FOCUS FRIDAY: TPRM Insights on GoAnywhere MFT, SolarWinds Web Help Desk, Cisco SNMP, and DNN Software vulnerabilities
INTRODUCTION
Welcome to this week’s edition of Focus Friday, where we analyze some of the most pressing cybersecurity incidents from a Third-Party Risk Management (TPRM) perspective. In this installment, we turn our attention to four newly disclosed vulnerabilities that carry significant risk for organizations and their vendor ecosystems: a deserialization RCE flaw in GoAnywhere MFT, a patch-bypass RCE in SolarWinds Web Help Desk, a stack overflow bug in Cisco’s SNMP subsystem, and a critical stored XSS issue in DNN Software. Each of these vulnerabilities impacts widely deployed technologies, ranging from secure file transfer platforms and IT help desk systems to core network infrastructure and content management portals. Understanding their implications—and knowing how to focus your risk management efforts—is crucial to reducing exposure across your vendor landscape.
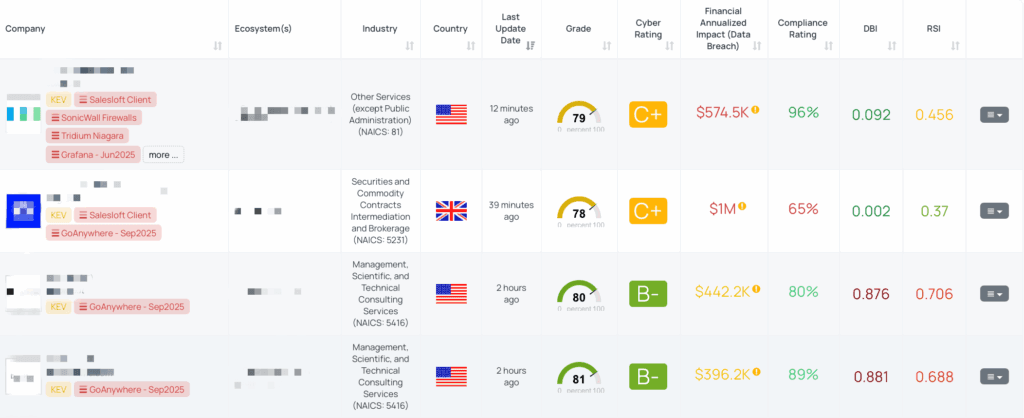
Filtered view of companies with GoAnywhere – Sep2025 FocusTag™ on the Black Kite platform.
CVE-2025-10035: GOANYWHERE MFT LICENSE SERVLET DESERIALIZATION RCE
What is the GoAnywhere deserialization vulnerability?
A critical deserialization vulnerability (CVE-2025-10035) has been identified in the License Servlet component of Fortra’s GoAnywhere Managed File Transfer (MFT) solution. The flaw allows an attacker who can present a forged license response signature to cause the application to deserialize an object they control, triggering arbitrary command execution (i.e. command injection).
Because this occurs in an endpoint tied to licensing operations, no prior authentication or user interaction is required, given the conditions are met.
The vulnerability carries a CVSS v3.1 score of 10.0 (Critical) and an EPSS score of 15.48%, highlighting both its severity and the elevated likelihood of exploitation.
Discovery / timeline
- The vulnerability was publicly disclosed on September 18, 2025, with an update date the same day.
- Fortra’s advisory indicates the issue was discovered during a security review around September 11, 2025.
Exploitation / known use in the wild
- At the time of disclosure, no proof-of-concept exploit or confirmed in-the-wild exploitation has been publicly reported.
- However, given the ease of exploitation and the history of GoAnywhere being targeted by ransomware groups in prior years, many security analysts warn that weaponization is likely imminent.
CISA / KEV status
- CVE-2025-10035 is not (yet) listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog.
- No published CISA advisory referencing this specific CVE is currently available.
- Because it is not yet in KEV, there is no mandated remediation timeline under BOD 22-01 for U.S. federal agencies tied to this CVE.
Why should TPRM professionals care about this?
GoAnywhere MFT is a file transfer solution often used in B2B, supply chain, financial, and integration contexts. If compromised, it could be used to:
- Access, manipulate, or exfiltrate sensitive data flowing through the vendor’s environment
- Use the compromised host as a foothold to pivot laterally into the vendor’s internal networks
- Impersonate or interfere with the vendor’s file transfer operations (e.g. disrupt data pipelines)
- Serve as a clean-up or stage for secondary malware deployment or data staging
From a third-party risk viewpoint, a vendor whose GoAnywhere instance is exposed to this vulnerability is a higher-risk node. It raises the possibility that even if the vendor is otherwise well-managed, this one “crown-jewel” application can grant attackers full control.
Because the exploit is unauthenticated and easily triggered (given conditions), the threat surface extends to any publicly exposed admin/license endpoint of GoAnywhere. Many organizations (or their vendors) might have these systems mistakenly internet-accessible for convenience or integrations.
What questions should TPRM professionals ask vendors?
Below are vendor-specific questions you can ask in the wake of this FocusTag:
- Have you upgraded all instances of Fortra’s GoAnywhere MFT to version 7.8.4 (Standard Release) or 7.6.3 (Sustain Release) to mitigate the risk of CVE-2025-10035?
- Can you confirm if you have implemented enhanced monitoring of application, web server, and system logs to detect unusual or malformed requests to the License Servlet, unexpected process execution originating from the GoAnywhere MFT service, or any unauthorized outbound connections from the server?
- Have you restricted access to the GoAnywhere MFT Admin Console by placing it behind a robust firewall or VPN and configuring strict access control lists (ACLs) to allow connections only from trusted internal IP addresses?
- Have you conducted an audit of your network architecture and firewall rules to confirm that no administrative ports for GoAnywhere MFT (e.g., 8000, 8001) are publicly accessible and that any required external access is strictly controlled and monitored?
Remediation Recommendations for Vendors
Below are recommended remediation and mitigation steps for vendors whose systems may be affected:
- Upgrade immediately: Move GoAnywhere MFT instances to versions 7.8.4 (latest) or 7.6.3 (sustain branch) which include fixes to block this deserialization path.
- Remove public exposure: Ensure the GoAnywhere Admin Console and License Servlet endpoints are not publicly reachable. Place them behind VPNs, firewalls, or IP-restricted access.
- Configure class whitelisting / validation: Use safe deserialization patterns, enforce whitelisting of allowed object types, and validate classes carefully.
- Tighten network segmentation & ACLs: Even internal access should be limited. Segregate critical MFT infrastructure and restrict which internal systems can communicate with it.
- Monitor & log aggressively: Enable deep logging on License Servlet endpoints, including capturing exceptions involving SignedObject.getObject or unexpected class deserialization traces. Trigger alerts for anomalies.
- Conduct threat hunts and audits: Scan for suspicious tooling, outbound traffic from the MFT host, or any unexplained processes on the host.
- Maintain rapid patch cycles: Given the speed of exploit development, aim for faster patch adoption windows going forward (e.g. test & deploy within days).
- Document compensating controls: For any interim period before patching, document the compensations (e.g. blocking, ACLs, monitoring) and obtain senior approval.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite published the GoAnywhere – Sep2025 FocusTag shortly after identifying potential exposures. The tag is meant to help customers identify which of their vendors are impacted by CVE-2025-10035 and thereby prioritize outreach and assessment.
Here’s how TPRM teams can operationalize this:
- Vendor filtering: Use the FocusTag to narrow down your vendor population to only those with GoAnywhere MFT instances exposed to the internet (or that match vendor-provided indicators).
- Asset intelligence: Black Kite can map the vendor’s publicly facing IPs, subdomains, or hosts that host the vulnerable service (License Servlet), giving you concrete targets to validate or cross-check vendor responses.
- Alerting and timeline tracking: As Black Kite updates the tag (e.g. with new IPs or newly observed exposures), your team stays current and can revisit vendors previously deemed safe.
- Prioritizing risk outreach: Rather than sending full questionnaires to all vendors, focus your questions and technical requests to only those tagged under GoAnywhere – this saves time and reduces “fatigue.”
- Historical context / updates: If Black Kite later issues updates to the tag (e.g. new exposures, further exploit details, or expiration changes), TPRM professionals will see the lineage and know which vendors to revisit.
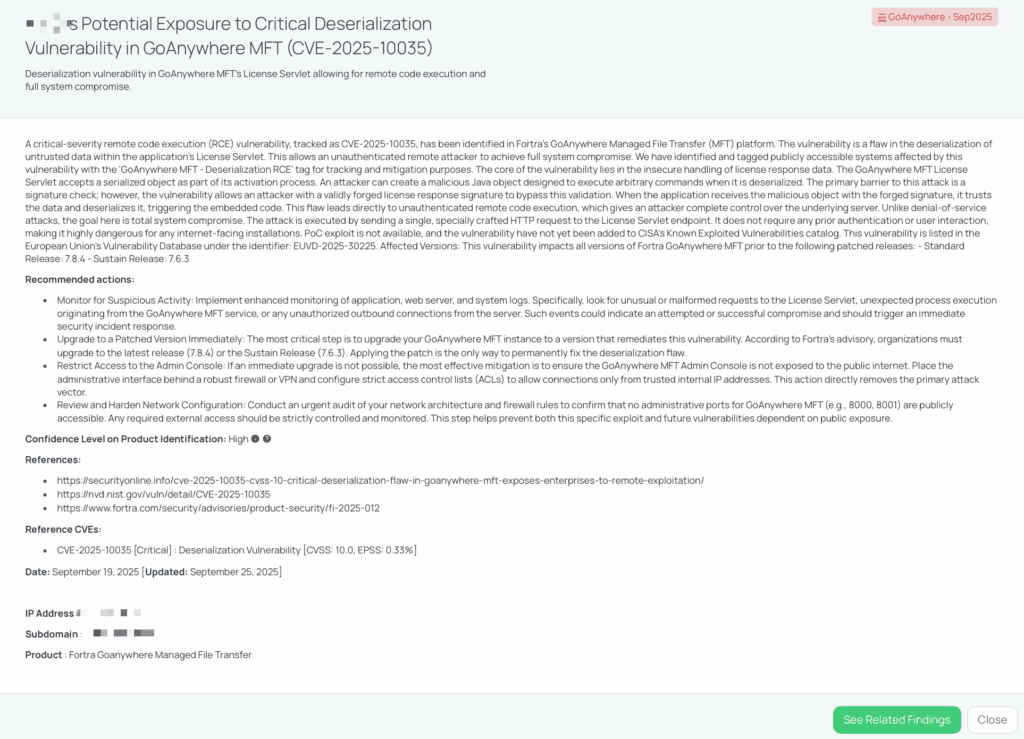
Black Kite’s GoAnywhere – Sep2025 FocusTagTM details critical insights on the event for TPRM professionals.
CVE-2025-26399: SOLARWINDS WEB HELP DESK REMOTE CODE EXECUTION
What is the SolarWinds Web Help Desk vulnerability?
CVE-2025-26399 is a critical remote code execution vulnerability affecting SolarWinds Web Help Desk. It results from insufficient validation during deserialization of untrusted data in the AjaxProxy component, allowing an unauthenticated attacker to execute arbitrary commands on the host system. This vulnerability acts as a patch-bypass over earlier fixes (notably CVE-2024-28988, which in turn bypassed CVE-2024-28986).
The vulnerability has a CVSS score of 9.8 (Critical) and an EPSS of 0.16 %. It was publicly disclosed in mid-September 2025, with SolarWinds releasing a hotfix (WHD 12.8.7 Hotfix 1) to address the flaw shortly thereafter. Although no public proof-of-concept or confirmed in-the-wild exploitation has been reported specifically for CVE-2025-26399, its predecessors (especially CVE-2024-28986) were actively exploited and have been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog.
Specifically, CVE-2024-28986 was added to CISA’s KEV list on August 15, 2024, following evidence of its active exploitation. That original vulnerability allowed unauthenticated attackers to execute commands via deserialization in AjaxProxy, and its impact was observed in real-world campaigns. Because CVE-2025-26399 bypasses earlier patches, it inherits a high risk even without public exploit confirmation.
Why should TPRM professionals care about this vulnerability?
Web Help Desk is frequently used by organizations (including technology service providers) for ticketing, asset tracking, and workflow automation. A compromise of a vendor’s Web Help Desk instance can lead to:
- Full system takeover (since the vulnerability allows code execution)
- Exposure or manipulation of help-desk tickets, which may include usernames, credentials, or sensitive internal data
- Use of the compromised system as a pivot point into other parts of the vendor’s infrastructure
- Disruption of IT support processes or manipulation of ticketing workflows
- Masking of malicious activity under the cover of legitimate help-desk operations
From a third-party risk lens, if a vendor’s instance is vulnerable, that vendor becomes a significantly higher risk, even if they otherwise maintain strong security practices elsewhere. Because this flaw bypasses prior fixes, the threat surface is broader: even vendors who patched earlier vulnerabilities may still be exposed.
What questions should TPRM professionals ask vendors?
To triage vendor risk around CVE-2025-26399, consider asking:
- Can you confirm if you have updated all instances of SolarWinds Web Help Desk to version 12.8.7 HF1 to mitigate the risk of CVE-2025-26399, CVE-2024-28988, and CVE-2024-28986?
- Have you implemented measures to restrict public access to the Web Help Desk, ensuring it is only accessible from trusted internal networks as recommended in the advisory?
- Are you actively monitoring system and network logs for unusual requests or unauthorized command execution related to Web Help Desk, specifically in relation to the AjaxProxy component?
- Given that the AjaxProxy component comes preinstalled and enabled by default in SolarWinds Web Help Desk, have you taken any additional steps to secure this component, considering its involvement in the mentioned vulnerabilities?
Remediation Recommendations for Vendors
Here are practical steps vendors should take:
- Apply Hotfix Immediately: Upgrade to Web Help Desk version 12.8.7 and install Hotfix 1, which addresses CVE-2025-26399.
- Review All Web Help Desk Instances: Inventory all deployments (production, staging, development) and ensure none remain on vulnerable versions.
- Restrict Exposure: Limit access to the AjaxProxy interface. Internal-only exposure or network segmentation is essential. Do not leave it publicly accessible.
- Enable Deep Logging & Alerts: Capture logs around deserialization operations, errors, and class loading, and trigger alerts on anomalous behavior.
- Conduct Post-patch Validation & Review: After patching, verify that exploit paths have been closed and run scanning or pen testing targeting the AjaxProxy interface.
- Segment and Harden Infrastructure: Isolate Web Help Desk systems, enforce least privilege, and monitor communication paths from that system into other segments.
- Document Interim Controls: If immediate patching isn’t possible, implement compensating controls (e.g. firewall restrictions, WAF rules, internal access only) and formalize them in the risk plan.
How TPRM professionals can leverage Black Kite for this vulnerability
When Black Kite publishes the SolarWinds Web Help Desk – Sep2025 FocusTag, it enables TPRM teams to:
- Filter vendor universe to those with exposed Web Help Desk assets or matching indicator patterns
- Obtain asset insight, including IP addresses, subdomains, or hosts running vulnerable Web Help Desk instances
- Track changes over time as Black Kite updates the tag with new observations or asset discoveries
- Prioritize vendor outreach by focusing on those flagged under this FocusTag (versus blanket questionnaires)
- Revisit previously assessed vendors if new exposures are added or the tag is revised
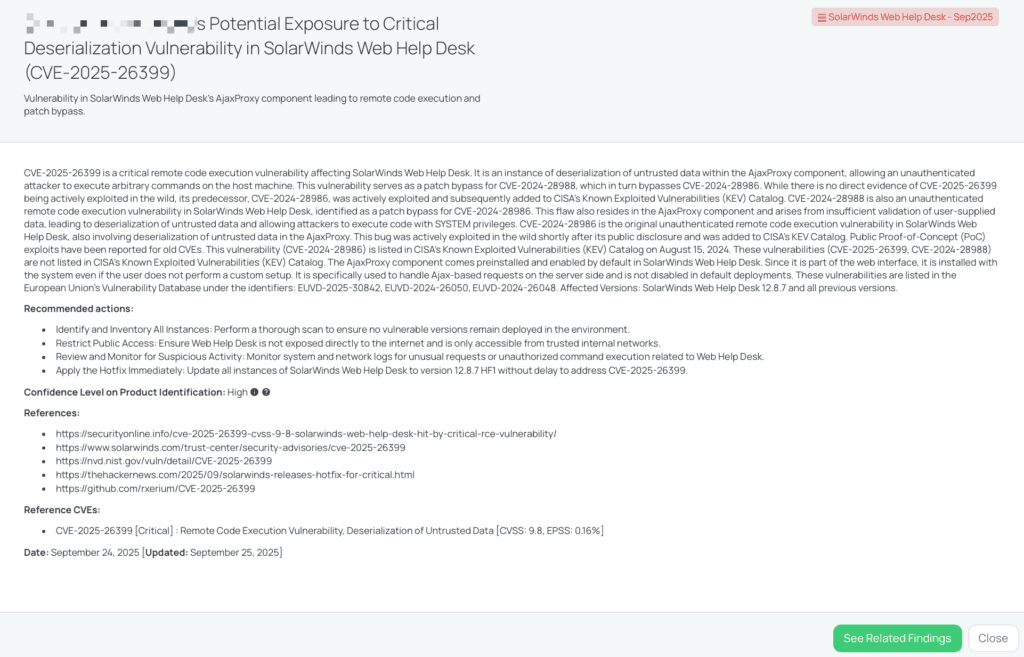
Black Kite’s SolarWinds Web Help Desk – Sep2025 FocusTagTM details critical insights on the event for TPRM professionals.
CVE-2025-20352: CISCO IOS/IOS XE SNMP STACK OVERFLOW
What is the Cisco SNMP vulnerability?
CVE-2025-20352 is a stack overflow vulnerability in the SNMP subsystem of Cisco IOS and IOS XE software (CWE-121). Under certain conditions, an authenticated attacker (using SNMPv2c read-only community or valid SNMPv3 credentials) can send a crafted SNMP packet that triggers a denial-of-service (DoS) on affected devices by forcing a reload. In higher privilege cases (e.g., administrative credentials in IOS XE), the same flaw permits remote code execution as root.
The vulnerability is rated High (CVSS 7.7) with an EPSS of 0.18 %. It was included in Cisco’s September 2025 patch release, where multiple vulnerabilities were addressed. Cisco has acknowledged in-the-wild exploitation — after local administrator credentials were compromised — indicating attackers have leveraged it in real attacks.
Despite this, CVE-2025-20352 is not currently listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog.
You can access the full list of affected versions in here.
Why should TPRM professionals care about this?
Cisco devices—routers, switches, and network infrastructure—are foundational in most vendor environments. A successful exploit here can lead to:
- Full compromise of network infrastructure (routing, switching)
- Loss of control over device configurations and traffic flows
- Potential pivoting into more sensitive segments of the vendor’s network
- Undetected persistence given control at the operating system level
- Denial of service, causing network disruption or outages
From a third-party risk viewpoint, any vendor environment that uses Cisco IOS or IOS XE devices with SNMP enabled—and especially if administrative SNMP access is permitted—represents an elevated risk vector. A breach of such devices could impact not only the vendor’s operations but also affect downstream connectivity or trust with your systems.
What questions should TPRM professionals ask vendors about this vulnerability?
Below are focused questions tied to CVE-2025-20352:
- Have you updated all affected Cisco devices running IOS and IOS XE Software to the fixed versions, specifically Cisco IOS XE Software Release 17.15.4a and later, and Meraki CS versions later than 17 for Meraki MS390 and Cisco Catalyst 9300 Series Switches, to mitigate the risk of CVE-2025-20352?
- Have you implemented the recommended mitigation of explicitly excluding the affected object ID (OID) from SNMP processing as a temporary measure until patches can be fully deployed to address the stack overflow vulnerability in the SNMP subsystem of Cisco IOS and IOS XE Software?
- Can you confirm if you have reviewed and restricted SNMP access on all Cisco devices, ensuring that only necessary devices and users have SNMP enabled and that strong, unique community strings (for SNMPv1/v2c) or robust user credentials (for SNMPv3) are in use?
- Have you regularly audited administrative and privilege 15 credentials on Cisco devices running IOS XE Software to ensure they adhere to the principle of least privilege and monitored for any anomalous activity related to SNMP or privilege escalation attempts?
Remediation Recommendations for Vendors
Here are recommended steps vendors should take to mitigate the risk:
- Apply the official updates: Move all Cisco IOS and IOS XE devices to fixed versions that close CVE-2025-20352. Cisco’s September update includes patches addressing this issue.
- Disable SNMP where unnecessary: If SNMP is not strictly required, disable it entirely.
- Restrict SNMP access: For devices where SNMP must remain active, restrict access to trusted hosts or networks only.
- Harden SNMP configuration: Use SNMPv3 with strong authentication and encryption; avoid default or weak community strings.
- Implement OID exclusions (if available): If Cisco advisory provides specific object identifiers to omit from SNMP processing, configure OID exclusion as a mitigation step until patches are in place.
- Segment network and restrict management paths: Ensure that SNMP traffic is isolated, and that management paths to critical devices are layered behind access control.
- Monitor and audit: Enable logging for unusual SNMP requests, buffer overrun alerts, or unexpected reboots. Cross-check for signs of misuse.
- Post-patch validation and penetration testing: After patching, simulate exploit attempts or run fuzz testing against SNMP services to verify vulnerabilities are closed.
How TPRM professionals can leverage Black Kite for this vulnerability
Once Black Kite publishes the Cisco SNMP – Sep2025 FocusTag, TPRM teams can use it to:
- Filter vendor lists to those with Cisco devices, SNMP exposure, or matching indicators
- Receive asset-level intelligence, such as public IPs or hosts associated with vendor SNMP services
- Monitor updates or new observations — for example, if new SNMP-exposed assets appear or threat activity intensifies
- Prioritize outreach by focusing on vendors triggered by the tag rather than a broad sweep
- Reassess vendors over time if the tag is updated or expanded
This capability allows a more surgical, data-driven third-party risk process rather than broad blanket actions.
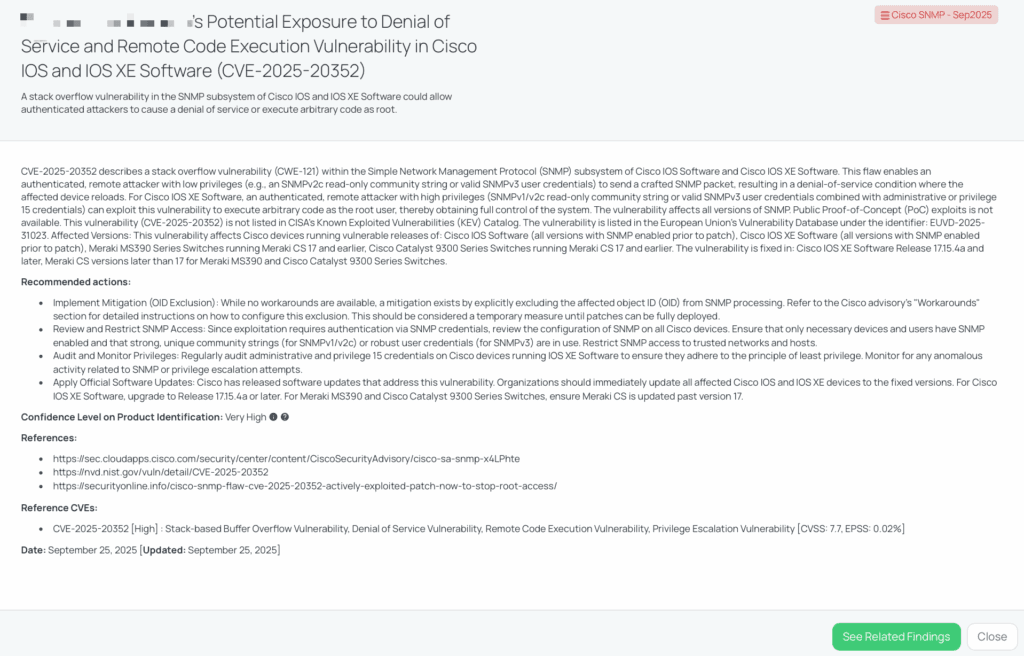
Black Kite’s Cisco SNMP – Sep2025 FocusTagTM details critical insights on the event for TPRM professionals.
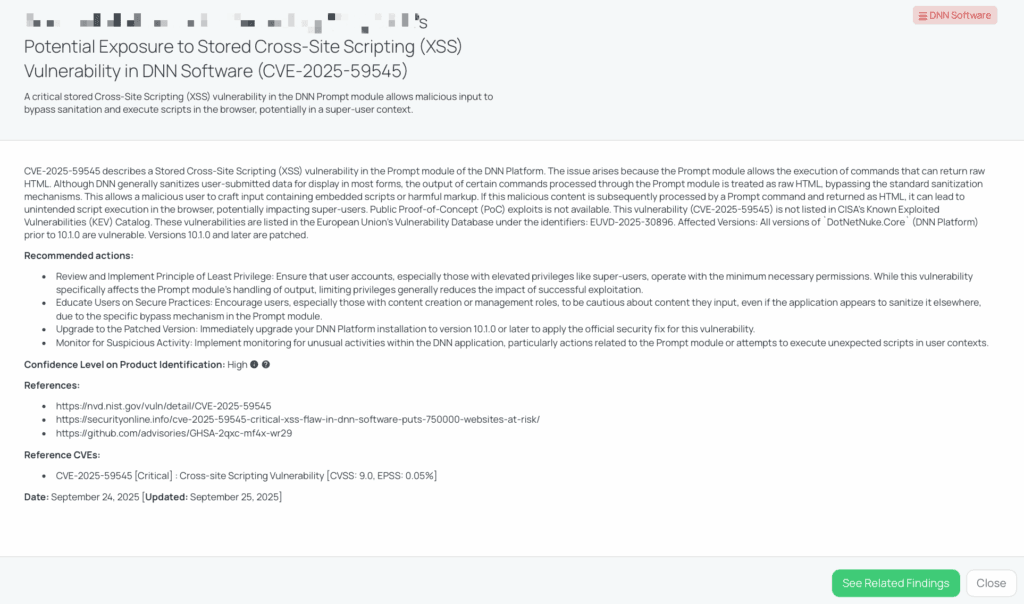
CVE-2025-59545: DNN PROMPT MODULE STORED XSS
The DNN Prompt Module is a command-line style interface within the DNN (DotNetNuke) Platform that allows administrators and advanced users to execute commands directly against the application for management and configuration tasks. It is designed to streamline administrative operations but, if insecurely implemented, can expose risks such as improper command handling or script injection.
What is the DNN Prompt XSS vulnerability?
CVE-2025-59545 is a stored cross-site scripting (XSS) vulnerability in the Prompt module of the DNN (DotNetNuke) platform. The issue arises because the Prompt module permits commands whose output is returned as raw HTML, bypassing the usual sanitization routines applied by DNN in other modules. An attacker can craft malicious input containing embedded scripts or markup, and when that input is processed through the Prompt command, the scripts execute in the browser context—potentially with elevated privileges (e.g. super-users).
The vulnerability is rated Critical (CVSS 9.1) with an EPSS of 0.05 %, per the FocusTag data. It was made public in late September 2025. Although no public proof-of-concept or known in-the-wild exploitation has been reported for CVE-2025-59545, its severity and bypass nature make it a serious concern. The issue is not (yet) listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog.
Affected versions include all DNN Platform (DotNetNuke.Core) versions prior to 10.1.0, which are vulnerable. Version 10.1.0 and later have been patched to address this flaw.
Why should TPRM professionals care about this vulnerability?
DNN is a content management framework often used by organizations and service providers for web portals, intranets, and partner-facing sites. A stored XSS in the Prompt module is dangerous because:
- It could allow script execution in contexts of elevated users, possibly exposing session tokens, cookies, or enabling further escalation.
- Attackers could insert persistent malicious scripts that compromise the integrity of vendor web content or trick users (e.g. employees, clients) into actions.
- Because the Prompt module is capable of executing custom commands, an attacker might chain this vulnerability into other exploitation or lateral moves.
- From a third-party risk angle, a vendor whose DNN instance is vulnerable increases your supply chain exposure: even if the vendor manages many parts well, this single web vulnerability can be a pivot point.
In effect, it makes the vendor’s web presence (particularly administrative or integration interfaces) a higher risk that demands scrutiny.
What questions should TPRM professionals ask vendors?
Here are targeted questions for assessing vendor exposure to CVE-2025-59545:
- Can you confirm if you have upgraded all instances of DNN Software to version 10.1.0 or later to mitigate the risk of CVE-2025-59545?
- Have you implemented monitoring for unusual activities within the DNN application, particularly actions related to the Prompt module or attempts to execute unexpected scripts in user contexts?
- Have you reviewed and implemented the Principle of Least Privilege to ensure that user accounts, especially those with elevated privileges like super-users, operate with the minimum necessary permissions?
- Have you educated your users, especially those with content creation or management roles, on secure practices to be cautious about content they input, even if the application appears to sanitize it elsewhere, due to the specific bypass mechanism in the Prompt module?
Remediation Recommendations for Vendors
Here are steps vendors should take to remediate or mitigate:
- Upgrade immediately to DNN Platform version 10.1.0 or later, which includes the fix for this vulnerability.
- Audit Prompt module usage: review all commands or features using Prompt, and limit them to minimal functionality or remove unnecessary features.
- Implement strict output sanitization: where possible, enforce HTML encoding or sanitization on output from Prompt commands.
- Restrict access: limit who can trigger the Prompt module (e.g. only trusted or administrative users).
- Alert & monitor: set up logging of any command execution via Prompt, track anomalous inputs, and trigger alerts on suspicious patterns.
- Conduct focused security testing (e.g. penetration tests) targeting Prompt endpoints to confirm that no XSS vectors remain.
How TPRM professionals can leverage Black Kite for this vulnerability
When Black Kite issues the DNN Software FocusTag (based on CVE-2025-59545), TPRM teams can:
- Filter vendor list to those operating DNN (DotNetNuke) instances, especially with publicly exposed installations or modules.
- Receive asset-level intelligence, such as domains, subdomains, or endpoints suspected of hosting vulnerable DNN Prompt modules.
- Track updates or new observations if Black Kite adds exposures or newly discovered vulnerable endpoints over time.
- Prioritize outreach — instead of blanket questionnaires, target vendors flagged by the tag and ask focused technical questions.
- Reassess vendors if the tag is updated or enriched, allowing you to revisit previously assessed vendors if new data emerges.
Black Kite’s DNN Software FocusTagTM details critical insights on the event for TPRM professionals.
ENHANCING TPRM STRATEGIES WITH BLACK KITE’S FOCUSTAGS™
In the context of this week’s vulnerabilities, the value of Black Kite’s FocusTags™ becomes even clearer. These tags are designed to equip TPRM teams with actionable intelligence that simplifies vendor risk evaluation and strengthens overall cyber resilience.
Key benefits include:
- Immediate Exposure Detection: Quickly highlight vendors affected by high-risk vulnerabilities like the GoAnywhere deserialization flaw, SolarWinds patch-bypass RCE, Cisco SNMP stack overflow, or DNN stored XSS.
- Risk Prioritization at Scale: By aligning the severity of each vulnerability with the importance of specific vendors, organizations can allocate resources more strategically and respond faster.
- Action-Driven Vendor Engagement: FocusTags enable targeted conversations with vendors about their specific security posture and remediation efforts, eliminating unnecessary questionnaires.
- Holistic Risk View: Beyond individual incidents, FocusTags provide a comprehensive picture of how evolving vulnerabilities may ripple through the supply chain, helping organizations develop proactive defenses.
Black Kite’s FocusTags™ transform complex vulnerability data into intelligence that directly informs decision-making, enabling TPRM professionals to act quickly and precisely in the face of evolving threats.
ABOUT FOCUS FRIDAY
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FOCUSTAGS™ IN THE LAST 30 DAYS:
- GoAnywhere – Sep2025: CVE-2025-10035, Deserialization Remote Code Execution Vulnerability in Fortra GoAnywhere MFT.
- SolarWinds Web Help Desk – Sep2025: CVE-2025-26399, Remote Code Execution Vulnerability in SolarWinds Web Help Desk.
- Cisco SNMP – Sep2025: CVE-2025-20352, Stack Overflow Vulnerability leading to DoS and Remote Code Execution in Cisco IOS and IOS XE Software.
- DNN Software: CVE-2025-59545, Stored Cross-Site Scripting (XSS) Vulnerability in DNN Prompt Module.
- Jetty – MadeYouReset: CVE-2025-5115, MadeYouReset DoS Vulnerability in Eclipse’s Jetty.
- Jenkins – Sep2025: CVE-2025-59474, CVE-2025-59475, CVE-2025-59476, Information Disclosure Vulnerability, Log Message Injection Vulnerability in Jenkins.
- CUPS – Sep2025: CVE-2025-58364, CVE-2025-58060, Deserialization Vulnerability, Denial of Service Vulnerability, Authentication Bypass Vulnerability in CUPS.
- SharePoint – Sep2025: CVE-2025-54897, CVE-2025-53760, CVE-2025-53760, Deserialization Vulnerability, Code Execution Vulnerability, Server-Side Request Forgery (SSRF) Vulnerability in Microsoft SharePoint.
- MSSQL – Sep2025: CVE-2025-47997, CVE-2025-55227, Race Condition Vulnerability, Command Injection Vulnerability in Microsoft SQL Server.
- SAP NetWeaver – Sep2025: CVE-2025-42944, CVE-2025-42922, CVE-2025-42958, Insecure Deserialization Vulnerability, Insecure File Operations Vulnerability, Missing Authentication Check Vulnerability in SAP NetWeaver.
- Django : CVE-2025-57833, SQL Injection Vulnerability in Django.
- FreePBX : CVE-2025-57819, Remote Code Execution Vulnerability in Sangoma’s FreePBX.
- Vault – Sep2025 : CVE-2025-6203, DoS Vulnerability in HashiCorp Vault.
- Citrix NetScaler – Aug2025 : CVE-2025-7775, CVE-2025-7776, CVE-2025-8424, Memory Overflow Vulnerability, Remote Code Execution Vulnerability, DoS Vulnerability, Improper Access Control Vulnerability in Citrix NetScaler ADC/Gateway.
- Salesforce Tableau – Aug2025 : CVE-2025-26496, CVE-2025-26497, CVE-2025-26498, CVE-2025-52450, CVE-2025-52451, Type Confusion Vulnerability, Remote Code Execution Vulnerability, Unrestricted File Upload Vulnerability, Path Traversal Vulnerability, Improper Input Validation Vulnerability in Salesforce Tableau.
- MadeYouReset HTTP/2 DoS Attack : CVE-2025-8671, CVE-2025-48989, CVE-2025-54500, CVE-2025-55163, CVE-2025-36047, MadeYouReset DoS Vulnerability in HTTP/2.
- Ivanti Connect Secure – Aug2025 : CVE-2025-5456, CVE-2025-5462, Out-of-bound Read Vulnerability, DoS Vulnerability, Buffer Overflow Vulnerability in Ivanti Connect Secure (ICS), Ivanti Policy Secure (IPS), Ivanti ZTA Gateway, Ivanti Neurons for Secure Access.
- PostgreSQL – Aug2025 : CVE-2025-8713, CVE-2025-8714, CVE-2025-8715, Arbitrary Code Injection Vulnerability, Exposure of Sensitive Information Vulnerability in PostgreSQL.
- Plesk Obsidian : CVE-2025-54336, Incorrect Comparison Vulnerability in Plesk Obsidian.
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTagTM at https://blackkite.com/cve-database/.
REFERENCES
https://nvd.nist.gov/vuln/detail/CVE-2025-10035
https://www.fortra.com/security/advisories/product-security/fi-2025-012
https://www.cve.org/CVERecord?id=CVE-2025-10035
https://nvd.nist.gov/vuln/detail/CVE-2025-26399
https://www.solarwinds.com/trust-center/security-advisories/cve-2025-26399
https://thehackernews.com/2025/09/solarwinds-releases-hotfix-for-critical.html
https://github.com/rxerium/CVE-2025-26399
https://nvd.nist.gov/vuln/detail/CVE-2025-20352
https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-snmp-x4LPhte
https://www.cve.org/CVERecord?id=CVE-2025-20352
https://nvd.nist.gov/vuln/detail/CVE-2025-59545