Focus Friday: TPRM Insights on Okta, OwnCloud, OpenVPN, and Citrix Incidents with Black Kite’s Focus Tags™
Written by: Kat Desy
Written by: Ferhat Dikbiyik
Additional Contributions: Ferdi Gül and Yavuz Han
Edited by: Katherine Desy
Welcome to this edition of Focus Friday, where Third-Party Risk Management (TPRM) meets real-time cyber intelligence. This week, we’re harnessing the power of Black Kite’s Focus Tags™ to dissect recent cybersecurity events. We will explore incidents, including the Okta data breach, vulnerabilities in OwnCloud and OpenVPN, the ongoing risks associated with a Citrix vulnerability, and the Boeing data breach. These Focus Tags™ not only identify affected vendors but also offer crucial insights for TPRM professionals looking to strengthen their cybersecurity posture. Dive into these critical events with us and discover how to enhance your TPRM strategies in the face of evolving cyber threats.
Okta Support System Breach: A TPRM Perspective
What is the Okta Data Breach?
In October 2023, the cybersecurity community was alerted to a significant breach in Okta’s support system. Initially downplayed, the breach’s severity became clear when Okta disclosed extensive unauthorized access to its support case management system using stolen credentials. This breach, first thought to impact only 1% of clients, was later revealed to have wider implications. Threat actors accessed HTTP Archive (HAR) files containing sensitive data like authentication cookies and session tokens. The extent of the breach became evident with companies like 1Password reporting related security incidents, indicating a broader impact on any organization using Okta’s services. This incident underscores the crucial need for robust TPRM strategies in identifying and mitigating cyber threats.
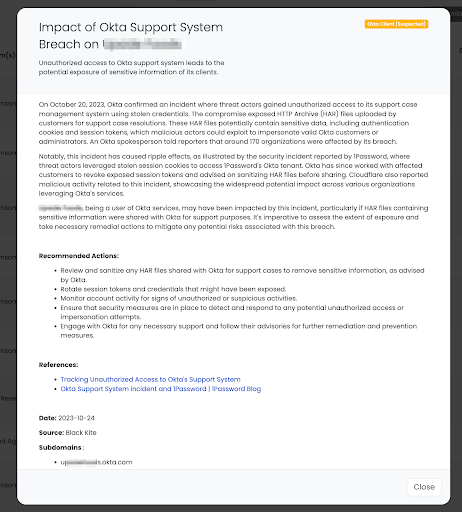
How Does the Okta Breach Impact TPRM Strategies?
In examining the Okta breach, let’s first explore its broader implications on Third-Party Risk Management strategies and the cascading effects on the vendor ecosystem. The Okta breach highlights a critical aspect of TPRM: the cascading risks of Nth-party impacts. This incident demonstrates how vulnerabilities in a primary vendor like Okta can ripple through the entire vendor ecosystem, affecting numerous organizations and their own networks. For TPRM professionals, it underscores the need for a comprehensive approach to risk management that extends beyond direct vendors to include their sub-vendors and partners. Effective TPRM must anticipate and mitigate these layered risks, ensuring robust protocols are in place to address potential breaches that can spiral through interconnected vendor networks.
What Questions Should TPRM Professionals Ask Vendors Using Okta?
Moving into a more tactical approach, let’s consider the essential inquiries TPRM professionals should make to vendors in light of the Okta incident. In response to the Okta breach, TPRM professionals should engage actively with their vendors utilizing Okta services. Key questions to ask include:
- “Did Okta directly notify you about the breach, and what specific details were provided?”
- “Have you conducted an in-depth analysis of potentially exposed HAR files, and what were the findings?”
- “Can you outline the technical steps taken to secure and monitor your systems post-breach?”
- “What changes or upgrades are you implementing to strengthen your defenses against similar vulnerabilities?”
These questions aim to assess the direct impact on the vendor and understand their mitigation and prevention strategies.
Remediation Steps for Vendors Affected by the Okta Breach
For vendors impacted by the Okta breach, immediate action is critical. Here are key remediation steps to secure systems and mitigate risks. Vendors using Okta should take immediate action to secure their systems and data:
- Review and sanitize any HAR files shared with Okta, removing sensitive information as per Okta’s guidance.
- Promptly rotate session tokens and credentials that might have been compromised.
- Vigilantly monitor account activities for any signs of unauthorized access.
- Implement robust security measures to detect and thwart any unauthorized access or impersonation attempts.
- Stay in close contact with Okta for ongoing support and adhere to their advisories for further remediation and preventive measures.
Leveraging Black Kite’s Okta Client Tags for TPRM Strategy
Black Kite promptly responded to the Okta breach by applying the ‘Okta Client’ tags. These tags were implemented on October 24, 2023, following a thorough analysis of thousands of active Okta subdomains. The tags encapsulate vital information, including client details, derived from digital signatures such as page titles, content, favicon images, and logos. This tagging system allows TPRM professionals to quickly identify and assess the risk posture of vendors using Okta services.
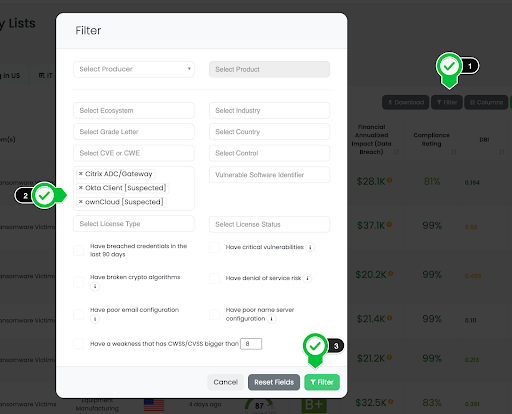
Steps for TPRM Professionals Using Black Kite to Identify Vendors:
- Navigate to the Company List page on the Black Kite platform.
- Click on the ‘Filter’ button.
- Select the ‘Tag’ option and type ‘Okta Client.’
- Optionally, add other filter criteria as needed for a more refined search.
- Click on the filter to apply and view the filtered list of vendors.
Black Kite’s ‘Okta Client’ tags bring immense value to TPRM professionals by precisely identifying which vendors are potentially impacted by the Okta breach. This targeted approach is crucial in efficient risk management, allowing professionals to focus their efforts on specific vendors rather than dispersing resources through blanket questionnaires to all vendors. By knowing exactly which vendors to reach out to, TPRM teams can conduct more focused and effective risk assessments, leading to quicker response times and more strategic security measures in the wake of such cyber incidents.
Critical Vulnerability in OwnCloud: CVE-2023-49103
What is OwnCloud Vulnerability?
In late November 2023, the cybersecurity world was alerted to a critical vulnerability in OwnCloud, a widely used open-source file synchronization and sharing platform. Tracked as CVE-2023-49103, this vulnerability received the maximum CVSS severity score of 10.0, due to its potential to expose sensitive information, including admin passwords, mail server credentials, and license keys in containerized deployments. The flaw allows remote threat actors to execute a command that reveals the server’s environment variables, containing these critical credentials. This vulnerability was quickly exploited in the wild, with threat-tracking firms observing mass exploitation starting from November 25, 2023. Over 11,000 instances were found exposed, predominantly in Germany, the U.S., France, and Russia.
The significance of this breach for TPRM lies in the widespread use of OwnCloud for data management and sharing, creating a vast network of potentially impacted vendors. This situation calls for an immediate and strategic response from TPRM professionals to identify and address the risks posed to their vendor networks.
What Are the TPRM Risks of the OwnCloud Vulnerability?
Exploiting vulnerabilities like CVE-2023-49103 in OwnCloud has become a prime attack vector for various threat actors, including ransomware gangs. For TPRM professionals, this raises significant concerns. The vulnerability’s ease of exploitation means that any vendor using OwnCloud is at a heightened risk of data theft and unauthorized access. The widespread use of OwnCloud amplifies this risk, potentially impacting a large segment of the vendor network. This situation necessitates a swift and comprehensive assessment of the vulnerability’s impact on vendors, prioritizing those most at risk due to their reliance on OwnCloud for critical data management and sharing.
What Questions Should TPRM Professionals Ask Vendors Potentially Exposed to OwnCloud’s CVE-2023-49103?
TPRM professionals should inquire about vendors’ exposure to and handling of the OwnCloud vulnerability:
- “Have you identified and assessed the impact of CVE-2023-49103 on your OwnCloud installations?”
- “What versions of OwnCloud are you currently using, and have they been updated to address this vulnerability?”
- “Can you detail the measures taken to secure the OwnCloud environment against this and similar vulnerabilities?”
What Are the Remediation Steps for Vendors Using OwnCloud?
For vendors using OwnCloud, immediate remediation is crucial:
- Download and install the latest version of ownCloud that addresses the vulnerability.
- Back up the existing ownCloud installation before making changes.
- Remove the current vulnerable installation and replace it with the updated version.
- Review and update security configurations to reduce exposure risks.
- Actively monitor network traffic, particularly for unusual requests to the “/GetPhpInfo.php” directory, to detect potential exploitation attempts.
How Can Black Kite Customers Utilize OwnCloud Tags for Enhanced TPRM?
Black Kite leverages internet-wide scanners for non-intrusive digital footprint discovery, allowing the identification of vendors using ownCloud. However, it’s important to note that while Black Kite can detect the use of ownCloud, it does not directly determine the versions in use. Here’s how Black Kite customers can effectively use ownCloud tags:
- Utilize Black Kite’s scanning capabilities to identify vendors in your network that use ownCloud.
- Once identified, engage with these vendors to understand if they have taken steps to address CVE-2023-49103.
- Encourage vendors to verify and update their ownCloud versions as necessary.
- Use this information to prioritize risk assessments and tailor your TPRM strategies, focusing on vendors with potential vulnerabilities.
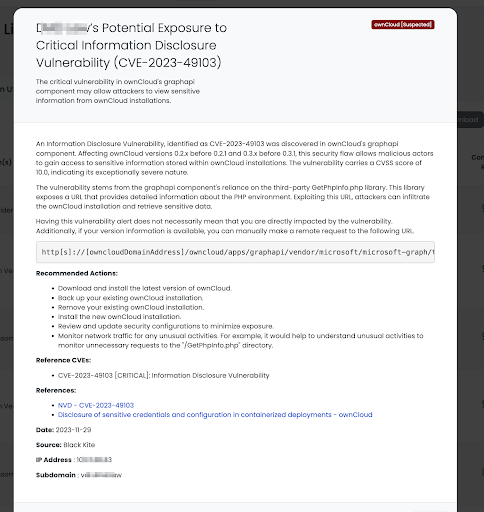
Within just 24 hours of the disclosure of CVE-2023-49103, Black Kite’s Research & Intelligence teams swiftly provided this critical vendor risk intelligence. By rapidly applying the ownCloud tags, Black Kite empowered its customers with timely and actionable data, underscoring the platform’s commitment to prompt and effective risk management solutions. This quick response demonstrates the agility and depth of Black Kite’s cyber risk intelligence capabilities, proving invaluable for TPRM professionals in navigating swiftly evolving cyber landscapes.
Black Kite’s scanning and tagging capabilities provide immense value to TPRM professionals. By identifying vendors using ownCloud, Black Kite enables a focused and efficient approach to managing cyber risks associated with vulnerabilities like CVE-2023-49103. This targeted identification saves significant time and resources, allowing TPRM teams to concentrate their efforts on the most pertinent risks. Thus, Black Kite not only enhances the effectiveness of cybersecurity strategies but also contributes to a more resilient digital ecosystem for its customers.
Assessing the Impact of OpenVPN Access Server Vulnerability on TPRM
What is OpenVPN Access Server Vulnerability CVE-2023-46850?
A critical use-after-free memory security issue, identified as CVE-2023-46850, was discovered in OpenVPN Access Server versions 2.11.0 through 2.11.3 and 2.12.0 through 2.12.1. This vulnerability poses a severe risk, as it could allow attackers to leak sensitive information from the server’s memory or, in more extreme cases, enable remote code execution (RCE), potentially granting them control over the affected server. To address this, OpenVPN released version 2.12.2, incorporating OpenVPN 2.6.7, which patches this vulnerability.
What Are the TPRM Risks of the OpenVPN Vulnerability?
This vulnerability underscores the importance of regular software updates and vigilant security practices in TPRM. The potential for sensitive data leakage and unauthorized remote code execution can significantly impact vendors using vulnerable versions of OpenVPN Access Server. TPRM strategies must now consider the heightened risk profile and increased likelihood of targeted attacks on these vendors, necessitating proactive measures to ensure their security posture is robust and up-to-date.
What Questions Should TPRM Professionals Ask Vendors Potentially Exposed to OpenVPN’s CVE-2023-46850?
- “Have you identified and addressed the impact of CVE-2023-46850 on your OpenVPN installations?”
- “Are you currently using a patched version of OpenVPN Access Server that resolves this vulnerability?”
- “What measures have you implemented to secure your VPN environment against similar vulnerabilities in the future?”
- “How are you monitoring for potential exploitation attempts or unauthorized access related to this vulnerability?”
Remediation Steps for Vendors Using OpenVPN Access Server:
Vendors should urgently take the following steps:
- Upgrade immediately to OpenVPN Access Server version 2.12.2 or later.
- Ensure all OpenVPN servers and clients are updated to the latest secure versions.
- Conduct a thorough review and update of security configurations.
- Monitor network traffic for signs of unusual or unauthorized activities, especially related to VPN access.
Leveraging Black Kite’s OpenVPN Tags for TPRM Strategy
Black Kite can assist TPRM professionals by identifying vendors that use OpenVPN Access Server through its non-intrusive internet-wide scanning capabilities. Although Black Kite cannot directly determine the versions in use, identifying vendors using OpenVPN is critical in understanding potential exposure and focusing risk management efforts. This approach allows TPRM teams to prioritize vendors who may be impacted and engage with them to verify and upgrade their OpenVPN installations, if necessary.
Black Kite’s capabilities in identifying and tagging vendors using OpenVPN Access Server provide significant value in managing and mitigating risks associated with CVE-2023-46850. By enabling targeted and efficient risk assessments, Black Kite helps TPRM professionals quickly identify and address potential vulnerabilities, enhancing the overall cybersecurity resilience of their vendor networks.
Ongoing Exploitation of Citrix Vulnerability: Citrix Bleed
What is the Citrix ‘Bleed’ Vulnerability?
In late August 2023, a critical vulnerability in Citrix NetScaler appliances, known as ‘Citrix Bleed’ and tracked as CVE-2023-4966, was discovered and subsequently exploited as a zero-day. This vulnerability required admins to take additional measures beyond patching, including wiping previous user sessions and terminating active ones. The reason for these extra steps is due to attackers stealing authentication tokens during the Citrix Bleed exploitation, which allowed them to maintain access to compromised devices even post-patching.
The severity of this vulnerability was highlighted when the LockBit ransomware gang exploited it, resulting in significant data breaches, including an attack on Boeing where 43GB of data were stolen and later leaked on the dark web. This incident underscores the vulnerability’s potential for widespread and severe impact, particularly when exploited by sophisticated cybercriminal groups.
Furthermore, it was reported that over 10,000 internet-exposed Citrix servers were vulnerable to Citrix Bleed attacks, illustrating the extensive reach and critical nature of this security flaw. This widespread vulnerability within Citrix servers presents a significant challenge for TPRM professionals, as it poses a direct threat to a large number of vendors and their networks.
What Questions Should TPRM Professionals Ask Vendors Potentially Exposed to Citrix ‘Bleed’?
Given the critical nature of the Citrix ‘Bleed’ vulnerability, TPRM professionals should query their vendors using Citrix NetScaler products with specific questions:
- “Can you confirm if your organization uses Citrix NetScaler ADC or Gateway, and if so, have you updated to the versions addressing CVE-2023-3519?”
- “What steps have you taken to check for signs of unauthorized access, such as new web shells or unusual HTTP error logs, post-update?”
- “How are you monitoring for and responding to potential ongoing exploits related to this vulnerability?”
- “Have you implemented any additional security measures in light of the Citrix ‘Bleed’ vulnerability to safeguard your systems?”
Remediation Steps for Vendors Using Citrix NetScaler Products
Vendors using Citrix NetScaler should urgently implement the following remediation steps:
- Update Citrix NetScaler ADC or NetScaler Gateway to the latest versions that address the CVE-2023-3519 vulnerability.
- If immediate patching isn’t feasible, restrict ingress IP addresses as a temporary measure.
- After upgrading, terminate all sessions and execute the CLI command: clear lb persistentSessions <vServer>.
- Rotate credentials for all identities accessing vulnerable appliances.
- Conduct thorough checks for signs of unauthorized access, such as new web shells, unusual HTTP error logs, and other indicators of compromise.
- Regularly monitor and review system logs and network traffic for anomalies that might indicate ongoing exploits.
- Implement enhanced security protocols and monitoring tools to detect and prevent future vulnerabilities and unauthorized access attempts.
These steps are vital to mitigate the risks associated with the Citrix ‘Bleed’ vulnerability and ensure the ongoing security of vendor networks.
How Can Black Kite Customers Effectively Utilize Citrix Gateway/ADC Tags?
Black Kite employs internet-wide scanners to perform non-intrusive digital footprint discovery, which is crucial in identifying vendors using Citrix NetScaler ADC or Gateway products. Given the widespread vulnerability of many versions of these products, the companies tagged by Black Kite are considered at risk. Here’s how customers can leverage this information:
- Use Black Kite’s scanning capabilities to identify vendors in your network using Citrix NetScaler products.
- Prioritize engagement with these vendors to ensure they have applied the necessary patches and taken recommended post-patching actions.
- Encourage continuous monitoring and stringent security measures among vendors to protect against potential exploitation.

Black Kite’s rapid response in applying and updating the Citrix Gateway/ADC tags – initially on July 16 and later updated on October 18 – demonstrates the platform’s commitment to providing timely and relevant risk intelligence. This proactive approach allows TPRM professionals to quickly identify at-risk vendors and take necessary actions to mitigate potential threats. Black Kite’s capabilities not only streamline the process of vendor risk assessment but also reinforce the overall cybersecurity resilience of customer networks against such critical vulnerabilities.
Operationalizing Focus Tags™: Maximizing Value and Strengthening Cybersecurity
Black Kite’s Focus Tags™ represent a pivotal tool in the arsenal of cybersecurity professionals. These tags, derived from thorough research and real-time analysis, provide targeted insights into the latest and most critical cyber vulnerabilities and incidents. Here’s how Black Kite customers can operationalize these Focus Tags™ to their maximum potential:
- Efficient Risk Identification: Use Focus Tags™ to quickly identify and assess vendors that might be impacted by specific cybersecurity incidents or vulnerabilities.
- Prioritized Risk Management: Focus Tags™ enable customers to prioritize their efforts on the most critical risks, ensuring that resources are allocated effectively.
- Proactive Engagement: Engage in informed discussions with vendors based on the intelligence provided by Focus Tags™, facilitating more productive and proactive risk mitigation efforts.
The Value of Focus Tags™:
The value derived from utilizing Focus Tags™ is substantial. They offer:
- Timeliness: Receive up-to-date information on the latest cyber threats, ensuring a rapid response.
- Relevance: Gain insights that are directly applicable to your vendor network, ensuring that your risk management strategies are highly targeted.
- Efficiency: Reduce the time and resources spent on identifying and assessing vendor risks, allowing for a more streamlined risk management process.
For organizations not yet utilizing Black Kite, this is a clarion call to enhance your cyber risk management strategies. Black Kite’s Focus Tags™, along with its suite of cyber risk intelligence tools, offer a comprehensive and proactive approach to managing third-party cyber risks.
Ready to unlock risk intelligence you can trust?
Take our platform for a test drive and request a demo today.
Focus Tags™ in the Last 30 days
- Qlik Sense: CVE-2023-48365, Unauthenticated RCE Vulnerability in Qlik Sense Enterprise for Windows
- Apache Superset: CVE-2023-40610, Privilege Escalation Vulnerability in Apache Superset <2.1.2 versions.
- OpenVPN Access: CVE-2023-46850, OpenVPN Access Server Flaw Exposes Sensitive Data and RCE Possible
- ownCloud: CVE-2023-49103, Information Disclosure Vulnerability in ownCloud’s Graphapi Component
- Atlassian Bamboo Data Center: CVE-2023-22516, RCE Vulnerability in Bamboo Data Center and Server Tagging
- Sophos Web Appliance: CVE-2023-1671 Pre-auth Command Injection Vulnerability in the version 4.3.10.3 and earlier
- Oracle Weblogic: CVE-2020-2551 Unauthenticated RCE Vulnerability over IIOP based on 10.3.6.0, 12.1.3.0, 12.2.1.3.0, 12.2.1.4.0
- Boeing Data Breach: Boeing Vendor Information disclosed in data breach
- Juniper Junos OS: CVE-2023–36845 Juniper Junos OS EX, SRX Series PHP External Variable Modification RCE Vulnerability
- SysAid: CVE-2023-47246 SysAid ITSM File System Path Traversal
- ServiceNow Data Exposure Flaw: ServiceNow clients
- SLP: CVE-2023-29552 LSP DOS
- Confluence: CVE-2023-22518 Confluence Data Center and Confluence Server Improper Authorization Vulnerability
- Apache ActiveMQ: CVE-2023-46604 Remote Code Execution Vulnerability
- F5 BIG-IP: CVE-2023-46747 and CVE-2023-46748 Remote Code Execution and Authenticated SQL Injection Vulnerabilities
- RoundCube: CVE-2023-5631RoundCube XSS Vulnerability
References:
https://blog.1password.com/okta-incident/
https://nvd.nist.gov/vuln/detail/CVE-2023-49103
https://nvd.nist.gov/vuln/detail/CVE-2023-46850
https://www.netscaler.com/blog/news/netscaler-investigation-recommendations-for-cve-2023-4966/
https://openvpn.net/security-advisory/access-server-security-update-cve-2023-46849-cve-2023-46850/

