GitHub Account of Canonical (Ubuntu Maker) Hacked; Cyber Risk & Third-Party Code-Sharing Sites
Written by: Black Kite
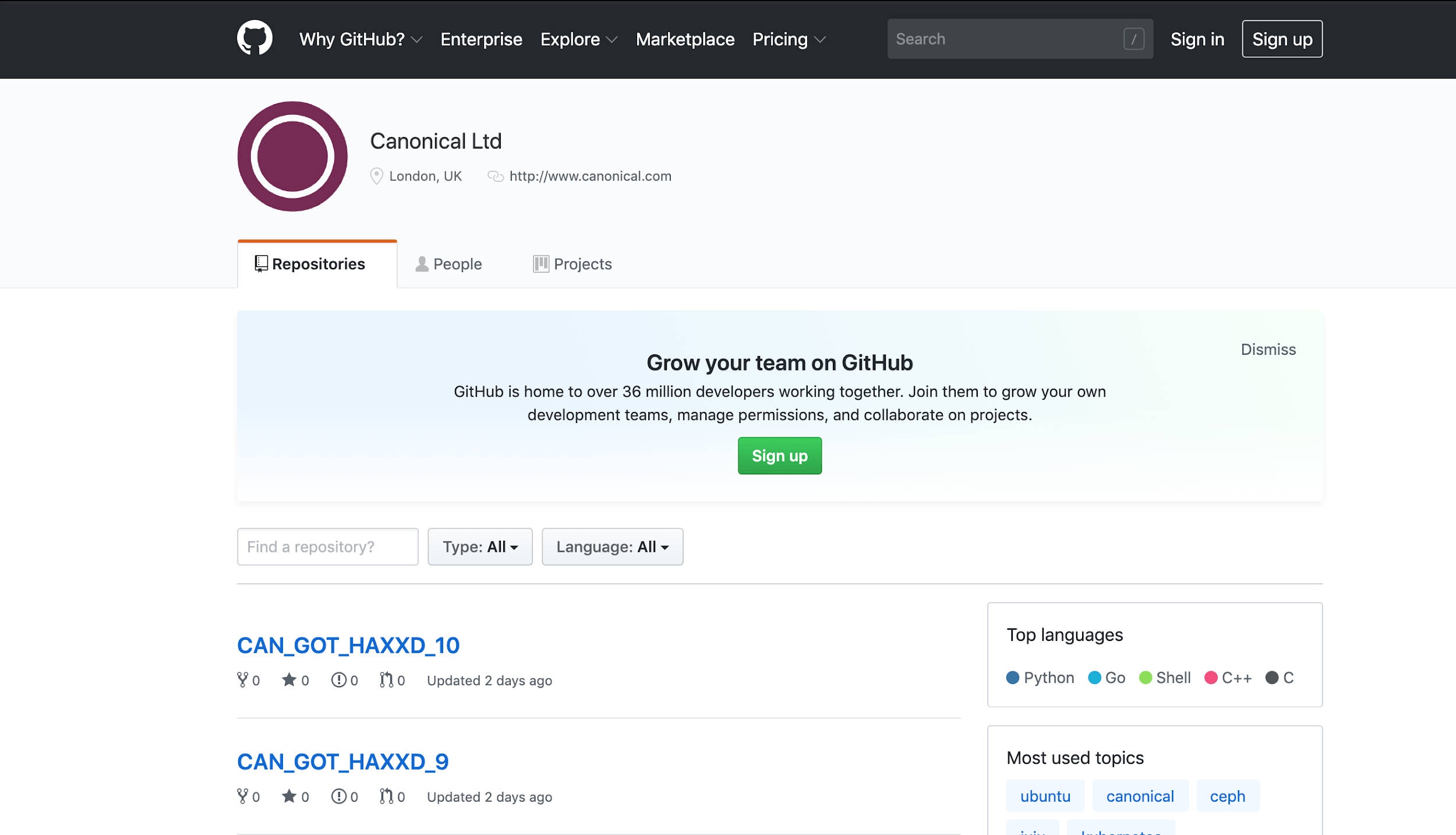
A third-party code sharing site was part of the latest breach. On July 6, the GitHub account of Canonical Ltd was hacked. Canonical is well-known for developing the famous Ubuntu Linux Distribution. The accounts on third-party code-sharing sites like GitHub may reveal critical information to adversaries when they are hacked.
In a public announcement, Ubuntu Security team stated that “Canonical has removed the compromised account from the Canonical organization in GitHub and is still investigating the extent of the breach, but there is no indication at this point that any source code or PII was affected.”
Statement also said: “Furthermore, the Launchpad infrastructure where the Ubuntu distribution is built and maintained is disconnected from GitHub and there is also no indication that it has been affected.”
GitHub Credentials Were Compromised
The Ubuntu Security team confirmed that the Canonical GitHub account’s credentials were compromised and “used to create repositories and issues among other activities.” A mirror of the account on web archives also shows ten repositories created by the attackers.

GitHub credentials may have been compromised by credential stuffing attacks, a method which hackers use to infiltrate a company’s system by automated injection of breached username/password pairs. Credential stuffing attacks have become more visible considering massive breached-credential collections are out there. DailyMotion, a video sharing platform, also suffered from credential stuffing attacks in January.

Hackers may have also searched for Git Configuration files that often include GitHub credentials. In fact, two days prior to the incident, cyber security firm Bad Packets detected scans for such files.

The Cyber Risk on Third-Party Code-Sharing Sites
Many companies and their developers use code-sharing sites like GitHub for code review, project management, and some other practical purposes. However, the accounts on these third-party platforms are also great treasures to hunt down by malicious actors. Repositories published on these platforms may expose vital information to hackers such as critical projects with their source code, important credentials, etc. Thus, companies should closely monitor their accounts on these code-sharing sites to avoid such incidents.
Even though code-sharing sites are not in the top 3 third parties that cause a data breach, it is important to check the cyber security posture of those platforms. Sites with a poor history of security will only place your company’s information at a greater risk.
Basic Steps to Mitigate Risk on Third-Party Code-Sharing Sites
Internal policies and strategies should be developed and enforced to identify and limit the various site which your organization might utilize for code sharing. While some code sharing sites have rules and behavior guidelines, maintain best practices in code development by running checks and scans on any code utilized from the sharing sites. Not everyone is posting or sharing code with good intentions. Malicious actors can post code which allows them to exploit it once embedded in your application. Other considerations for protecting your organization include the following best practices:
- Monitor activities on the accounts on third-party code-sharing sites,
- Monitor cyber security posture of those platforms,
- Review all the information shared on these sites and remove critical information if they are not supposed to be there,
- If possible, use multi-factor authentication to login to these accounts,
- Monitor breached credentials shared on hacker forums and deep web,
- If you discover your company’s information, take immediate steps to begin protecting existing accounts and data
- Change passwords at least quarterly,
- Train employees:
- Do not use company credentials for personal use -social media, online purchasing, etc. (Research shows that nearly 75% of people still use duplicate passwords across multiple systems)
- Use different password for business, personal and banking