Is AlphV/BlackCat Staging its Own Death for a Rich Exit?
Written by: Kat Desy
Written by: Ferhat Dikbiyik
Additional Contributors: Yavuz Han and Ekrem Celik
I’ve likened major ransomware gangs like AlphV/BlackCat to the elusive unicorns of the cybercrime world. They’re mythical in their reach and impact, yet as these unicorns can’t gallop into the stock market sunset, their exit strategies often have a darker tint. Now, we’re seeing AlphV possibly taking their final bow, after a spree hitting critical healthcare targets.
They’ve pocketed ransoms in the millions and left their partners in the lurch, fueling rumors of a classic scam exit. Could this be the grand finale for AlphV/BlackCat? I’m keeping an eye on this unraveling story, connecting the dots as they aim for one last jackpot before their possible disappearance. Let’s break down what this means and what might lie ahead in this cat-and-mouse game of cyber trickery. As we dive deeper into AlphV/BlackCat’s saga, the complexities of their operations begin to unravel, revealing a tale of audacity and subterfuge.
The Plot Thickens: A Cyber Titan Falls?
The narrative of AlphV/BlackCat has been as unpredictable as it has been dramatic. Their recent assault on the healthcare sector culminated in a major breach at Change Healthcare, an event that sent ripples across the cyber community. The incident, detailed in our latest blog post, underscored the urgent need for robust third-party risk management strategies.
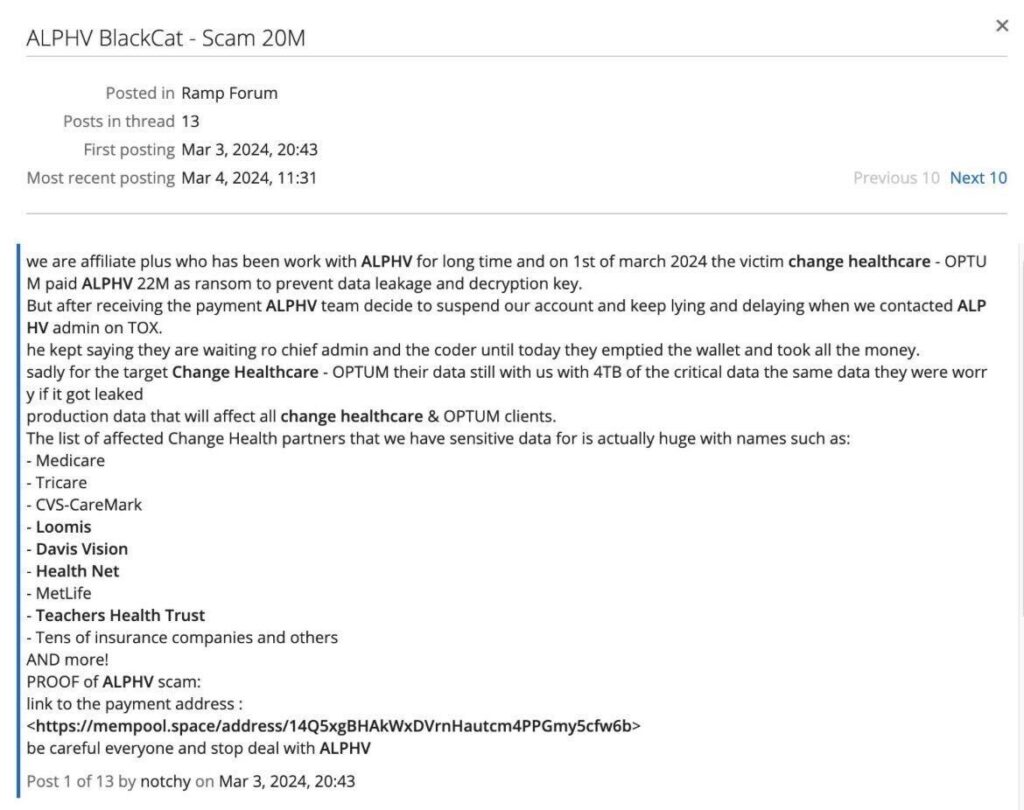
But in a twist fit for a cybercrime novel, an affiliate aired grievances about being duped by AlphV, even after a multimillion-dollar ransom was supposedly paid. The subsequent draining of AlphV’s crypto wallet hinted at a greater unraveling within the group. The recent FBI seizure of their site might signal a downfall, yet murmurs within the cyber underworld hint at a feigned demise, a strategic illusion crafted by a group known for their cunning and resilience.
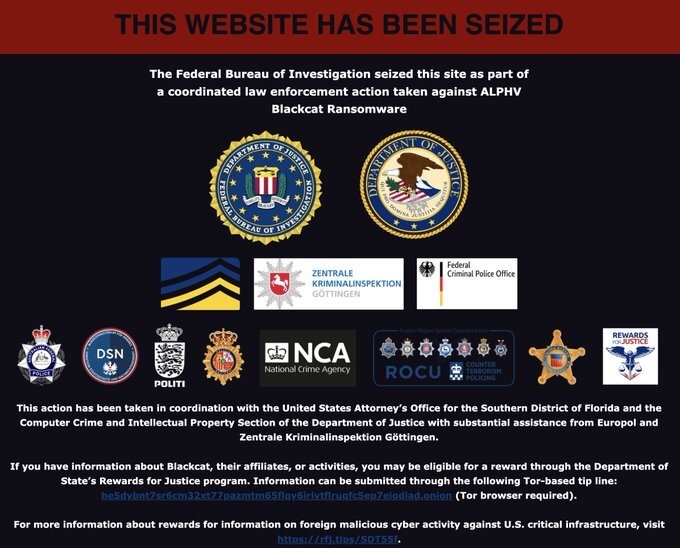
This intricate web of betrayal and subterfuge leaves us pondering AlphV/BlackCat’s next move. Is this the endgame they’ve designed, a clever ruse to bow out with their spoils? Or is the stage being set for a surprising encore? Our ongoing analysis and commentary seek to piece together these complex developments as they unfold.
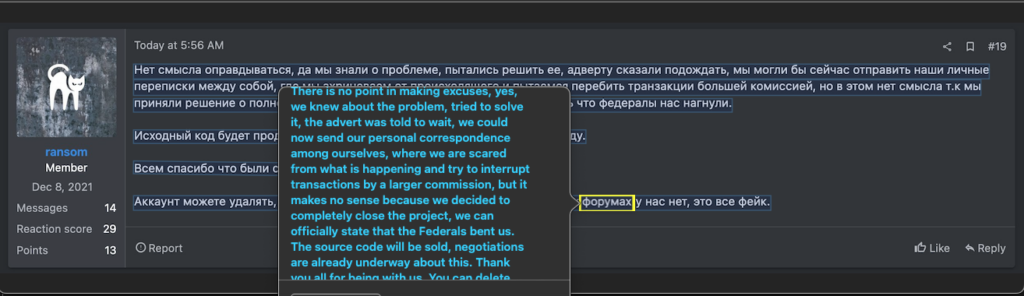
This audacious streak isn’t random but part of a calculated shift in strategy, pointing us towards their evolving choice of targets
AlphV/BlackCat: A Shift to Critical Targets
In the shadowy aftermath of the FBI’s intervention last December, the landscape of AlphV/BlackCat’s activities has shifted noticeably. Post-seizure, their dark web footprint shrunk, yet their attacks grew more daring, veering towards entities that form the backbone of society — critical infrastructures, energy corporations, and healthcare providers.

This wasn’t just a vendetta; it resembled a strategic strike for a massive payout. In 2023 alone, AlphV/BlackCat’s victim count soared over 400, a stark contrast to their more covert operations of the past. Despite high-profile hits like MGM Resorts capturing headlines, AlphV/BlackCat typically hunted smaller game. Half of their victims were small to mid-sized companies with annual revenues under $50M. Only about a quarter of their prey boasted revenues exceeding $500M.

Before the disruption, a mere 7.2% of their victims were in healthcare. That figure jumped to 12.7% afterward, signaling a disturbing pivot towards more critical sectors.
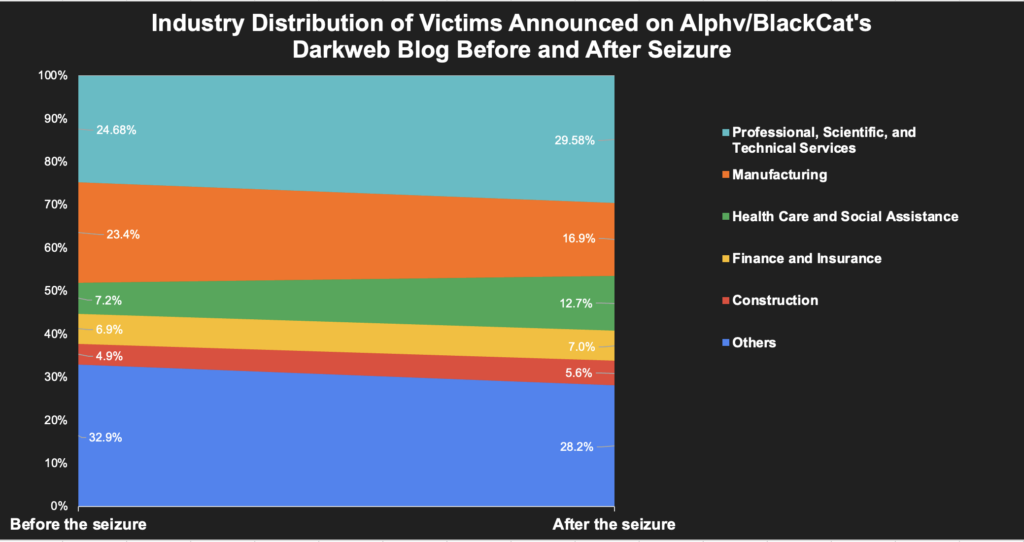
This pattern reveals a calculated approach: AlphV/BlackCat’s shift to targeting institutions integral to public welfare wasn’t random. It was a calculated risk, likely driven by the lure of a final, lucrative score before potentially disappearing into the digital ether. One significant target in their crosshairs, Change Healthcare, underscores the tangible impact of these cyber strategies on real-world entities.
Change Healthcare’s Cyber Ordeal: Challenges Amidst Transition
In the wake of AlphV/BlackCat’s targeted attacks, Change Healthcare became a prominent victim, its ordeal casting light on the complex cybersecurity challenges during corporate transitions. Recently acquired by UnitedHealth Group’s Optum, Change Healthcare faced the daunting task of securing its digital environment — a challenge magnified by the merger activities that often leave companies vulnerable to cyber threats.
The American Hospital Association (AHA) highlighted these concerns in a poignant letter, shedding light on the implications of such cyberattacks on the healthcare sector. Meanwhile, UnitedHealth Group’s response has been proactive, focusing on resilience and recovery in the face of adversity.
During mergers and acquisitions, patch management and tracking of vulnerabilities become herculean tasks. With hundreds of potential security gaps published regularly, it’s a monumental undertaking to maintain robust defenses. This period of transition for Change Healthcare was a window of opportunity that AlphV/BlackCat exploited, underscoring the persistent threat that ransomware groups pose to even the most vigilant of organizations.
The ordeal of Change Healthcare mirrors the broader narrative of AlphV/BlackCat’s operations, setting the stage for what appears to be their final act in the cyber arena.
The Final Gambit: AlphV/BlackCat’s Suspected Exit Strategy
In the shadowy realm of cybercrime, every move is calculated, but AlphV/BlackCat’s latest play feels like the final gambit. The streets of the dark web are buzzing with speculation: Is AlphV plotting their grand exit? It’s a narrative we’ve seen before – a flurry of bold strikes, a sudden crescendo of activity, then silence.
“Hit hard, hit fast, then vanish” seems to be the mantra. After their aggressive pivot to high-stakes targets, it appears AlphV may be orchestrating their swan song. The signs point to a classic setup: amassing a fortune and then cutting loose affiliates, leaving a trail of untraceable crypto and betrayed actors.
Could this be the endgame? It’s the move of a group not looking to overstay their welcome in the cybercrime spotlight. As the pieces fall into place, the picture emerges of a group ready to slip into the shadows, their pockets lined, leaving the cyber world grappling with the aftermath.
But let’s not be fooled – if AlphV is indeed bowing out, their legacy of disruption will linger. And as one titan exits the stage, the void will beckon new players. In the cybercrime theater, the show must go on.
As we ponder AlphV/BlackCat’s potential exit, we must also consider the aftermath for their network of affiliates and the cybercrime landscape at large.
Is BlackCat Simply Shedding its Western Tail?
As we delve deeper into the complex narrative of AlphV/BlackCat, insights from experts like Yelisey Bohuslavskiy of Redsense & Advintel offer alternative theories that challenge the prevailing exit scam scenario. He suggests that AlphV’s behavior might not signal a complete shutdown but a strategic reconfiguration, especially in dealing with their diverse affiliate makeup.
I share Bohuslavskiy’s perspective, recognizing that having Western affiliates, while advantageous in expanding a ransomware group’s reach, also brings inherent risks. Law enforcement in Western nations can often act more swiftly and efficiently, potentially compromising the entire network. The ideological and operational differences between Russian affiliates and their Western counterparts could be vast, with the latter possibly becoming a liability, even turning whistleblowers under pressure.
Moreover, Western affiliates may sometimes be driven by different motives, including greed, leading them to target organizations that draw undue attention and heat to the group. Such high-profile attacks can be a double-edged sword, bringing in large ransoms but also increasing the risk of law enforcement intervention.
Given these dynamics, AlphV might well consider its English-speaking affiliates within Scattered Spider as expendable, a segment that could be sacrificed to maintain the core group’s longevity and operational security. This shedding could allow AlphV to stay resilient in the face of adversity, potentially returning with a new encryption tool and a tighter, more ideologically aligned Russian-speaking core.
This viewpoint adds another layer to the discussion of what the future holds for AlphV/BlackCat. It suggests a level of strategic foresight, anticipating law enforcement patterns and preemptively adjusting to maintain their clandestine status. The group’s ability to adapt and evolve could set the stage for a reemergence, not as a swan song, but as a calculated transformation into a new era of cyber threats.
What’s Next: The Ripple Effects of AlphV/BlackCat’s Departure
As the curtain potentially falls on AlphV/BlackCat, the spotlight turns to the affiliates left in the cold, their anger simmering. This brewing storm of discontent could spell a seismic shift in the ransomware landscape. With AlphV possibly out of the picture, these affiliates stand at a crossroads, each path fraught with its own brand of chaos.
Lockbit, recently hit by law enforcement’s gaze, might find a lifeboat in these turbulent waters. The disbanding of AlphV could send a wave of seasoned affiliates toward Lockbit, breathing new life into its operations. It’s a twist of fate — one titan’s fall could be another’s resurgence.
Yet, not all affiliates are looking to jump ship to another gang. Some, armed with the know-how and a variant of BlackCat’s ransomware, might see this as their moment to rise from the ashes. We could witness the birth of new factions, each eager to carve out their piece of the cybercrime pie.
Then, there are those who might pivot toward redemption. In a world where loyalty is as thin as the next payout, the allure of turning whistleblower for law enforcement cannot be underestimated. These individuals, once shadow players in the cyber heist game, could become pivotal figures in dismantling the very networks they helped build. In the wake of giants, the ground is fertile for new seeds of cyber menace.
Each scenario opens up a Pandora’s box of possibilities. The end of AlphV/BlackCat isn’t just the closing of a chapter; it’s the beginning of an uncertain, tumultuous saga in the cybercrime chronicles.
Prevention is Key: Staying Off the Ransomware Radar with Black Kite
“If you hang around the barber shop long enough, sooner or later, you are going to get a haircut.”
In the world of cybersecurity, the old adage holds a new truth: “If you’re on the radar of ransomware groups for long enough, sooner or later, you’re going to experience a ransomware attack”. This isn’t just speculation, it’s backed by data. At Black Kite, we’ve taken a close look at the patterns leading up to ransomware incidents, and the findings are quite revealing.
Our analysis of last year’s ransomware victims shows a stark reality. Companies riddled with indicators of compromise — such as exploitable vulnerabilities, leaked credentials, or subpar email configurations — stand a nearly 50% chance of facing a ransomware attack. And if these companies are considered ‘juicy targets’, with significant country-, industry-, or revenue-based appeal, the odds are even less in their favor.
The graphical data we’ve compiled (as shown in the image) underscores the power of the Ransomware Susceptibility Index® (RSI™). Companies with a lower RSI™ value have a substantially higher likelihood of falling victim to such attacks. It’s a sobering reminder that in the digital age, your cybersecurity posture directly influences your risk of being targeted.
How do you steer clear of this unwanted attention? The key is to stay off the radar altogether. That’s where Black Kite comes in. We offer the foresight needed to avoid becoming a beacon for ransomware gangs. By identifying and mitigating the very indicators that put you or your vendors at risk, we help ensure your cyber ecosystem is not just waiting in the barber shop, so to speak.
In closing, as we continue to witness the fallout from ransomware groups like AlphV/BlackCat, let’s not lose sight of the proactive steps we can take. With Black Kite’s comprehensive risk assessment and monitoring solutions, your company or your vendors don’t have to be an inevitable statistic. Instead, you can maintain a posture that deters ransomware groups, keeping your organization’s ecosystem secure, resilient, and, most importantly, operational.

THE BLACK KITE CYBER VILLAINS & THREAT ACTORS DOSSIER
Learn about the threat actors that are still out there.

