New Federal Cybersecurity Legislation Aimed at Protecting Critical Infrastructure
Written by: Black Kite
On Tuesday March 15th, 2022, President Biden signed a $1.5 trillion government funding package that includes the Cyber Incident Reporting for Critical Infrastructure Act. The Act requires critical infrastructure owners and civilian federal agencies to report to the U.S. Department of Homeland Security within 72 hours if they experience a substantial cyberattack.
It would also require any company considered critical infrastructure to report ransomware payments within 24 hours. A requirement such as this is a direct result of pressure upon the government to better protect critical infrastructure amid the recent debilitating attacks on various critical systems.
What sectors are included in ‘critical infrastructure’?
While the new legislation has not specifically laid out who is responsible for following this requirement, 16 sectors have been labeled by CISA as critical infrastructure. According to CISA, “the assets, systems, and networks, whether physical or virtual, are considered so vital to the United States that their incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof.”
- Chemical Sector
- Communications Sector
- Commercial Facilities Sector
- Dams Sector
- Critical Manufacturing Sector
- Defense Industrial Base Sector
- Emergency Services Sector
- Energy Sector
- Financial Services
- Food and Agriculture Sector
- Government Facilities
- Healthcare and Public Health Sector
- Information Technology Sector
- Nuclear Reactors, Materials, and Waste Sector
- Water and Wastewater Systems Sector
- Transportation Systems Sector
What is the Federal Government doing with the breach information shared?
While the CISA director claims that the data provided will give clearer visibility into protecting critical infrastructure, as of right now, CISA has not disclosed how it will use the provided data from breach reports. In fact, this remains one of the biggest concerns regarding a law such as this.
“When the first data breach notification laws came into effect in 2003, I was immediately a supporter. The breaches at the time involved the sensitive data of individuals and failing to notify said individuals about the breach put them at risk. The new legislation is much more nebulous. Often, laws such as this are something called security theater. They are created to establish the appearance of protection that in practice has a negligible effect on reducing risk,” said CSO Bob Maley.
Additionally, the new law does not require simultaneous reporting to the FBI, who investigates digital intrusions, bringing up concerns from the DOJ.
“This bill as drafted leaves one of our best tools, the FBI, on the sidelines and makes us less safe at a time when we face unprecedented threats,” said Deputy Attorney General Lisa Monaco.
Prior to this requirement, there was already a system in place for voluntarily sharing breach information with the DHS. However, there was no motivation for that offering. “If the government could craft legislation to be less of a requirement of businesses, and instead produce a situational awareness tool that is so incredibly valuable that they would be dying to submit information. That’s the tool that would allow them to succeed.”
So, does this legislation bring a true risk reduction to the table, or is it simply security theater? Sen. Gary Peters (D., Mich) said “You’re going to want to comply because CISA is there providing robust support for you, The only way the industry can protect itself is that people have to have situational awareness.” He is correct: situational awareness is paramount. But time will tell if new legislation will actually bring this about.
What exactly is situational awareness?
According to MITRE, the organization responsible for standards like CVE and CWE, used by the Black Kite platform, cyber situational awareness is “understanding your environment and accurately predicting and responding to potential problems that might occur. The systems and networks that operate in cyberspace have vulnerabilities that present significant risks to both individual organizations and national security. By anticipating what might happen to these systems, leaders can develop effective countermeasures to protect their critical missions.”
Cyber situational awareness is a combination of network awareness, threat information, and mission dependencies.
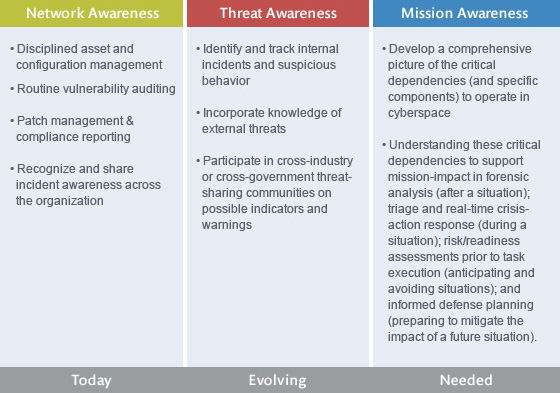
The issue within legislation such as the Cyber Incident Reporting for Critical Infrastructure Act is that active situational awareness needs to be immediate. In the hands of a government agency, which is historically slow and delayed due to national security, immediacy is difficult to achieve. Unfortunately in the case of this new act, rulemaking still has to be completed.
As of now, these reporting requirements for critical infrastructure will not be effective for at least two years given that final rules have to be proposed and published first. Two years, in a world where data breaches are occurring left and right against our most vulnerable or necessary sectors? Not going to cut it. Once again, we are left less agile than our adversaries.
In a Dark Reading article, Tom Kellerman takes a much more positive view. He believes the legislation will create positive change such as forcing companies to hire a CISO with budget and appropriate oversight. “It’s a game changer” he states. “I agree with his perspective,” says CSO Bob Maley, “but I still have reservations about how long it will take for any positive impact to manifest itself.”
Ready to start taking action before action is taken against your company? Build out your strategy with Black Kite.
Book A Free Demo
