FOCUS FRIDAY: TPRM INSIGHTS ON IVANTI EPMM, GOANYWHERE, AND VMWARE VULNERABILITIES
Written by: Ferhat Dikbiyik
Additional Contributions: Ferdi Gül and Yavuz Han
Edited by: Katherine Desy
Welcome to another engaging edition of Focus Friday. This week, we dive into the intricate world of Third-Party Risk Management (TPRM), examining some of the most pressing cybersecurity concerns. Our focus is on dissecting the complexities of recent high-profile vulnerabilities, specifically in Ivanti EPMM, GoAnywhere, and VMware vCenter. We’ll explore these issues through the lens of Black Kite’s innovative Focus Tags™, providing TPRM professionals with the insights needed to tackle these challenges effectively.
Ivanti EPMM Critical Authentication Bypass Vulnerabilities: CVE-2023-35082 and CVE-2023-35078
What is the Significance of the Ivanti EPMM Authentication Bypass Vulnerabilities?
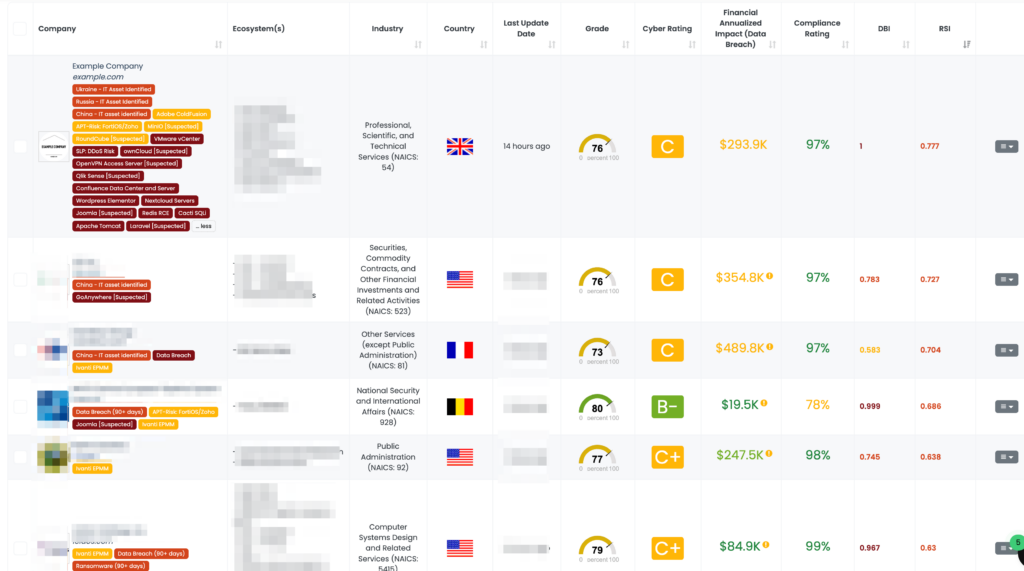
The Ivanti Endpoint Manager Mobile (EPMM) software has been identified with two critical vulnerabilities, CVE-2023-35082 and CVE-2023-35078, both categorized as authentication bypass issues. These vulnerabilities have high severity levels, with CVSS scores of 9.8. The EPSS score for CVE-2023-35082 is 6.81%, indicating a moderate likelihood of being exploited, while CVE-2023-35078 has a significantly higher EPSS of 95.33%, indicating a very high likelihood of exploitation. They have recently been discovered to pose a serious threat as they allow unauthorized remote access without credentials, leading to potential data breaches and unauthorized server modifications. CVE-2023-35078 is particularly notable for being actively exploited in the wild, with attacks first observed by government agencies in Norway. Both vulnerabilities were added to CISA’s KEV catalog on January 18, 2024, and CISA has published advisories emphasizing the urgent need for remediation.
Why Should TPRM Professionals Pay Attention to These Vulnerabilities?
From a TPRM perspective, the vulnerabilities in Ivanti EPMM are critically significant due to the product’s widespread use in managing mobile devices, including in sensitive sectors. An exploit of these vulnerabilities could lead to the leakage of sensitive information, unauthorized changes, and severe operational disruptions. This risk is particularly acute for organizations relying heavily on mobile device management, making it essential for TPRM professionals to promptly assess their vendors’ exposure to these vulnerabilities.
Essential Questions for Vendors Regarding Ivanti EPMM Vulnerabilities
TPRM professionals should ask the following specific questions to their vendors:
- Are your systems using Ivanti EPMM, particularly versions MobileIron Core <=11.10 and <=11.7?
- Have you applied the latest updates or the RPM script provided by Ivanti for these vulnerabilities?
- Can you provide evidence of a recent security audit or checks performed post-update to ensure no unauthorized access has occurred?
- What measures are in place to continuously monitor for signs of exploitation related to these vulnerabilities?
Remediation Recommendations for Vendors
Vendors affected by these vulnerabilities should:
- Immediately upgrade to the latest version of Ivanti EPMM.
- Apply the RPM script provided by Ivanti, especially for versions between 11.3 and 11.10.
- Conduct a thorough review of application configurations for any unauthorized changes.
- Continuously monitor systems for any signs of security breaches.
Leveraging Black Kite for Managing Ivanti EPMM Vulnerabilities
Black Kite published the Focus Tag™ for these vulnerabilities on December 7, 2023, with an update on January 18, 2024. TPRM professionals can use Black Kite’s platform to identify vendors using vulnerable versions of Ivanti EPMM and to obtain critical asset information, such as IP addresses and subdomains, that are at risk. This intelligence enables targeted and effective risk management, especially when dealing with a large number of vendors. The provision of detailed asset information sets Black Kite apart, offering a significant advantage in managing third-party risks efficiently.
GoAnywhere MFT Vulnerability: A Recall of the Cl0p Ransomware Incident (CVE-2024-0204)
What Does the GoAnywhere MFT Vulnerability (CVE-2024-0204) Entail?
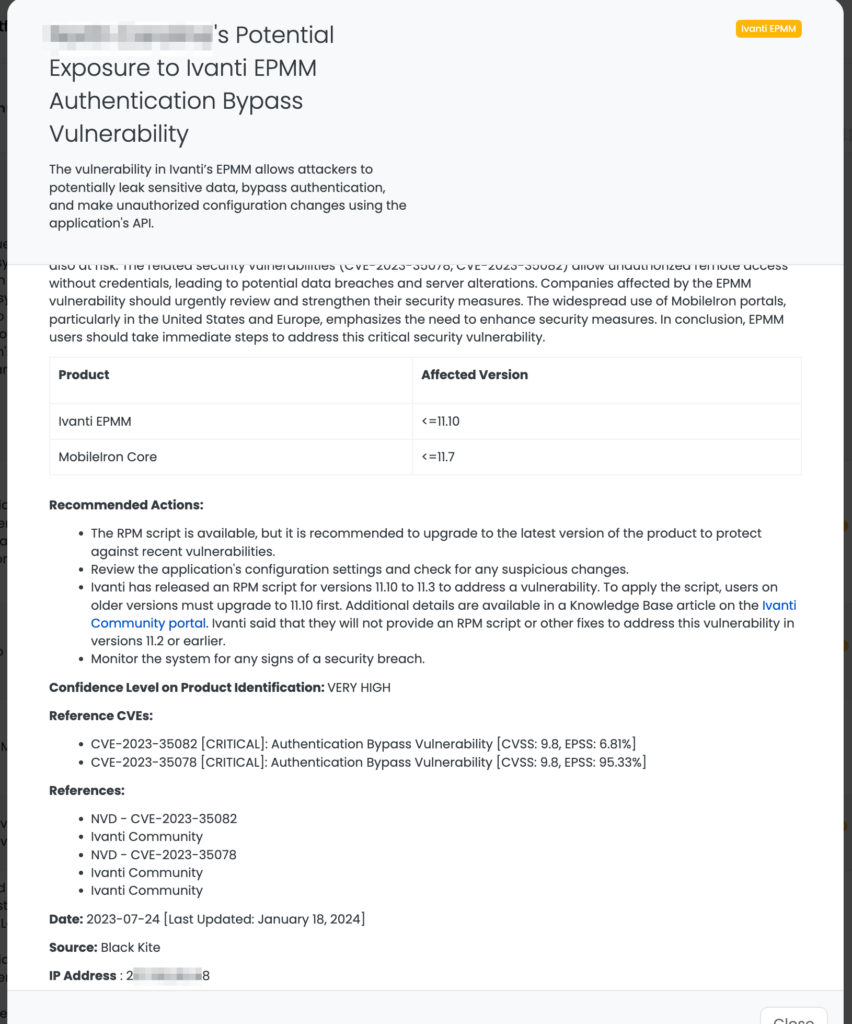
CVE-2024-0204, a critical authentication bypass issue in Fortra’s GoAnywhere MFT software, is a stark reminder of the potential dangers posed by such vulnerabilities. This flaw allows attackers to remotely create administrator accounts in versions prior to 7.4.1. With a CVSS score of 9.8 and an EPSS score of 0.06%, the threat it poses is heightened by the public availability of exploit code. Its quiet patching in December, followed by a recent public disclosure, has put many organizations on high alert.
Why is the GoAnywhere MFT Vulnerability Significant in a TPRM Context?
The history of the Cl0p ransomware group exploiting a similar vulnerability in GoAnywhere and MOVEit raises serious concerns. Their recent resurgence and known preference for targeting MFT server vulnerabilities underscore the urgency for TPRM professionals to ensure their vendors’ security against such threats. The potential for this new vulnerability to be similarly exploited necessitates a proactive, vigilant approach in third-party risk management.
Key Questions for Vendors About CVE-2024-0204
TPRM professionals should query their vendors:
- Have you implemented the patch for GoAnywhere MFT version 7.4.1 or later to mitigate CVE-2024-0204?
- What measures have been taken to monitor and detect unauthorized administrative access since the patch?
- Can you provide a timeline of actions taken following the disclosure of CVE-2024-0204?
- How are you ensuring ongoing vigilance against potential exploitation of this vulnerability, especially in light of past incidents like the Cl0p ransomware attack?
Remediation Steps for Vendors Impacted by CVE-2024-0204
Vendors using GoAnywhere MFT should:
- Ensure they have updated to version 7.4.1 or later.
- Review and restrict access to the administrative portal, employing strong password policies.
- Conduct thorough security audits to check for any traces of unauthorized access or modifications.
- Establish continuous monitoring protocols for abnormal activities, especially in administrative areas.
The Role of Black Kite in Addressing CVE-2024-0204
Black Kite’s publication of the Focus Tag™ on January 24, 2024, serves as a crucial resource for TPRM professionals. By providing detailed asset information and timely intelligence, Black Kite aids in the swift identification of potentially vulnerable systems. In light of the Cl0p ransomware group’s historical exploitation of similar vulnerabilities, the information from Black Kite becomes invaluable in preempting and mitigating potential threats.
VMware vCenter Server and the CVE-2023-34048 Vulnerability
What is the CVE-2023-34048 Vulnerability in VMware vCenter Server?
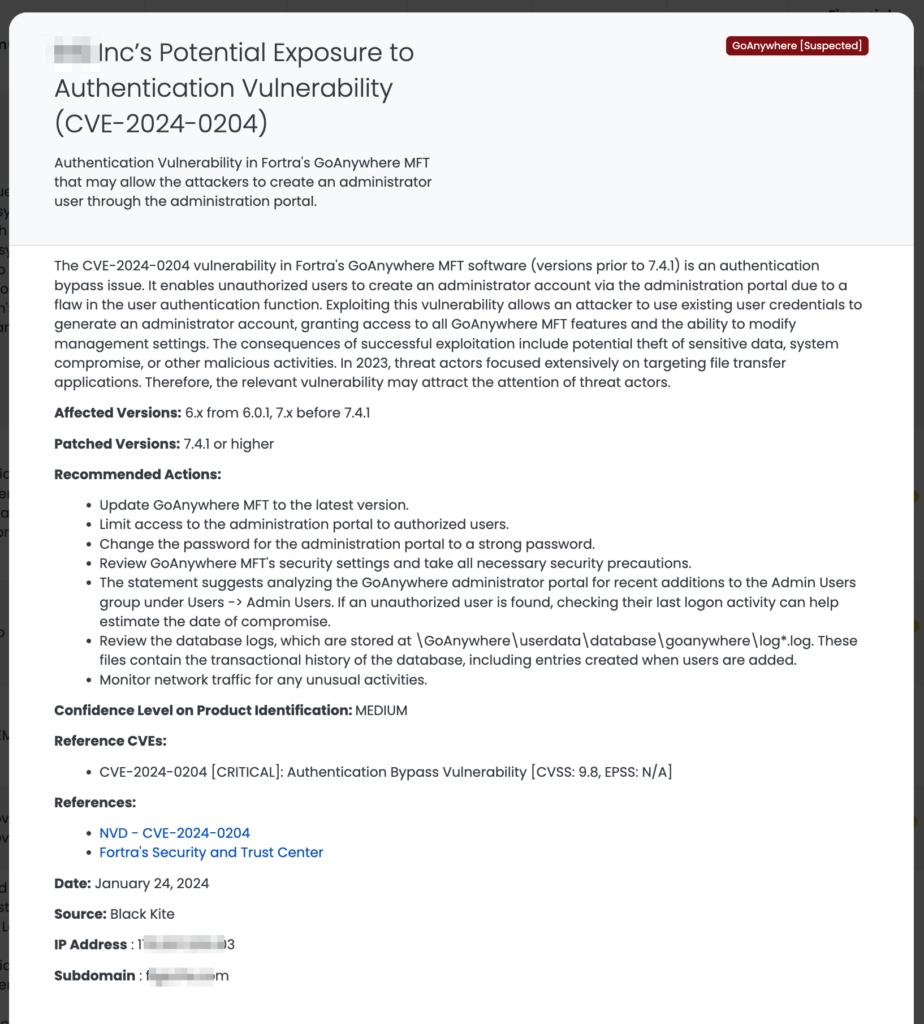
CVE-2023-34048 is a critical vulnerability in VMware vCenter Server, identified as an out-of-bounds write issue in the implementation of the DCERPC protocol. It is classified with a CVSS score of 9.8, indicating its high severity. This vulnerability, which allows remote code execution, was added to CISA’s Known Exploited Vulnerabilities Catalog on January 22, 2024. Notably, it has been exploited by Chinese hackers as a zero-day for two years.
Why is CVE-2023-34048 Critical for TPRM Professionals?
The active exploitation of CVE-2023-34048 by sophisticated APT groups, particularly the Chinese cyber espionage group UNC3886, makes it a significant concern for TPRM professionals. These groups have leveraged the vulnerability to breach vCenter servers and deploy backdoors, indicating a high level of sophistication and targeting. The fact that this vulnerability remained a zero-day for an extended period highlights the critical need for constant vigilance and prompt action on emerging threats in virtualization platforms.
Questions for Vendors Concerning CVE-2023-34048
- Are you aware of and have you patched the CVE-2023-34048 vulnerability in your VMware vCenter Server?
- What steps have you taken to monitor and prevent exploitation similar to the attacks by UNC3886 and other APT groups?
- Can you confirm the implementation of enhanced security measures post-patching to protect against advanced persistent threats?
- How are you ensuring the ongoing security of your VMware infrastructure in light of the recent advanced exploitation techniques?
Remediation Recommendations
Vendors should urgently:
- Apply the latest patches provided by VMware for CVE-2023-34048.
- Continuously monitor systems for signs of compromise or unusual activities.
- Implement advanced security measures, including EDR solutions, to detect and mitigate sophisticated attacks.
- Engage in regular security audits and assessments to identify and address potential vulnerabilities proactively.
Leveraging Black Kite in Response to CVE-2023-34048
Black Kite’s platform plays a pivotal role in enabling TPRM professionals to effectively manage the risks associated with CVE-2023-34048. By providing comprehensive and up-to-date intelligence, Black Kite aids in identifying potentially vulnerable systems and assists in prioritizing and guiding remediation efforts, particularly in environments susceptible to sophisticated APT exploits like those conducted by UNC3886.
Enhancing TPRM Strategies with Black Kite’s Focus Tags™
As we navigate the dynamic and often tumultuous landscape of cybersecurity threats, Black Kite’s Focus Tags™ stand out as pivotal tools in the arsenal of any adept Third-Party Risk Management (TPRM) professional. This week, we’ve scrutinized a range of vulnerabilities, from the Ivanti EPMM and GoAnywhere breaches to the complex challenges posed by VMware vCenter. Each presents unique risks and requires nuanced responses, a task made more manageable by the strategic use of Focus Tags™. Here’s a glimpse of how these tags revolutionize TPRM tactics:
- Immediate Threat Identification: Black Kite’s Focus Tags™ rapidly pinpoint vendors impacted by these specific vulnerabilities, allowing TPRM teams to initiate prompt and effective responses.
- Prioritization and Resource Allocation: These tags aid in discerning the criticality of each vulnerability in relation to vendor significance, ensuring optimal distribution of attention and resources.
- Enhanced Vendor Dialogue: Armed with precise information, TPRM professionals can engage in targeted discussions with vendors, focusing on their particular vulnerabilities and defense strategies.
- Holistic View of Threats: Offering more than just isolated data points, Black Kite’s Focus Tags™ present an expansive view of the cybersecurity threat landscape, enabling a strategic, all-encompassing approach to cybersecurity defenses.
In light of this week’s highlighted vulnerabilities, the value of Black Kite’s Focus Tags™ in transforming complex cyber threat intelligence into actionable insights is unequivocally clear. For TPRM professionals seeking to proactively and effectively navigate the ever-shifting sands of cybersecurity threats, these tags are not just tools but essential guides.
Want to take a closer look at Focus Tags™?
Take our platform for a test drive and request a demo today.
Focus Tags™ in the last 30 days:
- Citrix ADC/Gateway:CVE-2023-6549 [Updated], Buffer Overflow Vulnerability
- Ivanti EPMM:CVE-2023-35082 [Updated], Authentication Bypass Vulnerability
- GoAnywhere [Suspected]:CVE-2024-0204, Authentication Bypass Vulnerability
- Redis RCE: CVE-2023-41056, Remote Code Execution Vulnerability
- Ivanti ICS: CVE-2024-21887, Command Injection Vulnerability, CVE-2023-46805, Authentication Bypass Vulnerability
- Cacti SQLi: CVE-2023-51448, Blind SQL Injection (SQLi) Vulnerability
- Juniper OS:CVE-2024-21591 [Updated Tag], Remote Code Execution Vulnerability
- Kyocera Device Manager [Suspected]:CVE-2023-50916, Path Traversal Vulnerability
- Apache Tomcat:CVE-2023-46589, Improper Input Validation Vulnerability
- Laravel [Suspected]:CVE-2018-15133, Deserialization of Untrusted Data Vulnerability
- SonicWall SonicOS: CVE-2023-0656, A Stack-Based Buffer Overflow Vulnerability, DOS Attack, RCE Vulnerability
- Confluence Data Center and Server:CVE-2023-22527 [Updated Tag], Template Injection Vulnerability
- Citrix ADC/Gateway:CVE-2023-6549 [Updated], Buffer Overflow Vulnerability
- Adobe ColdFusion: CVE-2023-29300 and CVE-2023-38203, Deserialization of Untrusted Data Vulnerability [Updated]
- Joomla: CVE-2023-23752, Improper Access Control Vulnerability in Joomla
- Apache Superset Auth. Bypass: CVE-2023-27524, Insecure Default Initialization of Resource Vulnerability in Apache Superset
- NextCloud Servers: CVE-2023-49792, Trusted Proxy Remote Address Spoofing Vulnerability in Nextcloud Server and Enterprise Server
- Barracuda ESG: CVE-2023-7102, Parameter Injection Vulnerability
References:
- https://forums.ivanti.com/s/article/CVE-2023-35082-Remote-Unauthenticated-API-Access-Vulnerability-in-MobileIron-Core-11-2-and-older https://forums.ivanti.com/s/article/CVE-2023-35078-Remote-unauthenticated-API-access-vulnerability
- https://www.fortra.com/security/advisory/fi-2024-001
- https://twitter.com/TheDFIRReport/status/1749066611678466205
- https://core.vmware.com/resource/vmsa-2023-0023-questions-answers#current-update
- https://www.cisa.gov/news-events/alerts/2023/10/26/vmware-releases-security-advisory-vcenter-server https://www.mandiant.com/resources/blog/chinese-vmware-exploitation-since-2021

