Popular Video-Sharing Platform Hit by Credential-Stuffing Attack
Written by: Black Kite
The popular video-sharing platform, DailyMotion, released an announcement on January 25 about a persistent attack on their system. It is an ongoing attack where attackers use previously compromised username/password combinations.
The press release read: “The attack consists in “guessing” the passwords of some dailymotion accounts by automatically trying a large number of combinations, or by using passwords that have been previously stolen from web sites unrelated to DailyMotion.” which is the very definition of credential stuffing.
What is credential stuffing?
Credential stuffing is a method that hackers use to infiltrate a company’s system by automated injection of breached username/password pairs. We can see credential stuffing in the 2017 – OWASP Top 10 critical web application security risk report as the second most critical category: Broken Authentication.

Hackers use credentials to bypass anti-spam and firewall devices to access users’ accounts. Once inside the company network, they can send phishing emails or compromise company systems/data. Note that attackers just need to gain access to only a few accounts, or only one admin account to compromise a system. According to the OWASP report, hackers conduct money laundering, social security fraud, and identity theft, or disclose legally protected highly sensitive information.
There are numerous popular tools to simplify the process of credential stuffing. For instance, Sentry MBA can repeatedly try a username/password list for a targeted website. It uses an IP address list to route the traffic through so that the source of log-in attempts vary. It even features OCR capabilities for bypassing CAPTCHA-like counter-measures.
Most people use the same username/password combination on multiple login sites (cross credential use). If a breach list of a site is acquired, the attackers can use the same list for another site with credential stuffing tools such as Sentry MBA. The research shows a 1% to 2% success rate on cross credential use.
Billions of credentials are out there
According to the 4iQ Identity Breach Report, 8.7 billion (detected and verified) raw identity-record data were on the surface, deep, and dark web in 2017, which represents a 182% increase over the previous year. 44% of this data (approximately 3.8 billion) are usernames, passwords, and other credential information.
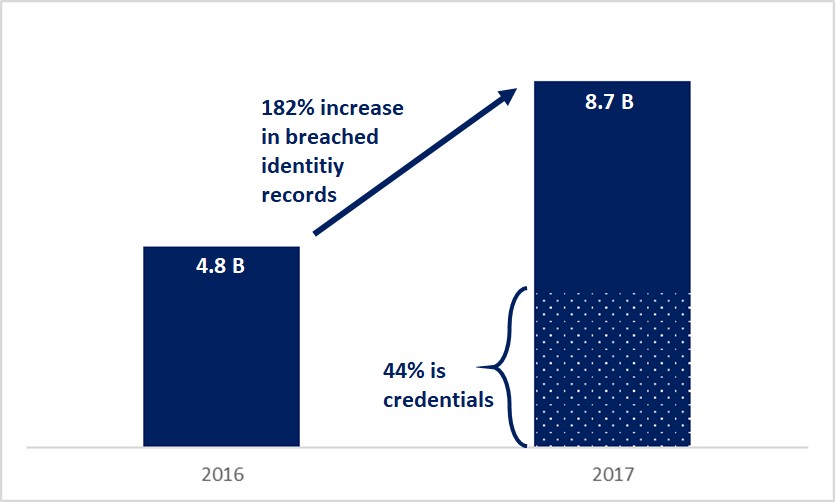
Recently, a large set of leaked credentials, likely one of the largest, was discovered by security researchers. This set called Collection #1, includes 773 million credentials. Collection #1 was only the start, because a new report states that Collection #2 to #6 are also available online. These collections include 2.2 billion unique usernames with associated passwords. They are shared and downloaded in hacker forums free of charge.
Expect to see more credential stuffing attacks
It is very possible that attackers used the Collection #1 set to attack DailyMotion and they are not the only likely target. Popular platforms may suffer this particular type of attack since this large set of credentials is now accessible by adversaries.
Hijacking accounts on different platforms can also cause third-party attacks. Employees of a third-party vendor (supplier, partner, etc.) may use their corporate e-mail addresses with the same passwords that they use to log-in to their corpariton’s system. If these credentials are included in the leaked credential data set, adversaries can access to third-party system and use the privileges of the employee to access to target company.

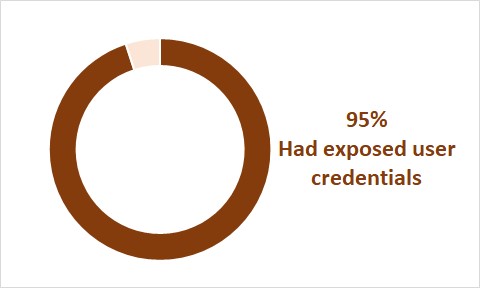
95% had exposed user credentials
Black Kite has one of the largest commercial databases of hacked credentials to help its customers to uncover exposure. Black Kite conducted research that reviewed trends and insights from its Cyber Risk Scorecard Service. The research included detailed external security risk data from 5,217 organizations across multiple industries and over one million active assets on the Internet, including web and network devices. Black Kite found a whopping 95% of respondents had exposed user credentials (for more information download Black Kite Cyber Security Risk Brief 2018).
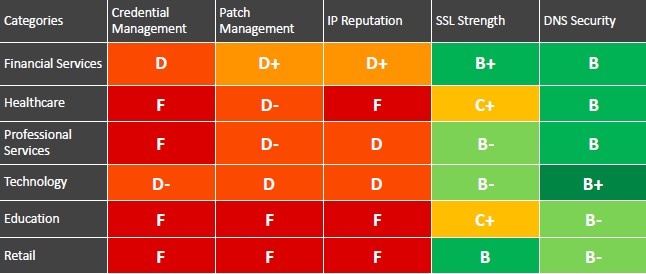
Industrial based comparison
The Black Kite 2018 Cyber Security Risk Brief also provides industry report cards (shown below) that give an industrial-based comparison for different risk categories based on easy-to-understand A-F letter grades. Companies in Financial Services and Technology scored slightly better in Credential Management than companies in Healthcare, Professional Services, Education, and Retail. Much work remains as the average grade was “C” or worse!
Simple Steps to Prevent
Black Kite recommends best practices that are well documented by compliance and security professionals:
- Use 2-factor authentication
- Change passwords at least quarterly
- Train employees:
- Do not use company credentials for personal use -social media, online purchasing, etc. (Research shows that nearly 75% of people still use duplicate passwords across multiple systems)
- Use different password for business, personal and banking
- Monitor cyber data leaks continuously
How to monitor data leaks and manage credentials
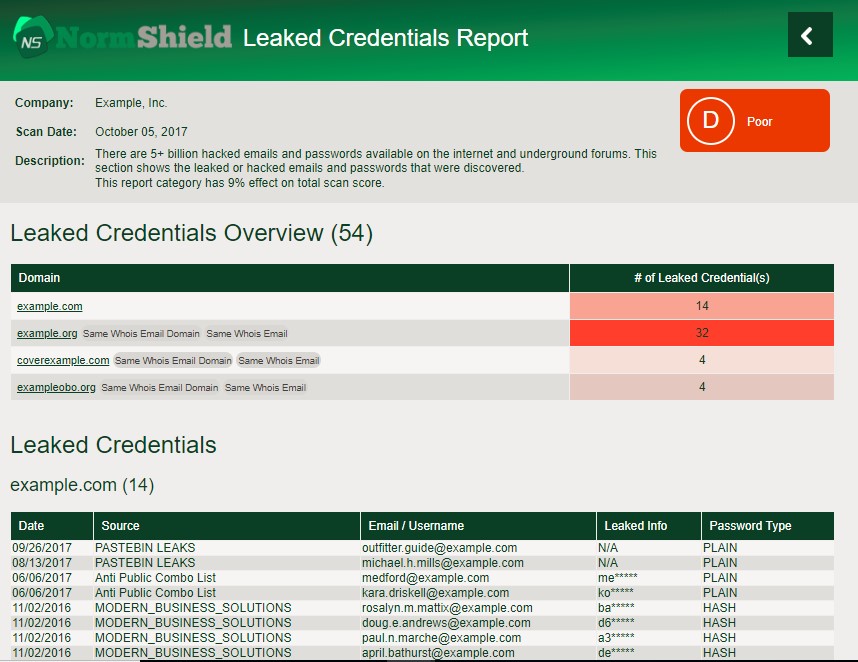
There are free tools for searching breached accounts. Black Kite provides a free service here. However, manual searches for large organizations are not efficient. The Black Kite Cyber Risk Scorecard Service monitors all levels of the Internet: the surface, deep, and dark web. It provides leaked credentials with details and an assessment of a company’s cyber risk (which can be used for benchmarking).
To act now and learn your cyber risk score on Credential Management among other categories, visit www.blackkite.com

