Mitigating the Storm: Vendor Risk Management Amidst the Recent Cisco IOS XE Web UI Vulnerability (CVE-2023-20198)
Written by: Black Kite
Written by Ferhat Dikbiyik, Head of Research
Additional Contributors: Yavuz Han & Ferdi Gul
Updated on October 24: New identified implants, a new patch available.
The recent unveiling of a critical vulnerability in the Cisco IOS XE Web UI, designated as CVE-2023-20198, has drawn significant attention in the cybersecurity community. This vulnerability enables remote, unauthenticated attackers to create an account with privilege level 15 access on affected systems, thereby gaining full control over the compromised device. The affected systems include both physical and virtual devices running Cisco IOS XE software with the Web UI feature enabled, particularly those with the HTTP or HTTPS Server feature toggled on. The exposure of this vulnerability not only underscores the inherent risks within software interfaces but also amplifies the necessity of comprehensive Third Party Risk Management (TPRM) practices to mitigate cascading risks across the vendor ecosystem.
In this article, we will delve deeper into the Cisco IOS XE Web UI vulnerability, exploring the affected products, the extent of its impact on organizations, and the implications from a Third Party Risk Management perspective. Through a structured examination, we aim to provide insights on how businesses can better identify and mitigate risks associated with third-party vendors, ensuring a fortified defense against such cybersecurity threats.
What is the Recent Cisco IOS XE Web UI Vulnerability (CVE-2023-20198)?
The recently discovered vulnerability, dubbed CVE-2023-20198, is a severe flaw in the Cisco IOS XE Web UI that poses a grave threat to organizations utilizing affected Cisco devices. This vulnerability has been rated with the maximum CVSS (Common Vulnerability Scoring System) score of 10.0 by Cisco, indicating its critical nature. Successful exploitation enables unauthenticated remote attackers to establish privileged accounts with high-level access on the affected devices, essentially granting them full administrative privileges.
The exploitation process involves the attackers deploying an implant through specially crafted HTTP requests. This implant, based on the Lua programming language, facilitates arbitrary command execution, allowing the attackers to gain full control over the compromised device. The technical exploration by Talos revealed that the implant gets delivered through an HTTP POST request to the device, carrying out three specific functions as dictated by certain parameters within the request. This meticulous exploitation mechanism highlights not only the sophistication of the attack but also the potential for widespread unauthorized access and subsequent malicious activity across the affected network infrastructure.
On October 23, Talos updated its analysis, identifying an updated version of the implant and providing a new curl command to check for infected devices. This update further underscores the evolving nature of this vulnerability and the importance of staying updated on the latest developments to ensure effective remediation and mitigation efforts.
What Products Are Impacted by the Recent Cisco IOS XE Web UI Vulnerability (CVE-2023-20198)?
The products impacted by this vulnerability include a range of Cisco devices running the IOS XE Software with the Web UI feature enabled. Specifically, these products encompass:
- Enterprise switches
- Aggregation and industrial routers
- Access points
- Wireless controllers.
How Many Companies Were Affected?
A recent Shodan search conducted by the Black Kite Research Team revealed that over 144,000 Cisco devices with the Web UI feature enabled are active globally. Notably, almost 26,000 of these devices are situated in the US, indicating a substantial potential for risk exposure among numerous companies relying on Cisco’s networking solutions.
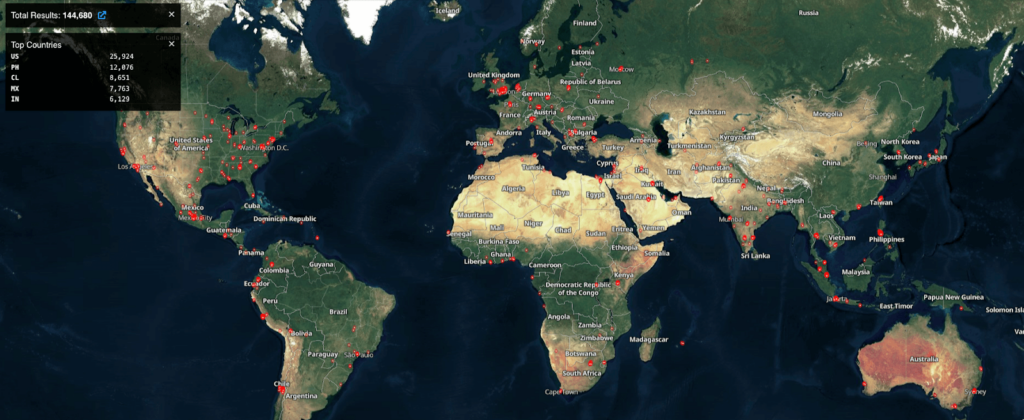
Furthermore, a report from CERT Orange Cyberdefense on October 18, 2023, highlighted that 34,500 Cisco devices were compromised in CVE-2023-20198 attacks. This additional information underscores the extent of the compromise and further amplifies the urgency for companies to evaluate and fortify their vendor risk management strategies.
What Are the Risks from a Third-Party Risk Management Perspective?
The revelation of the Cisco IOS XE Web UI vulnerability underscores the need for a vigilant Third Party Risk Management (TPRM) strategy. Identifying vendors at risk due to this vulnerability is paramount to prevent potential data breaches, operational disruptions, and financial repercussions. Here are some specific questions to pose to vendors:
- Have you identified any devices running Cisco IOS XE Software with the Web UI feature enabled within your infrastructure?
- If affected, have you taken steps to disable the HTTP/HTTPS server features as recommended by Cisco?
- What actions are being taken to monitor and remove unauthorized accounts created due to this vulnerability?
- Can you share the timeline for the patch application once Cisco releases a fix for this vulnerability?
- How are you enhancing the security around the Web UI and management interfaces to prevent such vulnerabilities in the future?
However, without knowing which vendors truly utilize the affected product or the asset hosting the product, sending a blanket questionnaire to all vendors can be a tiresome and challenging task. This scenario accentuates the importance of having precise intelligence on vendor product usage to ensure effective and efficient risk management.
How Can Companies Identify Vendors Affected by the Recent Cisco IOS XE Web UI Vulnerability (CVE-2023-20198)?
Leveraging the capabilities of Black Kite’s platform, companies can effortlessly identify vendors that may be exposed to the risks associated with the Cisco IOS XE Web UI vulnerability. By utilizing the FocusTags™ feature, users can filter vendors using the affected software, offering a streamlined approach to pinpoint potential risks within their vendor ecosystem. This targeted identification process allows for more effective communication with vendors, ensuring timely mitigation actions, and ultimately fostering a stronger cybersecurity posture across the supply chain.
Black Kite’s platform simplifies the process of identifying vendors impacted by the Cisco IOS XE Web UI vulnerability through a step-by-step approach:
- Navigate to the Company List page on the Black Kite platform.
- Click on the Filter button.
- Select the Tag option and type ‘Cisco IOS XE Web UI Vulnerability.’
- (Optional) Add any other filter options as needed to narrow down your search.
- Click on the Filter button to apply the filters.
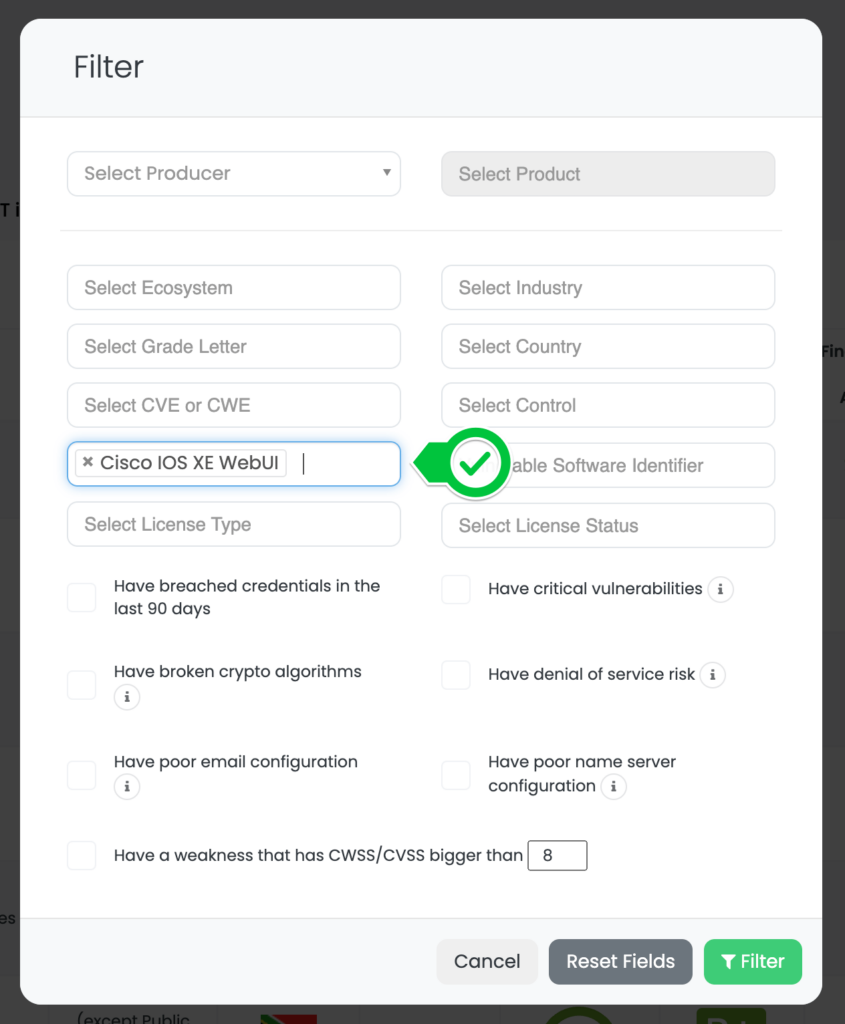
Upon executing these steps, the platform will display a list of companies using the vulnerable products, along with the IP addresses where the product is hosted. This feature facilitates efficient identification, allowing for better management and mitigation of risks associated with this vulnerability in your vendor ecosystem.
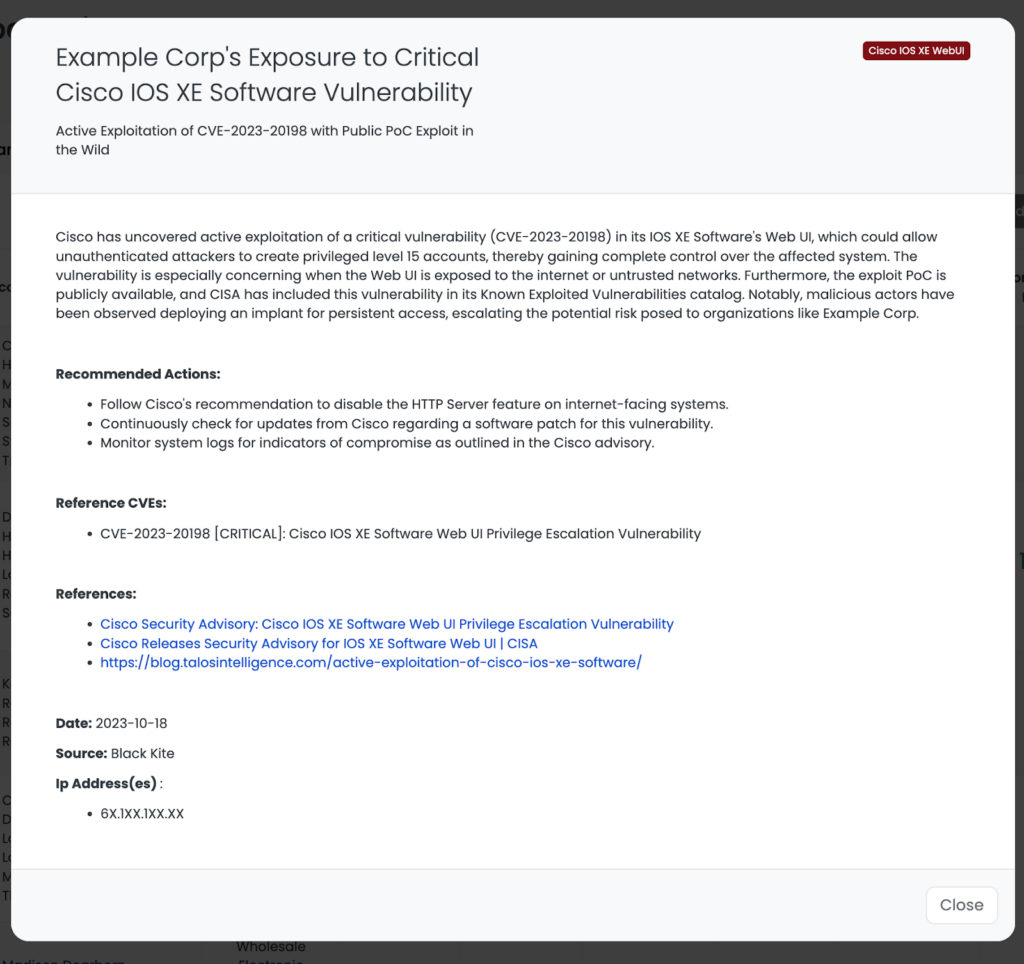
Latest Developments
Since the initial discovery of the Cisco IOS XE Web UI vulnerability, there have been significant updates to combat the risks associated with CVE-2023-20198. On October 23, Talos identified an updated version of the implant and provided a new curl command to check for infected devices. Moreover, Cisco has initiated the rollout of patches to address this vulnerability, with the first fixed software release being 17.9.4a.
Remediation Recommendations
Self-Risk Mitigation: What Steps Should Companies Take?
In the event that companies find themselves using vulnerable Cisco IOS XE software, immediate action is essential to prevent unauthorized access and potential data breaches. Here are the recommended steps:
- Apply the patches. Cisco has released a patch to address the vulnerabilities. The first fixed software release available is 17.9.4a, with updates for other software release trains to roll out at a yet undisclosed date.
- Disable the Web UI feature on all devices running Cisco IOS XE software to prevent unauthorized access until a patch is released.
- Monitor network traffic for any unusual activity and investigate any unauthorized account creation on the system.
- Stay updated on Cisco’s advisories for the release of a security patch and apply it promptly once available.
- Continually monitor for updates from Cisco beyond the initial patch to stay protected against any future related vulnerabilities.
Vendor Risk Management: How Should Companies Engage with Affected Vendors?
When a vendor within a company’s ecosystem is identified as using a vulnerable product, a structured approach is necessary to assess and mitigate the extended risks. The following steps are advised:
- Communicate with the vendor to understand the extent of the vulnerability within their systems and the steps they are taking for mitigation.
- Re-evaluate the risk assessment of the vendor in light of the vulnerability and adjust your company’s cybersecurity strategy accordingly.
- Consider leveraging Black Kite’s platform to continuously monitor the vendor’s cybersecurity posture and ensure they have taken necessary steps to mitigate the risks associated with this vulnerability.
Conclusion
The Cisco IOS XE Web UI vulnerability serves as a stark reminder of the complex cybersecurity challenges faced by organizations and the extended risk in vendor networks. Proactive measures, both in self-risk mitigation and vendor risk management, are crucial to navigating the maze of third-party risks. Leveraging advanced tools like Black Kite’s platform can significantly streamline the identification and mitigation process, fostering a resilient cybersecurity posture amidst a dynamically evolving threat landscape. Through informed actions and collaborative engagement with vendors, companies can significantly diminish the risk horizon and safeguard their operational integrity.
References
- Cisco. (2023). Cisco IOS XE Software Web UI Command Injection Vulnerability. Retrieved from Cisco Security Advisory
- Bleeping Computer. (2023). Over 10,000 Cisco Devices Hacked in IOS XE Zero-Day Attacks. Retrieved from Bleeping Computer Article
- Talos Intelligence. (2023). Active Exploitation of Cisco IOS XE Software. Retrieved from Talos Blog
- Black Kite. (2023). New Black Kite FocusTags Provide Instant Visibility of High-Profile Cyber Events at Scale. Retrieved from Black Kite Blog

