Focus Friday: TPRM Insights on Adobe ColdFusion, Joomla, Apache Superset, and NextCloud Vulnerabilities
Written by: Kat Desy
Written by: Ferhat Dikbiyik
Additional Contributions: Ferdi Gül and Yavuz Han
Edited by: Katherine Desy
Welcome to this week’s edition of Focus Friday, where we delve into the world of Third-Party Risk Management (TPRM) through the lens of recent high-profile cybersecurity vulnerabilities. Today, we’re examining four critical vulnerabilities that have been making waves in the cybersecurity landscape: Adobe ColdFusion, Joomla, Apache Superset, and NextCloud Servers. Each of these vulnerabilities presents unique challenges and risks, and understanding them is key to fortifying your TPRM strategies. Let’s explore the details of these vulnerabilities and learn how Black Kite’s Focus Tags™ can be instrumental in managing these threats effectively.
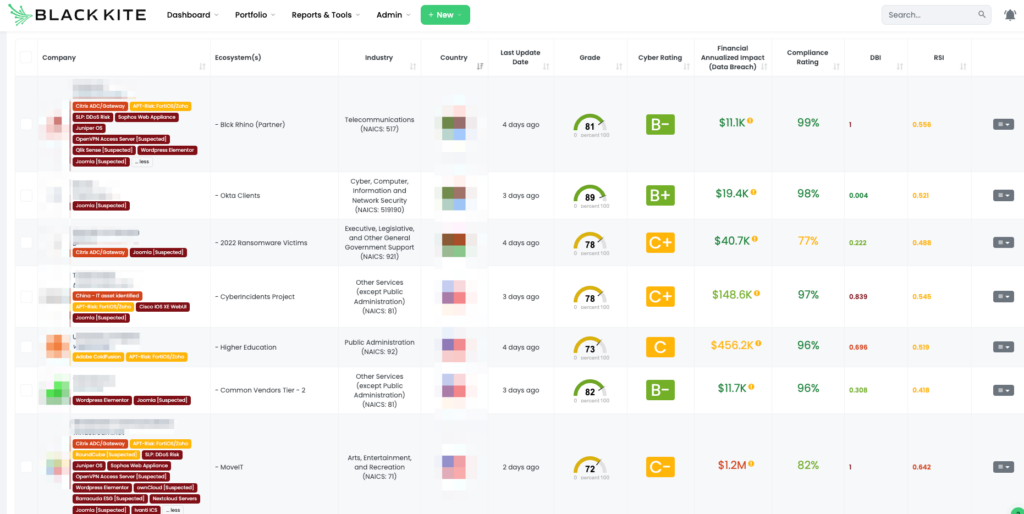
Addressing Adobe ColdFusion Vulnerabilities: CVE-2023-29300 and CVE-2023-38203
What Are the Deserialization Vulnerabilities in Adobe ColdFusion?
CVE-2023-38203 and CVE-2023-29300 are critical deserialization vulnerabilities in Adobe ColdFusion, affecting versions 2018, 2021, and 2023. These vulnerabilities, both rated at a CVSS score of 9.8, indicate a critical severity level. Deserialization of untrusted data in these versions can lead to arbitrary code execution without user interaction. CVE-2023-38203 affects versions up to 2018u17, 2021u7, and 2023u1, while CVE-2023-29300 impacts versions up to 2018u16, 2021u6, and the initial 2023 release. Both vulnerabilities have been recognized as being exploited in the wild and were added to CISA’s Known Exploited Vulnerabilities Catalog on January 8, 2024, signaling an urgent need for remediation.
Why Should TPRM Professionals Focus on Adobe ColdFusion Vulnerabilities?
For TPRM professionals, the critical nature of CVE-2023-29300 and CVE-2023-38203 in Adobe ColdFusion represents a significant security risk. These vulnerabilities could allow attackers to execute arbitrary code on systems running vulnerable ColdFusion versions, potentially leading to data breaches or further network compromise. Given Adobe ColdFusion’s widespread use for web development, these vulnerabilities pose a high risk to any vendor utilizing this platform. TPRM professionals must ensure their vendors are aware of these vulnerabilities and have taken necessary actions to mitigate them.
What Questions Should TPRM Professionals Ask Vendors About Adobe ColdFusion Vulnerabilities?
To assess the impact of CVE-2023-29300 and CVE-2023-38203, TPRM professionals should ask:
- “Have you updated Adobe ColdFusion to the latest patched versions to address these vulnerabilities?”
- “What measures are in place to detect and prevent unauthorized code execution on your ColdFusion servers?”
- “Can you confirm the implementation of security configurations recommended by Adobe for ColdFusion?”
- “How do you monitor for signs of exploitation or unusual activities related to these vulnerabilities?”
Recommended Remediation Actions for Vendors Impacted by Adobe ColdFusion Vulnerabilities:
Vendors affected by CVE-2023-29300 and CVE-2023-38203 should:
- Upgrade Adobe ColdFusion to the latest version that patches these vulnerabilities.
- Follow Adobe’s guidance on updating ColdFusion JDK/JRE LTS versions and confirm compatibility.
- Apply security configurations as outlined on Adobe’s ColdFusion Security page and Lockdown guides.
- Regularly scan the server for vulnerabilities and maintain updated security patches.
- Implement strong access controls and regularly review system logs for suspicious activities.
Leveraging Black Kite for Managing Adobe ColdFusion Vulnerability Risks:
Black Kite’s tag for Adobe ColdFusion vulnerabilities, published on July 19, 2023, and updated on January 9, 2024, is a crucial tool for TPRM professionals. It helps in identifying vendors using vulnerable versions of Adobe ColdFusion and provides insights into specific IT assets at risk. TPRM professionals can use this tag to prioritize vendor communication and risk mitigation strategies, ensuring a proactive approach to managing these significant vulnerabilities.
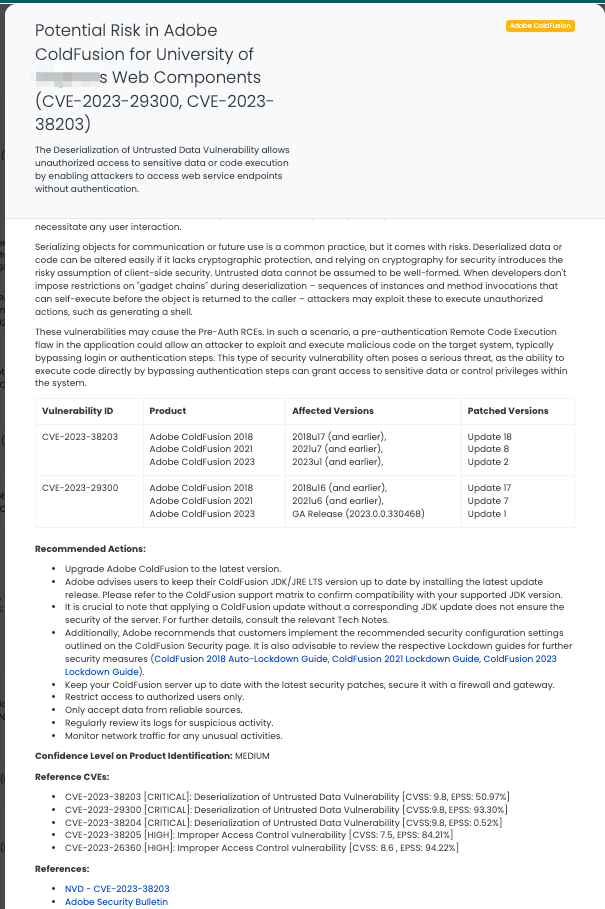
Joomla CVE-2023-23752: Improper Access Control Vulnerability
What Is the Improper Access Control Vulnerability in Joomla?
CVE-2023-23752 is a notable vulnerability in Joomla versions 4.0.0 through 4.2.7, identified as an improper access control issue. Classified with a CVSS score of 5.3, this medium-severity vulnerability allows unauthorized access to web service endpoints. Discovered on February 24, 2023, the vulnerability has been exploited in the wild, with threat actors leveraging it for unauthorized data access. Notably, the vulnerability was added to CISA’s Known Exploited Vulnerabilities Catalog on January 8, 2024, underscoring its criticality for immediate action. Though it is a medium-severity vulnerability, its exploitation in the wild recently makes the vulnerability worth having a Focus Tag.
Why Should TPRM Professionals Focus on Joomla Vulnerability?
For TPRM professionals, CVE-2023-23752 poses a considerable risk due to its potential for unauthorized data access and configuration disclosure. The exploitation of this vulnerability can lead to sensitive information leakage, such as database credentials, which could be used for more damaging attacks. As Joomla is a widely used content management system, the risk extends to a significant number of vendors and necessitates prompt attention.
What Questions Should TPRM Professionals Ask Vendors?
To understand the impact and mitigation of CVE-2023-23752, consider asking the following:
- “Have you updated Joomla to version 4.2.8 or later to address the vulnerability?”
- “Can you detail the measures implemented to prevent unauthorized access to web service endpoints?”
- “How do you monitor and respond to unauthorized attempts to access sensitive data?”
- “Are there any additional security controls in place to safeguard against similar vulnerabilities?”
Remediation Recommendations for Affected Vendors
Vendors impacted by CVE-2023-23752 should:
- Promptly update Joomla to version 4.2.8, which contains the necessary patches.
- Review and strengthen access control mechanisms to web service endpoints.
- Continuously monitor for unauthorized access attempts and anomalies in network traffic.
- Regularly audit system configurations and security settings to prevent similar vulnerabilities.
Leveraging Black Kite for Managing Joomla Vulnerability Risks
Black Kite’s tag for the Joomla vulnerability, released on [specific date], provides TPRM professionals with essential insights. It identifies vendors using vulnerable Joomla versions and guides in prioritizing risk mitigation strategies. Black Kite’s comprehensive approach helps operationalize these insights for proactive vulnerability management.
For detailed information on this vulnerability, you can refer to the NVD – CVE-2023-23752 and PingSafe’s analysis.
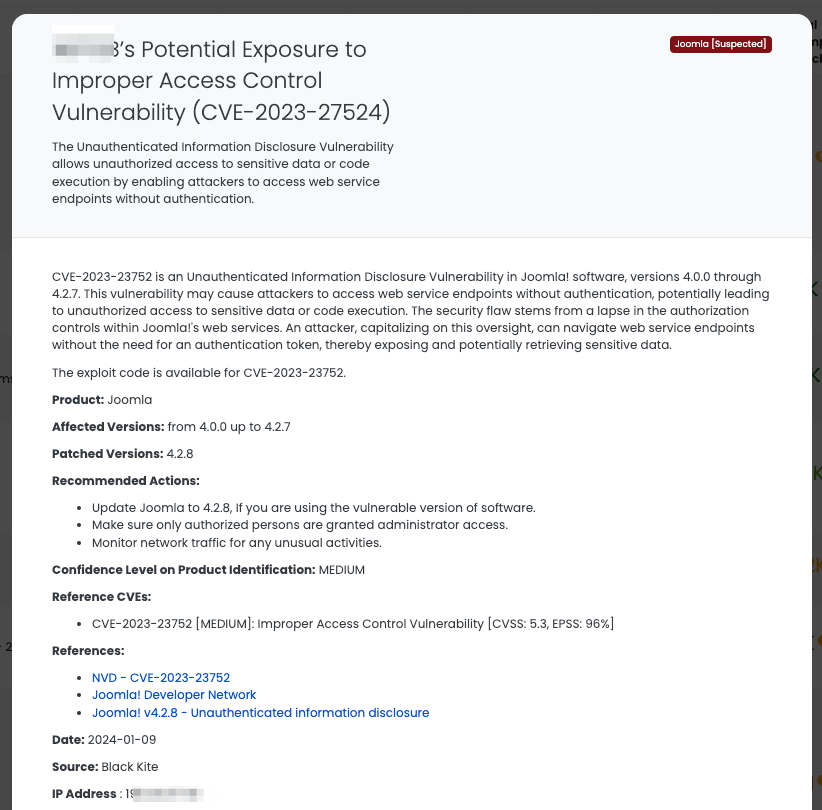
Understanding Apache Superset CVE-2023-27524 Vulnerability
What Is the Apache Superset Session Validation Attack Vulnerability?
CVE-2023-27524 is a critical vulnerability in Apache Superset versions up to 2.0.1, characterized as a session validation attack due to an insecure default initialization of resources. It’s notably severe, with a CVSS score of 9.8 (critical) and an EPSS score of 96%, indicating a high likelihood of exploitation. The flaw was discovered and publicized on April 24, 2023, and its exploitation in the wild led to its addition to CISA’s Known Exploited Vulnerabilities Catalog on January 8, 2024.
Why Should TPRM Professionals Focus on Apache Superset’s CVE-2023-27524?
TPRM professionals need to prioritize this vulnerability due to its high severity and potential for significant impact. The flaw allows attackers to access restricted resources and perform administrative actions, posing a serious risk to data integrity and system security. Given Apache Superset’s role in data exploration and visualization, the vulnerability can have widespread implications across different data ecosystems.
Key Questions for Vendors Regarding CVE-2023-27524
TPRM professionals should inquire specifically about the vulnerability’s mitigation:
- “Have you updated Apache Superset to version 2.0.2 or later to remediate CVE-2023-27524?”
- “Is the SECRET_KEY value in your Apache Superset installation unique and confidential?”
- “What measures are in place to detect unauthorized access or code execution related to this vulnerability?”
- “How do you ensure continuous monitoring and prompt response to potential exploitation attempts?”
Remediation Recommendations for Apache Superset CVE-2023-27524
Affected vendors should:
- Update Apache Superset to version 2.0.2 or higher.
- Change the default SECRET_KEY to a unique and secure value.
- Implement strong access controls and continuously monitor for unauthorized activities.
- Regularly audit security configurations and update them as necessary.
Leveraging Black Kite for Apache Superset CVE-2023-27524 Management
Black Kite’s Focus Tag, released on January 9, 2024, is an invaluable tool for TPRM professionals handling CVE-2023-27524. It aids in identifying affected vendors and provides critical data for prioritizing risk mitigation efforts. By leveraging this tag, professionals can adopt a proactive stance in managing the risks posed by this high-likelihood vulnerability.
For more detailed information on CVE-2023-27524, you can refer to sources like the National Vulnerability Database and Qualys ThreatPROTECT.
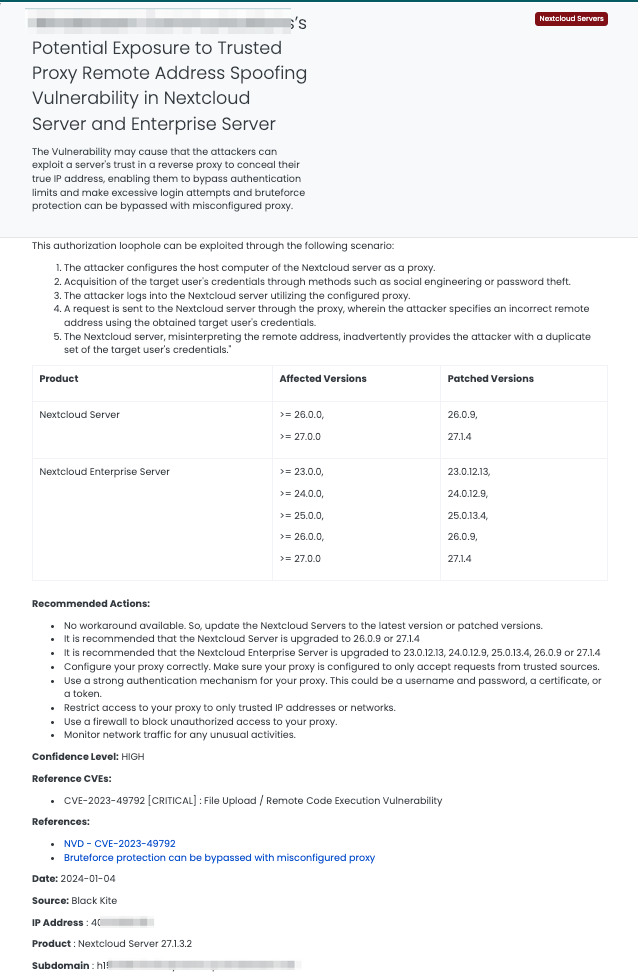
Understanding Nextcloud Server Vulnerability: CVE-2023-49792
What Is the Trusted Proxy Remote Address Spoofing Vulnerability in Nextcloud Server?
CVE-2023-49792 is a critical vulnerability found in various versions of Nextcloud Server and Nextcloud Enterprise Server. This vulnerability, classified under CWE-307 (Improper Restriction of Excessive Authentication Attempts), allows an attacker to mislead the server into reading an incorrect remote address when a trusted reverse proxy is configured. By doing so, an attacker can bypass brute-force protection mechanisms, leading to unauthorized authentication attempts. The vulnerability has a CVSS score of 9.8, indicating a critical level of severity. It was disclosed on December 22, 2023, and affected versions include Nextcloud Server prior to 26.0.9 and 27.1.4, as well as Nextcloud Enterprise Server prior to versions 23.0.12.13, 24.0.12.9, 25.0.13.4, 26.0.9, and 27.1.4.
Why Is This Vulnerability Significant for TPRM Professionals?
TPRM professionals should be particularly vigilant about CVE-2023-49792 due to its critical impact on authentication security. The vulnerability allows attackers to bypass authentication limits set by Nextcloud servers, potentially leading to unauthorized access and data breaches. This poses a significant risk to any organization using the affected versions of Nextcloud, as it compromises the integrity and confidentiality of stored data.
Essential Questions for Vendors Regarding CVE-2023-49792:
In addressing this vulnerability, TPRM professionals should ask the following questions:
- “Have you updated to the patched versions of Nextcloud Server or Nextcloud Enterprise Server?”
- “What measures have been implemented to ensure the correct configuration of reverse proxies?”
- “How are authentication attempts monitored to detect potential abuses?”
- “Are there any additional security controls in place to safeguard against similar vulnerabilities?”
Remediation Recommendations
For vendors affected by CVE-2023-49792, the following actions are recommended:
- Update to the latest patched versions of Nextcloud Server or Nextcloud Enterprise Server.
- Ensure the correct configuration of reverse proxies to prevent misinterpretation of remote addresses.
- Implement robust monitoring and alerting mechanisms to detect and respond to unusual authentication attempts.
- Conduct regular security audits to identify and rectify potential vulnerabilities.
Leveraging Black Kite for CVE-2023-49792 Risk Management
Black Kite’s Focus Tag for CVE-2023-49792, released on January 4, 2024, enables TPRM professionals to identify affected vendors and streamline their risk mitigation strategies. This tag provides crucial information for prioritizing and addressing the risks associated with this vulnerability, ensuring effective and proactive management.
For more detailed insights into this vulnerability, refer to the National Vulnerability Database NVD – CVE-2023-49792 and the vendor’s security advisory.
Enhancing TPRM Strategies with Black Kite’s Focus Tags™
In today’s rapidly evolving cyber threat landscape, staying ahead of vulnerabilities is imperative for robust Third-Party Risk Management (TPRM). Black Kite’s Focus Tags™ are at the forefront of this challenge, providing essential insights and tools to effectively manage these risks. The value of these tags becomes evident when faced with critical vulnerabilities like those in Adobe ColdFusion, Joomla, Apache Superset, and NextCloud Servers. Here’s how Black Kite’s Focus Tags™ transform TPRM practices:
- Real-Time Vulnerability Tracking: Instantly identifying vendors affected by the latest vulnerabilities allows for a swift and strategic response.
- Risk Prioritization: By evaluating both vendor importance and vulnerability severity, Focus Tags™ help in allocating resources more effectively.
- Informed Vendor Conversations: Facilitate targeted discussions with vendors, focusing on their specific security posture in relation to the identified vulnerabilities.
- Comprehensive Security Overview: With a broad view of the threat landscape, these tags aid in enhancing overall cybersecurity strategies.
Black Kite’s Focus Tags™, especially when dealing with the complexities of recent vulnerabilities in diverse systems, offer a streamlined, intelligent approach to TPRM, converting intricate cyber threat data into actionable intelligence. This capability is critical for managing risks efficiently and proactively in an environment where cyber threats are constantly evolving.
Want to take a closer look at Focus Tags™?
Take our platform for a test drive and request a demo today.
Focus Tags™ in the last 30 days:
- Adobe ColdFusion: CVE-2023-29300 and CVE-2023-38203, Deserialization of Untrusted Data Vulnerability [Updated]
- Joomla: CVE-2023-23752, Improper Access Control Vulnerability in Joomla
- Apache Superset Auth. Bypass: CVE-2023-27524, Insecure Default Initialization of Resource Vulnerability in Apache Superset
- NextCloud Servers: CVE-2023-49792, Trusted Proxy Remote Address Spoofing Vulnerability in Nextcloud Server and Enterprise Server
- Redis RCE: CVE-2023-41056, Remote Code Execution Vulnerability
- Ivanti ICS: CVE-2024-21887, Command Injection Vulnerability, CVE-2023-46805, Authentication Bypass Vulnerability
- Cacti SQLi: CVE-2023-51448, Blind SQL Injection (SQLi) Vulnerability
- Barracuda ESG: CVE-2023-7102, Parameter Injection Vulnerability
- Mlflow: CVE-2023-6753, A Path Traversal Vulnerability in MLflow.
- Elementor Plugin: CVE-2023-48777, File Upload / Remote Code Execution Vulnerabilities in The Elementor Website Builder versions identified before <=3.18.1
- APT Risk: FortiOS/Zoho: Vulnerabilities used by nation-state actors as part of Volt Typhoon campaign
- Atlassian Confluence Data Center and Server: CVE-2023-22522, Template Injection Vulnerability
- Adobe ColdFusion: CVE-2023-26360, Improper Access Control Vulnerability
- Qlik Sense: CVE-2023-48365, Unauthenticated RCE Vulnerability in Qlik Sense Enterprise for Windows
- Apache Superset: CVE-2023-40610, Privilege Escalation Vulnerability in Apache Superset <2.1.2 versions.
- OpenVPN Access: CVE-2023-46850, OpenVPN Access Server Flaw Exposes Sensitive Data and RCE Possible
- ownCloud: CVE-2023-49103, Information Disclosure Vulnerability in ownCloud’s Graphapi Component
References:
https://nvd.nist.gov/vuln/detail/CVE-2023-38203
https://helpx.adobe.com/security/products/coldfusion/apsb23-41.html
https://nvd.nist.gov/vuln/detail/CVE-2023-29300
https://helpx.adobe.com/security/products/coldfusion/apsb23-40.html
https://nvd.nist.gov/vuln/detail/CVE-2023-23752
https://www.exploit-db.com/exploits/51334
https://nvd.nist.gov/vuln/detail/CVE-2023-27524
https://www.openwall.com/lists/oss-security/2023/04/24/2
https://lists.apache.org/thread/n0ftx60sllf527j7g11kmt24wvof8xyk
https://nvd.nist.gov/vuln/detail/CVE-2023-49792 https://github.com/nextcloud/security-advisories/security/advisories/GHSA-5j2p-q736-hw98

