FOCUS FRIDAY: TPRM INSIGHTS ON CISCO ASA, FTD & IOS, VMWARE VCENTER, WD MY CLOUD, AND FORMBRICKS VULNERABILITIES
Written by: Ferdi Gül
Welcome to this week’s edition of Focus Friday, where we explore recent high-profile vulnerabilities through the lens of Third-Party Risk Management (TPRM). In this issue, we examine critical flaws impacting widely used platforms and devices, including Cisco ASA, Cisco IOS family products, VMware vCenter, Western Digital My Cloud NAS devices, and the open-source Formbricks framework. These vulnerabilities range from remote code execution to authentication bypass, each carrying unique implications for organizations and their supply chains. Our analysis highlights not just the technical details, but why these issues matter to TPRM professionals and how they can take immediate, informed action.
CVE-2025-20333 & CVE-2025-20362 – Cisco ASA and FTD
Among the ongoing Cisco vulnerabilities that have not been discussed since last week, in our blog post last week we mentioned the Cisco SNMP vulnerability. If you’d like to revisit the details of that vulnerability, you can find them here.
What are the Cisco ASA Zero-Day Vulnerabilities?
Two zero-day vulnerabilities have been identified in Cisco Secure Firewall Adaptive Security Appliance (ASA) Software and Firepower Threat Defense (FTD) Software, actively exploited by the threat actor cluster known as ArcaneDoor (UAT4356 / Storm-1849).
- CVE-2025-20333 (Critical) is a buffer overflow vulnerability (CVSS: 9.9, EPSS: 0.84%) affecting the VPN web server. Attackers with valid VPN credentials can send crafted HTTP requests to execute arbitrary code as root.
- CVE-2025-20362 (Medium) is a missing authorization flaw (CVSS: 6.5, EPSS: 0.68%) that allows unauthenticated remote attackers to access restricted web endpoints through malicious HTTP requests.
Both vulnerabilities were disclosed and added to the CISA KEV catalog on September 25, 2025, with exploitation confirmed in the wild. Cisco advisories confirm that attackers have leveraged these flaws for persistent access, even manipulating read-only memory (ROM) for survival across reboots and upgrades. No public PoC code is available, but active campaigns have been reported .
Why should TPRM professionals care about these vulnerabilities?
Cisco ASA and FTD appliances are commonly deployed as perimeter defense and VPN gateways, which means they manage sensitive remote access sessions across enterprise networks. A compromise at this layer:
- Provides adversaries with privileged access to internal environments.
- May enable credential theft or lateral movement into corporate systems.
- Undermines confidence in VPN security, exposing confidential communications.
- Could allow persistent footholds through firmware-level tampering.
For organizations that rely on third-party vendors using Cisco ASA or FTD, the vendor’s failure to patch or detect compromise could directly impact downstream data confidentiality and availability.
What questions should TPRM professionals ask vendors about these vulnerabilities?
When assessing vendor exposure, ask:
- Have you applied the official security updates provided by Cisco to patch both CVE-2025-20333 and CVE-2025-20362 vulnerabilities in your Cisco Secure Firewall Adaptive Security Appliance (ASA) Software and Cisco Secure Firewall Threat Defense (FTD) Software?
- Can you confirm if you have implemented CISA’s Emergency Directive ED 25-03 and applied the recommended mitigations within 24 hours of the inclusion of CVE-2025-20333 and CVE-2025-20362 in the Known Exploited Vulnerabilities (KEV) Catalog?
- Have you checked your systems for unauthorized ROM modifications, which is a persistence mechanism tied to the exploitation campaign by the advanced threat actor ArcaneDoor?
- 4. Have you followed CISA’s emergency directive to identify, analyze, and mitigate potential compromises, including searching for IOCs linked to ArcaneDoor, in response to the vulnerabilities CVE-2025-20333 and CVE-2025-20362?
Remediation Recommendations for Vendors subject to this risk
Vendors operating affected appliances should:
- Apply Cisco security updates immediately, following the official advisories for ASA and FTD.
- Implement CISA’s Emergency Directive ED 25-03, which mandates mitigations within 24 hours for KEV-listed flaws.
- Scan and investigate for IOCs tied to ArcaneDoor, including ROM modification, persistence techniques, and malware signatures.
- Harden VPN web servers by enforcing strong credential policies and limiting external access wherever possible.
- Enable and monitor Secure Boot on Firepower appliances to detect firmware tampering attempts.
How can TPRM professionals leverage Black Kite for this vulnerability?
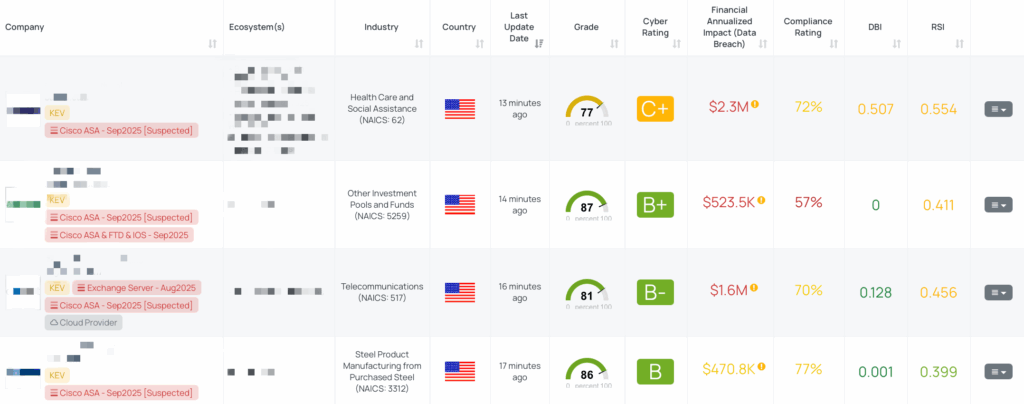
Black Kite published the Cisco ASA – Sep2025 Focus Tag on September 26, 2025, shortly after the vulnerabilities were added to the CISA KEV catalog. The Focus Tag identifies vendors potentially exposed to these zero-days and provides associated IP addresses or subdomains tied to ASA/FTD deployments.
From a TPRM perspective, this Focus Tag allows organizations to:
- Quickly pinpoint at-risk vendors without sending blanket questionnaires.
- Validate vendor patching activity against the provided asset information.
- Prioritize risk discussions with vendors confirmed to be operating affected Cisco security appliances.
CVE-2025-20363 – Cisco ASA, FTD, IOS, IOS XE, IOS XR
What is the Cisco ASA & FTD & IOS Buffer Overflow Vulnerability?
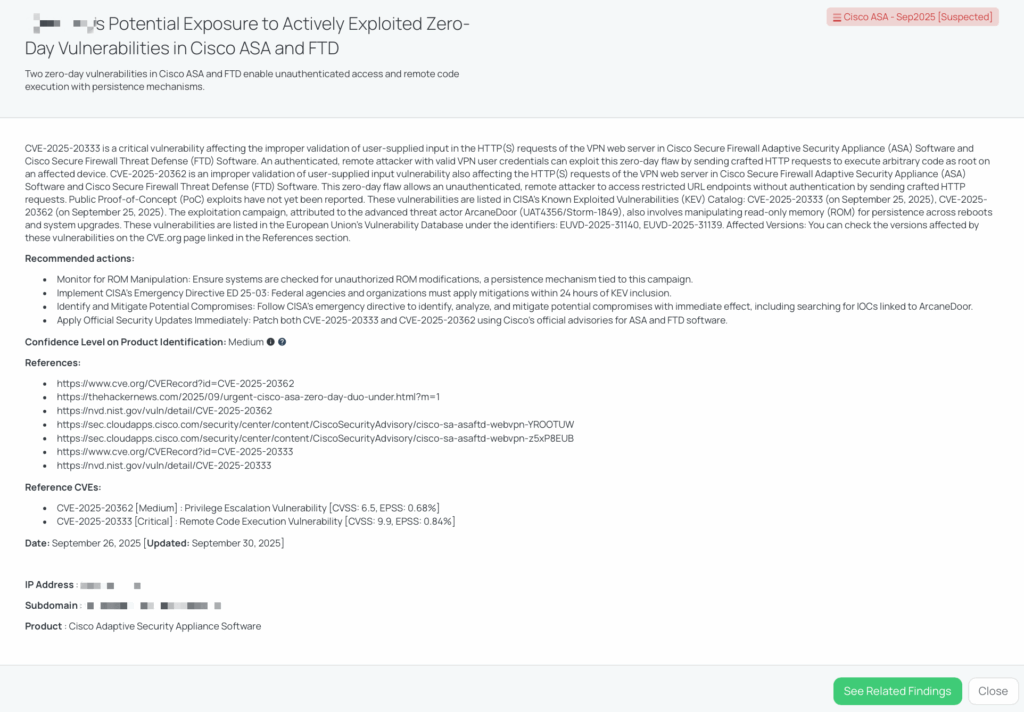
CVE-2025-20363 is a heap-based buffer overflow vulnerability (CWE-122) in the WebVPN file-upload handler of Cisco ASA, FTD, IOS, IOS XE, and IOS XR. It carries a CVSS score of 9.0 (Critical) and an EPSS score of 0.12%. Successful exploitation leads to root-level remote code execution (RCE).
The flaw affects a broad range of Cisco products, with more than 2,500 versions listed as vulnerable. On ASA and FTD appliances, the attack requires no authentication, making it highly dangerous for internet-exposed SSL VPN services. For IOS-based systems, low-privilege credentials are required, but adversaries can chain this with other zero-days (such as CVE-2025-20333 and CVE-2025-20362) to achieve full RCE without credentials.
Cisco disclosed this vulnerability on September 25, 2025, along with related zero-days, and released patches immediately. While exploitation has not yet been confirmed in the wild, security researchers assess it as a high-risk candidate for weaponization by advanced actors. It is not currently listed in the CISA KEV Catalog, but defenders are urged to treat it as a critical threat.
Why should TPRM professionals care about this vulnerability?
Cisco ASA, FTD, and IOS devices are widely used as enterprise firewalls, VPN gateways, and edge routers. If exploited:
- Attackers can seize administrative control of perimeter defenses, bypassing segmentation.
- Compromised devices may be used to intercept VPN traffic or conduct man-in-the-middle attacks.
- Organizations depending on vendor-managed infrastructure risk indirect exposure if vendors fail to remediate quickly.
- Long-lived persistence (e.g., through bootkits like RayInitiator or malware such as LINE VIPER) makes eradication difficult.
For third-party risk programs, any vendor running unpatched Cisco security appliances becomes a potential conduit for adversary lateral movement into supply chains.
What questions should TPRM professionals ask vendors about this vulnerability?
To evaluate vendor exposure, consider:
- Have you updated all affected Cisco products, including ASA, FTD, IOS, IOS XE, and IOS XR to the latest fixed version to mitigate the risk of CVE-2025-20363?
- Can you confirm if you have implemented a Zero Trust Architecture (ZTA) to eliminate the attack surface and render unauthenticated perimeter vulnerabilities like CVE-2025-20363 ineffective?
- Have you performed comprehensive threat hunting and forensics following CISA’s detailed Core Dump and Hunt Instructions for all public-facing ASA devices to detect any compromise related to CVE-2025-20363?
- 4. Can you confirm if you have reset the device to factory default, reconfigured the device from scratch with new passwords, and re-generated all certificates and keys used on the appliance after upgrading to a fixed release of the affected Cisco products?
Remediation Recommendations for Vendors subject to this risk
Vendors operating affected Cisco systems should:
- Patch immediately using Cisco’s official software updates across ASA, ASAv, FTD, IOS, IOS XE, and IOS XR. Workarounds are not supported.
- Conduct full threat hunting to detect IOCs tied to exploitation, including ROM manipulation and bootkits.
- Assume compromise if any signs are detected: reset devices to factory defaults, reconfigure from scratch, rotate all credentials, and regenerate certificates.
- Limit exposure by restricting VPN/HTTPS interfaces to trusted networks only, and enforce multi-factor authentication (MFA) for IOS-based products requiring low-privilege credentials.
- Adopt Zero Trust principles, reducing reliance on perimeter VPN appliances and mitigating lateral movement.
How can TPRM professionals leverage Black Kite for this vulnerability?
Black Kite published the Cisco ASA & FTD & IOS – Sep2025 Focus Tag on September 28, 2025, covering CVE-2025-20363. The tag highlights vendors potentially running exposed Cisco appliances and provides associated IP addresses or subdomains tied to affected systems.
For TPRM teams, this Focus Tag enables:
- Rapid identification of vendors at risk, reducing the scope of outreach.
- Verification of vendor remediation timelines against real-world asset data.
- Prioritization of security questionnaires toward vendors most exposed to perimeter compromise.
By operationalizing this tag, customers can directly correlate vendor assets with Cisco’s affected product lines, ensuring faster mitigation and reduced supply chain risk.
CVE-2025-41250 – VMware vCenter
What is the VMware vCenter SMTP Header Injection Vulnerability?
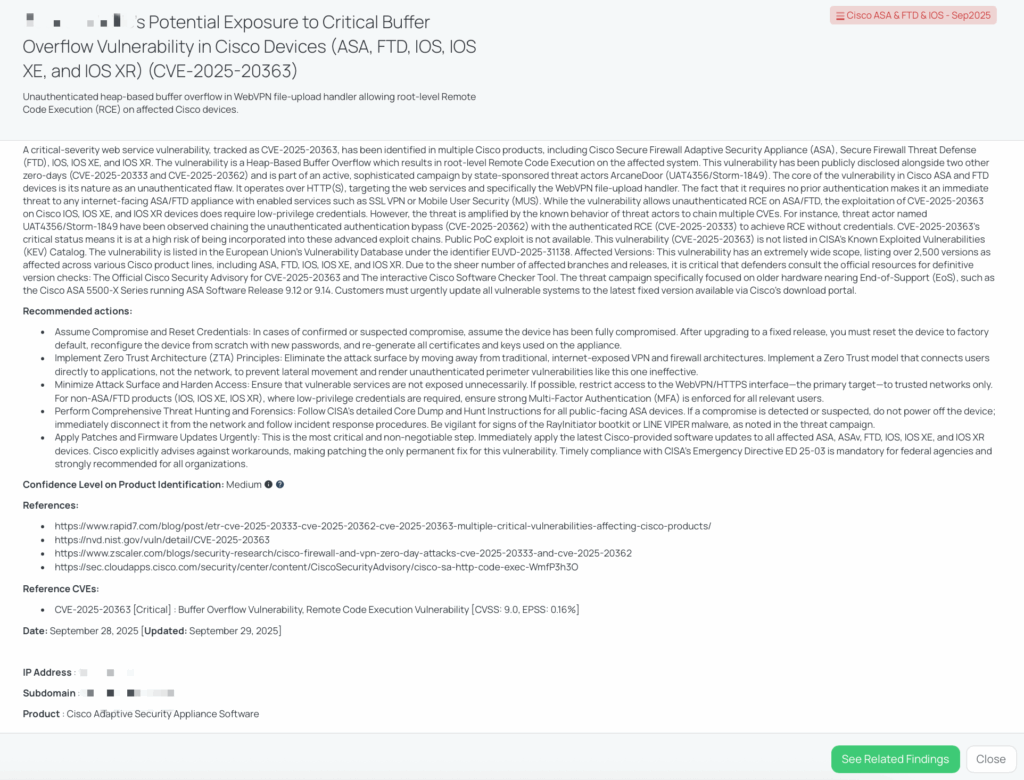
CVE-2025-41250 is a SMTP header injection flaw in VMware vCenter Server. It has a CVSS score of 8.5 (High) and an EPSS score of 0.05%. The vulnerability allows a malicious actor with non-administrative privileges, who can create scheduled tasks, to manipulate notification emails generated by vCenter.
The issue was disclosed on September 29, 2025, as part of VMware’s advisory (VMSA-2025-0016). Exploitation requires that an SMTP server is configured in vCenter. While no public Proof-of-Concept is available and the vulnerability is not listed in the CISA KEV catalog, it is recognized in the EU Vulnerability Database. Broadcom assessed the severity as Important, and no workarounds are provided.
Why should TPRM professionals care about this vulnerability?
VMware vCenter is a critical management component in many enterprise environments, orchestrating virtualization infrastructure. If abused:
- Attackers could alter or forge system notifications, leading to disinformation or evasion of security monitoring.
- By chaining email manipulation with username enumeration or weak password recovery flaws, attackers might gain a broader foothold in enterprise systems.
- Vendors relying on vCenter for infrastructure management may unknowingly propagate fraudulent or misleading notifications downstream to their clients.
From a TPRM standpoint, vendors using unpatched vCenter versions could introduce risks of compromised administrative workflows and exposure of sensitive operational data.
What questions should TPRM professionals ask vendors about this vulnerability?
When assessing risk, targeted questions include:
- Which version of VMware vCenter Server are you currently running, and does it fall into the affected range?
- Have you applied the fixed versions (9.0.1.0, 8.0 U3g, 7.0 U3w, 5.2.2, or the corresponding Telco Cloud patches) to remediate CVE-2025-41250?
- Have you reviewed user permissions, especially for non-administrative accounts with scheduled task privileges, to minimize exploitation risk?
- Do you have monitoring in place to detect unauthorized changes to scheduled tasks or unexpected email activity originating from vCenter?
Remediation Recommendations for Vendors subject to this risk
To mitigate exposure, vendors should:
- Apply official updates immediately, upgrading to the patched versions specified in Broadcom’s advisory.
- Inventory and verify all vCenter instances across the environment, ensuring no outdated builds remain active.
- Enforce least-privilege principles, restricting scheduled task creation to trusted accounts only.
- Implement monitoring and alerting for unusual SMTP or task-related activity within vCenter.
How can TPRM professionals leverage Black Kite for this vulnerability?
Black Kite released the VMware vCenter – Sep2025 Focus Tag on September 30, 2025, mapping out vendors potentially at risk from CVE-2025-41250. The tag identifies exposed vCenter assets, including IPs and subdomains, allowing risk teams to:
- Quickly determine vendor exposure to this vulnerability.
- Prioritize outreach to vendors confirmed to be running vulnerable VMware versions.
- Cross-check remediation status against asset intelligence, reducing guesswork and improving efficiency.
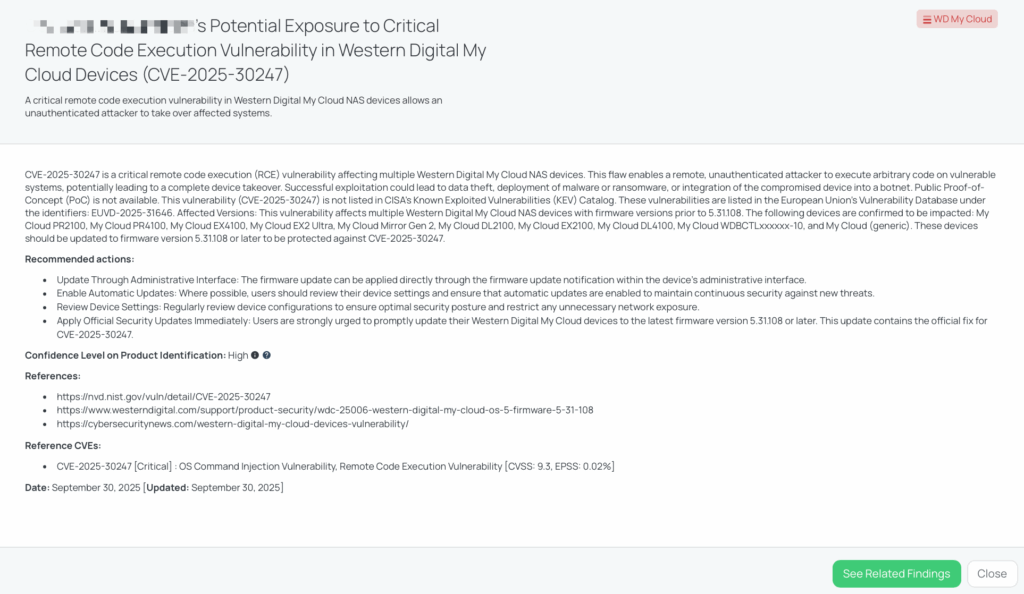
CVE-2025-30247 – WD My Cloud
WD My Cloud is a personal cloud storage solution developed by Western Digital (WD). Essentially, it is a Network Attached Storage (NAS) device that provides centralized file storage, backup, and sharing solutions for homes or small to medium-sized businesses.
What is the WD My Cloud Command Injection Vulnerability?
CVE-2025-30247 is a command injection vulnerability in Western Digital My Cloud NAS devices. It is rated Criticalwith a CVSS score of 9.3 and an EPSS score of 0.87%. The flaw allows a remote, unauthenticated attacker to execute arbitrary code, leading to full device takeover.
The vulnerability was disclosed on September 24, 2025, with firmware update version 5.31.108 released as the fix. Exploitation could enable attackers to steal stored data, deploy ransomware, or enlist the compromised NAS devices into botnets. Currently, there is no public PoC exploit available, and it is not listed in the CISA KEV Catalog. However, its severity and the popularity of My Cloud devices make it a high-risk issue for consumers and businesses alike.
Why should TPRM professionals care about this vulnerability?
NAS devices like WD My Cloud are often used by vendors for data backup, storage, and file sharing. If compromised:
- Attackers can exfiltrate sensitive vendor or customer data.
- Devices may be weaponized to deliver malware or ransomware within vendor environments.
- Vendors could unknowingly expose clients to risk by hosting critical files on vulnerable, internet-connected storage systems.
From a TPRM perspective, unmanaged NAS exposures at vendors present a direct risk to data confidentiality and availability in supply chains.
What questions should TPRM professionals ask vendors about this vulnerability?
When evaluating vendor exposure, questions include:
- Do you operate WD My Cloud NAS devices in your environment, and if so, which models and firmware versions?
- Have you updated all My Cloud devices to firmware version 5.31.108 or later?
- Are automatic firmware updates enabled to ensure future vulnerabilities are patched promptly?
- How do you monitor NAS devices for unusual activity, such as unauthorized access or changes to stored data?
Remediation Recommendations for Vendors subject to this risk
To mitigate the risk, vendors should:
- Update to firmware 5.31.108 or later immediately, which contains the official fix for CVE-2025-30247.
- Apply updates via the administrative interface and verify all devices reflect the new version.
- Enable automatic updates to reduce patching delays for future vulnerabilities.
- Restrict unnecessary network exposure, ensuring NAS devices are not directly accessible from the internet.
- Audit device configurations regularly to enforce security best practices.
How can TPRM professionals leverage Black Kite for this vulnerability?
Black Kite released the WD My Cloud Focus Tag on September 30, 2025, identifying vendors potentially running vulnerable NAS devices. The tag highlights exposed assets, such as IP addresses and device subdomains, that may host outdated firmware.
For TPRM teams, this Focus Tag provides:
- Visibility into vendor deployments of WD My Cloud devices.
- Confirmation of patching status against known affected versions.
- Prioritization of risk assessments toward vendors most likely to be impacted.
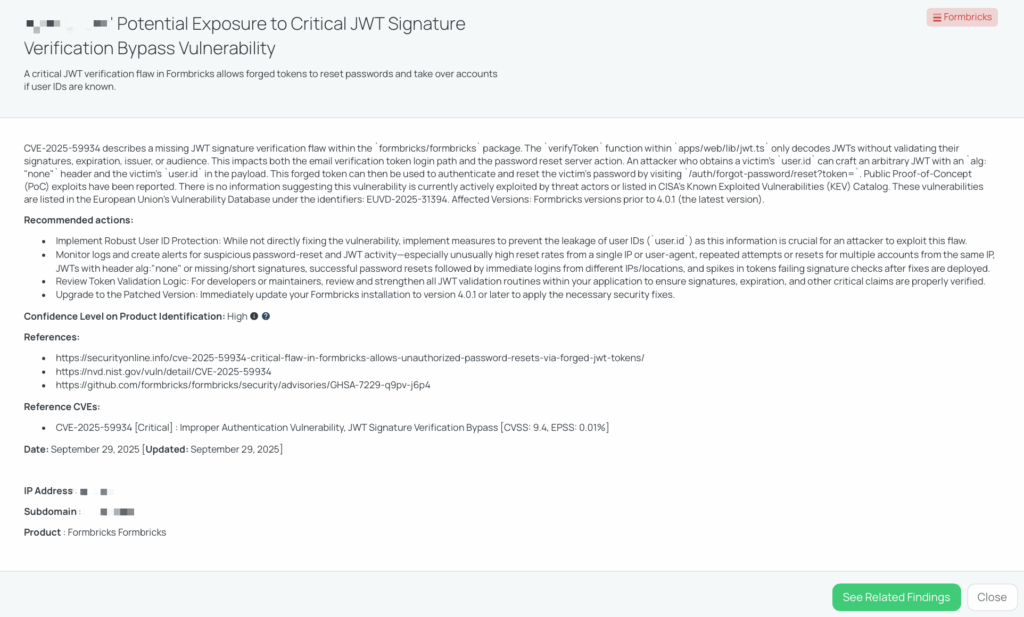
CVE-2025-59934 – Formbricks
Formbricks is an open-source Experience Management (XM) platform. It has been developed to collect user feedback, conduct surveys, and analyze user experience.
What is the Formbricks JWT verification bypass vulnerability?
CVE-2025-59934 is a critical authentication/validation flaw in the formbricks/formbricks package where the JWT verification routine decodes tokens without validating signatures, expiration, issuer, or audience. It is scored CVSS 9.4 (Critical) and has an EPSS of 0.01%. An attacker who knows a victim’s user.id can craft a forged JWT (for example using alg: “none”) and use it to authenticate as the victim or to perform a password reset via the application’s password-reset flow. Public proof-of-concept exploit code and detailed exploit steps are documented in the project advisory.
- First public advisory and PoC publication: Sep 26, 2025.
- Exploitation in the wild: No confirmed active exploitation reported at the time of the advisory.
- CISA KEV: Not listed in the KEV catalog.
- Vendor advisory / patch: Formbricks published a security advisory and patched the issue in version 4.0.1.
Why should TPRM professionals care about this vulnerability?
Formbricks is used to build user-facing web flows (forms, authentication, password resets). This flaw directly undermines authentication integrity: if an attacker can reset passwords or authenticate as users, they can access accounts, view or export sensitive submissions, and perform administrative or data-exfiltration actions depending on that installation’s permissions. From a third-party risk perspective, a compromised Formbricks instance hosted by a vendor could expose customer data, allow escalation into connected systems, or enable supply-chain abuse (fraudulent form submissions, account takeovers, or lateral access into other services). Because exploitation requires only knowledge of a user.id, leaked or guessable identifiers increase risk substantially.
What questions should TPRM professionals ask vendors about this vulnerability?
Use these targeted questions when assessing vendor exposure:
- Do you run Formbricks instances in production, and if so which versions? (Please list hostnames/IPs and version numbers.)
- Have all instances been upgraded to Formbricks 4.0.1 or later? If not, what is your patch schedule and mitigation plan?
- Where do you store or expose user identifiers (user.id)? Have you audited logs, APIs, or public endpoints for possible ID leakage?
- Have you monitored for unusual password-reset activity, forged-JWT attempts, or successful resets originating from unexpected IPs or user-agents?
Remediation recommendations for vendors subject to this risk
Recommended actions for any affected vendor or maintainer:
- Upgrade immediately to Formbricks 4.0.1 (or later) which contains the fix for the JWT verification bypass.
- Audit JWT handling across the codebase: replace any use of jwt.decode (without verification) with jwt.verifyor equivalent that enforces signature, exp, iss, and aud checks.
- Rotate session tokens and force password resets for accounts if compromise is suspected; consider short-lived session tokens while remediation is applied.
- Harden exposure of user identifiers: treat user.id as sensitive — avoid embedding or exposing it in public URLs, APIs, or client-side code where possible.
- Add monitoring and alerts for abnormal password reset rates, repeated use of tokens with alg:”none”, or resets followed by immediate access from distant geolocations.
- Perform a log review and incident hunt to detect any successful misuse of the password-reset flow prior to patching.
How can TPRM professionals leverage Black Kite for this vulnerability?
Black Kite published the Formbricks Focus Tag (late September 2025), mapping vendors and assets that may be running vulnerable Formbricks versions. TPRM teams can use the tag to:
- Identify which third parties in their vendor inventory host detectable Formbricks endpoints.
- Prioritize outreach to vendors that show exposed or unpatched instances and require immediate patching or compensating controls.
- Verify remediation by rechecking discovered assets after vendors report patching.
- Reduce unnecessary questionnaire volume by focusing follow-up on vendors that Black Kite intelligence shows as demonstrably exposed.
Maximizing Third-Party Risk Management with Black Kite’s Focus Tags™
The vulnerabilities covered this week reveal how quickly risks can emerge across critical infrastructure, enterprise virtualization environments, personal cloud devices, and open-source platforms. Addressing these threats effectively requires visibility beyond internal systems. That’s where Black Kite’s Focus Tags™ bring significant value to TPRM strategies.
Focus Tags empower risk teams with:
- Real-Time Risk Detection – Identify vendors exposed to these vulnerabilities within hours of disclosure.
- Risk-Based Prioritization – Focus attention on the most business-critical vendors impacted by severe vulnerabilities.
- Vendor-Specific Engagement – Ask vendors precise, vulnerability-tailored questions rather than sending broad questionnaires.
- End-to-End Risk Context – Correlate technical exposure with business impact by tying affected assets (IP addresses, domains, and subdomains) to vendors in your ecosystem.
By operationalizing Black Kite’s Focus Tags™, TPRM teams transform overwhelming volumes of threat data into clear, actionable intelligence. This approach not only accelerates response times but also reduces vendor fatigue, ensuring organizations can stay resilient as cyber threats continue to evolve.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTags™ in the Last 30 Days:
- Cisco ASA – Sep2025: CVE-2025-20333, CVE-2025-20362, Buffer Overflow Vulnerability, Missing Authorization in Cisco ASA and Cisco FTD.
- Cisco ASA & FTD & IOS – Sep2025: Buffer Overflow Vulnerability, Remote Code Execution Vulnerability in Cisco ASA, Cisco IOS, and Cisco FTD.
- VMware vCenter – Sep2025: CVE-2025-41250, SMTP Header Injection Vulnerability, Username Enumeration Vulnerability, Weak Password Recovery Mechanism Vulnerability in VMware vCenter.
- WD My Cloud: CVE-2025-30247, Command Injection Vulnerability in multiple Western Digital My Cloud network-attached storage (NAS) devices.
- Formbricks: CVE-2025-59934, Remote Code Execution Vulnerability in Formbricks.
- GoAnywhere – Sep2025: CVE-2025-10035, Deserialization Remote Code Execution Vulnerability in Fortra GoAnywhere MFT.
- SolarWinds Web Help Desk – Sep2025: CVE-2025-26399, Remote Code Execution Vulnerability in SolarWinds Web Help Desk.
- Cisco SNMP – Sep2025: CVE-2025-20352, Stack Overflow Vulnerability leading to DoS and Remote Code Execution in Cisco IOS and IOS XE Software.
- DNN Software: CVE-2025-59545, Stored Cross-Site Scripting (XSS) Vulnerability in DNN Prompt Module.
- Jetty – MadeYouReset: CVE-2025-5115, MadeYouReset DoS Vulnerability in Eclipse’s Jetty.
- Jenkins – Sep2025: CVE-2025-59474, CVE-2025-59475, CVE-2025-59476, Information Disclosure Vulnerability, Log Message Injection Vulnerability in Jenkins.
- CUPS – Sep2025: CVE-2025-58364, CVE-2025-58060, Deserialization Vulnerability, Denial of Service Vulnerability, Authentication Bypass Vulnerability in CUPS.
- SharePoint – Sep2025: CVE-2025-54897, CVE-2025-53760, CVE-2025-53760, Deserialization Vulnerability, Code Execution Vulnerability, Server-Side Request Forgery (SSRF) Vulnerability in Microsoft SharePoint.
- MSSQL – Sep2025: CVE-2025-47997, CVE-2025-55227, Race Condition Vulnerability, Command Injection Vulnerability in Microsoft SQL Server.
- SAP NetWeaver – Sep2025: CVE-2025-42944, CVE-2025-42922, CVE-2025-42958, Insecure Deserialization Vulnerability, Insecure File Operations Vulnerability, Missing Authentication Check Vulnerability in SAP NetWeaver.
- Django : CVE-2025-57833, SQL Injection Vulnerability in Django.
- FreePBX : CVE-2025-57819, Remote Code Execution Vulnerability in Sangoma’s FreePBX.
- Vault – Sep2025 : CVE-2025-6203, DoS Vulnerability in HashiCorp Vault.
- Citrix NetScaler – Aug2025 : CVE-2025-7775, CVE-2025-7776, CVE-2025-8424, Memory Overflow Vulnerability, Remote Code Execution Vulnerability, DoS Vulnerability, Improper Access Control Vulnerability in Citrix NetScaler ADC/Gateway.
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTagTM at https://blackkite.com/cve-database/.
References
https://nvd.nist.gov/vuln/detail/cve-2025-20333
https://nvd.nist.gov/vuln/detail/cve-2025-20362
https://thehackernews.com/2025/09/urgent-cisco-asa-zero-day-duo-under.html?m=1
https://www.cve.org/CVERecord?id=CVE-2025-20333
https://www.cve.org/CVERecord?id=CVE-2025-20362
https://nvd.nist.gov/vuln/detail/CVE-2025-20363
https://nvd.nist.gov/vuln/detail/CVE-2025-30247
https://www.cve.org/CVERecord?id=CVE-2025-41250
https://cybersecuritynews.com/western-digital-my-cloud-devices-vulnerability
https://nvd.nist.gov/vuln/detail/CVE-2025-59934
https://github.com/formbricks/formbricks/security/advisories/GHSA-7229-q9pv-j6p4

