied patches for such vulnerabilities and had not adequately monitored these risks, especially in third-party systems. The importance of patch management tracking and control for companies is even more evident here.
LESSONS LEARNED
The Fog ransomware incident shows that legitimate software can become cyber weapons when used carefully and that cybersecurity is not just about identifying “malicious software.” It is now necessary to approach every piece of software in the system as a potential threat, not just malicious software.
This incident highlights the following risks:
– Leaving legitimate tools outside of security controls can create serious vulnerabilities
– Antivirus and EDR solutions struggle to filter legitimate software without behavioral analytics
– Misuse of cloud services creates new channels for data leaks
This incident clearly shows that integrating third-party software into systems without security checks can pose serious risks. In particular, IT teams’ disregard for software labeled as “trusted” provides threat actors with opportunities to gain backdoor access. To prevent such incidents, it is critical for organizations to revisit their third-party software usage policies, enhance software supply chain security, and monitor all applications, including legitimate software, with behavioral analysis systems.
Solution Recommendations: Security Approach Must Be Redefined
The Fog attack is not just a ransomware incident, but also a lesson in where corporate security is vulnerable.
The following steps are vital for the future:
– Patch management is critical: Even publicly known vulnerabilities can be dangerous if they are not patched. Therefore, patch management must be strictly monitored across all systems.
– Behavior-based security is important: Traditional antivirus solutions cannot detect such attacks.
– Cloud-based data exits must be monitored: Attackers use popular cloud services to bypass security controls.- Supply chain software must be closely monitored with risk assessments.
HOW BLACK KITE HELPS
The emergence of groups like Fog highlights the need for continuous, high-resolution visibility into the global threat landscape. At Black Kite, we monitor both well-established actors and newer groups as they evolve, identifying changes in behavior, toolsets, and targeting patterns.
Our platform tracks early indicators of compromise, including unconventional tactics like the use of legitimate software or atypical cloud-based exfiltration channels. These insights help organizations stay informed—even when threat actors don’t follow traditional playbooks.
Just as importantly, Black Kite provides full visibility into your vendor ecosystem, highlighting which third-party organizations may be exposed to vulnerabilities or ransomware activity. This broader view allows companies to proactively assess risk—not only within their own networks, but across the partners and providers they depend on.
In a landscape where even small groups can create outsized disruption, visibility and context matter more than ever. Black Kite gives organizations the tools to stay ahead—not just reactively, but with foresight.
Sources:
- https://www.bleepingcomputer.com/news/security/fog-ransomware-attack-uses-unusual-mix-of-legitimate-and-open-source-tools/
- https://www.security.com/threat-intelligence/fog-ransomware-attack
- https://www.csoonline.com/article/4006743/fog-ransomware-gang-abuses-employee-monitoring-tool-in-unusual-multi-stage-attack.html
- https://therecord.media/fog-ransomware-incident-asia-financial-org-employee-monitoring